Creating a firewall ingress rule
- 1.Firstly, check current port settings to determine what ports the statd and nlockmgr daemons use on the client.
- 2.Then, go to the Firewall page in Google Cloud Console.
- 3.Next, click Create firewall rule.
- 4.Enter a Name for the firewall rule. ...
- 5.Specify the Network in which you want to implement the firewall rule.
- 6.Specify the Priority of the rule. ...
- 7.Next, choose Ingress for Direction of traffic.
- Go to the Firewall page in the Google Cloud console. ...
- Click Create firewall rule.
- Enter a Name for the firewall rule. ...
- Specify the Network in which you want to implement the firewall rule.
- Specify the Priority of the rule. ...
- Choose Egress for Direction of traffic.
How do you name a firewall rule?
Most modern firewalls support complex names with spaces, periods, underscores, etc....Things you should document in the comments field include:Date and time rule was created.Original author of rule.Description or rationale for rule.
How do I add a firewall rule?
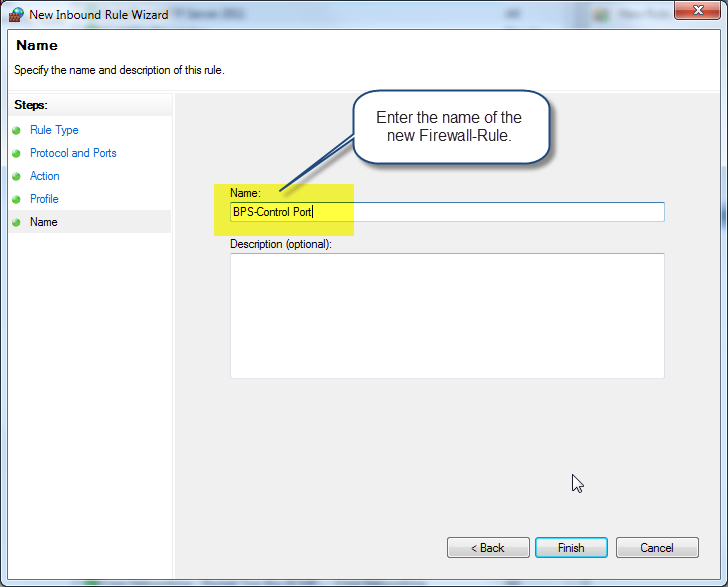
To create an inbound port rule Open the Group Policy Management Console to Windows Defender Firewall with Advanced Security. In the navigation pane, click Inbound Rules. Click Action, and then click New rule. On the Rule Type page of the New Inbound Rule Wizard, click Custom, and then click Next.
How do I enable firewall rule by network tag?
Create a firewall rule that allows traffic on HTTP (tcp/80) to any address and add network tag on juice-shop. In this step, you have to create a firewall rule that allows traffic on HTTP (tcp/80) to any address. In the GCP Console go to Navigation Menu >VPC Network > Firewall. Click Create firewall rule.
What is firewall rule in GCP?
Firewall rules in Google Cloud. When you create a VPC firewall rule, you specify a VPC network and a set of components that define what the rule does. The components enable you to target certain types of traffic, based on the traffic's protocol, destination ports, sources, and destinations.
How do I check firewall rules in GCP?
Controller Firewall RulesFrom the GCP console, navigate to VPC network > Firewall rules.In the Create a firewall rule screen, select Ingress as the Direction of traffic and Allow as the Action on match, as shown below:More items...
How do I set outgoing firewall rules?
Open the Group Policy Management Console to Windows Defender Firewall with Advanced Security. In the navigation pane, click Outbound Rules. Click Action, and then click New rule. On the Rule Type page of the New Outbound Rule wizard, click Custom, and then click Next.
How do I add a network tag in GCP?
Add tags to an existing VMGo to the VM instances page. Go to the VM instances page.Click an instance name.On the VM instance details page, click Edit.In the Network tags section, specify one or more tags, separated by commas.Click Save.
Does GCP have firewall?
Cloud Firewall's fully distributed, stateful inspection firewall engine is built natively into our software defined networking fabric, and enforced at each workload.
How do you add tags to GCP?
To create a tag key, do the following:Open the Tags page in the Google Cloud console. ... Select the Project picker at the top of the page.From the Organization picker, select your organization.Click add Create tag.In the Tag name box, enter the display name of your tag key.More items...
How do I enable ports in GCP?
You need to:Go to cloud.google.com.Go to my Console.Choose your Project.Choose Networking > VPC network.Choose "Firewall"Choose "Create Firewall Rule"To apply the rule to select VM instances, select Targets > "Specified target tags", and enter into "Target tags" the name of the tag.More items...•
How do I enable ports in GCP instance?
Opening Ports with Firewall Rules From the Compute Engine console, click “View Network Details” on the instance. Click on “Firewall Rules” in the sidebar. Create a new firewall rule. Give it a name, and choose whether you want to allow or deny traffic.
What is the default rule used in firewall?
The Firewall Filtering policy has one default rule, which handles all the traffic that does not match any user-defined rule with a higher rule order. The default rule always maintains the lowest precedence and cannot be deleted.
How do I add firewall rules to iptables?
You can add new rules to a specific position of the list by inserting them using iptables -I
How do I create a firewall rule in PowerShell?
How to Create, Edit or Remove Windows Firewall Rules with PowerShell?New-NetFirewallRule.Copy-NetFirewallRule.Disable-NetFirewallRule.Enable-NetFirewallRule.Get-NetFirewallRule.Remove-NetFirewallRule.Rename-NetFirewallRule.Set-NetFirewallRule.More items...•
How do I add a firewall in Windows 10?
Go to Start and open Control Panel. Select System and Security > Windows Defender Firewall. Choose Turn Windows Firewall on or off. Select Turn on Windows Firewall for domain, private, and public network settings.
How do I add an iptables rule?
To append a new rule to the end of a chain, your iptables command will have to use the -A. If you want to append the rule in another position, you have to use the -I option. This option enables you to specify the exact location of the rule.
How to configuring Firewall Rules in GCP?
By creating a firewall rule, you specify a Virtual Private Cloud (VPC) network and a set of components that define what rule does .
What is GCP firewall?
Google Cloud Platform (GCP) firewall rules let you allow or deny traffic to and from your virtual machine (VM) instances based on a configuration you specify.
What ports does a VPC use?
If the VPC network has a firewall egress rule that blocks traffic to TCP ports 111, 2046, 2049, 2050, or 4045, and targets the IP address ranges used by your Filestore instances.
Why do we need a firewall ingress rule?
First and foremost, we need to create a firewall ingress rule to enable traffic from Filestore instances to your clients in following conditions.
Where to find reserved IP address range?
You can get the reserved IP address range for any Filestore instance from the Filestore instances page or by running gcloud filestore instances describe.
How to show firewall rules in Google Cloud?
To show firewall rules in a particular network: Go to the VPC networks page in the Google Cloud Console. Go to the VPC networks page. Click the Name of a VPC network to go to its details page. On the details page for the network, click the Firewall rules tab.
What is firewall rule?
Creating firewall rules. Firewall rules are defined at the network level, and only apply to the network where they are created; however, the name you choose for each of them must be unique to the project. A firewall rule can contain either IPv4 or IPv6 ranges, but not both.
What does firewall insights do?
If you enable Firewall Rules Logging , Firewall Insights can provide insights about your firewall rules to help you better understand and safely optimize their configurations. For example, you can view which allow rules haven't been used in the last six weeks. For more information, see Using the Firewall rules details screen in the Firewall Insights documentation.
How to tell if a rule is disabled in GCloud?
In the gcloud command-line tool output, look for the disabled field. If it says disabled:false, the rule is enabled and being enforced. If it says disabled: true, the rule is disabled.
How to limit source tags?
To limit source by network tag, choose Source tags, then type the network tags in to the Source tags field. For the limit on the number of source tags, see VPC Quotas and Limits. Filtering by source tag is only available if the target is not specified by service account.
What is project_id in firewall?
PROJECT_ID is the ID of the project where the firewall rule is located.
How do firewall rules work?
Firewall rules are associated and applied to a VM instances through a rule's target parameter. By viewing all of the applied rules, you can check whether a particular rule is being applied to an interface.
What is GCP firewall?
GCP firewalls are VM-centric. Unlike traditional firewall devices, which are applied at the network edge, GCP firewall rules are implemented at VM level. This means the firewall rules can exist between your instances and other networks, and also between individual instances within the same VPC.
What is firewall rule?
Firewall rules are customizable software-defined networking constructs that let you allow or deny traffic to and from your virtual machine (VM) instances. To secure applications and respond to modern threats, firewall rules require monitoring and adjustment over time. GCP Firewall Rules Logging, which Google Cloud made generally available in ...
Why are there hundreds of firewall rules?
It’s not unusual for large enterprises to have hundreds of firewall rules due to the scale of the infrastructure and the complexity of network traffic patterns.With so much going on, it’s understandable, that application teams sometimes mislabel the VMs when they migrate them from on-prem to cloud and scale-up applications after migration. The consequences of mislabeling range from an application outage to a security breach. The same problem can also arise if we (mis)use service accounts.
How many source/target tags per firewall rule?
The maximum number of source/target tags per firewall rule is 30/70, and the maximum number of source/target per service account is 10/10. A firewall rule can use network tags or service accounts, but not both. As mentioned, the complexity of the firewall rules also matters.
What is firewall rules logging?
With Firewall Rules Logging, we can refine our firewall rules by following a few best-practices and identify undesired network traffic in near real-time. In addition to firewall rules logging, we’re always working on more tools and features to make managing firewall rules and network security in general easier.
What are the two immutable firewall rules?
Every VM has two immutable implied firewall rules: implied allow of egress, and implied deny of ingress at lowest priority. However, Firewall Rule Logging does not generate any entries for these implied firewall rules.
How to conserve network space?
Conserve network space by planning proper CIDR blocks (segmentations) for your VPC network to group related applications in the same subnet.
Can you restrict access to loadbalancer?
you can as well refer as well to Restrict Access For LoadBalancer Service for more control.
Can you filter with Ingress controller?
You can do this kind of filtering with some Ingress controllers, but I don't think that includes ingress-gce right now, so it would be somewhat funky to set up.
Can you use a firewall tag to restrict IPs?
since the load balancer is within your network, you can create a ingress firewall rule to deny or allow whatever source IP with a "tag" (assuming that you in mind your authorized IP), after you create your firewall tag in you cluster instance template, which you cluster instance group using modify it by adding the tag to it and roll the update on the instance group, in this case all you node cluster will have the tag to restrict some IPs.
Can load balancers use ingress firewall?
since the load balancer is within your network , you can create a ingress firewall rule to deny or allow whatever source IP with a "tag" (assuming that you in mind your authorized IP), after you create your firewall tag in you cluster instance template, which you cluster instance group using modify it by adding the tag to it and roll the update on the instance group, in this case all you node cluster will have the tag to restrict some IPs.
Inbound rules for Cloud Manager
The source for inbound rules in the predefined firewall rules is 0.0.0.0/0.
Outbound rules for Cloud Manager
The predefined firewall rules for Cloud Manager opens all outbound traffic. If that is acceptable, follow the basic outbound rules. If you need more rigid rules, use the advanced outbound rules.
Inbound rules for Cloud Volumes ONTAP
The source for inbound rules in the predefined security group is 0.0.0.0/0.
Outbound rules for Cloud Volumes ONTAP
The predefined security group for Cloud Volumes ONTAP opens all outbound traffic. If that is acceptable, follow the basic outbound rules. If you need more rigid rules, use the advanced outbound rules.
