
What are the methods of encryption?
The Methods of Encryption
- Elliptic Curve Cryptography (ECC)
- RSA
- ElGamal Encryption
- Exponential Key Exchange
- Twofish
- Triple DES
- Advanced Encryption Standard (AES)
- Blowfish
What is the best encryption software for Windows 10?
What Are The Best Encryption Software To Protect Your Privacy
- AxCrypt. With more than 20 million downloads worldwide, AxCrypt ranks among the best free file encryption software for Windows, Mac, Android, and iOS devices.
- CertainSafe. CertainSafe is undoubtedly one of the best encryption software for Windows in 2021. ...
- CryptoExpert 8. ...
- Folder Lock. ...
- VeraCrypt. ...
- Dekart Private Disk. ...
- DiskCryptor. ...
- Gpg4win. ...
- Bitlocker. ...
- Encrypto. ...
What is standard encryption method?
Well-known symmetric encryption methods include the now-outdated Data Encryption Standard (DES) and its successor, the Advanced Encryption Standard (AES). Data Encryption Standard (DES) DES is a symmetric encryption method that was developed by IBM in the 1970s and standardized in 1977 by the US National Institute of Standards and Technology (NIST).
What is HIPAA encryption?
In conclusion, HIPAA encryption is an important means of protecting sensitive data – necessary to remain compliant with HIPAA regulations. If you are involved in working with electronically protected health information, then knowing what type and strength of HIPAA encryption to use in different circumstances is vital to maintaining the appropriate protections.
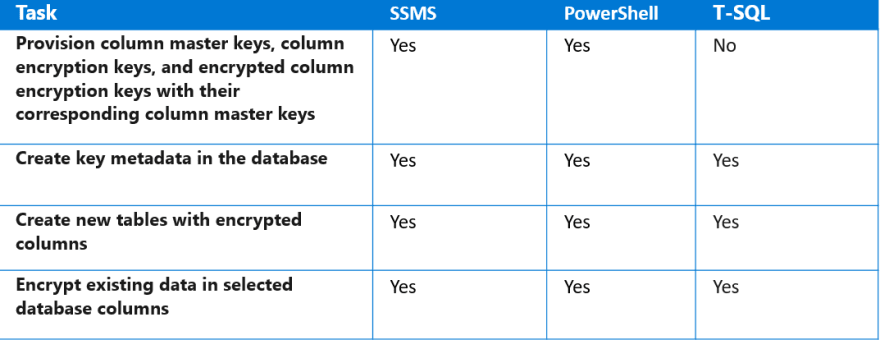
What encryption is used for database?
The four major types of database encryption are: Business Application Encryption (BA), DBMS Application Encryption (DA), DBMS Package Encryption (DP), and DBMS Engine Encryption (DE). Each database encryption takes place at separate layers and often have different functionality and requirements.
What are three methods of database encryption?
There are several data encryption approaches available to choose from. Most internet security (IS) professionals break down encryption into three distinct methods: symmetric, asymmetric, and hashing.
How do you implement database encryption in database?
There are different methods of database encryption possible:Transparent encryption: Encrypts stored data at the database level.Column-level encryption: Allows for each column within a database table to have a unique decryption key.Symmetric encryption: Uses one private key to decrypt data retrieved from the database.More items...
What are two ways to encrypt data in a database?
Symmetric and asymmetric database encryption This private key alters the data in a way that causes it to be unreadable without first being decrypted.
What are the 4 basic types of encryption systems?
While the most common are AES, RSA, and DES, there are other types being used as well. Let's dive into what these acronyms mean, what encryption is, and how to keep your online data safe.
What are the 2 types of data encryption?
There are two types of encryption in widespread use today: symmetric and asymmetric encryption. The name derives from whether or not the same key is used for encryption and decryption.
How do I know if my database is encrypted?
You can query the sys. dm_exec_connections dynamic management view (DMV) to see if the connections to your SQL Server is encrypted or not. If the value of encrypt_option is "TRUE" then your connection is encrypted.
What is the major issue with database encryption?
One major issue of having encryption is that if someone loses the decryption key, that would mean big trouble. You can relate that it is much the same as having a password, but it is treated as a global key to decrypt all the encrypted data.
Are SQL databases encrypted?
Transparent data encryption (TDE) encrypts SQL Server, Azure SQL Database, and Azure Synapse Analytics data files. This encryption is known as encrypting data at rest. To help secure a database, you can take precautions like: Designing a secure system.
What are the disadvantages of database encryption?
Data Encryption Cons The more data encryption keys there are the more difficult IT administrative tasks for maintaining all of the keys can be. If you lose the key to the encryption, you have lost the data associated with it.
Can encrypted data be hacked?
Encrypted data can be hacked or decrypted with enough time and computing resources, revealing the original content. Hackers prefer to steal encryption keys or intercept data before encryption or after decryption. The most common way to hack encrypted data is to add an encryption layer using an attacker's key.
What is the method of encryption?
Encryption is the method by which information is converted into secret code that hides the information's true meaning. The science of encrypting and decrypting information is called cryptography. In computing, unencrypted data is also known as plaintext, and encrypted data is called ciphertext.
What are different encryption algorithms?
Common Encryption AlgorithmsTriple DES. Triple DES was designed to replace the original Data Encryption Standard (DES) algorithm, which hackers eventually learned to defeat with relative ease. ... AES. ... RSA Security. ... Blowfish. ... Twofish.
What is symmetric and asymmetric encryption?
Symmetric encryption uses a single key that needs to be shared among the people who need to receive the message while asymmetric encryption uses a pair of public key and a private key to encrypt and decrypt messages when communicating.
Which of the following type of encryption is more secure in SQL?
Microsoft SQL Server customers should choose the AES encryption algorithm when encrypting SQL Server databases with Transparent Data Encryption (TDE) or Cell Level Encryption (CLE). While other standard methods such as Triple DES are available, using AES is recommended for better ongoing compliance.
What is database encryption?
Database encryption can generally be defined as a process that uses an algorithm to transform data stored in a database into " cipher text " that is incomprehensible without first being decrypted. It can therefore be said that the purpose of database encryption is to protect the data stored in a database from being accessed by individuals with potentially "malicious" intentions. The act of encrypting a database also reduces the incentive for individuals to hack the aforementioned database as "meaningless" encrypted data is of little to no use for hackers. There are multiple techniques and technologies available for database encryption, the most important of which will be detailed in this article.
What is transparent data encryption?
Transparent data encryption (often abbreviated as TDE) is used to encrypt an entire database, which therefore involves encrypting " data at rest ". Data at rest can generally be defined as "inactive" data that is not currently being edited or pushed across a network. As an example, a text file stored on a computer is "at rest" ...
What is EFS in database?
Encrypting File System (EFS) It is important to note that traditional database encryption techniques normally encrypt and decrypt the contents of a database. Databases are managed by "Database Management Systems" (DBMS) that run on top of an existing operating system (OS).
How does asymmetric encryption work?
Asymmetric encryption expands on symmetric encryption by incorporating two different types of keys into the encryption method: private and public keys. A public key can be accessed by anyone and is unique to one user whereas a private key is a secret key that is unique to and only known by one user. In most scenarios the public key is the encryption key whereas the private key is the decryption key. As an example, if individual A would like to send a message to individual B using asymmetric encryption, he would encrypt the message using Individual B's public key and then send the encrypted version. Individual B would then be able to decrypt the message using his private key. Individual C would not be able to decrypt Individual A's message, as Individual C's private key is not the same as Individual B's private key. Asymmetric encryption is often described as being more secure in comparison to symmetric database encryption given that private keys do not need to be shared as two separate keys handle encryption and decryption processes. For performance reasons, asymmetric encryption is used in Key management rather than to encrypt the data which is usually done with symmetric encryption.
Why is column level encryption important?
In order to explain column-level encryption it is important to outline basic database structure. A typical relational database is divided into tables that are divided into columns that each have rows of data. Whilst TDE usually encrypts an entire database, column-level encryption allows for individual columns within a database to be encrypted. It is important to establish that the granularity of column-level encryption causes specific strengths and weaknesses to arise when compared to encrypting an entire database. Firstly, the ability to encrypt individual columns allows for column-level encryption to be significantly more flexible when compared to encryption systems that encrypt an entire database such as TDE. Secondly, it is possible to use an entirely unique and separate encryption key for each column within a database. This effectively increases the difficulty of generating rainbow tables which thus implies that the data stored within each column is less likely to be lost or leaked. The main disadvantage associated with column-level database encryption is speed, or a loss thereof. Encrypting separate columns with different unique keys in the same database can cause database performance to decrease, and additionally also decreases the speed at which the contents of the database can be indexed or searched.
How is hashing used in database?
Hashing is used in database systems as a method to protect sensitive data such as passwords; however it is also used to improve the efficiency of database referencing. Inputted data is manipulated by a hashing algorithm. The hashing algorithm converts the inputted data into a string of fixed length that can then be stored in a database. Hashing systems have two crucially important characteristics that will now be outlined. Firstly, hashes are "unique and repeatable". As an example, running the word "cat" through the same hashing algorithm multiple times will always yield the same hash, however it is extremely difficult to find a word that will return the same hash that "cat" does. Secondly, hashing algorithms are not reversible. To relate this back to the example provided above, it would be nearly impossible to convert the output of the hashing algorithm back to the original input, which was "cat". In the context of database encryption, hashing is often used in password systems. When a user first creates their password it is run through a hashing algorithm and saved as a hash. When the user logs back into the website, the password that they enter is run through the hashing algorithm and is then compared to the stored hash. Given the fact that hashes are unique, if both hashes match then it is said that the user inputted the correct password. One example of a popular hash function is SHA (Secure Hash Algorithm) 256.
Why is EFS not used?
Due to the issues concerning performance, EFS is not typically used in databasing applications that require frequent database input and output. In order to offset the performance issues it is often recommended that EFS systems be used in environments with few users.
What is database encryption?
Database encryption for business security. Whether large or small, customers of every size may very well be dealing with sensitive data—data that, in many cases, may be subject to regulations. This data might include credit cards, Social Security numbers, classified information, or medical records.
Why is encryption important in a database?
This is crucial because if a system is breached, the data is still only readable for users who have the right encryption keys. There are a few different options for implementing a database encryption algorithm, including varying lengths of keys.
What is TDE in database?
TDE Method: Transparent data encryption (TDE) executes encryption and decryption within the database engine itself. This method doesn’t require code modification of the database or application and is easier for admins to manage. Since it’s a particularly popular method of database encryption, TDE is explored in further detail below.
What is API method?
API Method: This is application-level encryption that is appropriate across any database product (Oracle, MSSQL, etc). Queries within the encrypted columns are modified within the application, requiring hands-on work. If a business has an abundance of data, this can be a time-consuming approach. Additionally, encryption that functions at the application level can lead to increased performance issues.
Why is TDE encryption transparent?
This type of encryption is “transparent” because it is invisible to users and applications that are drawing on the data and is easily used without making any application-level changes. It is decrypted for authorized users or applications when in use but remains protected at rest. Even if the physical media is compromised or the files stolen, the data as a whole remains unreadable—only authorized users can successfully read the data. This provides a disincentive for hackers to steal the data at all. When all is said and done, using TDE can help a business remain in compliance with a range of specific security regulations.
How many bits does 3DES have?
3DES: Triple Data Encryption is another block cipher. It utilizes three 56-bit keys to encrypt data three times, resulting in a 168-bit key. This option is fairly secure, but also slower due to the multiple encryptions. While currently in place for a number of businesses, 3DES likely won’t last much longer as a standard.
What is transparent data encryption?
The term transparent data encryption, or “external encryption,” refers to encryption of an entire database, including backups. This is a method specifically for “data at rest” in tables and tablespaces—that is, inactive data that isn’t currently in use or in transit.
Why is encryption important?
Encryption is essential to help protect your sensitive personal information. But in the case of ransomware attacks, it can be used against you. It’s smart to take steps to help you gain the benefits and avoid the harm.
What is encryption in computer science?
Encryption is the process that scrambles readable text so it can only be read by the person who has the secret code, or decryption key. It helps provide data security for sensitive information.
What are the two types of encryption?
There are two types of encryption systems: symmetric encryption and asymmetric encryption. Here’s how they’re different.
What is encryption in text?
Encryption is the process of taking plain text, like a text message or email, and scrambling it into an unreadable format — called “cipher text.” This helps protect the confidentiality of digital data either stored on computer systems or transmitted through a network like the internet.
What is encryption on fitness watch?
Start Free Trial. Encryption can help protect data you send, receive, and store, using a device. That can include text messages stored on your smartphone, running logs saved on your fitness watch, and banking information sent through your online account. Encryption is the process that scrambles readable text so it can only be read by ...
Why is it important to keep security software up to date?
Keep your security software up to date. It can help protect your devices against cyberattacks.
When was the Data Encryption Standard established?
Data Encryption Standard is considered a low-level encryption standard. The U.S. government established the standard in 1977. Due to advances in technology and decreases in the cost of hardware, DES is essentially obsolete for protecting sensitive data.

Overview
Field-level encryption
Experimental work is being done on providing database operations (like searching or arithmetical operations) on encrypted fields without the need to decrypt them. Strong encryption is required to be randomized - a different result must be generated each time. This is known as probabilistic encryption. Field-level encryption is weaker than randomized encryption, but it allows users to test for equality without decrypting the data.
Transparent/External database encryption
Transparent data encryption (often abbreviated as TDE) is used to encrypt an entire database, which therefore involves encrypting "data at rest". Data at rest can generally be defined as "inactive" data that is not currently being edited or pushed across a network. As an example, a text file stored on a computer is "at rest" until it is opened and edited. Data at rest are stored on physical storage media solutions such as tapes or hard disk drives. The act of storing large amo…
Column-level encryption
In order to explain column-level encryption it is important to outline basic database structure. A typical relational database is divided into tables that are divided into columns that each have rows of data. Whilst TDE usually encrypts an entire database, column-level encryption allows for individual columns within a database to be encrypted. It is important to establish that the granularity of column-level encryption causes specific strengths and weaknesses to arise when compared to …
Filesystem-level encryption
It is important to note that traditional database encryption techniques normally encrypt and decrypt the contents of a database. Databases are managed by "Database Management Systems" (DBMS) that run on top of an existing operating system (OS). This raises a potential security concern, as an encrypted database may be running on an accessible and potentially vulnerable operating system. EFS can encrypt data that is not part of a database system, which implies tha…
Full disk encryption
BitLocker does not have the same performance concerns associated with EFS.
Symmetric and asymmetric database encryption
Symmetric encryption in the context of database encryption involves a private key being applied to data that is stored and called from a database. This private key alters the data in a way that causes it to be unreadable without first being decrypted. Data is encrypted when saved, and decrypted when opened given that the user knows the private key. Thus if the data is to be shared through a …
Key management
The "Symmetric & Asymmetric Database Encryption" section introduced the concept of public and private keys with basic examples in which users exchange keys. The act of exchanging keys becomes impractical from a logistical point of view, when many different individuals need to communicate with each-other. In database encryption the system handles the storage and exchange of keys. This process is called key management. If encryption keys are not managed a…