Is EAP-TLS better than other authentication methods?
For stronger security, none are better than an EAP-TLS, certificate-based authentication method. First and foremost, EAP-TLS as an authentication method is highly secure and prepared to thwart any ill-advised attacks on the network.
What is EAP-TLS (Extensible Authentication Protocol)?
Extensible Authentication Protocol – Transport Layer Security (EAP-TLS) is an IETF open standard that’s defined in RFC 5216. More colloquially, EAP-TLS is the authentication protocol most commonly deployed on WPA2-Enterprise networks to enable the use of X.509 digital certificates for authentication.
Is EAP-TTLS/PAP a security risk to your network?
Networks operating with a EAP-TTLS/PAP authentication method draw attention to themselves as targets for hackers because of the flawed systems under which EAP-TTLS/PAP operates. Many believe that EAP-TTLS/PAP should be avoided because glaring flaws exist in how it operates and newer authentication methods fill the security holes it leaves open.
What is the difference between EAP-TLS and TTLS?
The primary difference between EAP-TTLS and EAP-TLS is that the former only requires server-side certificates rather than the mutual certificate authentication that characterizes EAP-TLS. In order to compensate, TTLS uses a tunnel (hence “Tunneled” Transport Layer Security).

Is TTLS secure?
TLS Basics. Transport Layer Security (TLS) encrypts data sent over the Internet to ensure that eavesdroppers and hackers are unable to see what you transmit which is particularly useful for private and sensitive information such as passwords, credit card numbers, and personal correspondence.
Is EAP protocol secure?
EAP is used on encrypted networks to provide a secure way to send identifying information to provide network authentication. It supports various authentication methods, including as token cards, smart cards, certificates, one-time passwords and public key encryption.
Which EAP is most secure?
EAP-TLS. This is the most secure method as it requires certificates from client and server end. The process involves mutual authentication where client validates server certificate and server validates client certificate.
What is EAP TTLS in cyber security?
Extensible Authentication Protocol – Tunnelled Transport Layer Security. EAP-TTLS is a specific version of the EAP(Extensible Authentication Protocol) providing a framework to support authentication across a number of communication systems.
Is EAP-FAST secure?
EAP-FAST is an EAP method that enables secure communication between a client and an authentication server by using Transport Layer Security (TLS) to establish a mutually authenticated tunnel.
Is EAP-TLS encrypted?
The end result of EAP-TLS authentication is an encrypted channel of communication. The user is ready to access the secure network and utilize all resources available to them.
What EAP method should I use for WIFI?
PEAPFor "EAP method" select "PEAP". For "Phase 2 authentication" select "MSCHAPV2". If you are using the Nougat (7) OS on your Android, set "CA Certificate" to "Use system certificates" and "Domain" to "ed.ac.uk".
Which is more secure EAP-TLS or PEAP?
PEAP-MSCHAPv2 leaves your organization vulnerable to cyber attacks. EAP-TLS is a superior authentication protocol that uses digital certificates as opposed to credentials.
How does EAP work authentication?
The EAP authentication exchange proceeds as follows: 1) The authenticator (the server) sends a Request to authenticate the peer (the client). 2) The peer sends a Response packet in reply to a valid Request. 3) The authenticator sends an additional Request packet, and the peer replies with a Response.
What is the main advantage of EAP fast over EAP-TLS and PEAP?
EAP-FAST: Flexible Authentication via Secure Tunnel (FAST) is very similar to PEAP. FAST was created by Cisco Systems as an alternative to PEAP that allows for faster re-authentications and supports faster wireless roaming.
What is the difference between EAP and PAP?
Compared to EAP-TLS, the cleartext format of messages in PAP is vulnerable because they are not encrypted; hence, hackers can cause trouble by caching even a single cleartext message in the entire system. A Man-In-The-Middle (MITM) attack is the most common way to attack EAP-TTLS/PAP networks.
Does PAP use TLS?
TTLS+PAP is secure. In fact, TTLS uses TLS encryption to protect your passwords when they are sent over the network. This is the same TLS encryption you use every day to log into web sites such as GMail, outlook.com, Facebook, etc. So if you trust TLS (via HTTPS) for your web surfing, you should also trust it for TTLS.
Is EAP-TLS more secure than PEAP?
PEAP-MSCHAPv2: Which Authentication Protocol is Superior? PEAP-MSCHAPv2 leaves your organization vulnerable to cyber attacks. EAP-TLS is a superior authentication protocol that uses digital certificates as opposed to credentials.
How does EAP work authentication?
The EAP authentication exchange proceeds as follows: 1) The authenticator (the server) sends a Request to authenticate the peer (the client). 2) The peer sends a Response packet in reply to a valid Request. 3) The authenticator sends an additional Request packet, and the peer replies with a Response.
What EAP method should I use for WiFi?
PEAPFor "EAP method" select "PEAP". For "Phase 2 authentication" select "MSCHAPV2". If you are using the Nougat (7) OS on your Android, set "CA Certificate" to "Use system certificates" and "Domain" to "ed.ac.uk".
What is the primary benefit of using EAP as an authentication mechanism?
What is the primary benefit of using EAP-TTLS for authentication? The client must have a certificate. The client does not have to have a certificate.
What is EAP TLS?
More colloquially, EAP-TLS is the authentication protocol most commonly deployed on WPA2-Enterprise networks to enable the use of X.509 digital certificates for authentication. EAP-TLS is considered the gold standard for network authentication security, but despite being universally recognized as ultra-secure, it’s still not widely implemented.
What are the advantages of EAP TLS?
There are two primary advantages of EAP-TLS: 1 EAP-TLS is the strongest authentication security. The use of X.509 digital certificates makes the protocol the undisputed champion, especially when those certificates are encrypted using modern techniques like elliptical curve cryptography (ECC). 2 The end user experience in an EAP-TLS network is almost universally better than in credential-based networks. Certificates can’t be shared or removed from a device, so there’s no need for constant password-reset policies to maintain secure credentials. A certificate validity period is usually years-long instead of a password’s typical 90-day life.#N#Furthermore, users don’t need to remember passwords at all – certificates authenticate automatically. They can also be provisioned (or revoked) automatically and are easy to manage with a CMS like the one included in the SecureW2 Managed PKI.
How does EAP-TLS work?
It doesn’t rely on overly complicated encryption schemes or anything like that – it’s predicated on the strength of public key cryptography.
What is the difference between PEAP and EAP-TLS?
What’s the difference between PEAP and EAP-TLS? PEAP is an EAP protocol, despite the fact that it breaks the naming convention a little bit. The ‘P’ in ‘PEAP’ stands for “Protected” (Extensible Authentication Protocol).
What is server certificate validation?
Server certificate validationrequires both the client and the server to validate their identity, so a device configured for EAP-TLS authentication (and thus server certificate validation) won’t ever mistake a spoofed AP for the real one.
What is a spoofed access point?
Those hacks usually rely on spoofed access points (AP) to fool users’ devices into automatically attempting to authenticate to the fake AP. The device will automatically submit real credentials without the user’s knowledge, allowing the hacker to farm credentials with little effort.
Is EAP TLS good for MDM?
Fortunately, EAP-TLS is much more viable with automated device onboarding solutions for BY OD and MDM like SecureW2’s JoinNow MultiConnector. Streamlined onboarding makes configuration a simple task, making premium Wi-Fi security viable for a larger proportion of organizations.
What is a tunnel in EAP TTLs?
On EAP-TTLS, you are right again. After the server is securely authenticated to the client via its CA certificate and optionally the client to the server, the server can then use the established secure connection ("tunnel") to authenticate the client.
How many Q&A communities are there on Stack Exchange?
Stack Exchange network consists of 178 Q&A communities including Stack Overflow, the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Is PEAP an encapsulation?
PEAPis an encapsulation, is not a method, but you are almost right again. PEAP is similar in design to EAP-TTLS, requiring only a server-side PKI certificate to create a secure TLS tunnel to protect user authentication, and uses server-side public key certificates to authenticate the server. It then creates an encrypted TLS tunnel between the client and the authentication server.
Do you need a certificate for EAP TLS?
On EAP-TLS you are right, both sides require a certificate. With a client-side certificate, a compromised password is not enough to break into EAP-TLS enabled systems because the intruder still needs to have the client-side certificate.
Is client authentication optional?
Whereas with EAP-TTLS, client authentication seems optional according to the RFC and the TLS handshake is only done to create a secure tunnel which can be used to perform other authentication methods . Is that right?
What is EAP tunnel?
Both protocols are considered EAP methods, so they each send identifying information through the encrypted EAP tunnel. This encrypted tunnel prevents any outside user from reading the information being sent over-the-air. However, the process for the end user differs significantly between the two protocols.
What is EAP in WPA2?
The most widely used wireless network protocols today are the Extensible Authentication Protocols (EAP) used in WPA2-Enterprise. Utilizing an EAP authentication method ensures that users’ information is sent over-the-air using encryption and avoids interception. Read here how SecureW2 helped a marketing firm provide comprehensive authentication security for all their personal and managed devices.
What is a TLS handshake?
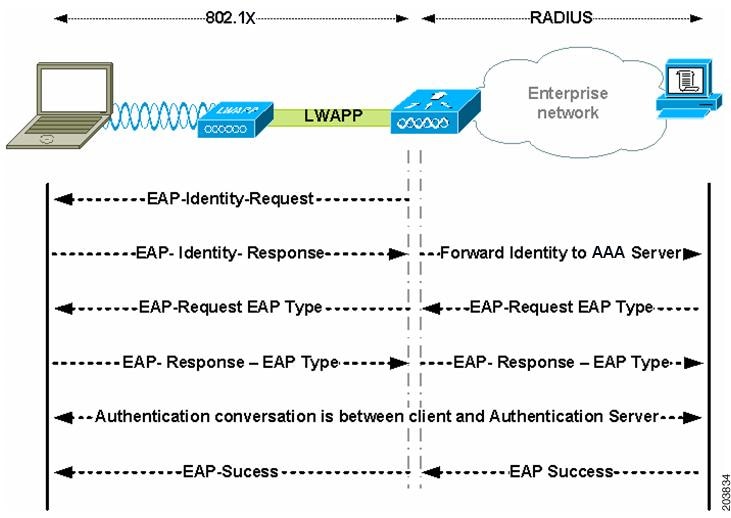
This is the communication process in which the server and client exchange identifying information. The two sides will verify one another’s identity, establish encryption algorithms, and agree on session keys to securely authenticate to the network. Below are images from the Certified Wireless Security Professional Study Guide detailing the process for both authentication protocols.
How does PEAP MSCHAPv2 work?
With PEAP-MSCHAPv2, the user must enter their credentials to be sent to the RADIUS Server that verifies the credentials and authenticates them for network access. EAP-TLS utilizes certificate-based authentication. Rather than sending credentials to the RADIUS Server over-the-air, credentials are used for a one-time certificate enrollment, and the certificate is sent to the RADIUS server for authentication.. Over the course of the user’s lifetime with the organization, being able to auto-authenticate without having to memorize a password or update due to a password change policy is a huge benefit to the user experience.
How to bypass support tickets and security risks of manual configuration?
To bypass the support tickets and security risks of manual configuration, it’s recommended that you deploy an onboarding software to automatically configure new users. SecureW2’s JoinNow onboarding solution configures users accurately with in a few steps. They simply identify themselves and once approved, their devices are securely configured for network access using EAP-TLS or PEAP-MSCHAPv2 authentication.. The process is fast, simple, and ensures all users are correctly configured.
Why is it important to secure wireless networks?
Ensuring network users are able to securely authenticate to the wireless network is paramount to the overall safety and security of your organization. So many attacks are aimed at exploiting the authentication process. According to IBM’s X-Force Threat Intelligence Index, 35% of exploitation activity involves Man-in-the-Middle Attacks.
What happens if your Radius is overloaded with authentication requests?
Additionally, if your RADIUS is overloaded with authentication requests and does not have redundancy measures, your network could experience request denials and time-consuming delays. For the sake of productivity, a shorter process can make a big difference.
How Does EAP-TLS Work?
Is EAP-TLS Secure?
- EAP-TLS is widely regarded as the most secure authentication protocol for 802.1X networks. The requirement for mutual certificate authentication has kept the protocol not just relevant, but dominant, for over 15 years. One of the primary security benefits of EAP-TLS networks is the ability to perform server certificate validation. This technique re...
Benefits of EAP-TLS
- There are two primary advantages of EAP-TLS: EAP-TLS is the strongest authentication security. The use of X.509 digital certificates makes the protocol the undisputed champion, especially when those certificates are encrypted using modern techniques like elliptical curve cryptography (ECC). Since digital certificates are tied to specific devices, your network visibility is drastically i…
Does EAP-TLS Require Certificates?
- Technically, the standard does not mandate the use of X.509 digital certificates. In reality, however, omitting certificates would negate the security benefits of the protocol and render much of the infrastructure pointless. Since EAP-TLS requires mutual authentication, you’re unlikely to ever find an implementation that does not require client-side certificates.
Alternate EAP Methods
- Extensible Authentication Protocol is not itself a wire protocol – it only defines a message format. The simple, utilitarian foundation has paved the way for a number of different strategies to encapsulate and protect EAP messages. Many different EAP methods have been defined, though only a few of them see widespread use. Here’s a list of methods you might encounter: 1. EAP Tu…