How To Create A Threat Model in 7 Easy Steps With Our Template
- Step 1: Inventory your assets The first step in creating a threat model is evaluating your most valuable assets. This is typically called Asset Inventory or Asset Classification. ...
- Step 2: Prioritize your assets ...
- Step 3: How will you be attacked? ...
- Step 4: Establish your detection methods ...
- Step 5: Plan your response ...
- Step 6: Develop your mitigations ...
- Step 7: Create your own threat model
- Identify security objectives. Clear objectives help you to focus the threat modeling activity and determine how much effort to spend on subsequent steps.
- Create an application overview. ...
- Decompose your application. ...
- Identify threats. ...
- Identify vulnerabilities.
How do I use the threat modeling tool?
The Threat Modeling Tool can help you with your threat modeling needs. For a basic introduction to the tool, see Get started with the Threat Modeling Tool. The Threat Modeling Tool is updated frequently, so check this guide often to see our latest features and improvements. To open a blank page, select Create A Model.
How do I create an azure threat model?
Make sure to select which template you’d like to use for your model You must select which template to use before creating a model. Our main template is the Azure Threat Model Template, which contains Azure-specific stencils, threats and mitigations. For generic models, select the SDL TM Knowledge Base from the drop-down menu.
What should be included in a threat model?
When you produce a threat model, you will: Document how data flows through a system to identify where the system might be attacked. Document as many potential threats to the system as possible. Document security controls that may be put in place to reduce the likelihood or impact of a potential threat.
What is threat modeling in SDLC?
Threat modeling looks at a system from a potential attacker’s perspective, as opposed to a defender’s viewpoint. Making threat modeling a core component of your SDLC can help increase product security. The threat modeling process can be decomposed into three high level steps. Each step is documented as it is carried out.
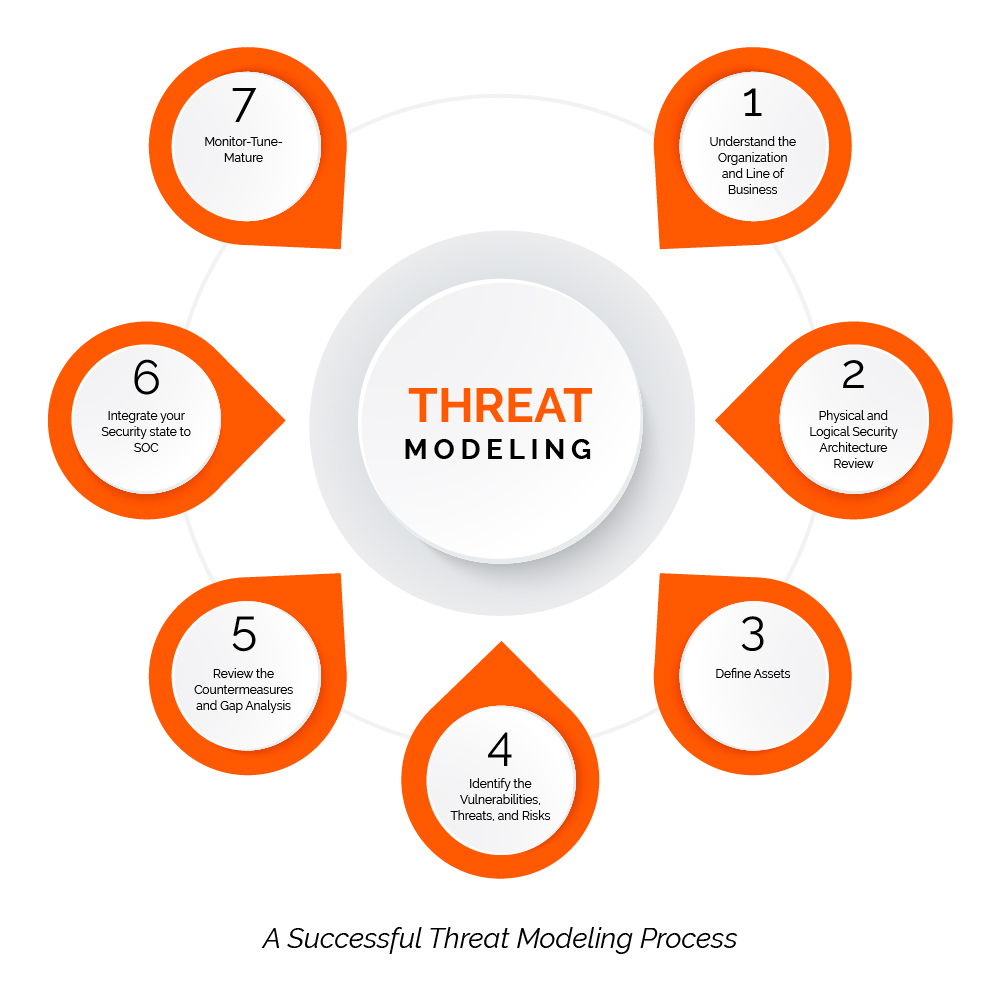
Which four 4 steps make the threat model?
Threat modeling is typically performed in stages, threat modeling in 4 steps:Diagram: what are we building?Identify threats: what can go wrong?Mitigate: what are we doing to defend against threats?Validate: validation of previous steps and act upon them.
How do you create a security threat model?
The five threat modeling steps are:Step 1: identify security objectives. ... Step 2: create an application overview. ... Step 3: decompose your application. ... Step 4: identify threats. ... Step 5: identify vulnerabilities.
What is a threat model examples?
Many threat modeling approaches involve a checklist or a template. For example, STRIDE recommends you consider six types of threats—spoofing, tampering, repudiation, information disclosure, denial of service, and escalation of privilege—for all dataflows that cross a trust boundary.
What are the 6 steps of threat modeling?
How Threat Modeling Protects Your Data AssetsStep 1: Asset Identification. Your first task is to catalog your assets, including data, applications, network components, and many others. ... Step 2: Attack Surface Analysis. ... Step 3: Attack Vectors. ... Step 4: Analysis. ... Step 5: Prioritization. ... Step 6: Security Controls.
What are the five stages of threat modeling?
There are five major threat modeling steps:Defining security requirements.Creating an application diagram.Identifying threats.Mitigating threats.Validating that threats have been mitigated.
What is a threat modeling tool?
The Threat Modeling Tool is a core element of the Microsoft Security Development Lifecycle (SDL). It allows software architects to identify and mitigate potential security issues early, when they are relatively easy and cost-effective to resolve. As a result, it greatly reduces the total cost of development.
What are popular threat Modelling techniques?
The most popular Threat Modelling techniques are Data Flow Diagrams and Attack Trees.
What Is threat modeling in SDLC?
Threat modeling involves thinking through every potential scenario that could lead to an application being compromised. Therefore, it's a good idea to include a threat model in your SDLC as early as possible. This can help ensure: Secure Design. Security is best handled proactively rather than as an afterthought.
What is the difference between threat modeling and risk assessment?
As NIST is quick to point out, “The assessment process is an information-gathering activity, not a security- or privacy-producing activity.” Whereas according to OWASP, “Threat modeling works to identify, communicate, and understand threats and mitigations within the context of protecting something of value.” The key ...
Is threat modeling difficult?
It's scary, complex, and the wrong choice might lead to a lot of unnecessary pain. You want expert advice, and you want the experts to agree. Most of the threat modeling processes previously taught at Microsoft were long and complex, having as many as 11 steps. That's a lot of steps to remember.
When should threat modeling be initiated?
While threat modeling should take place as early as possible, it's still a very useful activity no matter how close an application is to deployment or has been in production. While an app may have reached the end of its development cycle, you can still pick up threat modeling within the support cycle.
Who should be involved in threat modeling?
i.e. one of the information security team or the development team. For the designers or the architects: they should assign the risk mitigation to the development team to consider it while building the application.
How do you perform risk analysis and threat modeling?
Generally there are four main steps: Establish the scope of assessment and identify assets. Determine the threat to the assets and assess the impact and probability of occurrence. Assess vulnerabilities based on the implemented protection and calculate the risks.
What is the first step to understanding a security threats?
Answer: Perform a risk impact analysis is the correct answer.
Which one of the following are generally used as threat modeling diagrams?
The most popular Threat Modelling techniques are Data Flow Diagrams and Attack Trees.
What is your personal threat model?
Well, for that you need a “Personal Threat Model”. Your personal threat model is something you develop and refine over time to evaluate the risks associated with protecting your most valuable assets.
What is the most overlooked step in the security process?
The most overlooked step in the security process (in our opinion) is the detection phase. You can determine your most valuable assets and how you’re most likely to be attacked; but ultimately, that doesn’t matter if you can’t tell when you’ve been attacked.
Can you protect something if you don't know how open it is to attack?
Having at least a baseline understanding of your vulnerability is critical. After all, you can’t protect something if you don’t know how open it is to attack. With this in mind, let’s go over some of the things you need to consider in your threat model.
What is the first step in the threat modeling process?
The first step in the threat modeling process is concerned with gaining an understanding of the application and how it interacts with external entities. This involves:
Why is threat modeling important?
When source code analysis is performed outside the SDLC, such as on existing applications, threat modeling helps to clarify the complexity of source code analysis. It promotes a depth-first approach instead of a breadth-first approach. In other words, instead of reviewing all source code with equal focus, you can prioritize the security code review of components where the threat modelling indicates higher-risk threats.
What is the threat categorization?
A threat categorization such as STRIDE can be used, or the Application Security Frame (ASF) that defines threat categories such as Auditing & Logging, Authentication, Authorization, Configuration Management, Data Protection in Storage and Transit, Data Validation, and Exception Management.
How to mitigate vulnerability?
A vulnerability may be mitigated with the implementation of a countermeasure. Such countermeasures can be identified using threat-countermeasure mapping lists. Once a risk ranking is assigned to the threats in step 2, it is possible to sort threats from the highest to the lowest risk and prioritize mitigation efforts.
How are threats ranked?
Threats can be ranked from the perspective of risk factors. By determining the risk factor posed by the various identified threats, it is possible to create a prioritized list of threats to support a risk mitigation strategy, such as prioritizing the threats to be mitigated first. Different risk factors can be used to rank threats as High, Medium, or Low risk. In general, threat risk models use different factors to model risks such as those shown below:
What is risk mitigation strategy?
The risk mitigation strategy might involve evaluating these threats from the business impact they pose. Once the possible impact is identified, options for addressing the risk include:
Is threat modeling a security code review?
Threat modeling is not an approach to reviewing code, but it does complement the security code review process. The inclusion of threat modeling early on in the Software Development Life Cycle (SDLC) can help to ensure that applications are being developed with appropriate security threat mitigations from the very beginning. This, combined with the documentation produced as part of the threat modeling process, can give code reviewers a greater understanding of the system. This allows the reviewer to see where the entry points to the application are and the associated threats with each entry point.
What Is Threat Modeling?
Threat modeling involves identifying and communicating information about the threats that may impact a particular system or network. Security threat modeling enables an IT team to understand the nature of threats, as well as how they may impact the network.
Threat Modeling Process
The thinking powering the threat modeling process can be summed up by outlining the following:
Threat Modeling Techniques
A key step in the threat modeling process involves decomposing an element of infrastructure or an application that may face a threat. Decomposition involves making sure you understand how the application works and how it interfaces with entities within its system, as well as those that could pose a problem.
Threat Modeling Frameworks and Methodologies
STRIDE stands for spoofing, tampering, repudiation, informative disclosure, denial of service (DoS), and elevation of privilege.
How Fortinet Can Help
The FortiWeb web application firewall (WAF) solution enables an organization to protect their application programming interfaces (APIs) or a web application from threats.
FAQs
Threat modeling involves identifying and communicating information about the threats that may impact a particular system or network. Security threat modeling enables an IT team to understand the nature of threats, as well as how they may impact the network.
What is threat modeling?
Threat modeling is a structured approach of identifying and prioritizing potential threats to a system, and determining the value that potential mitigations would have in reducing or neutralizing those threats. This cheat sheet aims to provide guidance on how to create threat models for both existing systems or applications as well as new systems.
Why is it important to start a threat modeling process?
Before starting the threat modeling process it is important to identify business objectives of the applications you are assessing, and to identify security and compliance requirements that may be necessary due to business or government regulation.
What is a Threat Dragon?
The OWASP Threat Dragon project is a cross platform tool that runs on Linux, macOS and Windows 10. Threat Dragon (TD) is used to create threat model diagrams and to record possible threats and decide on their mitigations using STRIDE methodology. TD is both a web application and a desktop application; refer to the project's GitHub repository for the latest release.
What is likelihood in cyber security?
Likelihood is a measure of the possibility of a threat being carried out. A variety of factors can impact the likelihood of a threat being carried out, including how difficult the implementation of the threat is, and how rewarding it would be to the attacker.
What is impact in a threat?
Impact is a measure of the potential damage caused by a particular threat. Impact and damage can take a variety of forms. A threat may result in damage to physical assets, or may result in obvious financial loss. Indirect loss may also result from an attack, and needs to be considered as part of the impact.
Why is there a trust boundary between the application and the file?
If your application reads a file from disk, there's a trust boundary between the application and the file because outside processes and users can modify the data in the file. If your application makes a call to a remote process, or a remote process makes calls to your application, that's a trust boundary.
Who should assign risk mitigation to the development team?
For the designers or the architects: they should assign the risk mitigation to the development team to consider it while building the application.
How to create an attack tree?
Consider what you must do to launch a successful attack and identify goals and sub-goals of the attack. You can use a hierarchical diagram to represent your attack tree, or you can use a simple outline. What is important is that you construct something that portrays the attack profile of your application. Then you can evaluate security risks and use the appropriate countermeasures to mitigate them, such as correcting a design approach, hardening a configuration setting, and other solutions.
What is attack tree?
An attack tree is a way of identifying and documenting the potential attacks on your system in a structured and hierarchical manner.
Why do developers use trees?
Developers can use the trees to make informed coding decisions during implementation.
