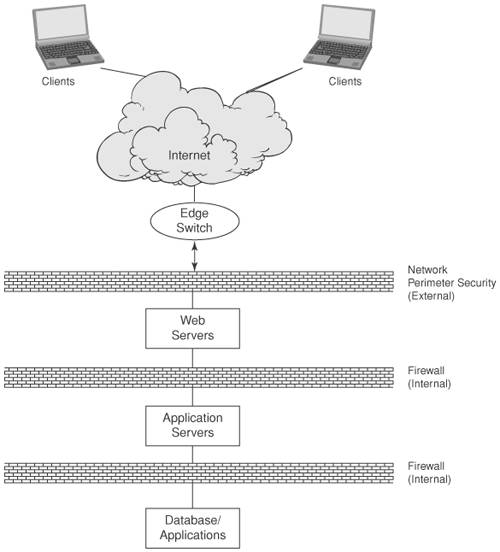
One of the better known set of Design Patterns for Security is SEI Secure Design Patterns: SEI Secure Design Patterns SEI Secure Design Patterns defines the following Secure Design Patterns: Secure Factory
Full Answer
What is a secure design pattern?
This report describes a set of secure design patterns, which are descriptions or templates describing a general solution to a security problem that can be applied in many different situations.
What are the benefits of reusable security patterns?
By using reusable security patterns, developers can reduce the cost associated with pro- ducing secure products while at the same time reducing the cost and the risk associated with secu- rity vulnerabilities for both developers and end users. 1.2.2 Approach The approach taken to define the patterns in this document is to
What are the security design principles of azure?
Security design principles describe a securely architected system hosted on cloud or on-premises datacenters (or a combination of both). Get an overview of Azure security technologies, guidance offerings, solution ideas, and reference architectures. Security priorities around governance, risk, and compliance.
What is the Open Group Guide to security patterns?
•Open Group Guide to Security Patterns [Blakely 2004]. This report contains architectural- level patterns and design-level patterns focusing on system availability and the protection of privileged resources. The patterns presented in this report are general patterns applicable to systems programmed in many different languages.
What is the purpose of secure factory?
What is a secure builder factory?
What is security-credential dependent selection?
What is secure design?
What is CMU/SEI-2009-TR-010?
How many secure design patterns were added to this report in the October 2009 update?
What is a design pattern?
See 4 more
About this website

What are the secure design patterns?
Secure design patterns are meant to eliminate the accidental insertion of vulnerabilities into code and to mitigate the consequences of these vulnerabilities.
What type of design pattern is factory?
The factory method is a creational design pattern, i.e., related to object creation. In the Factory pattern, we create objects without exposing the creation logic to the client and the client uses the same common interface to create a new type of object.
Which design pattern can be used to manage security?
The authenticator pattern is also known as the Pluggable Authentication Modules or Java Authentication and Authorization Service (JAAS). Security Context is a combination of the communication protection proxy, security context and subject descriptor pattern.
What is meant by a secure design?
“Secure By Design” refers to software that is developed from the ground up with the intention of making it as secure as possible. From the start, the software is engineered in a way that minimizes flaws which could compromise security after launch.
Which are the three types of factory method?
the abstract factory pattern, the static factory method, the simple factory (also called factory).
Is Singleton a factory?
As the above UML diagram shows, a singleton class has a single instance defined and we access it by the getInstance () method. So a singleton factory that is responsible for creating objects makes use of the getInstance method to return the same object (which is there in the class) again and again.
What is a security architecture pattern?
OSA IT security architecture patterns are based on architectural overview diagrams depicting a certain information usage context. These diagrams are then annotated with references to the NIST controls catalog. Some patterns that get used repeatedly across many IT Security Architectures are called modules.
What are the authorization patterns in cyber security?
What Are Authorization Patterns? These are security mechanisms that you can use to decide your client's privileges related to system resources. These system resources could be files, services, data, and application features built on your client's identity.
Which pattern should be used for file system implementation?
File System implementations use the composite design pattern as described previously.
Which is a secure design principles?
The main secure design principles are the following: a) Economy of mechanism: Keep the design as simple and small as possible. b) Fail-safe defaults: Base access decisions on permission rather than exclusion. c) Complete mediation: Every access to every object must be checked for authority (there and then).
What are the principles of secure design coding?
Confidentiality – only allow access to data for which the user is permitted. Integrity – ensure data is not tampered with or altered by unauthorized users. Availability – ensure systems and data are available to authorized users when they need it.
Which is not a secure coding practice?
Improper Logging and Log Handling.
What is the factory design pattern in Java?
The factory design pattern is used when we have a superclass with multiple sub-classes and based on input, we need to return one of the sub-class. This pattern takes out the responsibility of the instantiation of a class from the client program to the factory class.
What is another name of factory pattern?
The Factory Method Pattern is also known as Virtual Constructor.
What is the factory pattern used for?
Factory Method Pattern allows the sub-classes to choose the type of objects to create. It promotes the loose-coupling by eliminating the need to bind application-specific classes into the code.
What is Factory Method design pattern in C#?
Factory method is a creational design pattern which solves the problem of creating product objects without specifying their concrete classes. The Factory Method defines a method, which should be used for creating objects instead of using a direct constructor call ( new operator).
Secure Design Patterns - Carnegie Mellon University
Secure Design Patterns October 2009 • Technical Report Chad Dougherty, Kirk Sayre, Robert C. Seacord, David Svoboda, Kazuya Togashi (JPCERT/CC). In this report, the authors describe a set of general solutions to software security problems that can be applied in many different situations.
Categorization of Security Design Patterns
Categorization of Secure Design Patterns A thesis presented to the faculty of the Department of Computer and Information Sciences East Tennessee State University
SECURE DESIGN PRINCIPLES: How to Build Systems That Are ... - LinkedIn
First, it important to define the primary secure design principles. Different academic, research, or industry institutions may provide slight variations on this list contained, but the overall ...
Patterns for Security - OWASP
Security - 1 Classification, Facets, and Conceptual Space in Security Analysis and the Use of Patterns Dr. Michael Van Hilst Farquhar College of Arts and Sciences
Security patterns - Cloud Design Patterns | Microsoft Docs
Pattern Summary; Federated Identity: Delegate authentication to an external identity provider. Gatekeeper: Protect applications and services by using a dedicated host instance that acts as a broker between clients and the application or service, validates and sanitizes requests, and passes requests and data between them.
What is the purpose of secure factory?
The intent of the Secure Factory secure design pattern is to separate the security dependent logic involved in creating or selecting an object from the basic functionality of the created or selected object.
What is a secure builder factory?
The intent of the Secure Builder Factory secure design pattern is to separate the security depen-dent rules involved in creating a complex object from the basic steps involved in actually creating the object. A complex object is generally defined as a library object that is made up from many interrelated elements or digital objects [Arms 2000]. In the current context, a complex object is an object that makes use of several simpler objects.
What is security-credential dependent selection?
The security-credential dependent selection of the appropriate complex object builder is hid-den from the portions of the system that make use of the builder. An implementation of the Secure Builder Factory pattern operates as a black box supplying the appropriate builder to the caller. This in turn hides the security dependent complex object building behavior from the caller.
What is secure design?
Secure design patterns, as described by this report, provide general design guidance to eliminate the introduction of vulnerabilities into code or mitigate the consequences of vulnerabilities. Se- cure design patterns are not restricted to object-oriented design approaches but may also be ap- plied, in many cases, to procedural languages. These patterns are at a higher level of abstraction than secure coding guidelines. Secure design patterns differ from security patternsin that they do not describe specific security mechanisms (such as access control, authentication, and authorization (AAA) and logging), define secure development processes, or provide guidance on the configuration of existing secure systems. Three general classes of patterns are presented in this document:
What is CMU/SEI-2009-TR-010?
2| CMU/SEI-2009-TR-010 •Security Patterns: Integrating Security and Systems Engineering [Schumacher 2006]. This book contains a large number of patterns at varying levels of specificity. The patterns in this book range from high-level patterns involving the processes used to develop secure systems to design-level patterns addressing how to create objects with different access privileges.
How many secure design patterns were added to this report in the October 2009 update?
Six secure design patterns were added to this report in the October 2009 update:
What is a design pattern?
A pattern is a general reusable solution to a commonly occurring problem in design. Note that a design pattern is not a finished design that can be transformed directly into code. It is a descrip- tion or template for how to solve a problem that can be used in many different situations. Algo- rithms are not thought of as design patterns because they solve computational problems rather than design problems. Secure design patterns are meant to eliminate the accidental insertion of vulnerabilities into code and to mitigate the consequences of these vulnerabilities. In contrast to the design-level patterns popularized in [Gamma 1995], secure design patterns address security issues at widely varying levels of specificity ranging from architectural-level patterns involving the high-level design of the system down to implementation-level patterns providing guidance on how to implement por- tions of functions or methods in the system.
Why is factory pattern important?
The factory pattern can prove valuable in various application scenarios. Software where the concrete products to be created are unknownor are not defined in advancebenefits from the alternative approach for subclass management . Typical use cases include frameworksor class libraries, which have become virtually indispensable as a basic framework for the development of modern applications.
What are the advantages of factory design pattern?
Authentication systems also benefit from the advantages of the factory design pattern: Instead of a central class with various parameters that vary according to user authorization, the authentication process can be delegated to factory classes that make independent decisions about the handling of the respective user.
What is the goal of the factory method pattern?
The factory pattern aims to solve a fundamental problem in instantiation – i.e., the creation of a concrete object of a class – in object-oriented programming. In principle, creating an object directly within the class that needs or should use this object is possible, but very inflexible. It binds the class to this object and makes it impossible to change the instantiation independently of the class. This kind of code is avoided in the factory pattern approach by first defining a separate operation for creating the object – the factory method. As soon as this is called up, it generates the object instead of the class constructor already mentioned.
How does factory pattern work?
The factory pattern aims to solve a fundamental problem in instantiation – i.e., the creation of a concrete object of a class – in object-oriented programming. In principle, creating an object directly within the classthat needs or should use this object is possible, but very inflexible. It binds the class to this object and makes it impossible to change the instantiation independently of the class. This kind of code is avoided in the factory pattern approach by first defining a separate operationfor creating the object – the factory method. As soon as this is called up, it generates the object instead of the class constructor already mentioned.
What is factory method in software?
In software that is based on the factory method design pattern, the code of an object to be created (in this context also referred to as the “product”) is outsourced into a separate class . This abstract class, also called the “creator” or – matching the pattern – “factory”, delegates the object instantiation to a subclass (ConcreteCreator), which ultimately decides which product is created. For this purpose, the ConcreteCreator takes over the method createProduct () and returns a ConcreteProduct, which can optionally be extended by the Creator with production code before it is passed to the interface as a finished product.
What programming language is factory method?
Some of the best-known representatives include Java, JavaScript, C++, C#, Python, and PHP. The latter scripting language is also used in the following practical example, which is inspired by a German blog post by Phpmonkeys.
What is the factory method?
Among the many design strategies taught in this publication is the so-called factory method, which allows a class to delegate the creation of objects to subclasses. Concrete information on how to use this practical method is provided in particular by the factory method pattern, which is often today simply referred to as the factory pattern.
What is a design pattern?
In software engineering, a design pattern is a general reusable solution to a commonly occurring problem within a given context in software design. Wikipedia lists many different design patterns for example, but security is never mentioned.
Is security a one size fits all deal?
The thing about security is that it's never a one-size-fits-all sort of deal. Because of that you always have to adapt designs to apply to the threats you're willing to counter. A good security design pattern is just a good software design pattern.
What is security assurance?
Security provides confidentiality, integrity, and availability assurances against malicious attacks on information systems (and safety assurances for attacks on operational technology systems). Losing these assurances can negatively impact your business operations and revenue, as well as your organization’s reputation in the marketplace.
How does a dedicated host protect applications and services?
Protect applications and services by using a dedicated host instance that acts as a broker between clients and the application or service, validates and sanitizes requests, and passes requests and data between them.
What is a secure design pattern?
The term "design pattern" is often used to refer to any pattern which addresses issues of software architecture, design, or programming implementation. Secure Design Patterns gives the following defincitions. Pattern. Definition.
What is each pattern?
"Each pattern describes a problem which occurs over and over again in our environment, and then describes the core of the solution to that problem, in such a way that you can use this solution a million times over , without ever doing it the same way twice.” Christopher Alexander
What are principles in a system?
Principles provide the high level guidelines for a system. Patterns can be applied to implement these principles and allow use of known good solutions for common problems.
What is the purpose of secure factory?
The intent of the Secure Factory secure design pattern is to separate the security dependent logic involved in creating or selecting an object from the basic functionality of the created or selected object.
What is a secure builder factory?
The intent of the Secure Builder Factory secure design pattern is to separate the security depen-dent rules involved in creating a complex object from the basic steps involved in actually creating the object. A complex object is generally defined as a library object that is made up from many interrelated elements or digital objects [Arms 2000]. In the current context, a complex object is an object that makes use of several simpler objects.
What is security-credential dependent selection?
The security-credential dependent selection of the appropriate complex object builder is hid-den from the portions of the system that make use of the builder. An implementation of the Secure Builder Factory pattern operates as a black box supplying the appropriate builder to the caller. This in turn hides the security dependent complex object building behavior from the caller.
What is secure design?
Secure design patterns, as described by this report, provide general design guidance to eliminate the introduction of vulnerabilities into code or mitigate the consequences of vulnerabilities. Se- cure design patterns are not restricted to object-oriented design approaches but may also be ap- plied, in many cases, to procedural languages. These patterns are at a higher level of abstraction than secure coding guidelines. Secure design patterns differ from security patternsin that they do not describe specific security mechanisms (such as access control, authentication, and authorization (AAA) and logging), define secure development processes, or provide guidance on the configuration of existing secure systems. Three general classes of patterns are presented in this document:
What is CMU/SEI-2009-TR-010?
2| CMU/SEI-2009-TR-010 •Security Patterns: Integrating Security and Systems Engineering [Schumacher 2006]. This book contains a large number of patterns at varying levels of specificity. The patterns in this book range from high-level patterns involving the processes used to develop secure systems to design-level patterns addressing how to create objects with different access privileges.
How many secure design patterns were added to this report in the October 2009 update?
Six secure design patterns were added to this report in the October 2009 update:
What is a design pattern?
A pattern is a general reusable solution to a commonly occurring problem in design. Note that a design pattern is not a finished design that can be transformed directly into code. It is a descrip- tion or template for how to solve a problem that can be used in many different situations. Algo- rithms are not thought of as design patterns because they solve computational problems rather than design problems. Secure design patterns are meant to eliminate the accidental insertion of vulnerabilities into code and to mitigate the consequences of these vulnerabilities. In contrast to the design-level patterns popularized in [Gamma 1995], secure design patterns address security issues at widely varying levels of specificity ranging from architectural-level patterns involving the high-level design of the system down to implementation-level patterns providing guidance on how to implement por- tions of functions or methods in the system.
