How does SAML single sign-on work in Deep Security as a Service?
- Establish a trust relationship. In SAML single sign-on, a trust relationship is established between two parties: the identity provider and the service provider.
- Create Deep Security as a Service accounts from user identities. ...
- Implement SAML single sign-on in Deep Security as a Service. ...
What is SAML single sign-on authentication?
SAML single sign-on authentication typically involves a service provider and an identity provider. The process flow usually involves the trust establishment and authentication flow stages.
How does single sign-on with OpenID Connect and SAML work?
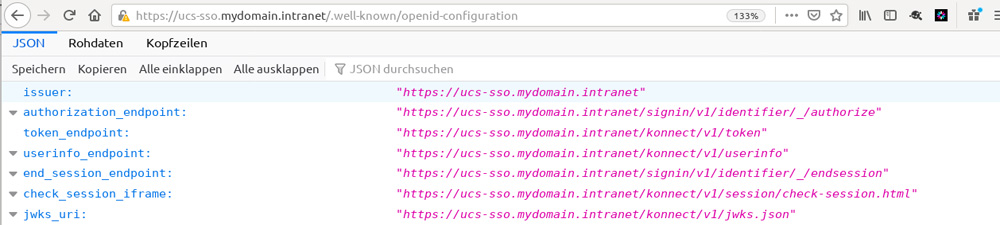
Let’s first take a look at how single sign-on with OpenID Connect and SAML works. Before users log in for the first time, admins have to establish trust between the Identity Provider (here: UCS) and the other services. OpenID Connect uses a shared secret for this: a very long password.
How to implement SSO with SAML?
There are many ways to implement SSO with SAML. Authentication and authorization data: SAML is used to allow users to log into a service (authentication) and also control which permissions a user has in that service (authorization). Identity provider: This is the service that has information about the user.
How does single sign on (SSO) work?
For SSO to work, there has to be trust between the services and the single point of authentication. This means that during the login process some kind of proof of successful login must be passed to the external service.
What is difference between SAML and SSO?
SAML 2.0 (Security Assertion Mark-up Language) is an umbrella standard that covers federation, identity management and single sign-on (SSO)....What is SAML?Use case typeStandard to useAccess to applications from a portalSAML 2.0Centralised identity sourceSAML 2.0Enterprise SSOSAML 2.02 more rows•Jul 3, 2017
How does technically single sign on work?
Single sign-on (SSO) is a technology which combines several different application login screens into one. With SSO, a user only has to enter their login credentials (username, password, etc.) one time on a single page to access all of their SaaS applications.
How does SSO work across domains?
The SSO domain authenticates the credentials, validates the user, and generates a token. The user is sent back to the original site, and the embedded token acts as proof that they've been authenticated. This grants them access to associated apps and sites that share the central SSO domain.
What is the difference between SSO and OAuth?
To Start, OAuth is not the same thing as Single Sign On (SSO). While they have some similarities — they are very different. OAuth is an authorization protocol. SSO is a high-level term used to describe a scenario in which a user uses the same credentials to access multiple domains.
What is single sign-on for dummies?
A single sign on provider is the tool that will 'vouch' for you to authorize on a website or a service. This means that your password will be known only to your SSO provider, and you won't have to give any credentials to a service directly. A good example of how single sign-on works is Google.
What is the difference between single sign-on and same sign-on?
On the other hand, single sign-on requires more overhead because of hardware and software requirements. Same sign-on requires you to log into each application, using the same userID and password to logon which helps end-users by reducing the number of userID and passwords to remember.
What advantages does single sign-on offer?
SSO reduces the number of attack surfaces because users only log in once each day and only use one set of credentials. Reducing login to one set of credentials improves enterprise security.
How do you make a single sign-on?
To configure single sign-on on your own:Go to Admin Console > Enterprise Settings, and then click the User Settings tab.In the Configure Single Sign-On (SSO) for All Users section, click Configure.Select your Identity Provider (IdP). ... Upload your IdP's SSO metadata file. ... Click Submit.
Benefits of SAML Authentication
Without much ado, the benefits of SAML authentication include: 1. Standardization: SAML is a standard format that allows seamless interoperability...
How Does SAML Authentication Really Work?
Let's take an in-depth look at the process flow of SAML authentication in an application. SAML single sign-on authentication typically involves a s...
Aside: SAML Authentication With Auth0
With Auth0, SAML authentication is dead simple to implement. We can easily configure our applications to use Auth0 Lock for SAML authentication.In...
Establish Two Auth0 Accounts
If you do not already have two Auth0 accounts, you will need to create them. If you do already have two accounts, you can skip to step #2.In the Au...
Set Up The Auth0 IDP (Account 2)
In this section you will configure one Auth0 account (account 2) to serve as an Identity Provider. You will do this by registering an application,...
Set Up The Auth0 Service Provider (Account 1)
In this section you will configure another Auth0 account (account 1) so it knows how to communicate with the second Auth0 account (account 2) for s...
Add Your Service Provider Metadata to The Identity Provider
In this section you will go back and add some information about the Service Provider (account 1) to the Identity Provider (account 2) so the Identi...
Register A Simple Html Application With Which to Test The End-To-End Connection.
In this section, you will register an application in Auth0 that will use the SAML connection you set up in the above steps.Make sure you are logged...
Test The Connection from Service Provider to Identity Provider
In this section, you will test to make sure the SAML configuration between Auth0 account 1 (Service Provider) and Auth0 account 2 (Identity Provide...
Create The Html Page For A Test Application
In this section you will create a very simple HTML page that invokes the Auth0 Lock Widget which will trigger the SAML login sequence. This will en...
What is SAML in IT?
SAML stands for Security Assertion Markup Language. It is an XML-based open-standard for transferring identity data between two parties: an identity provider (IdP) and a service provider (SP). Identity Provider — Performs authentication and passes the user's identity and authorization level to the service provider.
Why do you need to sign in to multiple service providers?
This allows for a faster authentication process and less expectation of the user to remember multiple login credentials for every application. In the example above, that user could have clicked on any of the other icons in their dashboard and been promptly logged in without ever having to enter more credentials!
Does SAML require user information to be maintained and synchronized between directories?
Loose Coupling of Directories — SAML doesn't require user information to be maintained and synchronized between directories. Reduced Costs for Service Providers — With SAML, you don't have to maintain account information across multiple services. The identity provider bears this burden.
Small SSO Glossary
Identity Provider: The service which authenticates users (for example username and password verification) to confirm that a person is who they say they are.
What is Single-Sign-on?
Every time a user logs in with a username and the associated password, he proves to the underlying system that he really is who he claims to be. Sometimes a second factor is involved, such as a YubiKey or an text message – this is called two-factor authentication (2FA).
Single Sign-on with OpenID Connect
Before users log in for the first time, admins have to establish trust between the Identity Provider (here: UCS) and the other services. OpenID Connect uses a shared secret for this: a very long password. Administrators must therefore store the same shared secret in UCS and in the external service’s configuration.
Single Sign-on with SAML
In SAML, trust between Identity Providers and services is ensured by exchanging certificates. Like with web servers, there are two certificates ( public and private ). Administrators have to save the UCS IdP’s public certificate when setting up the service so that the service users log in to can verify the authentication of the UCS IdP.
How does SSO work with OpenID Connect and with SAML?
So, how exactly does the login to a service work? Let’s look at both methods, OpenID Connect and SAML. It’s vital to understand all the single steps, especially if things don’t work as expected and you need to identify problems and do some debugging.
How to debug Single Sign-on with SAML
Both methods have one thing in common: a lot of messages are exchanged. As UCS admin you can look at those messages for debugging purposes. If something is working, you have several options to track down a problem. In case of SAML, I recommend the Firefox add-on SAML-tracer.
SAML Debugging with the Firefox Add-on SAML-tracer
Finally, I would like to show how administrators can use the Firefox extension SAML-tracer to view and analyze the SAML messages. In my example, I’ve clicked the LOGIN button in the UCS portal to open the dialog for entering my username and password. At the same time, the Firefox add-on is running in the background and keeping track of the events:
What is SAML in the cloud?
SAML is the gold standard for single sign-on for cloud apps. It eliminates all passwords and instead uses digital signatures to establish trust between the identity provider and the cloud app. Using SAML, users can seamlessly access multiple applications, allowing them to conduct business faster and more efficiently.
What is SAML response?
A SAML Response is generated by the Identity Provider. It contains the actual assertion of the authenticated user. In addition, a SAML Response may contain additional information, such as user profile information and group/role information, depending on what the Service Provider can support.
Why do organizations know the identity of users?
Most organizations already know the identity of users because they are logged in to their Active Directory domain or intranet. It makes sense to use this information to log users into other applications, such as web-based applications, and one of the more elegant ways of doing this is by using SAML. SAML Response.
What is an identity provider?
An Identity Provider (IdP) is the entity providing the identities, including the ability to authenticate a user. The Identity Provider typically also contains the user profile: additional information about the user such as first name, last name, ...
What is SAML authentication?
Authentication and authorization data: SAML is used to allow users to log into a service (aut hentication) and also control which permissions a user has in that service (authorization). Identity provider: This is the service that has information about the user.
What is SAML in IT?
What Is SAML? SAML stands for Security Assertion Markup Language. According to Wikipedia, it is “an open standard for exchanging authentication and authorization data between parties, in particular, between an identity provider and a service provider.”. That’s a lot of terms there.
What is SSO on Facebook?
That is SSO in a nutshell. In more technical terms, we would say that SSO handles the authentication of a user in a federated identity system.
Does Nike have an SSO?
Nike would probably have an SSO provider like OneLogin or Okta. Nike would add any external web services they want their employees to be able to access there. An employee could log into the portal and then click a link to go to the appropriate web service and be automatically logged in there.
What is identity provider in SSO?
The identity provider is the entity or server which proves the user’s identity. SAML SSO works by sending the user’s identity from one location, here you can say identity provider to another location, i.e., service provider. Now the question arises how it is done.
What does it mean to provide a username and password?
By providing a username and password, the application authenticates you whether you are the right person to access the account. In other words, you prove your identity to the application. The application also authorizes you to access content based on your rights.
What is Azure AD signature?
Azure AD signs the assertion in response to a successful sign-on. The Signature element contains a digital signature that the cloud service can use to authenticate the source to verify the integrity of the assertion.
What is the status element in a sign on?
The Status element conveys the success or failure of sign-on. It includes the StatusCode element, which contains a code or a set of nested codes that represents the status of the request. It also includes the StatusMessage element, which contains custom error messages that are generated during the sign-on process.
What is the issuer element in an AuthnRequest?
The Issuer element in an AuthnRequest must exactly match one of the ServicePrincipalNames in the cloud service in Azure AD. Typically, this is set to the App ID URI that is specified during application registration.
Does Azure AD validate signed authentication requests?
A Signature element in AuthnRequest elements is optional. Azure AD does not validate signed authentication requests if a signature is present. Requestor verification is provided for by only responding to registered Assertion Consumer Service URLs.
How does SSO work?
SSO works based upon a trust relationship set up between an application, known as the service provider, and an identity provider, like OneLogin. This trust relationship is often based upon a certificate that is exchanged between the identity provider and the service provider.
How to implement SSO?
The specifics on how an SSO solution is implemented will differ depending on what exact SSO solution you are working with. But no matter what the specific steps are, you need to make sure you have set clear objectives and goals for your implementation. Make sure you answer the following questions: 1 What different types of users are you serving and what are their different requirements? 2 Are you looking for an On Prem solution or a Cloud Based solution? 3 Will this solution be able to grow with your company and your needs? 4 What features are you looking for to ensure only trusted users are logging in? MFA, Adaptive Authentication, Device Trust, IP Address Whitelisting, etc.? 5 What systems do you need to integrate with? 6 Do you need API access?
What is SSO token?
An SSO token is a collection of data or information that is passed from one system to another during the SSO process. The data can simply be a user’s email address and information about which system is sending the token.
Why is it important to choose an SSO solution?
For this reason, it would be important to choose an SSO solution that gives you the ability to, say, require an additional authentication factor before a user logs into a particular application or that prevents users from accessing certain applications unless they are connected to a secure network.
What is SSO in FIM?
FIM just refers to a trust relationship that is created between two or more domains or identity management systems. Single Sign-on is often a feature that is available within a FIM architecture.
Why do we need SSO?
SSO often enables users to just get access to their applications much faster. SSO can also cut down on the amount of time the help desk has to spend on assisting users with lost passwords.
What is ADDS in Microsoft?
Users and resources are added to the directory service for central management and ADDS works with authentication protocols like NTLM and Kerberos.
Single sign-on options
Choosing an SSO method depends on how the application is configured for authentication. Cloud applications can use federation-based options, such as OpenID Connect, OAuth, and SAML. The application can also use password-based SSO, linked-based SSO, or SSO can be disabled.
Plan SSO deployment
Web applications are hosted by various companies and made available as a service. Some popular examples of web applications include Microsoft 365, GitHub, and Salesforce. There are thousands of others. People access web applications using a web browser on their computer.
My Apps
If you're a user of an application, you likely don't care much about SSO details. You just want to use the applications that make you productive without having to type your password so much. You can find and manage your applications at the My Apps portal. For more information, see Sign in and start apps from the My Apps portal.