Is ADFS using SAML?
ADFS uses a claim based access control authorization. This method involves authenticating users via cookies and Security Assertion Markup Language, also known as SAML. It means ADFS is a type of Security Token Service or STS.
What authentication does ADFS use?
claim-based authenticationADFS uses a claim-based authentication, which verifies a user from a set of “claims” about their identity from a trusted token. ADFS then gives users a single prompt for SSO, allowing them to access multiple applications and systems even if they reside on different networks.
How do I set up ADFS SAML?
Here's how you can configure ADFS SAML SSO for your users.Step 1: On your ADFS Server, Open up AD FS Management.Step 2: Right click on Relying Party Trusts and select Add Relying Party Trust. ... Step 3: In the Select Data Source step, choose Enter data about the relying party manually.More items...•
Does ADFS support SSO?
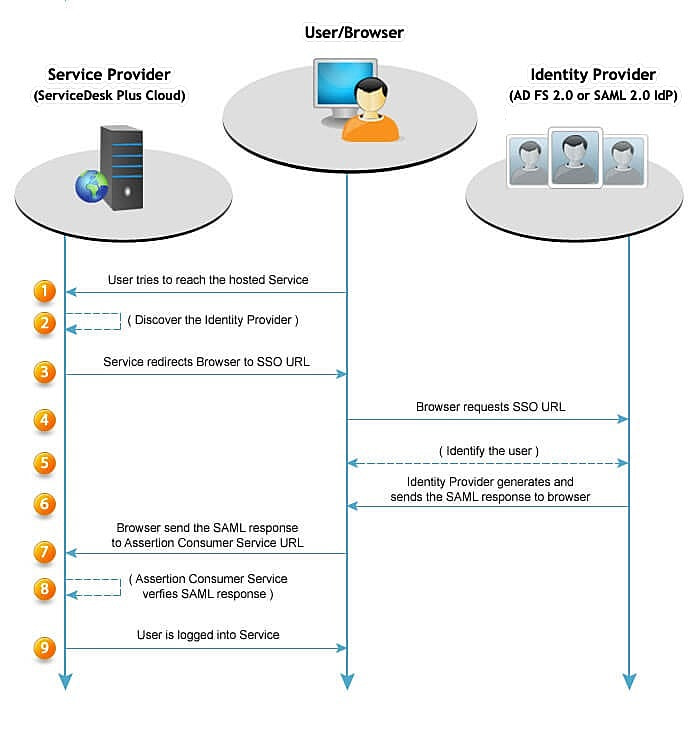
Note: SSO is available with the Basic, Plus and Premium subscription plans. You need an ADFS 2.0 identity provider (IdP) to handle the sign-in process and provide your users' credentials to TalentLMS.
Does ADFS use OAuth?
ADFS issues access tokens and refresh tokens in the JWT (JSON Web Token) format in response to successful authorization requests using the OAuth protocol. ADFS does not issue SAML tokens over the OAuth authorization protocol inherently, but can be allowed using SecureW2.
Is ADFS the same as SSO?
ADFS provides Web SSO to federated partners, which enables Requesting Parties' users to have an SSO experience to access their web-based applications/systems. ADFS does not extend the schema for Active Directory to create additional custom attributes in AD for the sole purpose of using them as claims.
Is SAML SSO or federation?
SAML (Security Assertion Markup Language) is a protocol that you can use to perform federated single sign-on from identity providers to service providers. In federated single sign-on, users authenticate at identity provider. Service providers consume the identity information asserted by identity providers.
How does ADFS implement SSO?
Log in to the server where ADFS is installed. Launch the ADFS Management application (Start > Administrative Tools > ADFS Management) and select the Trust Relationships > Relying Party Trusts node. Click Add Relying Party Trust from the Actions sidebar. Click Start on the Add Relying Party Trust wizard.
Does Active Directory use SAML?
In Windows Active Directory (AD) environments, SAML SSO can allow employees to access a wide range of applications using only their AD credentials. On-premises AD users can continue to use a centralized identity source (AD) for access to cloud apps like Microsoft 365.
How does SAML work with Active Directory?
SAML works by passing information about users, logins, and attributes between the identity provider and service providers. Each user logs in once to Single Sign On with the identify provider, and then the identify provider can pass SAML attributes to the service provider when the user attempts to access those services.
What replaces ADFS?
Azure Active Directory (Azure AD) offers a universal identity platform that provides your people, partners, and customers a single identity to access applications and collaborate from any platform and device. Azure AD has a full suite of identity management capabilities.
What is difference between AD and ADFS?
Since AD stores information of all users ( user IDs and passwords), it acts as the base identity store. ADFS uses all of this identity information in Active Directory and makes it available outside your network. This information can be used by other organizations and applications.
Does ADFS use JWT?
Security Tokens Modern authentication uses following token types: id_token: A JWT token issued by authorization server (AD FS) and consumed by the client. Claims in the ID token will contain information about the user so that client can use that.
Does ADFS use Kerberos?
Integrated Windows Authentication (IWA) authenticates users to Active Directory Federation Services (ADFS) using the Kerberos token that is issued when a user logs in to a Windows workstation. This is also known as SPNEGO authentication.
Is ADFS same as LDAP?
Whereas ADFS is focused on Windows environments, LDAP is more flexible. It can accommodate other types of computing including Linux/Unix. LDAP is ideal for situations where you need to access data frequently but only add or modify it now and then.
What is ADFS pass through authentication?
Pass-through authentication (PTA) is a feature of Azure AD Connect. It involves a simple service in the form of an agent running on one or several on-premises domain-joined servers, which validates a user's sign-on on behalf of Azure AD directly with the on-premises Active Directory (AD).
How to add SAML to Atlassian?
Go to admin.atlassian.com, select your organization, and navigate to Security > SAML single sign-on. Click Add SAML configuration to open this screen.
How to copy a certificate to a file?
From the Certificate dialog, switch to the Details tab and click Copy to File.
What is SAML in Confluence?
Security Assertion Markup Language (SAML) is an open standard for exchanging authentication and authorization data between an identity provider and a service (such as Confluence Cloud).
What does it mean to verify a domain?
Verify one or more domains, to confirm you own those – see Verify a domain for your organization . When you verify a domain, all the Atlassian accounts that use email addresses from the verified domain become managed by your organization.
Can you remove admin access to SAML?
You can remove admin access when you are satisfied that SAML single sign-on is working as expected. Because users won't be able to log in to your Atlassian products during the time it takes to configure SAML single sign-on, schedule a day and time for the changeover to SAML and alert your users in advance.
What is the name of the site you land on if your configuration was successful?
If your configuration was successful, you land on start.atlassian.com.
Does Atlassian use HTTPS?
Check that your Atlassian products and AD FS use the HTTPS protocol to communicate with each other, and that the configured product base URL is the HTTPS one.
Why does any of this matter?
Because after you stand-up ADFS, people will start knocking on your door telling you how they want to federate with some cloud-based application and one of your first questions to them should be:
What does response_type mean in ADFS?
response_type: tells that ADFS server that I want to perform OAuth and get an authorization code in return.
What is my token type that ADFS gives me to send back to the original application?
And lastly, after typing in my credentials, what is my token type that ADFS gives me to send back to the original application: When the WS-Fed sign-in protocol is used, ADFS will always issue a SAML 1.1 token back to your browser, which you then automatically POST back to the application.
Why do we call scenarios the flow?
It’s because the sign-in protocol will dictate the overall “Flow” of the scenario – How we should interact with the ADFS server, what parameters it requires, what exactly we are expecting in return.
What type of token is used for OAuth?
Summary: Now, that was pretty technical, but what does it highlight? We used the OAuth sign-in protocol, forms-based authentication was our authentication protocol, and our token type was JSON Web Token (JWT)
What is an authorization code in ADFS?
Once I authenticate, the ADFS server responds with an authorization code. BTW, this is a one-time use code. You’ll never see this code, but the application will store this to later get an access token, which it can then use to get the necessary user data the application requires.
What is WS-fed in ADFS?
WS-Fed is a sign-in protocol, which in plain English means that when the application you’re trying to gain access to redirects you to the ADFS server, it has to be done in specific way (WS-Fed) for the process to continue. Let’s give some easy examples in line with my example above.
What attribute does Shibboleth SP use?
Usually Shibboleth SP uses SAML attribute such as "mail" attribute (e.g., [email protected]) to log the user in to your website.
What happens after Shibboleth SP saves?
After Shibboleth SP save the value, automatically jumps to the interface accessed in the browser.
Where does Shibboleth SP save the value?
Shibboleth SP save the value belongs of SAML response which is getting from SAML Idp (this time is ADFS) to three places (※), and we can see it in https://SP 's domaim name/Shibboleth.sso/Session
What is the category of IIS and Tomcat?
Microsoft IIS and Apache Tomcat belong to "Web Servers" category of the tech stack.
Can you use SAML SP in Java?
You can use OneLogin Java SAML SP tookit ( Code Your Java App to Provide SSO via OneLogin) to build SAML SP for your Java-based GlassFish web application.
What is the meaning of "back up"?
Making statements based on opinion; back them up with references or personal experience.
Can you redirect a user to a Glassfish application?
From the cybersecurity perspective, you can NOT redirect the user info to establish the HTTP login session for Glassfish application. Otherwise, hackers can use the same user info to log in to Glassfish application without any authentication such as local username/password authentication or third-party SAML authentication.

Prerequisites
- 1.Using the AD FS Management tool, go to Service > Claim Descriptions.
2.Select Add Claim Description. - 3.Specify the claim:
•Display name: Persistent Identifier
Create a self-signed certificate
Create a policy key
Add a claims provider
Add a user journey
Add the identity provider to a user journey
Configure the relying party policy
Configure an AD FS relying party trust
Test your custom policy
Troubleshooting AD FS service