
What is OWASP used for?
Web security standards with the Open Web Application Security Project The Open Web Application Security Project (OWASP) focuses on improving the security of software. OWASP has made a range of tools to help meet web security standards, including automatically identifying security vulnerabilities in web applications.
What is OWASP ASVs?
What is the ASVS? The OWASP Application Security Verification Standard (ASVS) Project provides a basis for testing web application technical security controls and also provides developers with a list of requirements for secure development.
What is OWASP-Automated threats to web applications?
OWASP Automated Threats to Web Applications: Published July 2015 - the OWASP Automated Threats to Web Applications Project aims to provide definitive information and other resources for architects, developers, testers and others to help defend against automated threats such as credential stuffing.
What is internal verification in OWASP?
Internal Verification – The technical assessment of specific aspects of the security architecture of an application as defined in the OWASP ASVS. Cryptographic module – Hardware, software, and/or firmware that implements cryptographic algorithms and/or generates cryptographic keys.
See more
Is OWASP a framework?
The OWASP Security Knowledge Framework is an open source web application that explains secure coding principles in multiple programming languages. The goal of OWASP-SKF is to help you learn and integrate security by design in your software development and build applications that are secure by design.
What is OWASP certification?
Description. The OWASP Online Academy provides free online training and learning of Web Application Security, Mobile Testing, Secure Coding designed and delivered by the experts around the world. Currently the OWASP online academy project Website is on alpha-testing stage.
What is OWASP?
Definition. The Open Web Application Security Project (OWASP) is a nonprofit foundation dedicated to improving software security. It operates under an “open community” model, which means that anyone can participate in and contribute to OWASP-related online chats, projects, and more.
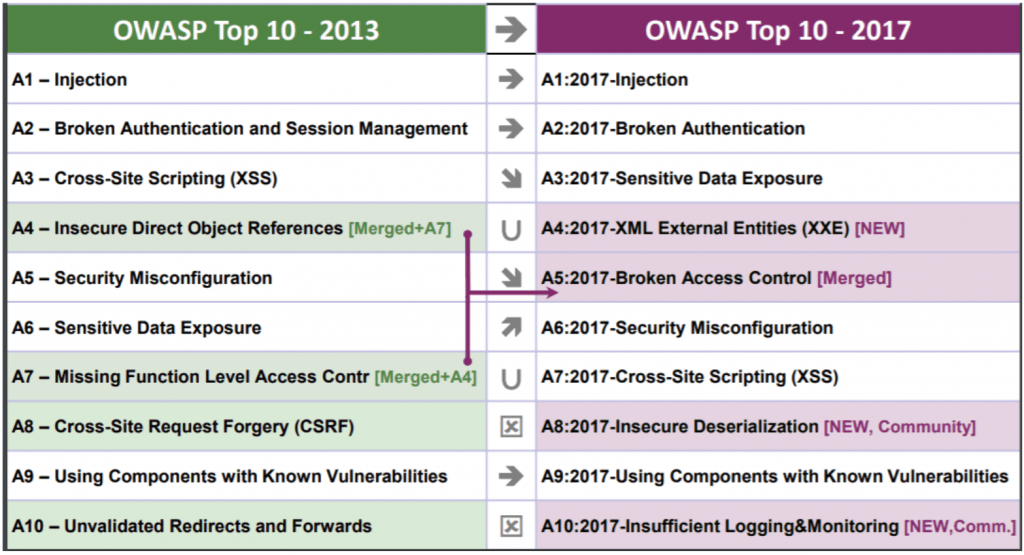
What are the top 10 OWASP?
OWASP Top 10 VulnerabilitiesSensitive Data Exposure. ... XML External Entities. ... Broken Access Control. ... Security Misconfiguration. ... Cross-Site Scripting. ... Insecure Deserialization. ... Using Components with Known Vulnerabilities. ... Insufficient Logging and Monitoring.More items...
What is Owasp vulnerability?
What Is an OWASP Vulnerability? OWASP vulnerabilities are security weaknesses or problems published by the Open Web Application Security Project. Issues contributed by businesses, organizations, and security professionals are ranked by the severity of the security risk they pose to web applications.
Why OWASP Top 10 is important?
The OWASP Top 10 is a standard awareness document for developers and web application security. It represents a broad consensus about the most critical security risks to web applications. Globally recognized by developers as the first step towards more secure coding.
Why is OWASP necessary?
The OWASP Top 10 is important because it gives organisations a priority over which risks to focus on and helps them understand, identify, mitigate, and fix vulnerabilities in their technology. Each identified risk is prioritised according to prevalence, detectability, impact and exploitability.
How is OWASP implemented?
OWASP top 10 Proactive Controls 2020Define Security Requirements.Leverage Security Frameworks and Libraries.Secure Database Access.Encode and Escape Data.Validate All Inputs.Implement Digital Identity.Enforce Access Controls.Protect Data Everywhere.More items...•
How is OWASP used?
OWASP seeks to educate developers, designers, architects and business owners about the risks associated with the most common web application security vulnerabilities. OWASP supports both open source and commercial security products.
How do you pronounce OWASP in English?
0:123:33Whiteboard Wednesday: An Intro to the OWASP Top 10 - YouTubeYouTubeStart of suggested clipEnd of suggested clipToday I'm going to talk to you about the OWASP top 10.MoreToday I'm going to talk to you about the OWASP top 10.
What is the top OWASP vulnerability for 2021?
The Top 10 OWASP vulnerabilities in 2021 are:Broken Access Control.Cryptographic Failures.Injection.Insecure Design.Security Misconfiguration.Vulnerable and Outdated Components.Identification and Authentication Failures.Software and Data Integrity Failures.More items...•
What is Log4j vulnerability?
Last week, a vulnerability was found in Log4j, an open-source logging library commonly used by apps and services across the internet. If left unfixed, attackers can break into systems, steal passwords and logins, extract data, and infect networks with malicious software.
Does OWASP have a certification?
The OWASP Top 10 Certification Exam (Foundation) consists of several multiple-choice questions based on the fundamental of this program.
What is OWASP in testing?
OWASP pen testing describes the assessment of web applications to identify vulnerabilities outlined in the OWASP Top Ten. An OWASP pen test is designed to identify, safely exploit and help address these vulnerabilities so that any weaknesses discovered can be quickly addressed.
How does OWASP work?
The Open Web Application Security Project (OWASP), is an online community that produces free, publicly-available articles, methodologies, documentation, tools, and technologies in the field of web application security. Open source components have become an integral part of software development.
What is Level 2 OWASP?
Level 2 is typically appropriate for applications that handle significant business-to-business transactions, including those that process healthcare information, implement business-critical or sensitive functions, or process other sensitive assets.
What is OWASP in web security?
The Open Web Application Security Project ( OWASP) is an online community that produces freely-available articles, methodologies, documentation, tools, and technologies in the field of web application security.
What is the OWASP testing guide?
OWASP Testing Guide: The OWASP Testing Guide includes a "best practice" penetration testing framework that users can implement in their own organizations and a "low level" penetration testing guide that describes techniques for testing most common web application and web service security issues. Version 4 was published in September 2014, with input from 60 individuals.
What is OWASP project?
The Open Web Application Security Project ( OWASP) is an online community that produces freely-available articles, methodologies, documentation, tools, and technologies in the field of web application security.
Who is the founder of the OWASP Foundation?
Mark Curphey started OWASP on September 9, 2001. Jeff Williams served as the volunteer Chair of OWASP from late 2003 until September 2011. As of 2015. [update] , Matt Konda chaired the Board. The OWASP Foundation, a 501 (c) (3) non-profit organization in the US established in 2004, supports the OWASP infrastructure and projects.
What is a webgoat?
Webgoat: a deliberately insecure web application created by OWASP as a guide for secure programming practices. Once downloaded, the application comes with a tutorial and a set of different lessons that instruct students how to exploit vulnerabilities with the intention of teaching them how to write code securely.
What is OWASP?
The Open Web Application Security Project (OWASP) is a non-profit organisation focused on improving the security of software.
Why is OWASP important?
In a nutshell, OWASP helps developers write better, more secure code and gives consumers a better understanding of what’s possible (both in terms of attack and mitigation).
What is OWASP project?
The Open Web Application Security Project (OWASP) focuses on improving the security of software. OWASP has made a range of tools to help meet web security standards, including automatically identifying security vulnerabilities in web applications.
How many categories are there in OWASP?
Many common attacks are covered by OWASP standards, which can be broken down into 13 categories:
Introduction
The primary aim of the OWASP Application Security Verification Standard (ASVS) Project is to provide an open application security standard for web apps and web services of all types.
Latest Stable Version - 4.0.3
The latest stable version is version 4.0.3 (dated October 2021), which can be found:
Standard Objectives
The requirements were developed with the following objectives in mind:
How To Reference ASVS Requirements
Each requirement has an identifier in the format <chapter>.<section>.<requirement> where each element is a number, for example: 1.11.3.
License
The entire project content is under the Creative Commons v3.0 license.
What is OWASP project?
OWASP (Open Web Application Security Project) is a community-driven non-profit organization that works to improve the security of software. Because OWASP is an “open” security project, all of its materials are freely available online and can be accessed by anyone. Perhaps one of their most notable projects is the OWASP Top Ten , which identifies the top 10 security risks to a web application.
Why use the OWASP Top 10?
Many companies and organizations use the OWASP Top 10 to help identify security risks to their applications and to help developers avoid introducing those issues into their codebase.
What is MASVS testing?
For mobile application testing, the MASVS (Mobile Application Security Verification Standard) has been introduced by OWASP and includes a similar set of ASVS requirements but specifically oriented toward mobile applications.
What is OWASP ASVS?
The OWASP ASVS is a community-driven effort to standardize security testing. It combines multiple existing standards such as PCI DSS, OWASP Top 10, NIST 800-63-3, and the OWASP Proactive Controls 2018 in a commercially workable format. Each requirement in the ASVS is mapped to the Common Weakness Enumeration (CWE).
What is an ASVS attestation?
One significant aspect of pursuing an ASVS attestation is the ongoing relationship between the business and the security company. Due to the nature of ASVS, there is considerable back and forth during the engagement. This ultimately leads to a very secure application and a third-party attestation from a trusted security company showing that the application has met the rigorous standards of the ASVS. For instance, a typical ASVS security test roadmap might look like: 1 The business requests an ASVS security test at a specific assurance level (Level 1, Level 2, Level 3) 2 The security company performs the test and provides line items showing which requirements were passed, which were failed, and a description, proof-of-concept, and remediation steps for each issue. 3 The business remediates the issues reported with guidance from the security company. 4 The security company provides a final report showing all requirements as passed and all issues as remediated. The security company provides a written third-party attestation that confirms that the application adheres to the standard at the appropriate assurance level.
What is a pensive security?
In addition to high-quality penetration testing, vulnerability assessments, and many other services, Pensive Security provides all three levels of OWASP ASVS attestations. These attestations have provided extremely high value to our customers and are essential to our client’s security roadmap. Often, OWASP ASVS attestations are one part of a longer-term security plan, which includes several services. These services are strategically organized into a security plan that reduces the overall security risk of a business and demonstrates security excellence to customers and partners.

Overview
Publications and resources
• OWASP Top Ten: The "Top Ten", first published in 2003, is regularly updated. It aims to raise awareness about application security by identifying some of the most critical risks facing organizations. Many standards, books, tools, and many organizations reference the Top 10 project, including MITRE, PCI DSS, the Defense Information Systems Agency (DISA-STIG), and the United States Federal Trade Commission (FTC),
History
Mark Curphey started OWASP-Open Web Application Security Project on September 9, 2001. Jeff Williams served as the volunteer Chair of OWASP from late 2003 until September 2011. As of 2015 , Matt Konda chaired the Board.
The OWASP Foundation, a 501(c)(3) non-profit organization in the US established in 2004, supports the OWASP infrastructure and projects. Since 2011, OWASP is also registered as a no…
Awards
The OWASP organization received the 2014 Haymarket Media Group SC Magazine Editor's Choice award.
See also
• Open Source Security Foundation
External links
• Official website