
J. Walter Thompson
J. Walter Thompson, incorporated by James Walter Thompson in 1896, in 2018 was "the biggest of five advertising holding companies that control a significant portion of the world's advertising, marketing and communications firms." It has been owned by WPP plc since 1987.
How to generate a JSON Web Token (JWT)?
JSON Web Tokens (JWT) mechanisms for user authentication are becoming more and more popular in applications. JWT gained particular popularity with the growing fame of the microservice architecture: it entrusts the processing authentication data to the microservices, and therefore allows the application to avoid various authorization errors, increase productivity and …
What's the difference between JWTs and Bearer Token?
Sep 20, 2021 · The contents in a json web token (JWT) are not inherently secure, but there is a built-in feature for verifying token authenticity. A JWT is three hashes separated by periods. A JWT is three hashes separated by periods.
How to create a JWT token?
JSON web token (JWT), pronounced "jot", is an open standard ( RFC 7519) that defines a compact and self-contained way for securely transmitting information between parties as a JSON object. Again, JWT is a standard, meaning that all JWTs are tokens, but not all tokens are JWTs.
What is a simple JSON?
Jun 04, 2020 · There are multiple ways to allow a service to be used securely. JSON web tokens are one of them, although there are limitations to the security that JSON web tokens provide. JSON Web Tokens(JWT) is a way of representing claims securely between two parties. It is known to be secure because the JWT can be signed using a secret or public/private key. A very …

Can JWT token be stolen?
Generally speaking, this is nice, but what happens if your entire JWT is stolen? Because JWTs are used to identify the client, if one is stolen or compromised, the attacker has full access to the user's account in the same way they would if the attacker had compromised the user's username and password instead.Oct 14, 2020
Should you use JSON Web Tokens?
Information Exchange: JWTs are a good way of securely transmitting information between parties because they can be signed, which means you can be sure that the senders are who they say they are. Additionally, the structure of a JWT allows you to verify that the content hasn't been tampered with.
What are the pros and cons of using JSON Web Tokens?
Pros and Cons of JWTsJWTs expire at specific intervals. When a JWT is created it is given a specific expiration instant. ... JWTs are signed. Since JWTs are cryptographically signed, they require a cryptographic algorithm to verify. ... JWTs aren't easily revocable. ... JWTs have exploits. ... Sessions as an Alternative.Nov 4, 2019
How do I secure my API with JSON Web Tokens?
How JWT works to secure APIThe user and the client app first send in the option of sign in. ... Once verified, your application API will generate a JWT token and then sign in using that API secret key. ... The API then will give back the token to the respective client application.More items...•Aug 19, 2020
What are JSON Web Tokens used for?
JWT, or JSON Web Token, is an open standard used to share security information between two parties — a client and a server. Each JWT contains encoded JSON objects, including a set of claims. JWTs are signed using a cryptographic algorithm to ensure that the claims cannot be altered after the token is issued.Dec 8, 2020
How can I make my JWT more secure?
JWT Security Best PracticesJSON Web Tokens Introduction. ... JWTs used as Access Tokens. ... What algorithms to use. ... When to validate the token. ... Always check the issuer. ... Always check the audience. ... Make sure tokens are used as intended. ... Dealing with expiration, issued time and clock skew.More items...
How secure is token based authentication?
Because tokens can only be gleaned from the device that produces them—whether that be a key fob or smartphone—token authorization systems are considered highly secure and effective. But despite the many advantages associated with an authentication token platform, there is always a slim chance of risk that remains.Feb 6, 2020
What is JWT cookie?
A JWT is a mechanism to verify the owner of some JSON data. It's an encoded, URL-safe string that can contain an unlimited amount of data (unlike a cookie) and is cryptographically signed. When a server receives a JWT, it can guarantee the data it contains can be trusted because it's signed by the source.Jun 17, 2021
What are disadvantages of JWT token?
Cons of Using TokensCompromised Secret Key. One of the major cons of relying on tokens is that it relies on just one key. ... Data Overhead. The overall size of a JWT is quite more than that of a normal session token, which makes it longer whenever more data is added to it. ... Shorter Lifespan.
How do I secure my API backend?
Best Practices for Securing APIsPrioritize security. ... Inventory and manage your APIs. ... Use a strong authentication and authorization solution. ... Practice the principle of least privilege. ... Encrypt traffic using TLS. ... Remove information that's not meant to be shared. ... Don't expose more data than necessary. ... Validate input.More items...•Aug 7, 2020
What is difference between OAuth and JWT?
Basically, JWT is a token format. OAuth is an standardised authorization protocol that can use JWT as a token. OAuth uses server-side and client-side storage. If you want to do real logout you must go with OAuth2.
How do I make my website API secure?
Securing your API against the attacks outlined above should be based on: Authentication – Determining the identity of an end user. In a REST API, basic authentication can be implemented using the TLS protocol, but OAuth 2 and OpenID Connect are more secure alternatives.
What if a specific token should be used only once?
What if a specific token should be used only once? Let’s imagine a scenario when a user writes a generated token to execute the DELETE method in our API. Then, e.g. after a year – when he theoretically no longer has the appropriate permissions – he tries to use it again (the so-called replay attack).
What is JWT in security?
JWT (JSON Web Token) (in)security. JWT (JSON Web Token) is a mechanism that is often used in REST APIs it can be found in popular standards, such as OpenID Connect, but we will also encounter it sometimes using OAuth2. It is used both in large companies and smaller organisations. There are many libraries available that support JWT, ...
What is JWT cryptography?
JWT / JWS / JWE / JWK, a multitude of cryptographic algorithms, two different ways of encoding (serialization), compression, the possibility of more than one signature, encryption to multiple recipients – these are just a few examples.
What is JWT in web?
JSON Web Token (JWT) is a compact, URL-safe means of representing claims to be transferred between two parties. The claims in a JWT are encoded as a JSON object that is used as the payload of a JSON Web Signature (JWS) structure or as the plaintext of a JSON Web Encryption (JWE) structure (…) Simply put, JWT is a sequence ...
What is a JWT claim?
Most often you can see JWS, and it is this structure that is popularly called JWT. In turn, “ claim ” is usually a simple pair of “key” : “value”. An example of a JWT is shown below: You can see we have here three long strings of characters separated by a dot. The structure of the whole is as follows:
What happens if JWS verification finishes on inconsistent byte?
If the signature from JWS is checked by a byte after byte with the correct signature (generated by the party which accepts JWS), and if the verification finishes on the first inconsistent byte, we may be susceptible to a time attack.
What is RSA private key?
Just a little reminder: an RSA private key is used for signatures, and a public key associated with it can verify signatures. So in this case instead of a symmetric key (as it was in HS256 algorithm), we generate a pair of RSA keys.
Structure
Its structure is composed of 3 parts: Header, Payload and Signature; They are separated by a dot (.) and each part is individually encoded in Base64Url.
Header
The header specifies the algorithm that was used to generate the JWT signature and optionally other token properties. The main types of supported cryptographic algorithms are:
Payload
The Payload is a JSON object with the claims of the treated entity, in this part, authenticated user data is usually stored when used in authentication processes.
Signature
Signature is the joining of hashes generated from Header and Payload using base64UrlEncode, with a secret key or RSA certificate.
Some of the main implementation errors
When analyzing a JWT (JSON WEB Tokens), we can forget that the information contained in it should be considered as public, since anyone who gains access to a token can easily verify the information contained in the payload.
Main Exploration Techniques JSON WEB Tokens
The none algorithm is a curious addition to JWT (JSON WEB Tokens), originally present in the Header section to express that the token does not have a signature, has now been used to exploit one of the most well-known vulnerabilities in JWT.
What can we conclude about security in JSON Web Tokens?
JSON Web Token is a secure way to transfer data between two parties, as long as it is correctly implemented and used, having its pros and cons, each type of implementation must take into account the benefits and risks of its use.
What is JWT token?
A JSON Web Token (JWT) is an open standard ( RFC 7519) that defines a way for securely transferring information between two parties. It can be used for an authentication system. As this information is digitally signed, it can be verified and trusted.
What is a header in JWT?
A header in a JWT describes the operations that are applied to the JWT like signing/de-signing technique used on it. It also contains the data about the media/content type of the information that we are sending. Then to form the first part of the JWT, this JSON is Base64Url- encoded.
What is payload in JWT?
The payload is the second part of the jwt token. This contains all the user data. This data here is also referred to as the ‘claims’ of the JWT. This information is readable by anyone so it is always better to not using any confidential information here.
Is JWT secure?
JWT is secure, but at the same time, it is less secure. For example, JWT is more vulnerable to hijacking and has to be designed to prevent hijacking. An unexpired JWT can become a security risk. In case if you are using weak encryption then the token signature might get compromised.
What is JSON Web Token?
JSON web token (JWT) is the open standard that defines a self-contained and compact way for securely transferring information between two separate entities as a JSON object. This information is secure and verified because it is digitally signed.
Installation
There is a very simple command that helps you install JSON web token >> npm install jsonwebtoken
Configuration
After you have completed the standard installation the need arrives to include the package in js file. Your file name is a variable of your choice and has no repercussions on the end product. var jwt = require (‘jsonwebtoken'); Once the jwt is changed into a jsonwebtoken variable, you can use it to secure any kind of a web token for a RESTful API
Test Run
This process has the capability to help check, if or not the request that a person gives or received is via a trustworthy and authorized source or not
Header
This is the part of the program that holds the ALGORITHM and TOKEN TYPE. Decoded Header
Payload
This is the original encrypted data that is included in the payload section Decoded Data
Verified & Decoded signature
This is the most important part of the JWT token that plays a significant part in securing the encoded token that will help it decide if the data is supposed to be accepted or reject the custom signature.
Spring Boot Based REST API
I will be securing REST API for company that I created in this blog post on REST APIs. This API also includes caching. A user will try to access /cachedemo/v1/companies/ and since APIs are protected, the user will get a response like below:
Adding User and User Registration
Since we want to add authorization for APIs, we will need to know where the user is able to log in and send credentials. These credentials will be validated, and a token will be generated. This token then will be transmitted in a request to an API call. The token will be validated in the Spring Security authorization filter that we will add.
Demo
With the all the code changes, now we are ready to create a user, login and access secured REST APIs. From the image above, a user gets Access Denied error for accessing secured APIs. To demo this, I have already registered a user with username test1 and password test@123.
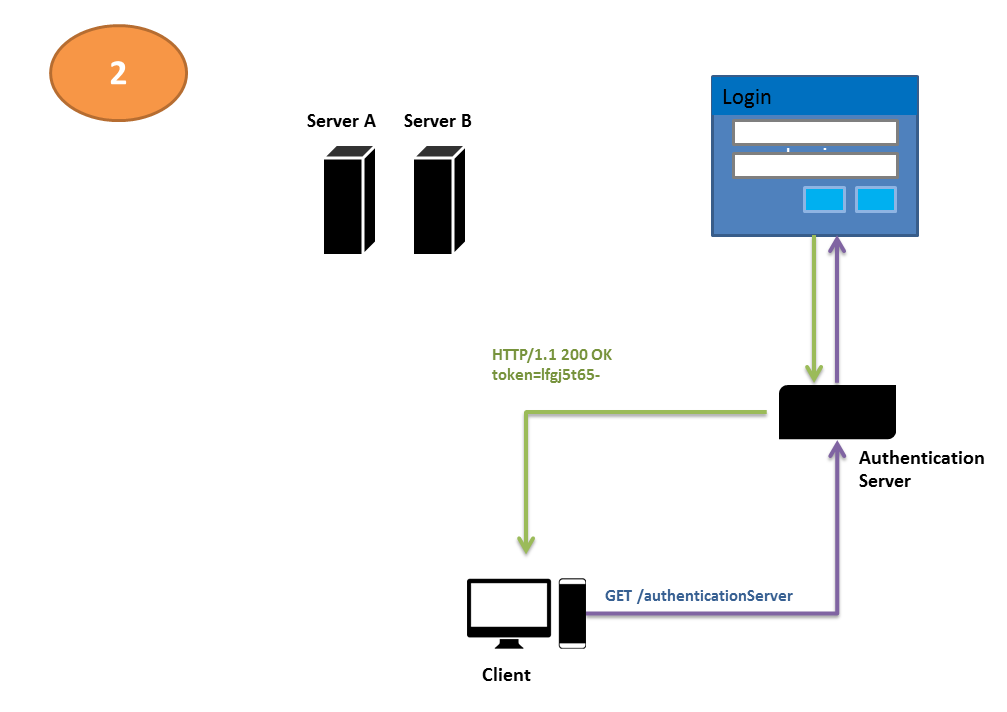
Introduction to JWT
- JSON Web Tokens (JWT) mechanisms for user authentication become more and more popular in the applications. JWT gained particular popularity with the growing famousness of the microservice architecture: it entrusts the processing authentication data to the microservices, a…
Another Example of JWT and First Security Problems
Alternative to JWT?
Useful Resources
- RFC 7519says: JSON Web Token (JWT) is a compact, URL-safe means of representing claims to be transferred between two parties. The claims in a JWT are encoded as a JSON object that is used as the payload of a JSON Web Signature (JWS) structure or as the plaintext of a JSON Web Encryption (JWE) structure (…) Simply put, JWT is a sequence of character...
Structure
- Let’s move on to our main topic – JWT security. JWTs can be sometimes used as “API keys“. En example of such a key may look like this: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpYXQiOiIxNDE2OTI5MDYxIiwianRpIjoiODAyMDU3Z…
Header
- Looking at many of the security problems I pointed out in the JWT, one might wonder if we have a proven alternative. At present, the answer is rather negative. One of the new ideas is PASETO: Paseto is everything you loveabout JOSE (JWT, JWE, JWS) without any of the many design deficits that plaguethe JOSE standards. Simply put, PASETO is to be a safe version of JWT. Will …
Payload
- 1.JSON Web Token Best Current Practices: https://tools.ietf.org/html/draft-ietf-oauth-jwt-bcp-04 2. JWT Handbook: https://auth0.com/resources/ebooks/jwt-handbook 3.Discussion on vulnerabilities of JWT: https://lobste.rs/s/r4lv76/jwt_is_bad_standard_everyone_should_avoid 4. JWT Cheat Sheet for Java (OWASP). https://www.owasp.org/index.php/JSON_Web_Token_(JW…
Signature
Some of The Main Implementation Errors
Main Exploration Techniques Json Web Tokens
What Can We Conclude About Security in Json Web Tokens?
References