
What does "at rest" mean involving data encryption?
The purpose of encryption at rest. Encryption at rest provides data protection for stored data (at rest). ... Azure Encryption at Rest Components. As described previously, the goal of encryption at rest is that data that is persisted on disk is encrypted with a secret encryption key. Azure resource providers encryption model support. ... Conclusion. ...
What is the encryption protocol for data at rest?
- A symmetric encryption key is used to encrypt data as it is written to storage.
- The same encryption key is used to decrypt that data as it is readied for use in memory.
- Data may be partitioned, and different keys may be used for each partition.
- Keys must be stored in a secure location with identity-based access control and audit policies. ...
Why encrypt data at rest?
Encryption at rest is a key protection against a data breach. Ask any business owner and they’ll tell you their number one digital security risk is a data breach. The recent ransomware attacks show that cyber terrorism becoming more and more common around the world. It’s more important now than ever to ensure that sensitive company data ...
Do you encrypt data at rest?
You can encrypt any type of data at rest. Encryption is commonly applied to the most valuable or sensitive data stored by an organization, such as customer records, credit card data, employee HR records, confidential reports and plans, and the like.
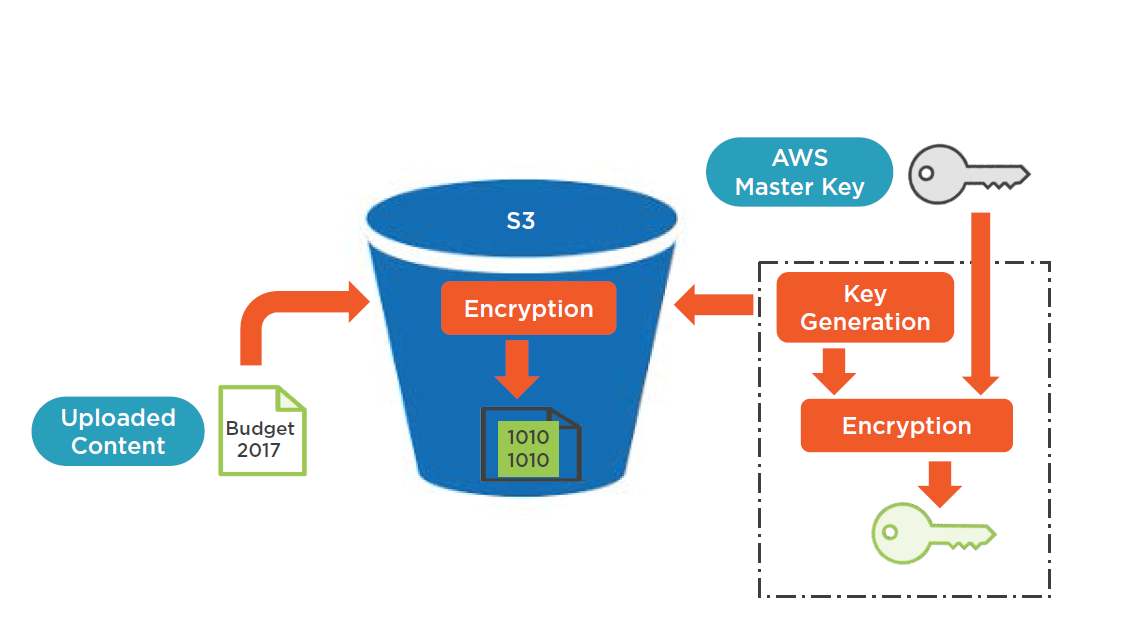
How does rest encrypt data?
With DARE, data at rest including offline backups are protected. Data encryption is done by using Transparent Data Encryption (TDE) where no changes are made to the application logic or schema. DARE is done for Oracle, DB2, and MySQL databases. DARE does not require any additional tools.
How is data encrypted at rest and in motion?
Encryption is another common solution used to secure data both at rest and in motion. Encrypting hard drives using operating systems' native data encryption solutions, companies can ensure that, if a device lands in the wrong hands, no one can access the data on the hard drive without an encryption key.
Is data encrypted in rest API?
REST APIs use HTTP and support Transport Layer Security (TLS) encryption. TLS is a standard that keeps an internet connection private and checks that the data sent between two systems (a server and a server, or a server and a client) is encrypted and unmodified.
Which encryption is best for data at rest?
The encryption of data at rest should only include strong encryption methods such as AES or RSA. Encrypted data should remain encrypted when access controls such as usernames and password fail.
What is data encryption techniques?
Data encryption works by securing transmitted digital data on the cloud and computer systems. There are two kinds of digital data, transmitted data or in-flight data and stored digital data or data at rest. Modern encryption algorithms have replaced the outdated Data Encryption Standard to protect data.
How does rest data work?
Data at rest is data that has reached a destination and is not being accessed or used. It typically refers to stored data and excludes data that is moving across a network or is temporarily in computer memory waiting to be read or updated.
How do I encrypt rest API data?
Since REST APIs use HTTP, encryption can be achieved by using the Transport Layer Security (TLS) protocol or its previous iteration, the Secure Sockets Layer (SSL) protocol. These protocols supply the S in “HTTPS” (“S” meaning “secure'') and are the standard for encrypting web pages and REST API communications.
Is rest protocol encrypted?
The connection is private (or secure) because symmetric cryptography is used to encrypt the data transmitted. The keys for this symmetric encryption are generated uniquely for each connection and are based on a shared secret negotiated at the start of the session.
Is Gmail encrypted at rest?
Gmail is encrypted with TLS, Transport Layer Security, while transferring your data and it protects your emails at rest with industry-standard 128-bit encryption.
What are the 4 basic types of encryption systems?
While the most common are AES, RSA, and DES, there are other types being used as well. Let's dive into what these acronyms mean, what encryption is, and how to keep your online data safe.
What are the 2 types of data encryption?
There are two types of encryption in widespread use today: symmetric and asymmetric encryption. The name derives from whether or not the same key is used for encryption and decryption.
Is AES-256 for data at rest?
256-bit AES encryption is a technique that uses a key length of 256 bits for this process. Because key combinations increase exponentially with key size, the AES-256 key has the mathematical equivalent of 2256 possible combinations. Using 256-bit AES encryption ensures your data is secure at rest.
How do you encrypt data in motion?
Data in motion can be encrypted using the following methods:Asymmetric encryption. This method uses one public key and one private key to encrypt and decrypt a message. ... TLS and SSL. One of the best known uses of cryptography for data in motion is TLS and SSL. ... HTTPS. ... Cryptography. ... IPSec.
Which option is used to protect data in use data in motion and data at rest from accidental or intentional leaks?
Encryption plays a major role in protecting data in use or in motion.
What is an example of securing data in motion?
Data being sent over an email or through workstream collaboration platforms like Slack, being transferred to a USB device or to a cloud storage are examples of data in motion. When it arrives, it becomes data at rest.
What are the 3 states of data?
Three states of data is a way of categorizing structured and unstructured data. The three states of data are data at rest, data in motion and data in use. Data can change states quickly and frequently, or it may remain in a single state for the entire life cycle of a computer.