
The headers are entirely encrypted. The only information going over the network 'in the clear' is related to the SSL
Transport Layer Security
Transport Layer Security (TLS) and its predecessor, Secure Sockets Layer (SSL), both of which are frequently referred to as 'SSL', are cryptographic protocols designed to provide communications security over a computer network. Several versions of the protocols are in widespread use in applications such as web browsing, email, Internet faxing, instant messaging, and voice-over-IP (VoIP).
What are HTTP security headers?
What are HTTP Security Headers? HTTP security headers are a subset of HTTP headers and are exchanged between a web client (usually a browser) and a server to specify the security-related details of HTTP communication. Some HTTP headers that are indirectly related to privacy and security can also be considered HTTP security headers.
What is the difference between HTTP headers and proprietary headers?
HTTP headers let the client and the server pass additional information with an HTTP request or response. An HTTP header consists of its case-insensitive name followed by a colon (: ), then by its value. Whitespace before the value is ignored. Custom proprietary headers have historically been used with an X- prefix,...
Why is it important to set up security headers correctly?
By setting up your security headers correctly not only you help protect your site, but your users as well. This will also help you cut down on security flaws and working hours invested in tracking and fixing them.
How to audit security headers received in a single request?
DrHEADer helps with the audit of security headers received in response to a single request or a list of requests. This is a Python based API-Security framework containing ApiSecurityHeader.py script which will check the above mentioned Security response headers are present and contains the required value.
Why does SSL on Vhosts not work?
What level of encryption is SSL?
How many reputations do you need to answer a highly active question?
Can malware take snapshots of data entering (or exiting) the SSL protocol?
Is a URL secure?
Is packet sniffing okay?
Does a proxy server know the address?
See 4 more
About this website
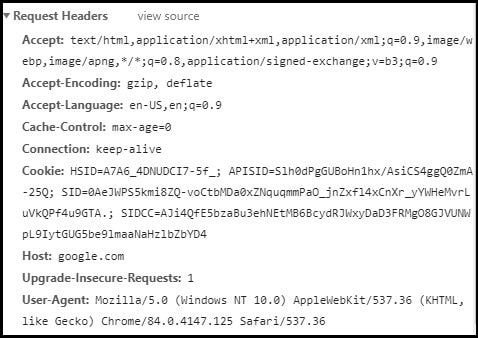
Can HTTP headers be hacked?
HTTP Host header attacks exploit vulnerable websites that handle the value of the Host header in an unsafe way. If the server implicitly trusts the Host header, and fails to validate or escape it properly, an attacker may be able to use this input to inject harmful payloads that manipulate server-side behavior.
Are HTTP headers encrypted in SSL?
HTTPS encrypts all message contents, including the HTTP headers and the request/response data.
What is HTTP header security?
HTTP security headers are a fundamental part of website security. Upon implementation, they protect you against the types of attacks that your site is most likely to come across. These headers protect against XSS, code injection, clickjacking, etc.
Can headers be sniffed?
The entire HTTP request (and response) is encrypted, including the URL. But yes, there is a way an attacker could grab the full URL: through the Referer header. If there is any external file (Javscript, CSS, etc.) which is not over HTTPS, the full URL could be sniffed in the Referer header.
Why is HTTP not secure?
Why HTTPS? The problem is that HTTP data is not encrypted, so it can be intercepted by third parties to gather data passed between the two systems. This can be addressed by using a secure version called HTTPS, where the S stands for Secure.
What HTTPS Cannot Encrypt?
What information does HTTPS not protect? While HTTPS encrypts the entire HTTP request and response, the DNS resolution and connection setup can reveal other information, such as the full domain or subdomain and the originating IP address, as shown above.
Are request headers case sensitive?
Are http headers case-insensitive? The http header names are case-insensitive. So “Content-Type” is equivalent with “content-type”.
Why do we use headers in API?
HTTP Headers are an important part of the API request and response as they represent the meta-data associated with the API request and response. Headers carry information for: Request and Response Body. Request Authorization.
How do I know if my HTTP security header is not detected?
This QID is reported when the following HTTP headers are missing X-Frame-Options, X-XSS-Protections HTTPand the X-Content-Type-Options. Please make a request for the starting URI in your web application and check its response headers are using a proxy. One or more of the above headers must be missing in the response.
Are headers encrypted?
Yes, headers are encrypted. It's written here. Everything in the HTTPS message is encrypted, including the headers, and the request/response load. Wikipedia is not the spec, which is what you should be quoting.
Does HTTP headers support authentication?
HTTP supports the use of several authentication mechanisms to control access to pages and other resources. These mechanisms are all based around the use of the 401 status code and the WWW-Authenticate response header. The client sends the user name and password as unencrypted base64 encoded text.
Are TCP headers encrypted?
The TCP header and payload are encrypted by TLS. Because encryption is performed in the protocol on one end system and decryption in the protocol of the other end system, the packet payload remains encrypted along the entire path.
Are rest headers encrypted?
Are the headers encrypted? Yes, if you are using the HTTPS (HTTP over SSL) protocol instead of plain HTTP.
How are HTTP headers encoded?
HTTP messages are encoded with ISO-8859-1 (which can be nominally considered as an enhanced ASCII version, containing umlauts, diacritic and other characters of West European languages). At the same time, the message body can use another encoding assigned in "Content-Type" header.
Are REST requests encrypted?
Since REST APIs use HTTP, encryption can be achieved by using the Transport Layer Security (TLS) protocol or its previous iteration, the Secure Sockets Layer (SSL) protocol. These protocols supply the S in “HTTPS” (“S” meaning “secure'') and are the standard for encrypting web pages and REST API communications.
Does TLS encrypt TCP header?
The TCP header and payload are encrypted by TLS. Because encryption is performed in the protocol on one end system and decryption in the protocol of the other end system, the packet payload remains encrypted along the entire path.
With HTTPS, are the URL and the request headers protected as the ...
That Depends.. If you use a packet sniffer you cannot see the data sent over the wire. The main problem with this approach is that the request url is often saved in the server's log in plain text, the browser history keeps the url, URLs are passed in Referrer headers and maybe persisted by third party services (google analytics).
ssl - Is a HTTPS query string secure? - Stack Overflow
I am creating a secure web based API that uses HTTPS; however, if I allow the users to configure it (include sending password) using a query string will this also be secure or should I force it to be
How to Read Email Message Header and Identify Encryption Used
Summary. The use of TLS, and Enforced TLS in a lot of cases now, is becoming more and more common. Cyber criminals are continually trying to intercept and read other people's emails with malicious intent.
Why does SSL on Vhosts not work?
That's why SSL on vhosts doesn't work too well - you need a dedicated IP address because the Host header is encrypted. † The Server Name Identification (SNI) standard means that the hostname may not be encrypted if you're using TLS. Also, whether you're using SNI or not, the TCP and IP headers are never encrypted.
What level of encryption is SSL?
With SSL the encryption is at the transport level, so it takes place before a request is sent.
How many reputations do you need to answer a highly active question?
Highly active question. Earn 10 reputation (not counting the association bonus) in order to answer this question. The reputation requirement helps protect this question from spam and non-answer activity.
Can malware take snapshots of data entering (or exiting) the SSL protocol?
And, malware at either end can take snapshots of data entering (or exiting) the SSL protocol - such as (bad) Javascript inside a page inside HTTPS which can surreptitiously make http (or https) calls to logging websites (since access to local harddrive is often restricted and not useful).
Is a URL secure?
Also, the URL isn't always secure: the domain, protocol, and port are visible - otherwise routers don't know where to send your requests. Also, if you've got an HTTP proxy, the proxy server knows the address, usually they don't know the full querystring. So if the data is moving, it's generally protected.
Is packet sniffing okay?
So if you're worried about packet sniffing, you're probably okay. But if you're worried about malware or someone poking through your history, bookmarks, cookies, or cache, you are not out of the water yet.
Does a proxy server know the address?
Also, if you've got an HTTP proxy, the proxy server knows the address, usually they don't know the full querystring.
What is HTTP header?
HTTP security headers are a fundamental part of website security. Upon implementation, they protect you against the types of attacks that your site is most likely to come across. These headers protect against XSS, code injection, clickjacking, etc. Let’s hash out HTTP security headers.
What is HTTP response header?
When a user visits a site through his/her browser, the server responds with HTTP Response Headers. These headers tell the browser how to behave during communication with the site. These headers mainly comprise of metadata.
What is X-Content-Type header?
The X-Content-Type header offers a countermeasure against MIME sniffing. It instructs the browser to follow the MIME types indicated in the header. Used as a feature to discover an asset’s file format, MIME sniffing can also be used to execute cross-site scripting attacks.
What happens when a site is HTTPS?
If a site is equipped with HTTPS, the server forces the browser to communicate over secure HTTPS. This way, the possibility of an HTTP connection is eliminated entirely.
What is the quote "Securing a website is like riding a bicycle"?
“Securing a website is like riding a bicycle. To keep your balance, you must keep moving.” This is what Albert Einstein’s famous bicycle quote would look like had he been a cybersecurity professional. Fortunately (or not), he wasn’t. Keeping the bicycle analogy going though, you can’t stop pedaling. The moment you do, the bicycle starts slowing down and you eventually just topple over. You don’t want that, do you?
What is content security policy?
Content Security Policy protects against Cross Site Scripting and other code injection attacks. Although it doesn’t eliminate their possibility entirely, it can sure minimize the damage. Compatibility isn’t a problem as most of the major browsers support CSP.
What Are HTTP Security Headers Exactly?
A big subset of those headers are security headers which instruct your browser exactly how to behave when it handles your website’s content and data.
Why use HTTP headers?
HTTP security headers are a great way to tighten your website’s security. There is actually no logic scenario when you shouldn’t use them. By setting up your security headers correctly not only you help protect your site, but your users as well. This will also help you cut down on security flaws and working hours invested in tracking and fixing them. Setting security headers the right way and keeping them up to date will greatly reduce the amount of risk mitigation actions needed in the future. Hopefully, this best practices will help you with that.
What is HSTS header?
The HSTS header prevents web browsers from accessing web servers over non- HTTPS connections. This helps prevent SSLstrip attacks when hackers launch a Man-in-the-Middle to redirect all traffic as unencrypted HTTP. HSTS avoids this by telling your browser that it must always use encryption.
What does X-content-type header do?
The x-content-type header prevents “ MIME sniffing ” which is really a feature in Internet Explorer and Google Chrome. It allows the browser to scan or “sniff” the content and respond away from what the header may instruct.
How long has the HyperText Transfer Protocol been around?
The HyperText Transfer Protocol had been in vogue for over 28 years now. Ever since it was implemented for making it easier for scientists to share and access data, security was always an afterthought.
Is cookie header security?
Cookie settings aren’t really security headers but can blend in well with the topic. Setting cookie options right is also critical in terms of securing your site. There are three different cookie options that you should know about – Secure, HttpOnly and SameSite.
Is HTTP headers good?
Tweet this: Website security: HTTP security headers are a good place to start. There’s a myriad of aspects to consider when looking to secure a site, and HTTP headers are a good place to start. Most of them aren’t all that complicated to implement. Keeping up with HTTP security headers best practices provides another security layer on top ...
What is a header in a request?
Headers can be grouped according to their contexts: Request headers contain more information about the resource to be fetched, or about the client requesting the resource. Response headers hold additional information about the response, like its location or about the server providing it.
What is HTTP header?
HTTP headers let the client and the server pass additional information with an HTTP request or response. An HTTP header consists of its case-insensitive name followed by a colon (: ), then by its value. Whitespace before the value is ignored.
What is a client hints?
HTTP Client hints are a set of request headers that provide useful information about the client such as device type and network conditions, and allow servers to optimize what is served for those conditions .
How to express push policy?
A client can express the desired push policy for a request by sending an Accept-Push-Policy header field in the request.
What is a fetch metadata request header?
Fetch metadata request headers provides information about the context from which the request originated. This allows a server to make decisions about whether a request should be allowed based on where the request came from and how the resource will be used.
What is the header field in a signature?
The Signature header field conveys a list of signatures for an exchange, each one accompanied by information about how to determine the authority of and refresh that signature.
What does HTTPS mean in HTTPS?
Identifies the original host requested that a client used to connect to your proxy or load balancer. Identifies the protocol (HTTP or HTTPS) that a client used to connect to your proxy or load balancer. Added by proxies, both forward and reverse proxies, and can appear in the request headers and the response headers.
What is a header response?
A 'Content Security Policy' header response prevents a wide array of attacks such as code injection, and XSS attacks. Unfortunately, it's also one of the most difficult policies to implement and has the greatest potential to break the appearance of your site if implemented incorrectly. In short, there is no easy way to implement this policy into your htaccess file without extensive testing.
What is strict transport security header?
The strict transport security security header forces the web browser to ensure all communication is sent via a secure https connection. If your site is serving mixed content then implementing this will break your site. Ensure that all URLs are being served as https before adding this to your .htaccess file.
What is XSS header?
By implementing the 'X XSS Protection header' you can prevent a degree of 'cross site scripting' (XSS) attacks. It's another easy security header to implement and is widely utilised by all of the huge sites such as Github, Facebook and Google.
What is content security policy?
The 'Content Security Policy' controls what host URLs (domain names) are allowed to interact with your site. Therefore, every 3rd party URL that exists within your sites plug-ins or extensions needs to be added to your Content Security Policy and then have the appropriate rules applied against them.
What is htaccess policy?
This policy prevents any Adobe resources on your site like PDF's and Flash being abused. By adding the below htaccess snippet you'll prevent hotlinking and stop resource abuse from other sites that try to load your site's assets.
Does a wildcard detect a security policy?
This tool only detects the presence of a security policy in the header response. It doesn't validate any policies for best practices. Therefore, even if you have a 'Content Security Policy' with a wildcard, it will still pass as having detected a valid 'Content Security Policy'.
Can analytics use https?
For example, analytics can introduce 5 different external URLs on your site which you can't easily see in the source code. It's still possible to introduce a very rudimentary 'Content Security Policy' by using the below code which simply enforces that all external URLs use the https protocol.
What is referer header?
The Referer (sic) header contains the address of a request ( for example, the address of the previous web page from which a link to the currently requested page was followed, or the address of a page loading an image or other resource). This has many fairly innocent uses, including analytics, logging, or optimized caching. However, there are more problematic uses such as tracking or stealing information, or even just side effects such as inadvertently leaking sensitive information.
What is referrer policy?
The Referrer-Policy header on your server to control what information is sent through the Referer header. For example, a directive of no-referrer would omit the Referer header entirely.
Can an image from a third party site be leaked?
By the same logic, an image from a third party site embedded in your page could result in sensitive information being leaked to the third party. Even if security is not compromised, the information may not be something the user wants shared.
Does HTTPS transmit referrer information?
This has many security advantages, including the fact that HTTPS sites will never transmit referrer information to non-HTTPS sites. This advice is less relevant now that most of the web is using HTTPS, but it is still a worthy consideration.
What is HTTP header?
A big part of these headers is the security HTTP headers, which are responsible for the behavior of your website.
Why do we need different headers?
Your web server security is crucial, and to improve it, you must configure different HTTP headers to make sure that your web-server is more secure from various types of attacks . Without these important headers, your website would be at risk and the attacker may compromise it.
What is HTTP strict transport security?
HTTP strict transport security is one of the HTTP security headers which comes into action here, it forces your website to be redirected from HTTP to HTTPS so that your fear of getting attacked by some hacker is eliminated, but if the problem remains there and your user is still accessing through HTTP, then it is easy for the hacker present on the same network to intercept your insecure connection, and your risk of getting attacked is increased.
What does the set cookie header mean?
The Set-cookie header confirms that your cookies are encrypted via HTTPS. If these cookies are not encrypted, then it could be dangerous for the user as many attacks like MiTM (Man-in-the-middle) attack can be performed by a hacker to steal your cookies.
What does XSS protection:0 mean?
X-XSS Protection:0 – When the value is set to 0, the XSS filter will be automatically disabled.
What is allow from URI in X-frame?
X-Frame-Options: allow-from URI – This option is used to allow the frame element for a specific URL address of any website.
What is content security policy?
Content Security Policy protects from various Cross-Site-Scripting (XSS) attacks that can severely harm your website. When you are using Content Security Policy, you are restricting your website from loading different scripts defined in the policy only such as scripts, CSS, images, etc.
Why does SSL on Vhosts not work?
That's why SSL on vhosts doesn't work too well - you need a dedicated IP address because the Host header is encrypted. † The Server Name Identification (SNI) standard means that the hostname may not be encrypted if you're using TLS. Also, whether you're using SNI or not, the TCP and IP headers are never encrypted.
What level of encryption is SSL?
With SSL the encryption is at the transport level, so it takes place before a request is sent.
How many reputations do you need to answer a highly active question?
Highly active question. Earn 10 reputation (not counting the association bonus) in order to answer this question. The reputation requirement helps protect this question from spam and non-answer activity.
Can malware take snapshots of data entering (or exiting) the SSL protocol?
And, malware at either end can take snapshots of data entering (or exiting) the SSL protocol - such as (bad) Javascript inside a page inside HTTPS which can surreptitiously make http (or https) calls to logging websites (since access to local harddrive is often restricted and not useful).
Is a URL secure?
Also, the URL isn't always secure: the domain, protocol, and port are visible - otherwise routers don't know where to send your requests. Also, if you've got an HTTP proxy, the proxy server knows the address, usually they don't know the full querystring. So if the data is moving, it's generally protected.
Is packet sniffing okay?
So if you're worried about packet sniffing, you're probably okay. But if you're worried about malware or someone poking through your history, bookmarks, cookies, or cache, you are not out of the water yet.
Does a proxy server know the address?
Also, if you've got an HTTP proxy, the proxy server knows the address, usually they don't know the full querystring.
