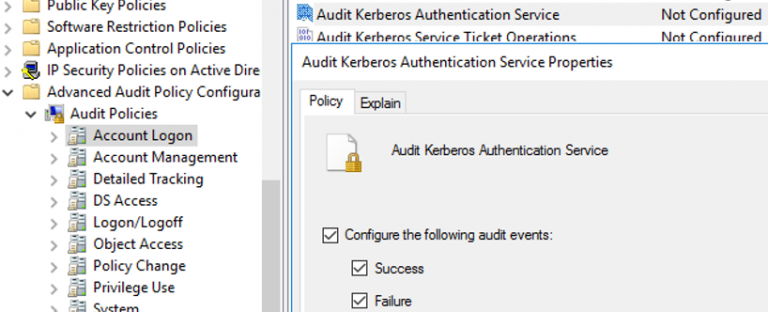
To check user login history in Active Directory, enable auditing by following the steps below: 1 Run gpmc.msc (Group Policy Management Console). 2 Create a new GPO. 3 Click Edit and navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policies.
- 1 Run gpmc. ...
- 2 Create a new GPO.
- 3 Click Edit and navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policies.
How to monitor user logons in Active Directory domain?
To check user login history in Active Directory, enable auditing by following the steps below:
- Run gpmc.msc (Group Policy Management Console).
- Create a new GPO.
- Click Edit and navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policies. ...
- To link the new GPO to your domain, right-click . Select Link an Existing GPO and choose the GPO that you created.
How do you add users to Active Directory?
- In the Tasks pane on the right, click New under Users, and select User from the menu.
- In the Create User dialog box, all required fields are marked by an asterisk. ...
- All new users must have a SamAccountName, which is the user’s AD logon name, but I recommend filling out the User UPN logon field, and SamAccountName will be filled in ...
How to enable audit failure logs in Active Directory?
To configure auditing for specific Active Directory objects:
- Select Start > Programs > Administrative Tools, and then select Active Directory Users and Computers.
- Make sure that you select Advanced Features on the View menu.
- Right-click the Active Directory object that you want to audit, and then select Properties.
- Select the Security tab, and then select Advanced.
- Select the Auditing tab, and then select Add.
How to audit successful and failed logons in Active Directory?
With ADAudit Plus
- Step 1: Enable auditing for logon failure?
- Logon to your domain controller with administrative privileges and launch the Group Policy Management console.
- Right-click the appropriate Group Policy Object linked to the Domain Controllers container and select Edit.

How do I monitor user activity in Active Directory?
Perform the following steps in the Event Viewer to track session time:Go to “Windows Logs” ➔ “Security”.Open “Filter Current Log” on the rightmost pane and set filters for the following Event IDs. You can also search for these event IDs. ... Double-click the event ID 4648 to access “Event Properties”.
How do I check my domain login history?
How to check user logon history? Step 1 -Run gpmc. msc → Create a new GPO → Edit it: Go to "Computer Configuration" → Policies → Windows Settings → Security Settings → Advanced Audit Policy Configuration → Audit Policies → Logon/Logoff: Audit Logon → Define → Success And Failures.
How do I test a specific user login history in Active Directory using PowerShell?
Getting User Last Logon History with PowerShell You can use the Get-Eventlog PowerShell cmdlet to get all events from the domain controller's event logs, filter them by the EventID you want, and display information about the time when a user authenticated in the domain and a computer used to logon.
How do I check Windows log history?
Checking Windows Event LogsPress ⊞ Win + R on the M-Files server computer. ... In the Open text field, type in eventvwr and click OK. ... Expand the Windows Logs node.Select the Application node. ... Click Filter Current Log... on the Actions pane in the Application section to list only the entries that are related to M-Files.More items...
How do I view Windows login sessions?
Right-click the taskbar, then select “Task Manager“. Select the “Users” tab. Details on the users logged into the machine are displayed.
How do I filter the security event log by user?
How to search the Windows Event Log for logins by usernameOpen event viewer and select the Security Logs.Select filter current log in the Actions pane.Select XML tab.Select 'Edit query manually'Replace the line with the highlighted line below and select okay.
How do I get the Active Directory PowerShell module?
On the Features page, expand Remote Server Administration Tools > Role Administration Tools > AD DS and AD LDS Tools, then select Active Directory module for Windows Powershell. Once selected, click Next. On the Confirmation page, click Install. Once the install completes successfully, click Close.
How do I view user activity in Windows Server 2016?
To monitor remote client activity and status. In Server Manager, click Tools, and then click Remote Access Management. Click REPORTING to navigate to Remote Access Reporting in the Remote Access Management Console.
How do I see who is logged into my Windows 2008 Server?
Step 1- Open the Command Line Interface by running "cmd" in the run dialog box (Win + R). Step 2- Type query user and press Enter. It will list all users that are currently logged on your computer.
How to track user changes in Active Directory?
To track user account changes in Active Directory, open “Windows Event Viewer”, and go to “Windows Logs” ➔ “Security”. Use the “Filter Current Log” option in the right pane to find the relevant events.
What is Lepide Active Directory Auditor?
Often cited as being both quicker and easier than native auditing methods, Lepide Active Directory Auditor (part of Lepide Data Security Platform) enables you to track user account changes in your Active Directory in a much better way. The following image shows the “User Status Modifications” report. The complete audit information about a user’s status change is shown in a single line record:
How to create a GPO in a domain?
To create a new GPO, right-click the domain name in the left panel, and click “Create a GPO in this domain, and Link it here”. It shows the “New GPO” window on the screen. Provide a name (User Account Management in our case) and click “OK”. The new GPO appears in the left pane.
What is Event ID 4740?
Event ID 4740 shows a user account was locked out.
Why configure above policy in Advanced Audit Policy Configuration?
This is because you have to enable all account management policies in “Local Policy” that will generate huge amount of event logs. To minimize the noise, “Advanced Audit Policy Configuration” should be preferred.
How to open Group Policy Management console?
Go to “Administrative Tools” and open “Group Policy Management” console on the primary “Domain Controller”.
Can you see the same user's status change record in Lepide Active Directory Auditor?
The record has been highlighted and the complete audit information, like who enabled the user and when, is available in a single line record.
What is the logon ID?
The logon ID is a number (unique between reboots) that identifies the most recently initiated logon session. Any subsequent activity is reported with this ID. By associating logon and logoff events with the same logon ID, you can calculate the logon duration.
Where are local logoffs recorded?
All local logon and logoff-related events are only recorded in the security log of individual computers (workstations or Windows servers) and not on the domain controllers (DCs).
How often does Windows update Group Policy?
By default, Windows updates Group Policy every 90 minutes; if you want the changes to be reflected immediately, you can force a background update of all Group Policy settings by executing the following command in the Windows Command Prompt:
Is logoff recorded on DCs?
Logoff events are not recorded on DCs. This information is vital in determining the logon duration of a particular user.
What happens when you audit Active Directory events?
When you audit Active Directory events, Windows Server 2003 writes an event to the Security log on the domain controller. For example, a user tries to log on to the domain by using a domain user account. If the logon attempt is unsuccessful, the event is recorded on the domain controller, not on the computer where the logon attempt was made. This behavior occurs because it's the domain controller that tried to authenticate the logon attempt but couldn't do so.
How to enable auditing of Active Directory?
To enable auditing of Active Directory objects: Configure an audit policy setting for a domain controller. When you configure an audit policy setting, you can audit objects, but you can't specify the object you want to audit. Configure auditing for specific Active Directory objects. After you specify the events to audit for files, folders, ...
What is audit policy setting?
An audit policy setting defines the categories of events that Windows Server 2003 logs in the Security log on each computer. The Security log makes it possible for you to track the events that you specify.
What is auditing in Windows 2003?
You can use Windows Server 2003 auditing to track both user activities and Windows Server 2003 activities that are named events, on a computer. When you use auditing, you can specify which events are written to the Security log. For example, the Security log can maintain a record of both valid and invalid logon attempts and events ...
How to run gpupdate on a computer?
Type gpupdate /Target:computer at the command prompt, and then press ENTER.
What file system do you need to audit?
The files and folders that you want to audit must be on Microsoft Windows NT file system (NTFS) volumes.
Is auditing on domain controllers?
By default, auditing is turned off. For domain controllers, an audit policy setting is configured for all domain controllers in the domain. To audit events that occur on domain controllers, configure an audit policy setting that applies to all domain controllers in a non-local Group Policy object (GPO) for the domain. You can access this policy setting through the Domain Controllers organizational unit. To audit user access to Active Directory objects, configure the Audit Directory Service Access event category in the audit policy setting.
Pull up the complete logon history of any user in your domain
With real-time monitoring and graphical displays, you'll gain better insight into user behavior and logon patterns.
What our customers say
I highly recommend ADAudit Plus. Now, I can easily monitor user logons, file deletions / modifications, changes in AD and export them as reports. The friendly UI and product support before and after-purchase are excellent.
