
Encase is traditionally used in forensics to recover evidence from seized hard drives. Encase allows the investigator to conduct in depth analysis of user files to collect evidence such as documents, pictures, internet history and Windows Registry
Windows Registry
The Windows Registry is a hierarchical database that stores low-level settings for the Microsoft Windows operating system and for applications that opt to use the Registry. The kernel, device drivers, services, Security Accounts Manager (SAM), and user interface can all use the Registry…
How to install and run encase forensics?
Step 4 – Attach your enCase dongle to the system. Light should blink on your dongle. Step 5 – Run enCase forensic software. Now you should have a full featured interface with all the respective functionalities enabled. Key Points to remember – 1. enCase will identify the hardware dongle / token on normal system running windows
How to use EnCase Forensic imager in a real case?
How to use EnCase Forensic Imager in a Real Case. For digital forensic investigators looking to extract evidence from a hard drive, here is a brief summary of the process. Evidence extraction process: Open EnCase Imager and choose 'Add Local Device' Uncheck 'Only Show Write-Blocked' (keep all other options checked).
How to use "encase" in a sentence?
When to Use Incase
- When Bramford pulled his ham from the oven, it was encased in a charred husk of blackened skin.
- Encased in its hard chrysalis, the larva underwent metamorphosis to become an adult butterfly.
- It doesn’t help that FedEx Corp. and United Parcel Service Inc. ...
How do I access EnCase forensic image file?
The following step by step procedure need to be performed to open and view EnCase image:
- First of all, you need to Download and Install E01 Viewer on the Desktop
- Now, select the Scan option and you will be provided three options i.e. EDB, OST & PST for scanning these Files. ...
- Then, click on the Browse button for where your .e01 image files are stored
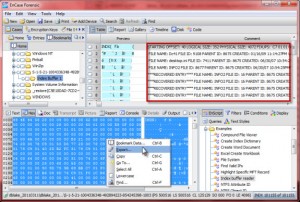
What does EnCase forensic software do?
EnCase® Forensic is the global standard in digital investigation technology for forensic practitioners who need to conduct efficient, forensically-sound data collection and investigations using a repeatable and defensible process.
What operating system does EnCase work on?
This latest version of EnCase runs on a variety of platforms, including Windows, Linux, and UNIX, and can read over 20 file systems, including TiVo file systems.
Is EnCase forensics open source?
EnCase Endpoint Security's integrated open-source toolkit strengthens and centralizes the incident response process with a robust set of integrations to various open source applications, combining the leading forensics and endpoint response platform with powerful, freely available, tools.
Is EnCase forensic free?
Is free to download and use. Requires no installation.
Why is EnCase used?
Encase is traditionally used in forensics to recover evidence from seized hard drives. Encase allows the investigator to conduct in depth analysis of user files to collect evidence such as documents, pictures, internet history and Windows Registry information. The company also offers EnCase training and certification.
What is EnCase endpoint investigator?
EnCase Endpoint Investigator provides investigators with seamless, remote access to laptops, desktops and servers ensuring that all investigation-relevant data is discreetly searched and collected in a forensically sound manner.
What is the difference between FTK and autopsy?
This is because FTK has stability issue and it crashes while processing and indexing of data. This makes FTK really slow as we can observe in the results. Autopsy is used for finding digital evidence while EnCase is used to process the evidence.
How do I recover deleted files from EnCase?
Right click on the file and click 'copy/unerase' to restore the document. Down in the bottom right hand corner you will see the progression of the copying to the chosen file destination. Find the extracted file and open it. It has now been restored.
What is EnCase safe?
EnCase SAFE is a server that is used to authenticate users, distribute licenses, provide forensic analysis tools, and communicate with target machines running the EnCase Servlet. EnCase Servlet runs locally on target machines and allows the EnCase SAFE to create an image from the target operating system.
What is autopsy tool?
“Autopsy® is a digital forensics platform and graphical interface to The Sleuth Kit® and other digital forensics tools. It is used by law enforcement, military, and corporate examiners to investigate what happened on a computer. You can even use it to recover photos from your camera's memory card.” — Official Website.
What is EnCase Enterprise?
EnCase® Enterprise delivers the most advanced forensic software with the broadest file type and OS support. With Version 7 you also get the most comprehensive encryption support, Passware integration for protected file detection, and Windows Event Log compatibility.
Is FTK open source?
FTK Imager is an open-source software by AccessData that is used for creating accurate copies of the original evidence without actually making any changes to it.
What evidence was found using Encase?
The incriminating evidence was found using EnCase. It discovered not only that the critical '1' had been deleted but also revealed who had removed it and – just as important – when. This case illustrates both the value of EnCase as an investigative tool and the importance of finding and protecting digital records as evidence.
When was Encase used in a murder?
In 2008, EnCase was used in another prominent homicide case: the murder of two-year old Caylee Anthony by her mother Casey. In this case, the killer's recovered search history revealed search queries for chloroform.
What is the first example of Encase's utility?
The first example of EnCase's utility involves a case of fraud.
How many PCs did Peterson use?
Investigators took away Peterson's five PCs and used EnCase to recover his internet search history. Amongst the incriminating evidence was a search for the tide times in the area where Laci's body was found. In 2005, EnCase was utilized to examine a floppy disk from serial killer Dennis Rader, dubbed the BTK strangler.
Thorough evidence collection
Acquire evidence from a variety of sources and dig deep into each source to uncover, collect and preserve potentially relevant information.
Customizable workflows
Improve investigation efficiency with optimized investigator workflows with predefined or customized conditions and filters to quickly locate evidence.
Comprehensive reporting
Provide the detailed evidence results other law enforcement personnel, attorneys and judges need to close cases faster.
What is an encase review package?
The EnCase Forensic Review Package lets you share findings with other people involved with your case, including detectives, district attorneys, field agents, and fellow investigators.
What is NSRL in encase?
The National Software Reference Library (NSRL) is provided in the EnCase hash library format, letting you easily de-NIST your potential evidence, eliminating thousands of known files from your evidence set.
How to increase confidence in your findings?
Increase confidence in your findings by using the proven, court-referenced digital forensics standard
Does Encase Forensic support OS?
No other product deliver s the broad file-type and operating-system ( OS) support of EnCase Forensic. With Version 7, you also get EnCase ® Decryption Suite, EnCase ® Physical Disk Emulator, EnCase ® Virtual File System, and EnCase ® FastBloc SE.
Can you use EnScripts to automate processes?
Now you can use custom EnScripts to automate common processes, which can greatly increase your efficiency. Template-driven processing results are consistent, providing easy-to-find, easy-to-use output.
Is Encase forensics the same as other products?
The powerful and efficient features of EnCase Forensic have made it the trusted standard in corporate and criminal investigations, as well as in courts around the world. No other product offers the same degree of functionality, court acceptance, and performance.
What is encase used for?
Encase is traditionally used in forensics to recover evidence from seized hard drives. Encase allows the investigator to conduct in depth analysis of user files to collect evidence such as documents, pictures, internet history and Windows Registry information. The company also offers EnCase training and certification.
What is Encase software?
EnCase is the shared technology within a suite of digital investigations products by Guidance Software ( now acquired by OpenText). The software comes in several products designed for forensic, cyber security, security analytics, and e-discovery use.
What is Encase file format?
EnCase contains functionality to create forensic images of suspect media. Images are stored in proprietary Expert Witness File format; the compressible file format is prefixed with case data information and consists of a bit -by-bit (i.e. exact) copy of the media inter-spaced with CRC hashes for every 64K of data. The file format also appends an MD5 hash of the entire drive as a footer.
When did Encase endpoint security come out?
In 2015 EnCase Endpoint Security was released which was the evolution of Endpoint Security into a more user friendly web interface as well as further integration with many other security tools to further expedite and shorten the response time from an attack or event.
When was Encase Enterprise released?
In 2002 EnCase Enterprise was released allowing the first network enabled digital forensic tool to be used in forensic, investigative, and security matters.
When was Encase created?
EnCase was originally created as Expert Witness by Andrew Rosen the founder of ASR Data in 1995 out of his home. In 1998 EnCase Forensic officially released (originally named Expert Witness for Windows). At the time there were no GUI forensic tools available.
Does Encase offer certification?
The company also offers EnCase training and certification.
Who makes Encase software?
All EnCase product line is developed and maintained by Guidance Software Inc. Guidance Software has been a leader in the forensics industry by providing robust tools and solutions for digital investigations which matches individuals and industries requirements. Guidance Software, Inc. was founded in 1997. Other than industrial purposes Guidance Software is used by legal as well as law enforcement personnel.
What is encase ediscovery?
The EnCase eDiscovery provides with continuous case assessment, an optimized process with the help of which, legal teams can quickly check necessary facts. Encase eDiscovery is designed for enterprise professionals, and provides the following:
How Does EnCase V8 work?
Encase v8 provides functionality to execute powerful analytic methods against evidence in a single automated session . While running this multi-threaded process, the Encase v8 optimizes the order and combinations of processing operations, ensuring the most efficient execution path is taken. The output of the Encase v8 is stored, per device, on disk, instead of memory, so that multiple devices can be processed simultaneously across several computers, and compiled into a case.
What is Encase Endpoint Security?
Encase Endpoint Security is created to merge the two separate industry processes, Incident Detection and Incident Prevention, to help security teams proactively address the gaps in their security process framework.
What is an investigation workflow?
Investigation Workflows: With a click an examiner can take a case from adding and processing evidence section to creating a report of findings. One of the important parts of an investigation depends on the ability of examiners to uncover evidences. Examiners can be rest assured that navigating EnCase Forensic would never slow down their progress.
How to mask data?
A commonly used technique for data masking is to rename a file and change the extension. Image files can be renamed so that they look like Windows DLL files. Signature analysis component verifies file type by comparing the file headers, or signature, with the file extension.
What is Enforce Risk Manager?
EnForce Risk Manager is a tool that provides solution for automatically identifying, categorizing, and remediating confidential data across the enterprise. Enforce risk manager gives in-depth insight and control to electronic data across all storage solution and devices like file shares, servers, and cloud repositories. This enables organizations to improve focus onto business intelligence, compliance and strengthen their security solution.
What is encase used for?
Encase is traditionally used in forensics to recover evidence from seized hard drives. Encase allows the investigator to conduct in depth analysis of user files to collect evidence such as documents, pictures, internet history and Windows Registry information. The company also offers EnCase training and certification.
Does Encase require a license?
EnCase Forensic Imager. Is a standalone product that does not require an EnCase Forensic license. Enables browsing and viewing of potential evidence files, including folder structures and file metadata. Uses strong AES 256-bit encryption to protect Lx01 and Ex01 files.
How does Encase Mobile Investigator work?
EnCase Mobile Investigator is designed with ease of use in mind: With intuitive evidence review, examiners can easily create a case and review parsed mobile device evidence , such as mobile app data, text messages, call records, internet history, e-mails, and cloud repositories associated with the widest variety of mobile devices. Once an acquisition is complete with EnCase Forensic or Endpoint Investigator, you can load that EnCase Mobile Acquisition (.ema) file into EnCase Mobile Investigator. When parsing is complete, you can begin analysis from categorized files and start putting pieces of the puzzle together. As you can see below, once you click on the thumbnail button, all graphic files will appear and you can easily bookmark any relevant evidence for your case. With EnCase Mobile Investigator, finding and gathering the evidence you need from a smartphone, smartwatch, tablet, or even drone, has never been easier.
What is Encase Endpoint Investigator 8.05?
Guidance Software (Now OpenText) has recently released EnCase® Forensic and EnCase Endpoint Investigator 8.05 supporting mobile device acquisitions in addition to the all-new EnCase Mobile Investigator, which offers powerful mobile data review and reporting capabilities for acquired mobile data.
Can an examiner access the cloud?
With an authentication key, (and the appropriate permissions), examiners can access a cloud account to retrieve critical evidence, such as e-mails or messages, that can be instrumental to a case closing. Over time, the use of digital evidence from the cloud in criminal and civil matters will continue to expand, ...
Can you bookmark a case with Encase?
As you can see below, once you click on the thumbnail button, all graphic files will appear and you can easily bookmark any relevant evidence for your case. With EnCase Mobile Investigator, finding and gathering the evidence you need from a smartphone, smartwatch, tablet, or even drone, has never been easier.
