By default, encryption is not enabled for S3 buckets, but a user can easily enable them and also choose the encryption method himself. AWS ensures that encryption has minimal effect on the latency of S3 buckets. In encryption, the data is translated to some other unreadable form using mathematical techniques and algorithms.
What does encryption do on S3?
When using SSE-S3, the encryption of an object uploaded to S3 happens as follows:
- The client uploads an object to S3.
- S3 generates a data key.
- S3 encrypts the object with the data key.
- S3 encrypts the data key with its master key.
- S3 saves the encrypted object & data key to disk.
- S3 destroys the plaintext data key from memory.
How do I Secure my Amazon S3 buckets?
Restrict access to your S3 buckets or objects by:
- Writing AWS Identity and Access Management (IAM) user policies that specify the users that can access specific buckets and objects. ...
- Writing bucket policies that define access to specific buckets and objects. ...
- Using Amazon S3 Block Public Access as a centralized way to limit public access. ...
- Setting access control lists (ACLs) on your buckets and objects. ...
How to configure encryption for Amazon S3?
For instructions, see Grant Amazon S3 Permission to Encrypt Using Your AWS KMS CMK .
- AWS managed key (aws/s3)
- Choose from your KMS master keys, and choose your KMS master key .
- Enter KMS master key ARN, and enter your AWS KMS key ARN.
How to encrypt S3 bucket using terraform?
- SSE-S3 requires that Amazon S3 manage the data and master encryption keys.
- SSE-C requires that you manage the encryption key.
- SSE-KMS requires that AWS manage the data key but you manage the master key in AWS KMS.
Are S3 buckets automatically encrypted?
For more information, see Reducing the cost of SSE-KMS with Amazon S3 Bucket Keys. Default encryption works with all existing and new Amazon S3 buckets. Without default encryption, to encrypt all objects stored in a bucket, you must include encryption information with every object storage request.
Is AWS S3 data encrypted by default?
Amazon provides several encryption types for data stored in Amazon S3. Is S3 encrypted? By default, data stored in an S3 bucket is not encrypted, but you can configure the AWS S3 encryption settings.
How do I know if my S3 bucket is encrypted?
03 Click on the name (link) of the S3 bucket that you want to examine to access the bucket configuration settings. 04 Select the Properties tab from the console menu to access the bucket properties. 05 In the Default encryption section, check the Default encryption feature status.
Does AWS encrypt data by default?
Additionally, Amazon EC2 and Amazon S3 support the enforcement of encryption by setting default encryption. You can use AWS Managed Config Rules to check automatically that you are using encryption, for example, for EBS volumes, RDS instances, and S3 buckets.
Are uploads to S3 encrypted?
Server-side encryption is data encryption at rest—that is, Amazon S3 encrypts your data as it uploads it and decrypts it for you when you access it. When you load tables using a COPY command, there is no difference in the way you load from server-side encrypted or unencrypted objects on Amazon S3.
How does S3 bucket encryption work?
S3 encrypts the object with plaintext data key and deletes the key from memory. The encrypted object along with the encrypted data key is then stored in S3. While retrieving the object S3 sends the encrypted data key to KMS.
Is EFS encrypted by default?
EFS is available in all versions of Windows except the home versions (see Supported operating systems below) from Windows 2000 onwards. By default, no files are encrypted, but encryption can be enabled by users on a per-file, per-directory, or per-drive basis.
How do I encrypt an existing S3 bucket?
Option 1Sign into the AWS Management Console.Navigate to the S3 console and find the bucket and object that was flagged as unencrypted.Select the object and choose Properties then Encryption.Use the wizard to choose the S3 encryption options you prefer.Save to apply encryption to the object.
What type of encryption does S3 use?
AES-256Amazon S3 server-side encryption uses one of the strongest block ciphers available, 256-bit Advanced Encryption Standard (AES-256) GCM, to encrypt your data.
Does AWS automatically encrypt data in transit?
Encryption in transit. All data flowing across AWS Regions over the AWS global network is automatically encrypted at the physical layer before it leaves AWS secured facilities. All traffic between AZs is encrypted.
What encryption does S3 use?
Amazon S3 uses AES-256 bit encryption to encrypt the data with the customer provided key and removes the key from its memory post completion of the encryption process whereas, in the decryption process, it first verifies and matches if the same key is provided (which was provided during the encryption) and then ...
Is EFS encrypted by default?
EFS is available in all versions of Windows except the home versions (see Supported operating systems below) from Windows 2000 onwards. By default, no files are encrypted, but encryption can be enabled by users on a per-file, per-directory, or per-drive basis.
What is Data Encryption?
Data encryption is the process of converting raw data into a coded form to help ensure that only authorized parties can read it. Data encryption pr...
How to Set Up Amazon S3 Encryption?
Encrypting an object will start by logging into the AWS Console.Both objects are unencrypted, and you can see that under Properties, the informatio...
How to Encrypt an Amazon S3 Bucket?
1. To encrypt a bucket, begin by clicking on the Properties tab, one tab over from the Overview tab2. In the Properties tab, select “Default encryp...
How to encrypt a bucket in Excel?
To encrypt a bucket, begin by clicking on the Properties tab, one tab over from the Overview tab: 2. In the Properties tab, select “Default encryption” and choose your preferred encryption option: 3. When you click “Save,” the entire bucket will now be encrypted.
What is S3 client side encryption?
S3 Client-Side Encryption puts all the responsibility for the encryption heavy lifting onto the user. Rather than allowing AWS to encrypt your data, you perform the encryption within your own data center and upload the encrypted data directly to AWS.
What is SSE S3?
With SSE-S3, you don’t have access to see or encrypt data using the key directly, but you can be assured that the raw data you own is encrypted at rest by AWS’s standard processes.
How to encrypt an object in Java?
To encrypt object1, click on Actions, and then select “Change Encryption” from the drop-down menu: 3. You then get another pop-up message that asks you what kind of encryption you want to set on the object: 4. In this case we want to use S3 server-side en cryption, so choose the “AES-256” option and hit “Save.”.
What is AWS S3 Inventory?
AWS S3 Inventory. The first option is AWS S3 Inventory, part of the AWS Inventory toolset. This allows you to set up reports on your S3 objects. Unfortunately, this requires some setup on your part to get going, and only works at the bucket level.
What is data encryption?
Data encryption protects your stored data against theft, ransomware attacks, and other security risks. If an attacker gets access or hold of your data, then they won’t be able to do anything with it unless they also get a hold of the key to unencrypt it.
Is object2 encrypted?
Even though your bucket is now automatically encrypting all objects that are uploaded to it, objects that existed before encryption was enabled are still unencrypted. In this scenario, object2 is still not encrypted.
Using encryption for cross-account operations
Be aware of the following when using encryption for cross-account operations:
Using default encryption with replication
When you enable default encryption for a replication destination bucket, the following encryption behavior applies:
Using Amazon S3 Bucket Keys with default encryption
When you configure your bucket to use default encryption for SSE-KMS on new objects, you can also configure S3 Bucket Keys. S3 Bucket Keys decrease the number of transactions from Amazon S3 to AWS KMS to reduce the cost of server-side encryption using AWS Key Management Service (SSE-KMS).
How Torq automates AWS S3 bucket encryption
With Torq’s no-code automation, this process can be automated — ensuring your S3 data at rest is protected at all times.
Get the workflow template
Already a Torq customer? You can find this workflow (Encrypt S3 Bucket in Response to Alert) and dozens more in Torq’s Workflow Library. Just add it to your Torq account, provide your CSPM and AWS credentials, create a CSPM policy to generate a webhook for Torq when an unencrypted bucket is found and enjoy better protection of your S3 data.
Get Started Today
Not using Torq yet? Get in touch for a trial account and see how Torq’s no-code automation accelerates security operations to deliver unparalleled protection.
Unencrypted AWS S3 Buckets
Ensure that encryption is enabled at the bucket level to automatically encrypt all objects when stored in Amazon S3. The S3 objects are encrypted during the upload process using Server-Side Encryption with either AWS S3-managed keys (SSE-S3) or AWS KMS-managed keys (SSE-KMS).
Audit
To determine if your Amazon S3 buckets have Default Encryption feature enabled, perform the following:
Still Need Help?
Come see why we are the #1 cloud management platform and why companies like Uber, Dickey’s BBQ Pit and Norwegian Cruise Line trust nOps to manage their cloud.
Section 1: Replicating new objects between S3 buckets
S3 Replication enables automatic, asynchronous copying of objects across Amazon S3 buckets. Buckets configured for object replication can be owned by the same or different AWS accounts and can be in the same or different AWS Regions.
Section 2: Replicating existing objects between S3 buckets
If your bucket has new and existing data to be replicated, it’s best to configure existing object replication. You can enable existing object replication by contacting AWS Support.
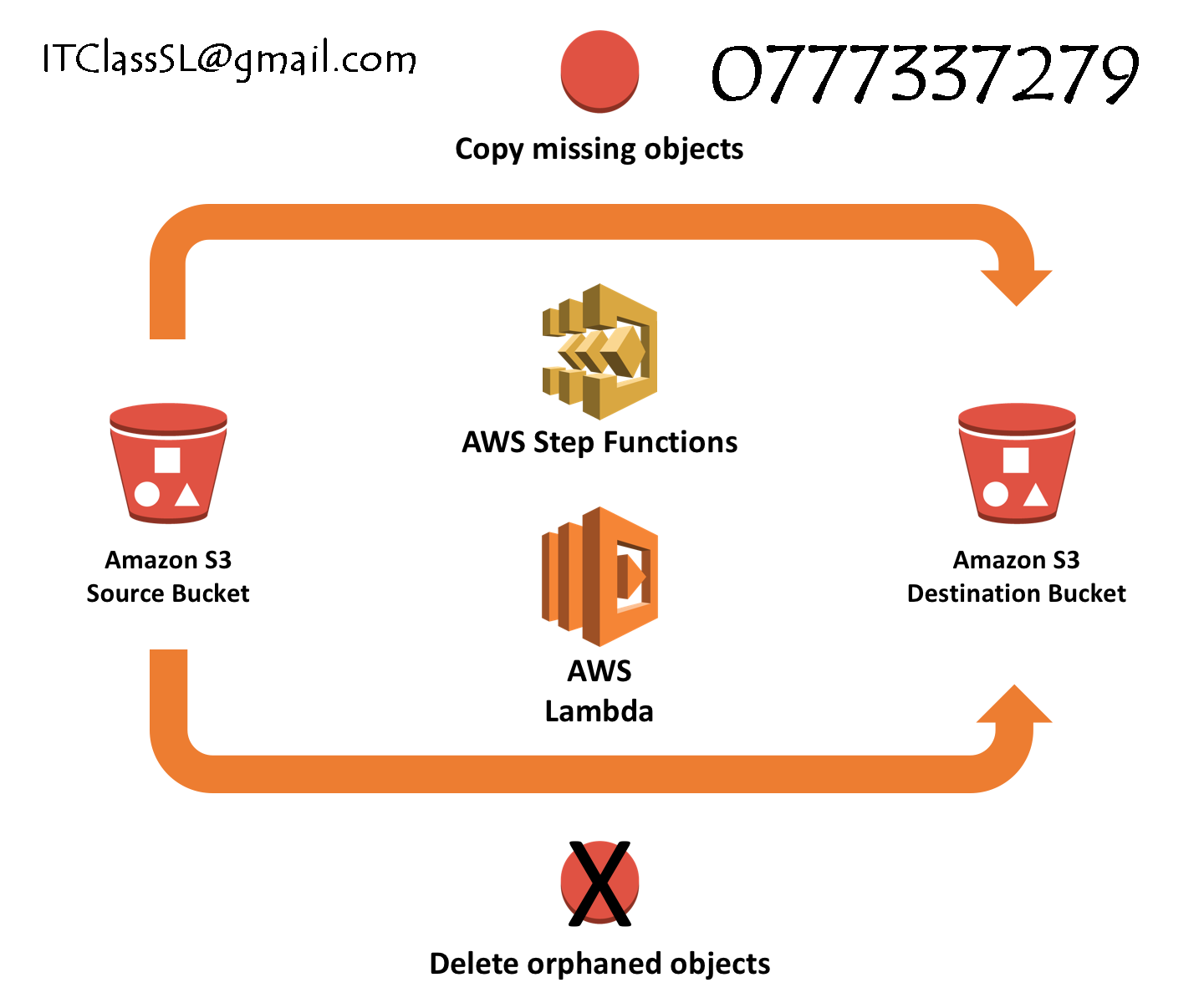
Section 3: Compare and copy objects between S3 buckets
If your bucket has objects that have previously been replicated, or failed, and that need to be copied to the destination bucket, you will first want to identify the objects that need to be copied.
Copy objects using S3DistCp
If your bucket has a number of objects larger than 5 GB, we recommend you to use S3DistCp to perform the copy operation. To run S3DistCp, you will need to launch an Amazon EMR cluster and execute S3DistCp from a Primary node.
Other considerations to keep in mind
If you want to sync your delete markers between source and destination buckets, you can easily enable or disable the replication of delete markers between source and destination buckets for each replication rule.
Cleaning up
To avoid incurring additional cost, you may consider deleting the respective resources created in your AWS account for services used for this migration. For example, the S3 inventory job and reports generated, S3 Batch Operations jobs, EMR clusters for S3DistCp, Athena tables and related S3 bucket/objects.
Conclusion
In this post, we’ve shown you how to use a combination of S3 Replication, S3 Inventory, S3 Batch Operations, and S3DistCp to synchronize bucket contents.