What Is Considered a Breach of HIPAA?
What are the most common HIPAA breaches?
Why is HIPAA important?
What is HIPAA law?
Why is auditing important?
Why do hospitals need password protected databases?
What is a better text for CT scan?
See 2 more

How do I know if HIPAA has been violated?
Often employers will identify employees who have caused HIPAA violations. Employees who realize they may have violated HIPAA Rules will often self-report. They will also report potential violations made by their coworkers. The HHS Office for Civil Rights is the primary enforcer of HIPAA Rules.
What qualifies as a HIPAA breach?
A breach is, generally, an impermissible use or disclosure under the Privacy Rule that compromises the security or privacy of the protected health information.
What are the 3 types of HIPAA violations?
Types of HIPAA ViolationsNo "Right to Revoke" Clause. ... Release of the Wrong Patient's Information. ... Release of Unauthorized Health Information. ... Missing Patient Signature on HIPAA Forms. ... Improper Disposal of Patient Records. ... Failure to Promptly Release Information to Patients.
What is not considered a HIPAA breach?
If your information is shared accidentally, then it is not considered a breach. For example, say an administrator emailed a person's PHI to another person unintentionally. That email would not be considered a breach if the administrator can prove that it was accidental and it didn't happen repeatedly.
What is the most common HIPAA breach?
Failing to Secure and Encrypt Data Perhaps the most common of all HIPAA violations is the failure to properly secure and encrypt data. In part, this is because there are so many different ways for this to happen.
What are the 5 most common violations to the HIPAA privacy Rule?
Lack of safeguards of protected health information. Lack of patient access to their protected health information. Lack of administrative safeguards of electronic protected health information. Use or disclosure of more than the minimum necessary protected health information.
What happens when a person violates HIPAA?
Failure to comply with HIPAA can also result in civil and criminal penalties. If a complaint describes an action that could be a violation of the criminal provision of HIPAA, OCR may refer the complaint to the Department of Justice (DOJ) for investigation.
Is Googling a patient a HIPAA violation?
Googling your patients does not violate HIPAA. You are acting as an observer of information rather than posting a patient's information online yourself. Regardless of the fact that doing some online research into your patients' pasts isn't technically illegal, it still should not be taken lightly.
Does talking about a patient violate HIPAA?
Maybe you missed this lesson, but talking about patients without a purpose or to an unauthorized person is never okay. Even if you mean no harm or don't think the patient will ever find out, it still violates the person's privacy.
What are some examples of how HIPAA can be violated?
Most Common HIPAA Violation Examples1) Lack of Encryption. ... 2) Getting Hacked OR Phished. ... 3) Unauthorized Access. ... 4) Loss or Theft of Devices. ... 5) Sharing Information. ... 6) Disposal of PHI. ... 7) Accessing PHI from Unsecured Location.
Can you be fired for accidentally breaking HIPAA?
Depending on the nature of the violation, the incident may warrant disciplinary action against the individual concerned which could see the employee suspended pending an investigation. Termination for a HIPAA violation is a possible outcome.
Is breaking HIPAA a crime?
According to the U.S. Department of Health and Human Services Office for Civil Rights (OCR): A person who knowingly obtains or discloses individually identifiable health information in violation of the Privacy Rule may face a criminal penalty of up to $50,000 and up to one-year imprisonment.
What are the 4 most common HIPAA violations?
5 Most Common HIPAA ViolationsThe 5 Most Common HIPAA Violations.HIPAA Violation 1: A Non-Encrypted Lost or Stolen Device. ... HIPAA Violation 2: Lack of Employment Training. ... HIPAA Violation 3: Database Breaches. ... HIPAA Violation 4: Gossiping and Sharing PHI. ... HIPAA Violation 5: Improper disposal of PHI.
What is considered to be a data breach?
What is a personal data breach? A personal data breach means a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorised disclosure of, or access to, personal data. This includes breaches that are the result of both accidental and deliberate causes.
Home - Centers for Medicare & Medicaid Services | CMS
Home - Centers for Medicare & Medicaid Services | CMS
What is a HIPAA violation? 26 HIPAA violation examples - Alleva
1. Employees Divulging Patient Information. Patient information needs to be kept private. Employees talking about patients to coworkers or friends is a HIPAA violation that can land you in a world of hurt.
What Happens if You Break HIPAA Rules? 2022 Update
Author: Steve Alder is the editor-in-chief of HIPAA Journal. Steve is responsible for editorial policy regarding the topics covered on HIPAA Journal. He is a specialist on healthcare industry legal and regulatory affairs, and has several years of experience writing about HIPAA and other related legal topics.
Examples of HIPAA Violations and Common Scenarios - YourDictionary
Examples of Employer HIPAA Violations. While employers don't provide healthcare, they do handle documentation related to group health insurance and medical records employees authorize their doctors to provide to the company for specific purposes (excused abscesses, Family Medical Leave (FML) documentation or disability accommodation requests).
What Compromised Information Constitutes a HIPAA Breach?
Q. The Code of Federal Regulations, specifically 45 CFR 160.103, defines protected health information (PHI). Is the following information PHI? A practice sends a patient a letter that includes the patient's name and address, patient number, admission date, account balance, and the practice's name; alternatively, the practice sends a letter that includes the patient's name and date of birth ...
What is covered entity?
Covered entities and business associates, as applicable, have the burden of demonstrating that all required notifications have been provided or that a use or disclosure of unsecured protected health information did not constitute a breach. Thus, with respect to an impermissible use or disclosure, a covered entity (or business associate) should maintain documentation that all required notifications were made, or, alternatively, documentation to demonstrate that notification was not required: (1) its risk assessment demonstrating a low probability that the protected health information has been compromised by the impermissible use or disclosure; or (2) the application of any other exceptions to the definition of “breach.”
What is unsecured health information?
Unsecured protected health information is protected health information that has not been rendered unusable, unreadable, or indecipherable to unauthorized persons through the use of a technology or methodology specified by the Secretary in guidance.
What is breach in health care?
A breach is, generally, an impermissible use or disclosure under the Privacy Rule that compromises the security or privacy of the protected health information. An impermissible use or disclosure of protected health information is presumed to be a breach unless the covered entity or business associate, as applicable, ...
How to notify a covered entity of a breach of unsecured health information?
Covered entities must notify affected individuals following the discovery of a breach of unsecured protected health information. Covered entities must provide this individual notice in written form by first-class mail, or alternatively, by e-mail if the affected individual has agreed to receive such notices electronically. If the covered entity has insufficient or out-of-date contact information for 10 or more individuals, the covered entity must provide substitute individual notice by either posting the notice on the home page of its web site for at least 90 days or by providing the notice in major print or broadcast media where the affected individuals likely reside. The covered entity must include a toll-free phone number that remains active for at least 90 days where individuals can learn if their information was involved in the breach. If the covered entity has insufficient or out-of-date contact information for fewer than 10 individuals, the covered entity may provide substitute notice by an alternative form of written notice, by telephone, or other means.
What is HIPAA breach notification?
The HIPAA Breach Notification Rule, 45 CFR §§ 164.400-414, requires HIPAA covered entities and their business associates to provide notification following a breach of unsecured protected health information. Similar breach notification provisions implemented and enforced by the Federal Trade Commission (FTC), apply to vendors of personal health records and their third party service providers, pursuant to section 13407 of the HITECH Act.
How long does a business associate have to notify the covered entity of a breach?
A business associate must provide notice to the covered entity without unreasonable delay and no later than 60 days from the discovery of the breach.
What information should a business associate provide to the covered entity?
To the extent possible, the business associate should provide the covered entity with the identification of each individual affected by the breach as well as any other available information required to be provided by the covered entity in its notification to affected individuals.
What if Law Enforcement Delays Breach Notification?
In some situations, law enforcement may ask you to delay sending breach notifications because it may impede a criminal investigation, hinder national security, or harm your organization or a BA. Pay attention to how the delay request is delivered by law enforcement.
How to notify a person of a PHI breach?
You must notify all individuals whose PHI was compromised in the breach no later than 60 days after discovering the breach. Send a notification letter by first-class mail to the last known address, or send an email if the individual has previously agreed to electronic communication . If your records show that the person is ...
What is HIPAAtrek breach notification log?
Use HIPAAtrek’s Breach Notification Log to keep track of your breach mitigation and notification efforts.
What is breach notification?
Additionally, the breach notification rule applies to business associates (BA). When a BA discovers a breach, they should notify you or conduct a breach risk assessment, depending on your business associate agreement (BAA). The first day a BA knows of a breach – or would have known of the breach if they’d exercised reasonable diligence – is considered the day the breach is discovered. The breach must be known to anyone other than the person who caused it, including an employee, officer, or other agent of the BA.
How long do you have to notify the media of a breach?
You’ll send the media the same information that you sent to individuals in their notification letters no later than 60 days after discovering the breach. Be as prompt as possible.
What happens if you can't send a notification letter?
If you have insufficient or outdated contact information and can’t mail a written notification letter to some individuals, then you’ll need to make a substitute notice. The type of notice depends on how many people you’re unable to send a notification letter to.
What is the first day a BA knows of a breach?
The first day a BA knows of a breach – or would have known of the breach if they’d exercised reasonable diligence – is considered the day the breach is discovered. The breach must be known to anyone other than the person who caused it, including an employee, officer, or other agent of the BA. If the BA is not an agent of your organization, then ...
What is a breach?
A “breach” is defined as the “acquisition, access, use or disclosure of PHI” in violation of the HIPAA Privacy Rule (PDF, 1.52MB). Examples of a breach include: stolen or improperly accessed PHI, PHI inadvertently sent to the wrong provider and unauthorized viewing of PHI by an employee in your practice. PHI is “unsecured” if it is not encrypted to government standards. Conversely, if you lose PHI that has been encrypted to government standards, there is no breach.
What do I do if I learn of or suspect a breach?
The first step if you discover or suspect a breach is to conduct the required risk assessment. (You must take this step even if the breached PHI was secured through encryption. See related sidebar on encryption.)
Why is PHI protected?
The risks associated with breaches of unsecured protected health information (PHI) provide a powerful incentive to use increasingly affordable encryption technology. If you suffer a breach and the PHI is properly encrypted, you are spared the trouble and embarrassment of giving breach notification. More importantly, your patient’s privacy is protected because it is very difficult to crack encryption.
What are some examples of PHI breaches?
Examples of a breach include: stolen or improperly accessed PHI, PHI inadvertently sent to the wrong provider and unauthorized viewing of PHI by an employee in your practice. PHI is “unsecured” if it is not encrypted to government standards. Conversely, if you lose PHI that has been encrypted to government standards, there is no breach.
How long do you have to notify a patient of a breach of confidentiality?
If notice is required, you must notify any patient affected of a breach without unreasonable delay, meaning within 60 days ( or the limit specified by state law) of discovery.
How to contact a patient with a breach notice?
You must provide written notice to the patient at the patient’s last known address by first-class mail. Alternatively, you can contact your patients by email if they have indicated that this is the preferred manner of contact. A breach notice could alert a patient’s spouse or other family members to the fact that the patient is receiving mental health treatment even though the patient did not want this fact disclosed to family members. To help minimize this possibility, it is advisable to discuss with patients the physical or email address where they would prefer to be contacted in the unlikely event that you have to send a breach notice.
What happens if you send a PHI to a colleague?
For example, if you send the wrong patient’s PHI to a psychologist colleague for consultation, it should be easy to obtain written confirmation from the colleague that they have properly deleted or destroyed the PHI as soon as they realized you sent information on the wrong patient. By contrast, if your laptop is stolen you have little assurance that the thief will respect your patient’s confidentiality.
What is the best plan for HIPAA compliance?
Needless to say, the best plan is to secure your patients’ health and credit information, properly implement a HIPAA Compliance Plan, encrypt all digital data, and properly train your staff on their responsibilities. This is cheaper and more effective than trying to mitigate a Breach after the fact, and can save you many headaches down the road.
How long does it take to notify HHS of a breach?
According to HIPAA, if you have a Breach of over 500 patients’ information, you are required to notify HHS and local media outlets, plus post information about the Breach to your website in a conspicuous place within 60 days of discovering the Breach. There is a form on HHS’s website to do this.
How long does a breach of credit last?
Many groups that experience a Breach will offer their patients 1 year of credit monitoring service. This can be an expensive undertaking, but losing their good will, or even losing them as patients, can be much more expensive!
Do you have to notify HHS of a breach?
You do not have to notify local media and HHS at the time of the Breach, but are required to submit an accounting of the Breach to HHS at the end of the calendar year. You can submit your report online here.
Who do you notify if you are in California?
If you are in the State of California, or have any patients from the State, you must also notify the California Attorney General’s Office.
How long does a covered entity have to notify the Secretary of Health?
If a breach of unsecured protected health information affects fewer than 500 individuals, a covered entity must notify the Secretary of the breach within 60 days of the end of the calendar year in which the breach was discovered. (A covered entity is not required to wait until the end of the calendar year to report breaches affecting fewer than 500 individuals; a covered entity may report such breaches at the time they are discovered.) The covered entity may report all of its breaches affecting fewer than 500 individuals on one date, but the covered entity must complete a separate notice for each breach incident. The covered entity must submit the notice electronically by clicking on the link below and completing all of the fields of the breach notification form.
What is covered entity notification?
A covered entity must notify the Secretary if it discovers a breach of unsecured protected health information. See 45 C.F.R. § 164.408. All notifications must be submitted to the Secretary using the Web portal below.
How many individuals are affected by a breach notification?
A covered entity’s breach notification obligations differ based on whether the breach affects 500 or more individuals or fewer than 500 individuals . If the number of individuals affected by a breach is uncertain at the time of submission, the covered entity should provide an estimate, and, if it discovers additional information, submit updates in the manner specified below. If only one option is available in a particular submission category, the covered entity should pick the best option, and may provide additional details in the free text portion of the submission.
How many individuals can a covered entity report?
The covered entity may report all of its breaches affecting fewer than 500 individuals on one date, but the covered entity must complete a separate notice for each breach incident.
How to contact HHS OCR?
If you have any questions, you may call HHS OCR toll-free at: 1-800-368-1019, TDD: 1-800-537-7697 or send an email to [email protected]. Content created by Office for Civil Rights (OCR) Content last reviewed on January 5, 2015.
Are Data Breaches HIPAA Violations?
Data breaches are now a fact of life. Even with multi-layered cybersecurity defenses, data breaches are still likely to occur from time to time. OCR understands that healthcare organizations are being targeted by cybercriminals and that it is not possible to implement impregnable security defenses.
What are the 10 Most Common HIPAA Violations?
Listed below are 10 of the most common HIPAA violations, together with examples of HIPAA-covered entities and business associates that have been discovered to be in violation of HIPAA Rules and have had to settle those violations with OCR and state attorneys general. In many cases, investigations have uncovered multiple HIPAA violations. The settlement amounts reflect the seriousness of the violation, the length of time the violation has been allowed to persist, the number of violations identified, and the financial position of the covered entity/business associate.
What happens if you don't do a risk analysis?
The failure to perform an organization-wide risk analysis is one of the most common HIPAA violations to result in a financial penalty. If the risk analysis is not performed regularly, organizations will not be able to determine whether any vulnerabilities to the confidentiality, integrity, and availability of PHI exist.
What are the most common HIPAA violations that have resulted in financial penalties?
The most common HIPAA violations that have resulted in financial penalties are the failure to perform an organization-wide risk analysis to identify risks to the confidentiality, integrity, and availability of protected health information (PHI); the failure to enter into a HIPAA-compliant business associate agreement; impermissible disclosures of PHI; delayed breach notifications; and the failure to safeguard PHI.
Why is it important for HIPAA-covered entities to conduct regular HIPAA compliance reviews?
It is therefore important for HIPAA-covered entities to conduct regular HIPAA compliance reviews to make sure HIPAA violations are discovered and corrected before they are identified by regulators.
What is the HIPAA right of access?
The HIPAA Privacy Rule gives patients the right to access their medical records and obtain copies on request. This allows patients to check their records for errors and share them with other entities and individuals. Denying patients copies of their health records, overcharging for copies, or failing to provide those records within 30 days is a violation of HIPAA. OCR made HIPAA Right of Access violations one of its key enforcement objectives in late 2019.
What is a violation of HIPAA?
Accessing the health records of patients for reasons other than those permitted by the Privacy Rule – treatment, payment, and healthcare operations – is a violation of patient privacy. Snooping on healthcare records of family, friends, neighbors, co-workers, and celebrities is one of the most common HIPAA violations committed by employees. When discovered, these violations usually result in termination of employment but could also result in criminal charges for the employee concerned. Financial penalties for healthcare organizations that have failed to prevent snooping are relatively uncommon, but they are possible as University of California Los Angeles Health System discovered.
How long did Presense Health take to settle a HIPAA breach?
Presense Health took three months from the discovery of the breach to issue notifications – A delay that cost the health system $475,000. The maximum penalty for a HIPAA Breach Notification Rule violation is $1,500,000, or more if the delay is for more than 12 months.
How long does it take to report a breach of HIPAA?
Any breach of unsecured protected health information must be reported to the covered entity within 60 days of the discovery of a breach. While this is the absolute deadline, business associates must not delay notification unnecessarily. Unnecessarily delaying notifications is a violation of the HIPAA Breach Notification Rule.
How long does it take to notify HHS of a breach?
When the breach has impacted more than 500 individuals, the maximum permitted time for issuing the notification to the HHS is 60 days from the discovery of the breach, although breach notices should be issued without unnecessary delay. In the case of breaches impacting fewer than 500 individuals, HIPAA breach notification requirements are for notifications to be issued to the HHS within 60 days of the end of the calendar year in which the breach was discovered.
What is required for HIPAA breach notification?
The HIPAA breach notification requirements for letters include writing in plain language, explaining what has happened, what information has been exposed/stolen, providing a brief explanation of what the covered entity is doing/has done in response to the breach to mit igate harm, providing a summary of the actions that will be taken to prevent future breaches, and giving instructions on how breach victims can limit harm. Breach victims should also be provided with a toll-free number to contact the breached entity for further information, together with a postal address and an email address.
How long does it take to get a breach notification letter?
Breach notification letters must be sent within 60 days of the discovery of a breach unless a request to delay notifications has been made by law enforcement. In such cases, notifications should be sent ...
What is a breach in HIPAA?
A breach is defined as the acquisition, access, use, or disclosure of protected health information in a manner not permitted by HIPAA Rules. According to the HHS´ guidance on the HIPAA Breach Notification Rule, an impermissible use or disclosure of protected health information is presumed to be a breach unless the covered entity or business ...
How long does a breach notice stay on a website?
The link to the breach notice should be displayed prominently and should remain on the website for a period of 90 consecutive days. In cases where fewer than 10 individuals’ contact information is not up-to-date, alternative means can be used for the substitute notice, such as a written notice or notification by telephone.
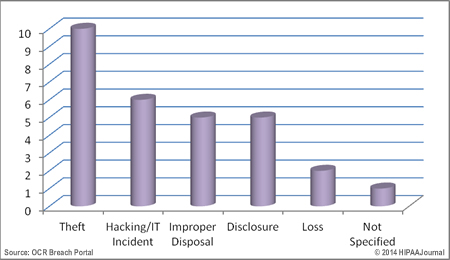
What Is Considered a Breach of HIPAA?
The law passed in 1996 stated that the HIPAA breach definition meant either purposefully or accidentally sharing or not safeguarding patient information. There are several ways considered to breach HIPAA. Here is a list of 10 of the most common breaches:
What are the most common HIPAA breaches?
The law passed in 1996 stated that the HIPAA breach definition meant either purposefully or accidentally sharing or not safeguarding patient information. There are several ways considered to breach HIPAA. Here is a list of 10 of the most common breaches: 1 Staff who are not authorized to access patient health information 2 Impermissible disclosure of patient health information 3 Failure to manage risks 4 Failure to properly document training to ensure compliance 5 Theft of patient information from the records 6 Failure to provide patients with their own information and records 7 Not monitoring who accesses medical information 8 Not encrypting devices that leave the facility with staff 9 Sharing personal health information online such as social media or to the press 10 Not removing access credentials for employees no longer working for you
Why is HIPAA important?
You also don’t want to make the news due to a cybersecurity breach.
What is HIPAA law?
History of the HIPAA Laws. Long before the Affordable Care Act, healthcare reform in 1996 meant the passing of the congress bill known as HIPAA, or Healthcare Insurance Portability and Accountability Act. This act had multiple facets including the idea that your healthcare insurance should be portable and that individuals could keep their ...
Why is auditing important?
An audit is a good way to see where your possible gaps are before you accidentally breach any patient information. Our risk assessment team can help show you where you can improve and where your team members need extra training.
Why do hospitals need password protected databases?
Now, healthcare providers and insurance providers must have encrypted and password safeguards in place to ensure their patients’ information is private.
What is a better text for CT scan?
If you must get information in this way about a specific patient there can’t be any specific information included, a better text would be “Patient A.B. CT scan returned positive.” If this text were intercepted or seen by someone other than yourself it doesn’t give any specific patient information.
