The major distinction is that a firewall blocks and filters network traffic, but an IDS/IPS detects and alerts an administrator or prevents the attack, depending on the setup. A firewall permits traffic depending on a set of rules that have been set up. It is based on the source, destination, and port addresses.
| Firewall | IDS | IPS |
|---|---|---|
| Placed at the perimeter of the network. Is the first line of defense | Placed after firewall | Placed after firewall |
| Does not analyze traffic patterns | Analyses traffic patterns | Analyses traffic patterns |
| Blocks malicious packets | Raises alert for malicious packets | Blocks malicious packets |
What is the full form of IPS ID?
FIREWALL IPS IDS; Abbreviation for-Intrusion Prevention System: Intrusion Detection System: Philosophy: Firewall is a network security device that filters incoming and outgoing network traffic based on predetermined rules: IPS is a device that inspects traffic, detects it, classifies and then proactively stops malicious traffic from attack.
What is the difference between a firewall and an IPS?
This is pretty similar to a firewall when it is applied to a network. That is because IPS stands between the external world (the internet) and your local area network. IPS is designed to deny network traffic proactively. It takes control of the traffic based on a security profile. As a result, it can detect known security threats.
What is the difference between a firewall and an IDS?
Firewalls limit access between networks to prevent intrusion and do not signal an attack from inside the network. An IDS evaluates a suspected intrusion once it has taken place and signals an alarm. An IDS also watches for attacks that originate from within a system.
What is the difference between IDS vs IPS?
IDS vs IPS - What's the Difference & Which do You Need? Intrusion Detection Systems ( IDS) and Intrusion Prevention Systems ( IPS) are two tools that network administrators use to identify cyber-attacks. IDS and IPS tools are both used to discover online threats but there is a distinct difference in how they operate and what they do.

Is a firewall an IDS?
IDS vs Firewalls An IDS provides no actual protection to the endpoint or network. A firewall, on the other hand, is designed to act as a protective system. It performs analysis of the metadata of network packets and allows or blocks traffic based upon predefined rules.
Is a firewall an IPS?
IPS was originally developed to work side-by-side with your network firewall. While firewalls filter network traffic and block traffic that's not approved, the IPS is designed to analyze the content of that traffic in real time to detect and prevent attacks.
Is IPS firewall A IDS?
The major distinction is that a firewall blocks and filters network traffic, but an IDS/IPS detects and alerts an administrator or prevents the attack, depending on the setup. A firewall permits traffic depending on a set of rules that have been set up. It is based on the source, destination, and port addresses.
What is the difference between firewall and IPS and IDS?
Essentially, firewalls are designed to limit access between networks to prevent intrusion but do not prevent attacks from inside a network. IDS and IPS send alerts when they suspect intrusion and also monitor for attacks from within a network.
Can an IPS replace a firewall?
An IPS can also trigger actions like closing access points and changing firewall configuration. IPS works like a combination of an intrusion detection system (IDS) and a firewall. Sometimes, IPS and IDS may be part of a network security solution that resembles a firewall.
Is firewall safer than IDS?
Firewalls are most visible part of a network to an outsider. Hence, more vulnerable to be attacked first. (A gateman will be the first person attacked by a thief!!) IDS are very difficult to be spotted in a network (especially stealth mode of IDS).
What are the 3 types of firewalls?
Firewall delivery methodsHardware-based firewalls. A hardware-based firewall is an appliance that acts as a secure gateway between devices inside the network perimeter and those outside it. ... Software-based firewalls. A software-based firewall, or host firewall, runs on a server or other device. ... Cloud/hosted firewalls.
What is IDS and IPS examples?
An intrusion detection system (IDS) monitors traffic on your network, analyzes that traffic for signatures matching known attacks, and when something suspicious happens, you're alerted. In the meantime, the traffic keeps flowing. An intrusion prevention system (IPS) also monitors traffic.
How does firewall act as IPS?
It blocks the offending user account or source IP address that attempts to access the target host, application, or other resources unethically. As soon as an IPS detects an intrusion event, it can also reconfigure or reprogram the firewall to prevent the similar attacks in future.
Can IDPS replace a firewall?
An IDPS is not a replacement for either a firewall or a good antivirus program. Rather, it is used in conjunction with your standard security products to increase your system specific or network-wide security.
How does firewall act as IPS?
It blocks the offending user account or source IP address that attempts to access the target host, application, or other resources unethically. As soon as an IPS detects an intrusion event, it can also reconfigure or reprogram the firewall to prevent the similar attacks in future.
What are IPS devices?
An intrusion prevention system (IPS) is an automated network security device used to monitor and respond to potential threats. Like an intrusion detection system (IDS), an IPS determines possible threats by examining network traffic.
Can firewalls block IPS?
Your firewall can also block certain IP addresses from connecting to your server. On a Windows server, you do this by logging into your server via RDP and creating a new firewall rule listing the IP addresses you want to block.
How important is IPS in firewall?
Intrusion Prevention Systems (IPS) If it detects in real time that a particular traffic flow is potentially dangerous, then those data packets are blocked or dropped – either way, they're denied entry. An Intrusion Prevention System sits as an extra vital layer of protection for your users.
Is a firewall an IDS or IPS?
Yes. True next-generation firewalls contain IDS and IPS functionality. However, not all firewalls are next-generation firewalls. Also, a firewall b...
How are IDS and IPS implemented?
An Intrusion Detection System (IDS) is responsible for identifying attacks and techniques and is often deployed out of band in a listen-only mode s...
Can an IPS block traffic?
Yes. An IPS constantly monitors traffic for known exploits to protect the network. The IPS then compares the traffic against existing signatures. I...
What can an IDS detect?
An IDS detects threats based on patterns of known exploits, malicious behaviors, and attack techniques. An effective IDS also detects evasive techn...
Can an IPS prevent DDoS?
An IPS can prevent certain types of DDoS (distributed denial of service) attacks. For example, application denial of service (AppDoS) attacks are o...
What IDS and IPS technologies, solutions, and products does Juniper offer?
Juniper offers both IDS and IPS solutions via a single software subscription deployed on any of Juniper’s next-generation firewall products and ser...
What is IDS and IPS?
These security measures are available as intrusion detection systems (IDS) and intrusion prevention systems (IPS), which become part of your network to detect and stop potential incidents.
How Does IDS Work?
The three IDS detection methodologies are typically used to detect incidents.
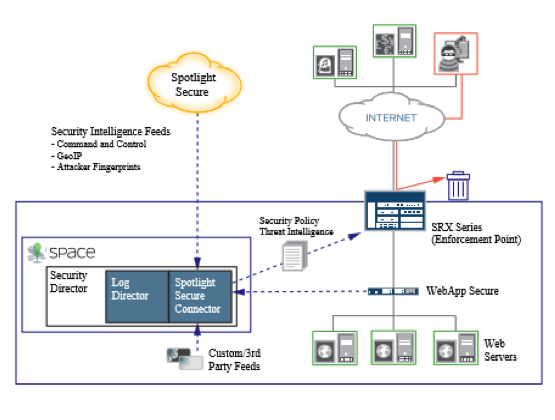
What is SRX gateway?
Juniper Networks uses its SRX Series Services Gateways for intrusion detection and prevention (IDP) services. You can selectively enforce various attack detection and prevention techniques on the network traffic passing through your chosen SRX Series device. You can define policy rules to match a section of traffic based on a zone, a network, or an application, and then take active or passive preventative actions on that traffic. The SRX Series device contains a full set of IPS signatures to secure networks against attacks. Juniper Networks regularly updates the predefined attack database. The SRX Series device can forward packet capture (PCAP) data from its traffic to a Juniper Secure Analytics (JSA) appliance using the PCAP Syslog Combination Protocol.
What is SRX policy?
You can define policy rules to match a section of traffic based on a zone, a network, or an application, and then take active or passive preventative actions on that traffic. The SRX Series device contains a full set of IPS signatures to secure networks against attacks.
What is intrusion prevention?
Intrusion prevention is the process of performing intrusion detection and then stopping the detected incidents. These security measures are available as intrusion detection systems (IDS) and intrusion prevention systems (IPS), which become part of your network to detect and stop potential incidents.
What is Juniper Mist Cloud?
The Juniper Mist Cloud delivers a modern microservices cloud architecture to meet your digital transformation goals for the AI-Driven Enterprise.
What is signature based detection?
Signature-Based Detection compares signatures against observed events to identify possible incidents. This is the simplest detection method because it compares only the current unit of activity (such as a packet or a log entry, to a list of signatures) using string comparison operations.
What is an IDS device?
IDS is a passive device which watches packets of data traversing the network, comparing with signature patterns and setting off an alarm on detection on suspicious activity. On the contrary, IPS is an active device working in inline mode and prevent the attacks by blocking it.
What is the difference between IPS and firewall?
The main difference being that firewall performs actions such as blocking and filtering of traffic while an IPS/IDS detects and alert a system administrator or prevent the attack as per configuration. A firewall allows traffic based on a set of rules configured.
What is an IDS firewall?
A firewall can deny any traffic that does not meet the specific criteria. IDS is a passive device which watches packets of data traversing the network, comparing with signature patterns and setting off an alarm on ...
What is firewall IPS?
Firewall is a network security device that filters incoming and outgoing network traffic based on predetermined rules. IPS is a device that inspects traffic, detects it, classifies and then proactively stops malicious traffic from attack.
What is an intrusion detection system?
An intrusion detection system (IDS) is a device or software application that monitors a traffic for malicious activity or policy violations and sends alert on detection.
What is configuration mode?
Configuration mode. Layer 3 mode or transparent mode. Inline mode , generally being in layer 2. Inline or as end host (via span) for monitoring and detection. Placement. Inline at the Perimeter of Network. Inline generally after Firewall. Non-Inline through port span (or via tap) Traffic patterns.
Firewalls
A firewall employs rules to filter incoming and outgoing network traffic. It uses IP addresses and port numbers to filter traffic. It can be set to either Layer 3 or transparent mode. The firewall should be the first line of defense and installed inline at the network’s perimeter.
Intrusion Prevention System (IPS)
IPS is a device that inspects, detects, classifies, and proactively prevents harmful traffic. It examines real-time communications for attack patterns or signatures and then blocks attacks when they have been detected. Placement and configuration in inline mode and generally being in Layer 2 after the firewall.
Intrusion Detection System (IDS)
IDS is either a hardware or software program that analyzes incoming network traffic for malicious activities or policy breaches (network behavior analysis) and issues alerts when they are detected. It detects real-time traffic and searches for attack signatures or traffic patterns, then sends out alarms.
What is an IPS? and What Does it Do?
An IPS (also known as an intrusion detection prevention system or IDPS) is a software platform that analyses network traffic content to detect and respond to exploits. The IPS sits behind the firewall and uses anomaly detection or signature-based detection to identify network threats.
Why are IDS and IPS Solutions Important?
IDS and IPS solutions are meaningful because they can identify cyberattacks that can damage a company’s information assets. The consequences of a cyber attack can be dramatic. The average cost of a malware attack on a company is $2.4 million. IS and IPS tools provide you with the means to detect cyber attacks.
Will a NGFW replace an IPS?
There are many similarities between the capabilities of IPS and the next-generation firewall. However, do not forget that the reason that IDS was first thought of was because security analysts determined that, no matter how strong a firewall is, some malicious traffic will always get through. IPSs are IDSs with added mitigation strategies. So, a firewall operates at the boundary of the network to block all malicious traffic and the IPS operates within the network as a second line of defense.
How are IDS and IPS solutions used?
IDS and IPS solutions that use signature-based detection look for attack signatures, activity, and malicious code that match the profile of known attacks. Attacks are detected by examining data patterns, packet headers, source addresses, and destinations.
Why are IDS and IPS important?
IDS and IPS solutions are meaningful because they can identify cyberattacks that can damage a company’s information assets. The consequences of a cyber attack can be dramatic. The average cost of a malware attack on a company is $2.4 million. IS and IPS tools provide you with the means to detect cyber attacks.
What is an IDS platform?
Briefly, an IDS platform can analyze network traffic for patterns and recognize malicious attack patterns. IPS combines the analysis functionality of an IDS with the ability to intervene and prevent the delivery of malicious packets. To put it simply, IDS systems detect, and IPS tools prevent.
What is an IDS alert?
The IDS monitors network traffic and sends an alert to the user when it identifies suspicious traffic. After receiving the alert the user can take action to find the root cause and remedy it. To detect bad traffic, IDS solutions come in two variations: a Network Intrusion Detection System (NIDS) and a Host Intrusion Detection System (HIDS).
What Is an IPS?
You want to stop an attack as soon as it's discovered, even if that means closing down legitimate traffic for security concerns. An intrusion protection system (IPS) could be just right for you.
Why use IPS or IDS?
Choose an option like this, and you could use the IPS for active network security while the IDS gives you a deep understanding of how the traffic moves across your network.
What is IPS monitoring?
No matter what type you choose, the IPS will take a predictable set of steps. An IPS monitors your network for suspicious activity or attacks in progress. When an anomaly is spotted, you're alerted.
What is an IPS system?
An intrusion protection system (IPS) could be just right for you. The goal of an IPS is to prevent damage. While you're kept in the loop about the attack, the system is already working to keep things safe. An IPS can protect against exterior intruders.
What is machine learning?
Machine learning. The system picks up information about everything that happens on your server in an average day, and that data helps to refine the protections in place. A system like this comes with plenty of advantages. You can set one up very quickly, and it's hard for attackers to spot your protections.
How does IPS work?
The IPS works in real time, and the technology inspects every packet moving through the protected space. It can take swift and significant action in response to an attack, and while that can keep you protected, these systems can throw up false positives. When that happens, traffic can slow for no reason whatsoever.
What does prior attack mean?
Prior attacks. The technology flags anything on your server that's been used in a known and successful attack on another server.
Why is an IPS connected in line?
As shown from the network topology above (Firewall with IPS), the IPS device is usually connected behind the firewall but in-line the communication path which transmits packets to/from the internal network.
What is an IDS?
An IDS (Intrusion Detection System) is the predecessor of IPS and is passive in nature. As shown from the network above (Firewall with IDS), this device is not inserted in-line with the traffic but rather it is in parallel (placed out-of-band).
Why is IPS placement required?
The above placement is required in order for the IPS device to block malicious traffic immediately before reaching internal servers.
What happens if IDS is detected?
If a security anomaly is detected in the network traffic, the IDS will just raise an alarm ( to the administrator) but it will not be able to block the traffic. Similarly to IPS, the IDS device also uses mostly signatures of known security attacks and exploits in order to detect an intrusion attempt. In order to send traffic to the IDS, the switch ...
What is the most common type of firewall?
Firewall. There are several types of firewalls but the most common one is the hardware network firewall . As you can see from all network diagrams in this article, the network firewall is found in all network designs since it’s the cornerstone of network security. The core function of a firewall is to allow or block traffic between source ...
What is stateful firewall?
Moreover, a network firewall is stateful. This means that the firewall keeps track of the states of connections that pass through it.
Why does the internal host keep the connection inside the connection table?
For example, if an internal host successfully accesses an Internet website through the firewall, the latter will keep the connection inside its connection table so that reply packets from the external webserver will be allowed to pass to the internal host because they already belong to an established connection.
What can IPS and IDS do to enhance your cybersecurity?
In this IDS VS. Firewall VS. IPS comparison, we will explain the importance of IPS and IDS. In general, network administrators and anyone concerned about cybersecurity take IPS and IDS very seriously. Why do they do that? Let’s find it out. Basically, security teams have a huge challenge to face the threat of data breaches and compliance fines. The threats are growing at a rapid speed, and there is absolutely no chance for poorly secured systems. The teams are always on the lookout for potential solutions that don’t cost a fortune. In other words, every single individual wants to find a cost-effective way to fight against cyber-threats. This is exactly when IDS/IPS technology comes to play. In general, IDS and IPS combination covers a pretty large area of a good cybersecurity system.
What is IPS in security?
That is because IPS stands between the external world (the internet) and your local area network. IPS is designed to deny network traffic proactively. It takes control of the traffic based on a security profile. As a result, it can detect known security threats.
Why is IPS important?
One of the most important things associated with IDS and IPS systems is that they are very much automated. That means you can use them in the existing security stack without any issue. IPS offers significant peace of mind for network administrators. That is particularly because of its ability to protect a network from known threats using minimal resources.
What is the difference between IDS and firewall?
If there is any traffic that does not meet the criteria of the firewall, that will be denied. ID S, on the other hand, is a passive device.
What is an IDS system?
IDS is the shortened form of Intrusion Detection Systems. This is a system that is developed to analyze and monitor traffic on a given network. It specifically keeps track of the potential attackers that use known cyber-threats to grab data from your network.
What is firewall security?
The concept. Basically, a firewall is a network security system that can filter both incoming and outgoing traffic on a network. It blocks or allows traffic based on rules that are preconfigured. It can be hardware, software, or a combination of both.
What is the importance of IDS and IPS?
Having an IDS, IPS, and a firewall on your network can significantly minimize the potential threats. Such systems can prevent your network from a variety of threats. However, to make it a complete system, you must be smart enough to take other measures as well.
How Does an Intrusion Prevention System Differ from a Firewall?
Depending on the generation of the Firewall, it can even go beyond that to inspect the payload. But once the packet passed the firewall into the trusted network undetected, maybe riding on top of another legitimate protocol like HTTP, the malicious content inside that packet may get the freedom required to fulfill its malicious goals. Here comes the role of the Intrusion Prevention System IPS to add those extra features to the ones offered by Firewalls:
What is NGIPS in intrusion prevention?
8. Integration with Sandboxing analysis (NGIPS): gives the Next Generation Intrusion Prevention System the ability to execute malicious files and contents inside a simulation sandbox, thus allowing it to closely and accurately study and monitor its behavior before hitting the real hosts and computers to achieve 100% true malicious content detection.
What is IPS signature based detection?
1. Signature-based detection: Intrusion Prevention System IPS does contain a large database with signatures for the different known attacks. Those signatures have been collected over the years using previously known attacks. The database is updated frequently to keep the signature database up to date as much as possible. Actually, the richer and the more frequently updated database can be an important indicator of the strength of the Intrusion Prevention System vendor.
What is IPS in security?
Intrusion Prevention System IPS is a network security/threat prevention technology that examines network traffic flows to detect and prevent vulnerability exploits. Vulnerability exploits usually come in the form of malicious inputs to a target application or service that attackers use to interrupt and gain control of an application or machine. Following a successful exploit, the attacker can disable the target application (resulting in a denial-of-service state), or can potentially access all the rights and permissions available to the compromised application.
What is anomaly based detection?
Anomaly-based detection: unlike firewalls, which are static in their nature, Intrusion Prevention Systems can monitor the network in which they are deployed in. They can collect information about it to build a baseline for traffic considered as normal. This is called the Normal Behavior of the network.
Why is it important to place IPS behind firewall?
It places them directly in front of untrusted networks (like the internet) that can easily overwhelm the IPS system. This is why the best practice is to place the IPS (either physical appliance or virtual one) behind the firewall. Like this, you will handle the basic filtering.
What is context awareness?
5. Contextual Awareness (NGIPS): offers a deep knowledge of the protected network in order to better evaluate different events and discover any potential attacks.
