
AWS has no access to your keys and cannot perform encryption or decryption on your behalf. You are responsible for the proper storage, management, and use of keys to ensure the confidentiality, integrity, and availability of your data. Data can be encrypted in AWS services as described in the following sections. Amazon S3
What is encryption and why is it important?
Why is encryption important?
- Security. Encryption can help prevent data breaches during transfer and storage. ...
- Privacy. Most encryption types allow only verified access to encrypted data. ...
- Integrity. Encryption can help protect against data manipulating attacks during transfer. ...
- Verification. Website developers can use encryption to verify a website's data. ...
- Regulation. ...
What is standard encryption method?
Well-known symmetric encryption methods include the now-outdated Data Encryption Standard (DES) and its successor, the Advanced Encryption Standard (AES). Data Encryption Standard (DES) DES is a symmetric encryption method that was developed by IBM in the 1970s and standardized in 1977 by the US National Institute of Standards and Technology (NIST).
What is the standard for encryption?
They include encryption for Gmail ... customers that rely on it to safeguard their most sensitive data. The TDF standard, meanwhile, has become the leading data control standard for the U.S ...
Why is data encryption so important?
- modification
- theft
- unauthorized disclosure
- unauthorized access
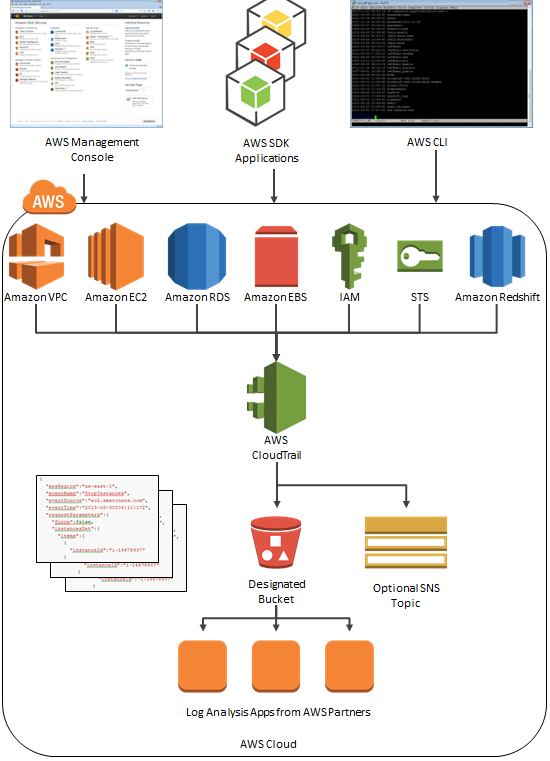
Is Amazon AWS encrypted?
All data flowing across AWS Regions over the AWS global network is automatically encrypted at the physical layer before it leaves AWS secured facilities. All traffic between AZs is encrypted. Additional layers of encryption, including those listed in this section, may provide additional protections.
What encryption does AWS use?
AWS cryptographic tools and services support two widely used symmetric algorithms. AES – Advanced Encryption Standard (AES) with 128-, 192-, or 256-bit keys. AES is often combined with Galois/Counter Mode (GCM) and known as AES-GCM. Triple DES – Triple DES (3DES) uses three 56-bit keys.
Is AWS encrypted by default?
Short description. New Amazon EBS volumes aren't encrypted by default. However, there is a setting in the Amazon Elastic Compute Cloud (Amazon EC2) console that turns on encryption by default for all new Amazon EBS volumes and snapshot copies created within a specified Region.
Does AWS encrypt at rest?
AWS provides the tools for you to create an encrypted file system that encrypts all of your data and metadata at rest using an industry standard AES-256 encryption algorithm .
Has AWS ever been hacked?
The most recent known Amazon Web Services (AWS) breach happened in December 2021, when hackers looted personally data on over 3 million users of FlexBooker, an online booking software. As in most AWS breaches, this information was exposed due to improperly configured S3 buckets on the part of the business using AWS.
Can AWS decrypt data?
AWS services encrypt your data and store an encrypted copy of the data key along with the encrypted data. When a service needs to decrypt your data, it requests AWS KMS to decrypt the data key using your KMS key.
Is Amazon S3 encrypted?
When you use server-side encryption, Amazon S3 encrypts an object before saving it to disk and decrypts it when you download the objects. For more information about protecting data using server-side encryption and encryption key management, see Protecting data using server-side encryption.
How does AWS encryption work?
Each message is encrypted under a unique data key. Then the data key is encrypted by the wrapping keys you specify. To decrypt the encrypted message, the AWS Encryption SDK uses the wrapping keys you specify to decrypt at least one encrypted data key. Then it can decrypt the ciphertext and return a plaintext message.
Can we encrypt EC2 instance?
You can encrypt both the boot and data volumes of an EC2 instance. When you create an encrypted EBS volume and attach it to a supported instance type, the following types of data are encrypted: Data at rest inside the volume.
Is Google cloud encrypted?
Google uses several layers of encryption to protect customer data at rest in Google Cloud products. Google Cloud encrypts all customer content stored at rest, without any action required from the customer, using one or more encryption mechanisms.
Are AWS API calls encrypted?
Data encryption in transit in Amazon API Gateway API Gateway doesn't support unencrypted (HTTP) endpoints. For greater security, you can choose a minimum Transport Layer Security (TLS) protocol version to be enforced for your API Gateway custom domain.
Who enables AWS encryption?
All AWS services that handle customer data encrypt data in motion and provide options to encrypt data at rest. All AWS services that offer encryption at rest using AWS KMS or AWS CloudHSM use AES-256.
How and why does encryption work?
Encryption works by using an algorithm with a key to convert data into unreadable data (ciphertext) that can only become readable again with the right key. For example, a simple phrase like “Hello World!” may look like “1c28df2b595b4e30b7b07500963dc7c” when encrypted.
Encryption as part of your security strategy
An effective security strategy begins with stringent access control and continuous work to define the least privilege necessary for persons or systems accessing data. AWS requires that you manage your own access control policies, and also supports defense in depth to achieve the best possible data protection.
Requirements for an encryption solution
To get the most from an encryption solution, you need to think about two things:
Encrypting data at rest and in motion
All AWS services that handle customer data encrypt data in motion and provide options to encrypt data at rest. All AWS services that offer encryption at rest using AWS KMS or AWS CloudHSM use AES-256.
Summary
At AWS, security is our top priority and we aim to make it as easy as possible for you to use encryption to protect your data above and beyond basic access control. By building and supporting encryption tools that work both on and off the cloud, we help you secure your data and ensure compliance across your entire environment.
Benefits
To aid your compliance efforts, AWS regularly achieves third-party validation for thousands of global compliance requirements that we continually monitor to help you meet security and compliance standards for finance, retail, healthcare, government, and beyond.
Strategic Security
AWS is designed to help you build secure, high-performing, resilient, and efficient infrastructure for your applications. World-class security experts who monitor our infrastructure also build and maintain our broad selection of innovative security services, which can help you simplify meeting your own security and regulatory requirements.
Customers
"AWS allowed us to store information in a cost effective manner while alleviating the burden of supporting the necessary infrastructure since AWS takes care of that. It really is a win-win for us and our customers."
Partners
APN Partners offer hundreds of industry-leading security solutions that help customers improve their security and compliance. The scalability, visibility, and affordability our partners inherit with the cloud enables them to create world-class offerings for customers.
Learning
Learn about cloud security with resources such as whitepapers, videos, articles, blog posts, training, and documentation. Learn more >>
Vulnerability Reporting
Learn about our practice for addressing potential vulnerabilities in any aspect of our cloud services.
Cloud encryption advantages
The most important thing to remember about encryption on AWS is that you always own and control your data. This is an extension of the AWS shared responsibility model, which makes the secure delivery and operation of your applications the responsibility of both you and AWS.
Addressing three common encryption questions
For many of the technology leaders I work with, agility and risk mitigation are top IT business goals. An enterprise-wide cloud encryption and data protection strategy helps define how to achieve fine-grained access controls while maintaining nearly continuous visibility into your risk posture.
How can I use encryption to prevent unauthorized access to my data in the cloud?
The primary way to protect access to your data is access control. On AWS, this often means using IAM to describe which users or roles can access resources like Amazon Simple Storage Service (Amazon S3) buckets. IAM allows you to tightly define the access for each user—whether human or system—and set the conditions in which that access is allowed.
How can I use encryption to meet compliance requirements in the cloud?
The first step is to identify your compliance requirements. This can often be done by working with your company’s risk and compliance team to understand the frameworks and controls that your company must abide by.
How do I demonstrate compliance with company policy to my stakeholders in the cloud?
You probably have internal and external stakeholders that care about compliance and require that you document your system’s compliance posture.
Summary
Encryption in the cloud is easier than encryption on-premises, powerful, and can help you meet the highest standards for controls and compliance. The cloud provides more comprehensive data protection capabilities for customers looking to rapidly scale and innovate than are available for on-premises systems.
Compatibility with encryption libraries and services
The AWS Encryption SDK is supported in several programming languages. All language implementations are interoperable. You can encrypt with one language implementation and decrypt with another. Interoperability might be subject to language constraints. If so, these constraints are described in the topic about the language implementation.
Learning more
For more information about the AWS Encryption SDK and client-side encryption, try these sources.
Sending feedback
We welcome your feedback! If you have a question or comment, or an issue to report, please use the following resources.
Short description
You can view encryption information for your snapshots or AMI using the console or using the AWS Command Line Interface (AWS CLI).
Resolution
1. Run the describe-images command with the BlockDeviceMappings query filter to view the snapshots associated with the AMI. In the following example, replace image-ids and region with the ID and Region of your AMI.

How and Why Does Encryption Work?
Encryption as Part of Your Security Strategy
- An effective security strategy begins with stringent access control and continuous work to define the least privilege necessary for persons or systems accessing data. AWS requires that you manage your own access control policies, and also supports defense in depth to achieve the best possible data protection. Encryption is a critical component of a defense-in-depth strategy beca…
Requirements For An Encryption Solution
- To get the most from an encryption solution, you need to think about two things: 1. Protecting keys at rest: Are the systems using encryption keys secured so the keys can never be used outside the system? In addition, do these systems implement encryption algorithms correctly to produce strong ciphertexts that cannot be decrypted without access to the right keys? 2. Indepe…
Encrypting Data at Rest and in Motion
- All AWS services that handle customer data encrypt data in motion and provide options to encrypt data at rest. All AWS services that offer encryption at rest using AWS KMS or AWS CloudHSM use AES-256. None of these services store plaintext encryption keys at rest — that’s a function that only AWS KMS and AWS CloudHSM may perform using their FIPS 140-2 validated HSMs. This ar…
Summary
- At AWS, security is our top priority and we aim to make it as easy as possible for you to use encryption to protect your data above and beyond basic access control. By building and supporting encryption tools that work both on and off the cloud, we help you secure your data and ensure compliance across your entire environment. We put security at th...