
- Port list separated by commas: $ nmap -p80,443 localhost.
- Port range denoted with hyphens: $ nmap -p1-100 localhost.
- Alias for all ports from 1 to 65535: # nmap -p- localhost.
- Specific ports by protocol: # nmap -pT:25,U:53 <target>
- Service name: # nmap -p smtp <target>
How to do basic port scanning with Nmap?
How to do basic port scanning with Nmap? Method 2 of 2: Using the Command Line Download Article Install Nmap. Before using Nmap, you will need to install it so that you can run it from the command line of your operating system. Open your command line. Nmap commands are run from the command line, and the results are displayed beneath the command.
What you should know about Nmap?
What you should know about Nmap? Nmap (Network Mapper) is a free and open-source network scanner created by Gordon Lyon (also known by his pseudonym Fyodor Vaskovich). Nmap is used to discover hosts and services on a computer network by sending packets and analyzing the responses. Is Nmap safe? The site is certainly good and safe.
How to scan an IP network range with Nmap?
syntax: nmap -sU <target> In order to scan a particular UDP port, you can use -p option for port selection nmap -sU -p 4500 192.168.1.6 . Similar to TCP scan we can give a port range and we can also scan all UDP ports nmap -sU -p1-500 192.168.1.6 and nmap -sU -p- 192.168.1.6. OS Detection Scan
Is Nmap illegal to use?
casual scan USUALLY is not illegal. But constantly scan someone and steal BW with scan packets from him is. NMAP (like a bunch of other tools) is just a tool. It inst illegal. However you can use it for illegal purposes. b) because it may be just a victim, with a backdoor installed.
How do you scan which ports are open?
You'll use the netstat program to identify open ports, and then use the nmap program to get information about the state of a machine's ports on a network. When you're done you'll be able to identify common ports and scan your systems for open ports.
Does Nmap show all ports?
By default, Nmap scans the 1,000 most popular ports of each protocol it is asked to scan. Alternatively, you can specify the -F (fast) option to scan only the 100 most common ports in each protocol or --top-ports to specify an arbitrary number of ports to scan.
What are the Nmap commands?
Nmap CommandsScan a Range of IP Address. Aim: To scan the entire IP range. ... Port Scanning. Aim: To scan a specific port or entire port range. ... Ping Scan Using Nmap. ... Saving the Nmap Scan Output to a File. ... Most Popular Ports Scanning. ... Display Open Ports. ... Exclude Host/ IP Addresses for the Scan. ... Service Version Detection.
How many ports are open on the machine Nmap?
By default, Nmap scans the most common 1,000 ports for each protocol. This option specifies which ports you want to scan and overrides the default. Individual port numbers are OK, as are ranges separated by a hyphen (e.g. 1-1023 ).
How do I scan 65535 ports in Nmap?
Scan All TCP Ports with Range We can specify the port range with the -p option. As we know TCP port numbers are between and 65535 . We will use -p0-65535 as an option in order to scan all TCP ports. We do not specify the TCP protocol because the default protocol for Nmap port scan is TCP.
How long does it take Nmap to scan all ports?
By default, Nmap scans the most common 1,000 ports. On a fast network of responsive machines, this may take a fraction of a second per host. But Nmap must slow down dramatically when it encounters rate limiting or firewalls that drop probe packets without responding. UDP scans can be agonizingly slow for these reasons.
How do I scan 1000 ports in Nmap?
To view these one-thousand ports, use the following command: $ sudo nmap -sT --top-ports 1000 -v -oG - # Nmap 7.70 scan initiated Mon Feb 3 12:12:04 2020 as: nmap -sT --top-ports 1000 -v -oG - # Ports scanned: TCP(1000;1,3-4,6-7,9,13,17,19-26,30,32-33,37,42-43,49,53,70,79-85,88-90...
How Nmap tool scan both TCP and UDP ports?
Fortunately, Nmap can help inventory UDP ports. UDP scan is activated with the -sU option. It can be combined with a TCP scan type such as SYN scan ( -sS ) to check both protocols during the same run. UDP scan works by sending a UDP packet to every targeted port.
Nmap Commands to Scan All Open Ports
Computer ports are endpoints that facilitate data communication over networks. That's why they are essential to both hackers and security analysts. Nmap makes scanning open ports easier even for starting users.
Monitor Network Ports Using Nmap
Nmap's simple interface and rich feature set make it the go-to tool for scanning open ports. Plus, it provides many extra facilities, including service detection and bug discovery.
Where is the Nmap test server?
The nmap creators provide a test server located at scanme.nmap.org.
What is port scanning?
Port Scanning: Port scanning is the process of attempting to connect to a number of sequential ports, for the purpose of acquiring information about which are open and what services and operating system are behind them.
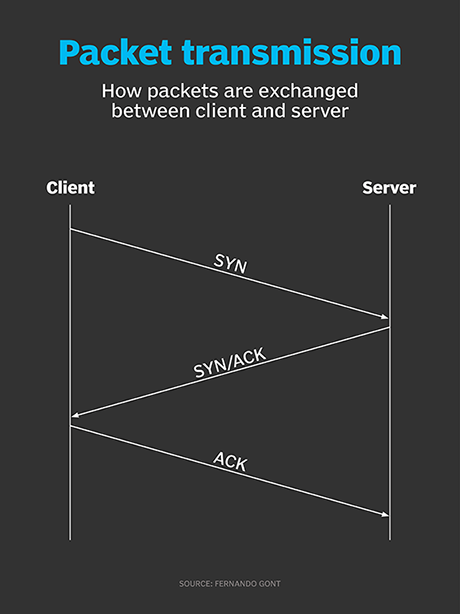
How to start a TCP connection?
To start a TCP connection, the requesting end sends a “synchronize request” packet to the server. The server then sends a “synchronize acknowledgment” packet back. The original sender then sends back an “acknowledgment” packet back to the server, and a connection is established.
What is a port in TCP/IP?
In TCP/IP and UDP networking, ports are endpoints for logical communications. A single IP address may have many services running, such as a web server, an application server, and a file server. In order for each of these services to communicate, they each listen and communicate on a specific port.
What is the process that takes place when an application or service uses an internet socket to handle the data it is inputting?
Binding: The process that takes place when an application or service uses an internet socket to handle the data it is inputting and outputting.
What is port in a network?
Port: An addressable network location implemented inside of the operating system that helps distinguish traffic destined for different applications or services.
What is the default port for secure web traffic?
For example, when you connect to https://digitalocean.com, you’re connecting to the digitalocean.com server on port 443 , the default port for secure web traffic.
Listing open ports on a target
This recipe describes how to use Nmap to determine the port states of a target, a process used to identify running services commonly referred to as port scanning. This is one of the tasks Nmap excels at, so it is important to learn about the essential Nmap options related to port scanning.
There's more..
Port scanning is one of the most powerful features available, and it is important that we understand the different techniques and options that affect the scan behavior of Nmap.
What is nmap in Linux?
Nmap is the command commonly used for the purpose of scanning the ports. In this article, we discussed how to scan open ports on Linux systems using nmap along with examples to demonstrate the use of these and various options to further specify the use.
What is nmap used for?
Nmap (Network Mapper) is the most popular discovery tool used by Network Administrators for security auditing and mapping their network. This core tool is furthermore used for finding live hosts, OS detection, performing port scanning, and version detection.
What command to use to check open ports?
There are several commands available to check open ports and scan them on your system, but nmap is the most used command for this purpose. In this article, we’ll discuss how to scan all open ports with nmap on your Linux system.
Why is it important to check all open ports?
Checking ports open on a network is extremely crucial as any open port can easily be attacked by hackers and cause security threats. That’s why it is important to perform a scan and check all the open ports and if they’re not in use, close them.
What is open port?
Here open ports are those that are accepting incoming packets from a location and they can pose a security risk as such ports can be used by various attackers.
Can we scan any port?
We can scan any port, a range of IP addresses , or any host we can use the nmap command in the following way:
Can you run nmap without sudo?
You can also run nmap without sudo but an unprivileged scan uses -sT (TCP Connect) while privileged (root) uses -sS (TCP SYN Stealth).
How to scan a range of ports?
A range of ports can be scanned by separating them with a hyphen.
What is nmap in penetration testing?
It can provide detailed information like OS versions, making it easier to plan additional approaches during penetration testing.
Why use Nmap?
There are a number of reasons why security pros prefer Nmap over other scanning tools.
How does stealth scan work?
Stealth scanning is performed by sending an SYN packet and analyzing the response. If SYN/ACK is received, it means the port is open, and you can open a TCP connection. However, a stealth scan never completes the 3-way handshake, which makes it hard for the target to determine the scanning system.
What is nmap used for?
What is Nmap and How to Use it – A Tutorial for the Greatest Scanning Tool of All Time. Nmap is the most famous scanning tool used by penetration testers. In this article, we will look at some core features of Nmap along with a few useful commands.
What is port scanning?
Port scanning is one of the most fundamental features of Nmap. You can scan for ports in several ways. Using the -p param to scan for a single port. > nmap -p 973 192.164.0.1. If you specify the type of port, you can scan for information about a particular type of connection, for example for a TCP connection.
What is a nmap?
Nmap is short for Network Mapper. It is an open-source Linux command-line tool that is used to scan IP addresses and ports in a network and to detect installed applications. Nmap allows network admins to find which devices are running on their network, discover open ports and services, and detect vulnerabilities.
What ports does DNS scan for?
Quickly scan for some of the standard ports like FTP, SMTP, DNS, Finger, POP3, SFTP, RPC, IRC, IMAP, VNC, etc. through DNS Tools.
How many ports does Hacker Target scan?
Hacker Target lets you perform a quick scan with most standard following ten ports with a hosted NMAP port scanner.
What is spyse port scanner?
Spyse’s Port Scanner eliminates the wait for long scans and gives users some flexibility in performing reconnaissance.
Is the number of scanned ports growing?
Also, the number of scanned ports is constantly growing .
Can an attacker open unwanted ports?
Having unwanted ports opened is a lousy idea; an attacker can take advantage of it in many ways. Here are online FREE tools, which will help you to find out what all ports are opened so you can review and block them if not needed.
Does a port scan give accurate information?
Note: if you’re running a port scan on your website DNS and if that is behind the cloud proxy like Cloudflare or SUCURI, then it may not give you the accurate information.
