In short, the following principles should be followed to defend against CSRF:
- Check if your framework has built-in CSRF protection and use it If framework does not have built-in CSRF protection add CSRF tokens to all state changing requests (requests that cause ...
- For stateful software use the synchronizer token pattern
- For stateless software use double submit cookies
Full Answer
How do you defend against CSRF attacks?
The most common approach to defending against CSRF attacks is to use the Synchronizer Token Pattern (STP). STP is used when the user requests a page with form data: The server sends a token associated with the current user's identity to the client. The client sends back the token to the server for verification.
What is CSRF and how to prevent CSRF?
CSRF tokens prevent CSRF because without token, attacker cannot create a valid requests to the backend server. CSRF tokens should not be transmitted using cookies. The CSRF token can be added through hidden fields, headers, and can be used with forms, and AJAX calls. Make sure that the token is not leaked in the server logs, or in the URL.
Does using SSL prevent CSRF attacks?
Moreover, using SSL does not prevent a CSRF attack, because the malicious site can send an "https://" request. Typically, CSRF attacks are possible against web sites that use cookies for authentication, because browsers send all relevant cookies to the destination web site.
How can I prevent CSRF tokens from being leaked?
Make sure that the token is not leaked in the server logs, or in the URL. CSRF tokens in GET requests are potentially leaked at several locations, such as the browser history, log files, network appliances that log the first line of an HTTP request, and Referer headers if the protected site links to an external site.

How to prevent CSRF attacks?
To prevent CSRF attacks on the server side, banks and merchants should transition from cookies that perform session-tracking to session tokens that are dynamically generated. This would make it more difficult for an attacker to get a hold of a client’s session.
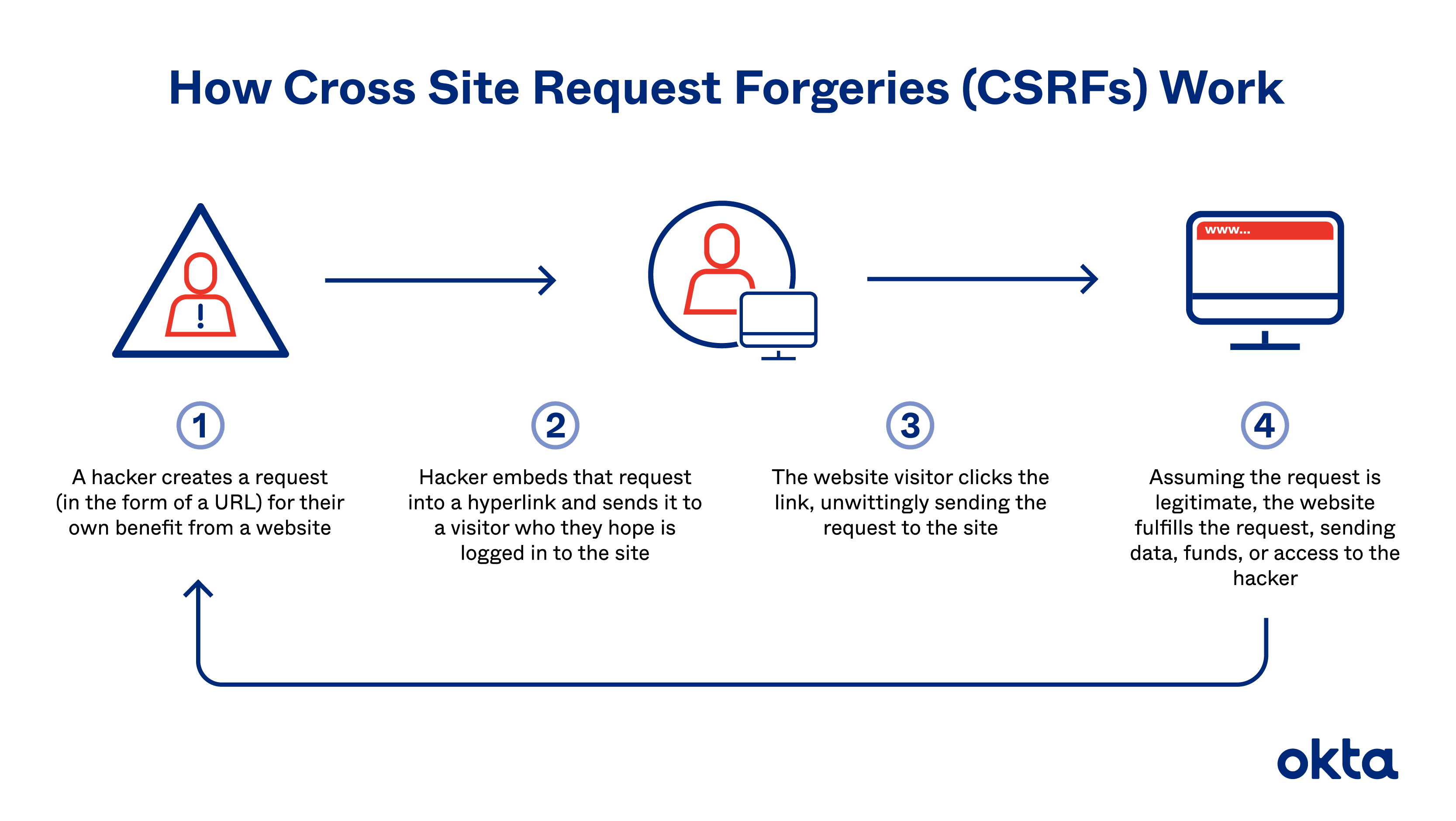
What is CSRF attack?
Cross-site request forgery (CSRF) attacks are becoming a more common attack method used by hackers. These attacks take advantage of the trust a website has for a user’s input and browser. The victim is tricked into performing a specific action they were not intending to do on a legitimate website; where they are authenticated to.
Can malicious scripts be quarantined?
Many malicious scripts can be blocked and quarantined by this software. Do not open any emails, browse to other sites or perform any other social network communication while authenticated to your banking site or any site that performs financial transactions.
Do sites have controls to prevent CSRF attacks?
Don’t trust that the site you're visiting has measures in place to prevent CSRF attacks. Many sites do have controls in place to protect against it, but it is not a good practice to assume this. Some sites could have controls in place today but after an upgrade or change in the code, may remove them later.
Will CSRF attacks continue?
As more financial transactions process on the internet, CSRF attacks will continue to grow. Also, the rise in using social network sites will contribute to the delivery of scripts that trigger these attacks. Following the preventive actions I have listed will reduce the possibility of you becoming a victim of a CSRF attack.
How to prevent CSRF?
One of the best methods to prevent a CSRF is to use frequently changing tokens instead of depending on session cookies for running a state change on the server.
What are the main targets of CSRF attacks?
The main targets for CSRF attacks are web actions involving a user's authentication. To be successful, it needs unintentional actions from the victim. During a CSRF attack, GET, DELETE, and PUT actions, as well as vulnerable POST requests are the main targets of an attacker. Let's look at the meaning of those terms:
How Do CSRF Attacks Affect You?
A CSRF is an attack used to implement unauthorized requests during web actions that require user login or authentication. CSRF attacks can take advantage of session IDs, cookies, as well as other server-based vulnerabilities to steal a user's credentials.
What is CSRF used for?
CSRF has been used to hijack over-the-web fund transactions as well as changing usernames and passwords, which leads to users losing access to the affected service.
What are the causes of a successful CSRF attack?
Weak or poor website security practices and carelessness on the user's path are some of the common causes of a successful CSRF attack.
How can an attacker take advantage of a user's session ID?
Once that barrier breaks, an attacker can quickly take advantage of the user's session ID via the cookies created by the user's browser and embed a script tag into the vulnerable website.
How to stop attackers from hijacking your session?
Although you might feel helpless to stop an attacker from hijacking your session, you can still help prevent this by ensuring that your browser doesn't store information like passwords and other login details.
Why is CSRF a problem?
If cookies are used to store authentication tokens and to authenticate API requests on the server, CSRF is a potential problem. If local storage is used to store the token, CSRF vulnerability might be mitigated because values from local storage aren't sent automatically to the server with every request. Thus, using local storage to store the antiforgery token on the client and sending the token as a request header is a recommended approach.
When using Windows Authentication, application endpoints must be protected against CSRF attacks in the same way as?
When using Windows Authentication, application endpoints must be protected against CSRF attacks in the same way as done for cookies. The browser implicitly sends the authentication context to the server, therefore endpoints need to be protected against CSRF attacks.
How are antiforgery tokens passed?
In traditional HTML-based apps, antiforgery tokens are passed to the server using hidden form fields. In modern JavaScript-based apps and SPAs, many requests are made programmatically. These AJAX requests may use other techniques (such as request headers or cookies) to send the token.
Why is Good Banking Site vulnerable?
The site is vulnerable to attack because it trusts any request that it receives with a valid authentication cookie.
Why is a bad crook site vulnerable?
The site is vulnerable to attack because it trusts any request that it receives with a valid authentication cookie. The user visits a malicious site, www.bad-crook-site.com.
When does an antiforgery token automatically generate?
The automatic generation of antiforgery tokens for HTML form elements happens when the <form> tag contains the method="post" attribute and either of the following are true:
Where does the Good Banking Site request run?
The request runs on the www.good-banking-site.com server with the user's authentication context and can perform any action that an authenticated user is allowed to perform.
How to mitigate CSRF?
Login CSRF can be mitigated by creating pre-sessions (sessions before a user is authenticated) and including tokens in login form. You can use any of the techniques mentioned above to generate tokens. Remember that pre-sessions cannot be transitioned to real sessions once the user is authenticated - the session should be destroyed and a new one should be made to avoid session fixation attacks. This technique is described in Robust Defenses for Cross-Site Request Forgery section 4.1.
What is a CSRF attack?
Cross-Site Request Forger y (CSRF) is a type of attack that occurs when a malicious web site, email, blog, instant message, or program causes a user's web browser to perform an unwanted action on a trusted site when the user is authenticated. A CSRF attack works because browser requests automatically include all cookies including session cookies. Therefore, if the user is authenticated to the site, the site cannot distinguish between legitimate authorized requests and forged authenticated requests. This attack is thwarted when proper Authorization is used, which implies that a challenge-response mechanism is required that verifies the identity and authority of the requester.
How often should CSRF tokens be generated?
CSRF tokens should be generated on the server-side. They can be generated once per user session or for each request. Per-request tokens are more secure than per-session tokens as the time range for an attacker to exploit the stolen tokens is minimal. However, this may result in usability concerns.
What happens when a request is issued by the client?
When a request is issued by the client, the server-side component must verify the existence and validity of the token in the request compared to the token found in the user session. If the token was not found within the request, or the value provided does not match the value within the user session, then the request should be aborted. Additional actions such as logging the event as a potential CSRF attack in progress should also be considered.
Why do subdomains use tokens?
This works because a sub domain has no way to over-write an properly crafted encrypted cookie without the necessary information such as encryption key.
Where is CSRF stored?
All subsequent calls in the page can extract the CSRF token from this <meta> tag. It can also be stored in a JavaScript variable or anywhere on the DOM. However, it is not recommended to store it in cookies or browser local storage.
Can you block a request if neither headers are present?
If neither of these headers are present, you can either accept or block the request. We recommend blocking. Alternatively, you might want to log all such instances, monitor their use cases/behavior, and then start blocking requests only after you get enough confidence.
