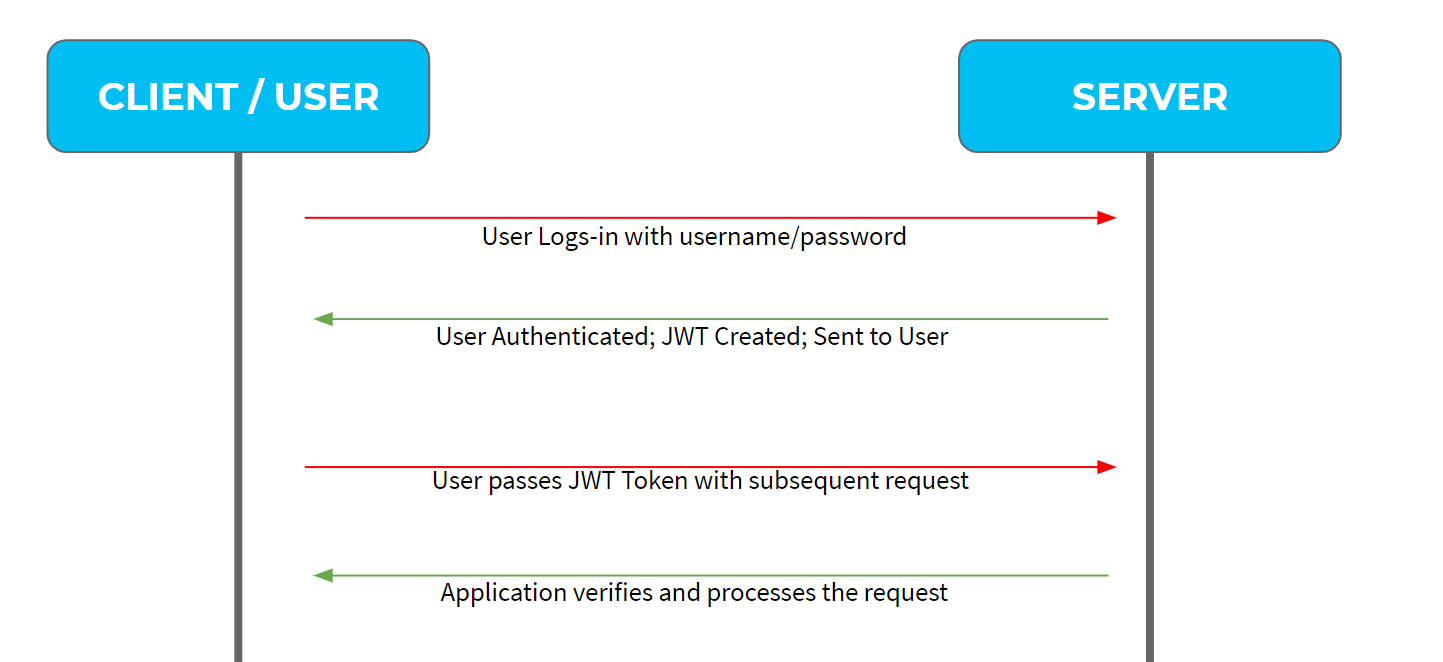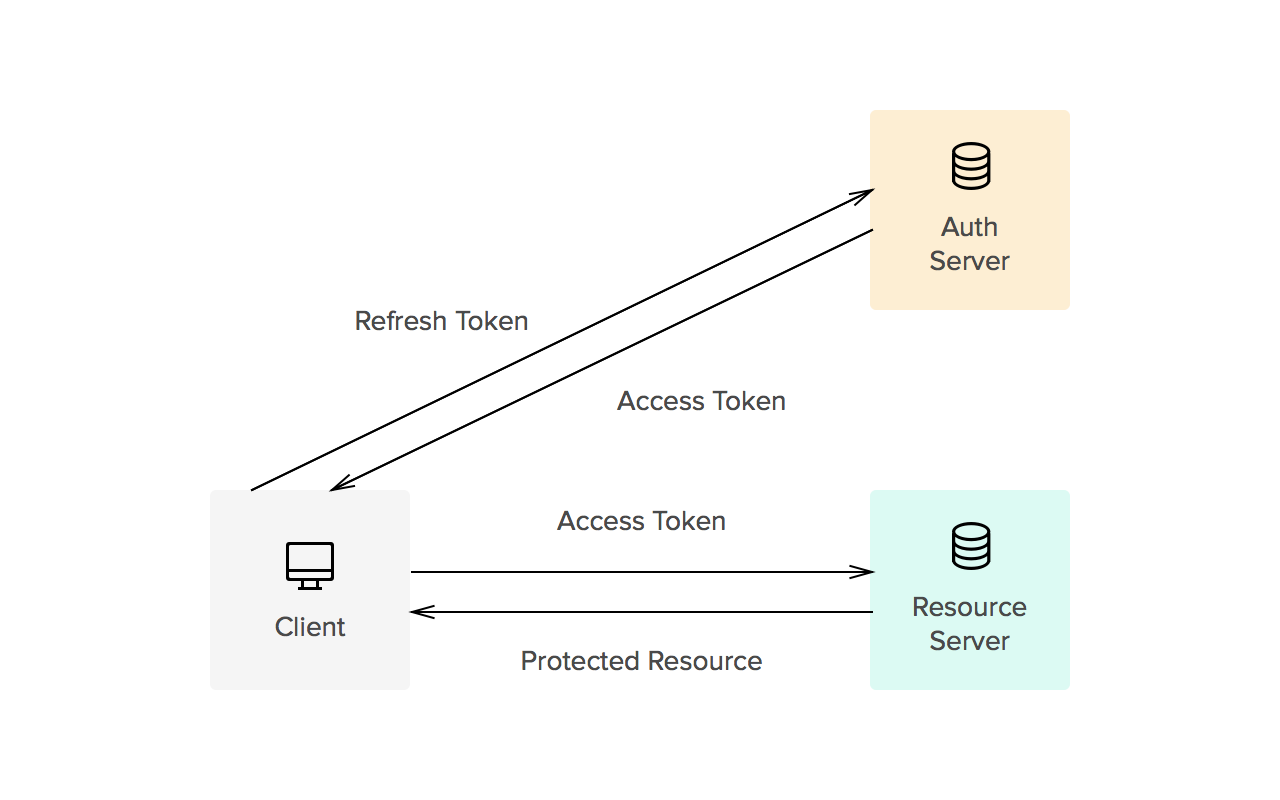
The following diagram shows how a JWT is obtained and used to access APIs or resources:
- The application or client requests authorization to the authorization server. This is performed through one of the different authorization flows. ...
- When the authorization is granted, the authorization server returns an access token to the application.
- The application uses the access token to access a protected resource (like an API).
Full Answer
How to validate a JWT token?
Verifying a JSON web token
- Confirm the structure of the JWT A JSON Web Token (JWT) includes three sections: Header Payload Signature 11111111111.22222222222.33333333333 These sections are encoded as base64url strings and are separated ...
- Validate the JWT signature The JWT signature is a hashed combination of the header and the payload. ...
- Verify the claims
Is a JWT usable as a CSRF token?
based on the fact that CSRF is only possible if the authentication cookie was sent along with the forged request, we can use JWT authentication to avoid CSRF attack. JWT - JSON Web Token is an open standard (RFC 7519) that defines a compact and self-contained way for securely transmitting information between parties as a JSON object .
What is the maximum size of JWT token?
What kind of data is typically stored in there? The standard ( RFC 7519) doesn't specify a maximum size for the token, so theoretically you can store as much data as you want, as long as you don't exceed the maximum size of your storage medium. However, this isn't really recommended since JWTs are supposed to be as compact as possible.
How to generate and access key for JWT?
- In the Signing Key box, paste the public and private key that you generated in the Create a public/private key pair step.
- For the key format, use either the default of JWT or switch to PEM, and then click Generate JWT.
- The signed JWT appears. Copy the JWT for use in the Get an access token step.

How does the JWT token work?
The authentication server verifies the credentials and issues a JWT signed using a private key. Moving forward, the client will use the JWT to access protected resources by passing the JWT in the HTTP Authorization header. The resource server then verifies the authenticity of the token using the public key.
How are JWT tokens stored?
A JWT needs to be stored in a safe place inside the user's browser. Any way,you shouldn't store a JWT in local storage (or session storage). If you store it in a LocalStorage/SessionStorage then it can be easily grabbed by an XSS attack. If the answer is helpful, please click "Accept Answer" and upvote it.
What happens if someone gets a JWT token?
One of the most important steps is to ask your clients to change their passwords immediately if there's an instance where the JWT token is stolen. Changing the password of an account will prevent attackers from exploiting the account and would eventually help in avoiding a data breach.
What are the 3 parts of JWT?
Figure 1 shows that a JWT consists of three parts: a header, payload, and signature. The header typically consists of two parts: the type of the token, which is JWT, and the algorithm that is used, such as HMAC SHA256 or RSA SHA256. It is Base64Url encoded to form the first part of the JWT.
Is JWT the same as Oauth?
Using JWT with OAuth2 JWT and OAuth2 are entirely different and serve different purposes, but they are compatible and can be used together. The OAuth2 protocol does not specify the format of the tokens, therefore JWTs can be incorporated into the usage of OAuth2.
Where does JWT store backend?
To keep them secure, you should always store JWTs inside an httpOnly cookie. This is a special kind of cookie that's only sent in HTTP requests to the server. It's never accessible (both for reading or writing) from JavaScript running in the browser.
Is it possible to steal JWT token?
The concerning bit in this process is where the JWT is being stored in the client-side because storing it insecurely would provide an attacker the possibility of hijacking it. Since the JWT is a session token can be used to access the resources that the compromised token has access to.
How long do JWT tokens last?
The JWT access token is only valid for a finite period of time. Using an expired JWT will cause operations to fail. As you saw above, we are told how long a token is valid through expires_in . This value is normally 1200 seconds or 20 minutes.
How do JWT tokens expire?
The API returns a short-lived token (JWT), which expires in 15 minutes, and in HTTP cookies, the refresh token expires in 7 days. JWT is currently used for accessing secure ways on API, whereas a refresh token generates another new JWT access token when it expires or even before.
What data is stored in JWT?
jwt Getting started with jwt What to store in a JWT The JWT RFC stablish three classes of claims: Registered claims like sub , iss , exp or nbf. Public claims with public names or names registered by IANA which contain values that should be unique like email , address or phone_number .
Does JWT token contain password?
No, the JWT doesn't contain credentials.
Is JWT authentication or authorization?
To authenticate a user, a client application must send a JSON Web Token (JWT) in the authorization header of the HTTP request to your backend API. API Gateway validates the token on behalf of your API, so you don't have to add any code in your API to process the authentication.
Can we store JWT token in localStorage?
Many people don't realize that JWTs are essentially the same thing as a username/password. If an attacker can get a copy of your JWT , they can make requests to the website on your behalf and you will never know. Treat your JWTs like you would a credit card number or password: don't ever store them in local storage.
Is JWT stored in cookie?
In web browser, you can store JWT in local/session storage or in cookie.
Where are the tokens stored?
Since tokens are stored in local/session storage or a client side cookie, they are open to an XSS attack getting the attacker access to the token. This is a valid concern, and for that reason you should keep your tokens expiration low. But if you think about the attack surface on cookies, one of the main ones is XSRF.
Where are JWT tokens stored in react?
Storing JWT Token We can store it as a client-side cookie or in a localStorage or sessionStorage. There are pros and cons in each option but for this app, we'll store it in sessionStorage.
When should a user agent send a JWT?
Whenever the user wants to access a protected route or resource , the user agent should send the JWT, typically in the Authorization header using the Bearer schema. The content of the header should look like the following:
Why do we use signatures in JWT?
The signature is used to verify the message wasn't changed along the way , and, in the case of tokens signed with a private key, it can also verify that the sender of the JWT is who it says it is.
What is the JSON Web Token structure?
In its compact form, JSON Web Tokens consist of three parts separated by dots (. ), which are:
How do JSON Web Tokens work?
In authentication, when the user successfully logs in using their credentials, a JSON Web Token will be returned. Since tokens are credentials, great care must be taken to prevent security issues. In general, you should not keep tokens longer than required.
Why should we use JSON Web Tokens?
Let's talk about the benefits of JSON Web Tokens (JWT) when compared to Simple Web Tokens (SWT) and Security Assertion Markup Language Tokens ( SAML).
What are JSON tokens?
In its compact form, JSON Web Tokens consist of three parts separated by dots (. ), which are: 1 Header 2 Payload 3 Signature
What is JWT authorization?
Authorization: This is the most common scenario for using J WT. Once the user is logged in, each subsequent request will include the JWT, allowing the user to access routes, services, and resources that are permitted with that token . Single Sign On is a feature that widely uses JWT nowadays, because of its small overhead and its ability to be easily used across different domains.
How does JWT differ from other web tokens?
JWTs differ from other web tokens in that they contain a set of claims. Claims are used to transmit information between two parties. What these claims are depends on the use case at hand. For example, a claim may assert who issued the token, how long it is valid for, or what permissions the client has been granted.
What is a JWT bearer token?
In simpler terms, you can think of a JWT bearer token as an identity badge to get into a secured building. The badge comes with special permissions (the claims); that is, it may grant access to only select areas of the building. The authorization server in this analogy is the reception desk—or the issuer of the badge.
What Is JWT?
JWT, or JSON Web Token, is an open standard used to share security information between two parties — a client and a server. Each JWT contains encoded JSON objects, including a set of claims. JWTs are signed using a cryptographic algorithm to ensure that the claims cannot be altered after the token is issued.
How to use JWTs?
A common way to use JWTs is as OAuth bearer tokens. In this example, an authorization server creates a JWT at the request of a client and signs it so that it cannot be altered by any other party. The client will then send this JWT with its request to a REST API. The REST API will verify that the JWT’s signature matches its payload and header to determine that the JWT is valid. When the REST API has verified the JWT, it can use the claims to either grant or deny the client’s request.
What is a JWT string?
A JWT is a string made up of three parts, separated by dots (.), and serialized using base64. In the most common serialization format, compact serialization, the JWT looks something like this: xxxxx.yyyyy.zzzzz.
What is JWT used for?
In short, JWTs are used as a secure way to authenticate users and share information.
What is a JSON token?
Now that you understand JSON as a data text format, you may be wondering What are tokens? To put it simply, a token is a string of data that represents something else, such as an identity. In the case of authentication, a non-JWT based token is a string of characters that allow the receiver to validate the sender’s identity. The important distinction here is lack of meaning within the characters themselves.
What is JWT (JSON Web Token)?
JWT, or JSON Web Token, is an open standard used to share information between two parties securely — a client and a server. In most cases, it’s an encoded JSON containing a set of claims and a signature. It’s usually used in the context of other authentication mechanisms like OAuth, OpenID to share user-related information.
Structure of JWT
JWT structure is divided into three parts: header, payload, signature & is separated from each other by dot (.), and will follow the below structure:
How does JWT Authentication work? When to use JWT Authentication?
When it comes to API authentication and server-to-server authorization, JSON web token (JWT) is particularly a useful technology. In terms of Single Sign-On (SSO), it means that a service provider can receive trustworthy information from the authentication server.
How JWT Single Sign-On (SSO) works for multiple web apps
Single Sign-On (SSO) allows you to authenticate users in your systems and subsequently informs applications that the user has been authenticated. On successful authentication, a JWT token is generated and returned, which can be consumed by the app to create a user session. The token is automatically verified with the IDP when they sign in.
How is a JWT generated?
A signed JSON Web Token consists of three parts, each of which are encoded using Base64 and separated by a point.
What are JWTs used for?
Compared with traditional options for authentication and authorization with cookies, JWTs come with several advantages. This has led to their popularity in contexts like the following:
What is JSON Web Token?
A JSON Web Token (JWT) is an access token standardized according to RFC 7519, which makes it possible for two parties to securely exchange data. It contains all important information about an entity, meaning that no database queries are necessary and the session doesn’t need to be saved on the server.
How do JSON Web Tokens work?
As soon as a user has successfully entered their login information, the JWT will be returned with the key and saved locally. This transfer should take place over HTTPS to ensure that the data is protected.
How many parts are in a JSON token?
A signed JSON Web Token consists of three parts, each of which are encoded using Base64 and separated by a point.
What is a JWT header?
The header usually contains two parts and provides important information about the token. It contains the type of the token and the signing/encryption algorithm being used. For example, a JWT header can look as follows:
Why is it necessary to use a secret key?
In order to ensure that the signature works, it’s necessary to use a secret key that is only known to the issuing app. The signature verifies that nothing was changed in the message along the way. In the case of a token that was signed with a private key, it also ensures that the sender is who they claim to be.
What is JWT token?
JSON Web Token (JWT) is an open standard (RFC 7519) for securely transmitting information between parties as JSON object. It is compact, readable and digitally signed using a private key/ or a public key pair by the Identity Provider (IdP). So the integrity and authenticity of the token can be verified by other parties involved.
What is JWT signature?
Signature is most important part of a JSON Web Token (JWT). Signature is calculated by encoding the header and payload using Base64url Encoding and concatenating them with a period separator. Which is then given to the cryptographic algorithm.
How it works?
Basically the identity provider (IdP) generates a JWT certifying user identity and Resource server decodes and verifies the authenticity of the token using secret salt / public key.
What happens if JWT is persisted on cookies?
If JWT is persisted on cookies, we need to create HttpOnly cookie. This will restrict third party javascripts from reading jwt token from cookie.
How many parts are in a JSON token?
A JSON Web Token consists of 3 parts separated by a period.
Can a JWT session expire?
Revoking the session of a user from backend server is difficult. Since a JWT is set to automatically expire, If an attacker gets the token before it expires It leads to various exploits. Building a token revocation list on your server to invalidate tokens could be best way to mitigate.
Can custom claims be included in a claim set?
Custom claims can also be included in the claim set. When using custom claim sets,
What is JWT in HTML?
The JWT is very compact and can be easily exchanged in HTML and HTTP environments. The header and payload can be easily decoded (since it’s just base64) to retrieve information contained within the token. The signature can be just used to maintain the integrity of the token and not to secure the contained information.
What is the header of a JWT?
The header consists of two parts i.e. the type of token and the algorithm used for signing (such as HMAC SHA256 or RSA). The token type helps to interpret the token and in this case it’s JWT. For example,
How does a JSON Web Token work?
When a user sends his credentials to the server to login, the server authenticates the user. If the authorization is successful, the server sends a JSON Web Token to the user. The user can use the JWT to request any protected services/resources from the server by including the JWT in the Authorization header using the Bearer schema.
Why is JSON Web Token important?
JSON Web Token helps to maintain the integrity and authenticity of the information because it is digitally signed using secret or public/private key pair using RSA or ECDSA. An important thing to keep in mind about JWT is that it is a signed token and not an encrypted one. Therefore, even though JWT can verify the integrity ...
What is the NBF in JWT?
nbf (Not Before) Claim: The “nbf” claim identifies the time before which the JWT must not be accepted for processing. The current date/time must be after or equal to the not-before date/time.
Why is signature important in JWT?
Signature is the most important part of JWT which helps to verify if the information within the token has been tampered with or not. It can be also used to verify that the sender of the JWT is who it says it is.
Why are JSON parsers so popular?
Compatibility: In most programming languages, JSON parsers are popular because they map directly to objects. Contrary, there is no natural document-to-object mapping in XML. This makes it simpler than SAML assertions to operate with JWT.
What is JWT token?
JWT is considered an open standard (RFC 7519) for transmitting sensitive information between multiple parties.
How are tokens created?
In many cases, tokens are created via dongles or key fobs that generate a new authentication token every 60 seconds in accordance with a known algorithm. Due to the power these hardware devices hold, users are required to keep them safe at all times to ensure they don’t fall into the wrong hands.
How does token authentication work?
As part of the login process, users receive a cryptographically secure one-time passcode that is time-limited to 30 or 60 seconds, depending on the settings at the server end. These soft tokens are generated either by an authenticator app on the device or sent on demand via SMS.
What is token based authentication?
Token-based authentication is just one of many web authentication methods used to create a more secure verification process. Other web authentication methods include biometric authentication and password authentication. While each authentication method is unique, all methods fall under one of the following three categories: knowledge (something you know), inheritance (something you are), and possession (something you own).
Why use token authentication?
By pairing this tried and true process with other comprehensive security measures, MSPs help keep their customers safe from security breaches that put their bottom line—and their reputation—in jeopardy.
Why is it important to implement a robust authentication strategy?
Implementing a robust authentication strategy is critical when it comes to helping your customers protect their networks from a security breach. But for your strategy to truly be effective requires strict adherence to all relevant best practices. Here are a few key factors to keep in mind when deploying a token-based authentication strategy:
What are the elements of a token?
The most common token systems contain a header, payload, and signature . The header consists of the payload type as well as the signing algorithm being used. The payload contains the claims, which are simply any statements pertaining to the user. The signature is exactly what it sounds like—the signature used to prove that the message hasn’t been jeopardized in transit. These three elements work together to create a highly efficient and secure authentication system.