How to add an SSH key to an existing DigitalOcean droplet
- (1) Retrieve and save your current public key to a text file
- (2) Upload the SSH key to a file sharing service. This will give you a link that you can use to download the key. ...
- (3) Reset your droplet's password. ...
- (4) Add SSH key to droplet. ...
- Create Droplets.
- Connect With SSH. Connect With OpenSSH. Connect With PuTTY.
- Connect With the Droplet Console.
- Transfer Files With Filezilla.
- Access Droplet Metadata.
- Add SSH Keys to Droplets. Create Keys With OpenSSH. Create Keys With PuTTY. Add SSH Keys to a Team. Add Keys to Existing Droplets.
- Tag Droplets.
- Track Performance.
How do I connect to a droplet using SSH keys?
If this happens, you can delete the old Droplet’s host key from your local system with the command ssh-keygen -R 203.0.113.0 and then reconnect. The next part of the connection process is authentication. If you’ve added SSH keys, you’ll connect to the Droplet immediately (or after entering the passphrase for your key pair).
How do I log in to my DigitalOcean droplet using SSH?
To log in to your Droplet with SSH, you need three pieces of information: To get your Droplet’s IP address, visit the DigitalOcean Control Panel. The IP address is displayed in the IP Address column after your Droplet has been created. You can mouse over it to copy it into your clipboard.
How do I connect to a droplet?
To connect to your Droplet, you’ll need to open a terminal. How you do this varies between operating systems and window managers, but generally: Linux: Search Terminal or press CTRL+ALT+T. macOS: Search Terminal. Bash on Windows: Search Bash. If you don’t have Bash on Windows, use PuTTY instead.
How do I manage a DigitalOcean droplet?
DigitalOcean Droplets are managed using a terminal and SSH. You’ll need to have an SSH client and, optionally, an SSH key pair. Clients generally authenticate either using passwords (which are less secure and not recommended) or SSH keys (which are very secure and strongly recommended).
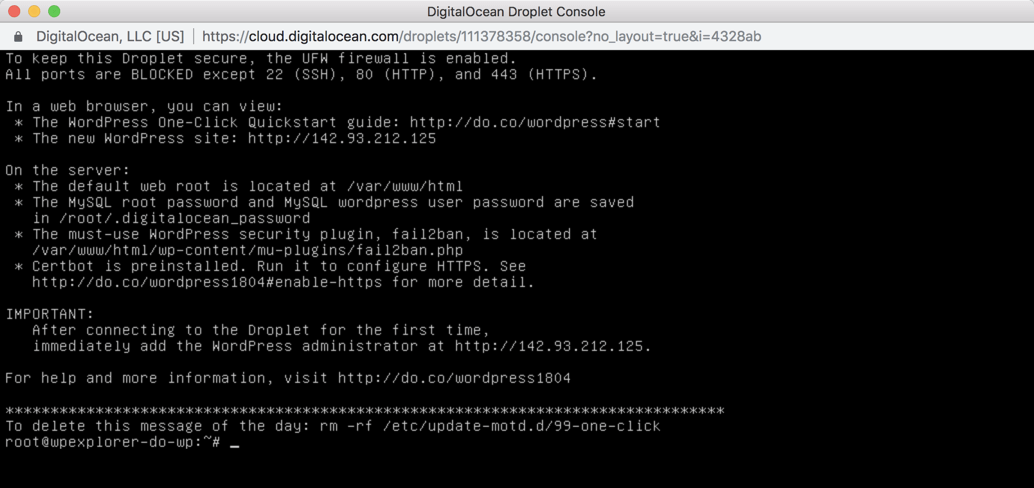
How do I login to a droplet?
Access the Droplet Console In the Droplet Console section, enter the user you want to log in as in the Log in as… field. By default, this is set to root . Once you choose a user, click Launch Droplet Console to open the Droplet console.
How do I get SSH key for DigitalOcean droplet?
Use OpenSSH to create new SSH keys on MacOS, Linux, or Windows Subsystem for Linux. Use PuTTY to create SSH keys on Windows systems without Bash. Add your SSH key to your Droplets. On DigitalOcean, you can upload your SSH public key to your account, which lets you add it to your Droplets at creation time.
How do I access the console in DigitalOcean?
Connecting to the Console in the Browser DigitalOcean droplets offer in-browser access to the console. Just click that "Console Access" button and enter "root" for the username, followed by the password from your e-mail.
How do I SSH?
How to use an SSH clientStart PuTTY.In the Host Name (or IP address) text box, type the hostname or IP address of the server where your account is located.In the Port text box, type 7822. ... Confirm that the Connection type radio button is set to SSH.Click Open.More items...
What is SSH key DigitalOcean?
SSH (Secure SHell) is an cryptographic protocol to administer and communicate with servers securely over an unsecured network. In this guide, we'll focus on setting up SSH keys, which provide a secure way of logging into your server, and are recommended for all users. Choose your operating system below to get started.
How do I add a key to SSH?
ssh on Linux.Set up your default identity. From the terminal, enter ssh-keygen at the command line. ... Add the key to the ssh-agent. If you don't want to type your password each time you use the key, you'll need to add it to the ssh-agent. ... Add the public key to your Account settings.
How do I SSH from the command line?
How to start a SSH session from the command line1) Type the path to Putty.exe here.2) Then type the connection type you wish to use (i.e. -ssh, -telnet, -rlogin, -raw)3) Type the username...4) Then type '@' followed by the server IP address.5) Finally, type the port number to connect to, then press
What are SSH commands?
ssh command instructs the system to establish an encrypted secure connection with the host machine. user_name represents the account that is being accessed on the host. host refers to the machine which can be a computer or a router that is being accessed.
How do I SSH into a server in terminal?
See our article Best Practices: Securing Your Computer to see how to keep your workstation secure.Open the terminal (command line interface) on your computer. ... You will see the name of your user on your terminal screen and a blinking cursor. ... The command to log in via SSH is ssh. ... Press Enter.More items...
How do I copy a SSH key?
ProcedureIn a terminal window, enter the following command: ssh-keygen -t rsa.Follow the prompts to generate the key. You must provide a file name and a passphrase. A public and a private key are generated. ... Copy the public key to each node computer, by using the following command: ssh-copy-id username @ node_name.
How do I find my SSH key in Windows?
Generating an SSH keyOpen the PuTTYgen program.For Type of key to generate, select SSH-2 RSA.Click the Generate button.Move your mouse in the area below the progress bar. ... Type a passphrase in the Key passphrase field. ... Click the Save private key button to save the private key.More items...•
What is SSH key file?
An SSH key is an access credential for the SSH (secure shell) network protocol. This authenticated and encrypted secure network protocol is used for remote communication between machines on an unsecured open network. SSH is used for remote file transfer, network management, and remote operating system access.
How do I log into SSH with a password?
To do so:Open the SSH terminal on your machine and run the following command: ssh your_username@host_ip_address. ... Type in your password and hit Enter. ... When you are connecting to a server for the very first time, it will ask you if you want to continue connecting.More items...•
How to configure SSH access?
To configure the SSH access, you’ll have to log in to your machine using the root access for the first time. This may be a little tricky, and to do the first access, you’ll need to set up a new password because every system comes with one predefined root user and password. The first thing you need to do is access the specific droplet page by ...
Can adduser jess create password?
adduser jess. And once you run the command, you’ll be prompted to create a password . You may optionally add some extra information for the user: Once you confirm all the information is correct, you can give your user sudo powers. Sudo powers will let you install things without having to access the root user.
Why is SSH so secure?
Password-based security is notoriously insecure due to password fatigue and the overuse of passwords such as ‘123456’. Secure Shell or SSH is a network communication protocol that solves this by using passwordless solutions for encryption, enabling two computers to communicate and securely share data. At a high level, SSH works by creating cryptographic key pairs consisting of a public and private key, which are computer generated and stored separately to ensure their security.
What is the new droplet console?
The new Droplet Console provides one-click SSH access to your Droplets through a native-like SSH/Terminal experience. It also eliminates the need for a password or manual configuration of SSH keys. Starting today, we’re pleased to announce that the new Droplet Console is now available to all Droplet users.
Is SSH the default encryption protocol?
SSH has become the default encryption protocol for many industries, but it was difficult to use SSH keys with DigitalOcean’s current Recovery (VNC) console, which is why we developed our new Droplet Console. The new Droplet Console is backed by an agent that security supervises the key pair, while also providing one-click SSH access to our users. You can see the full list of features below.
