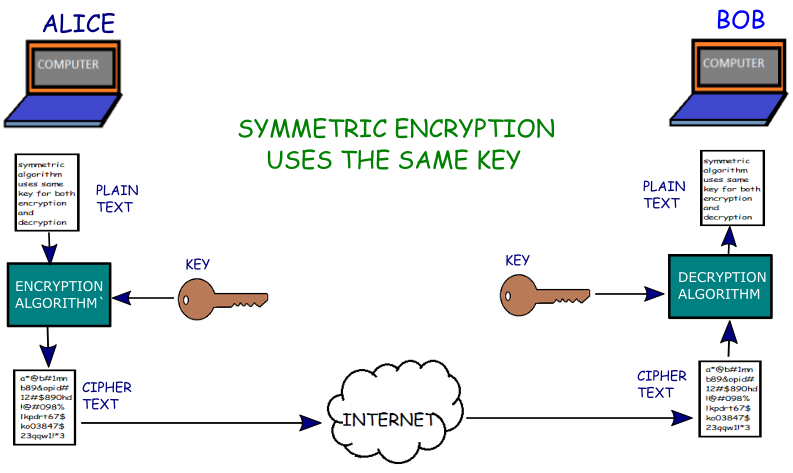
What are some examples of symmetric and asymmetric encryption?
What are some examples of symmetric and asymmetric encryption? Symmetric encryption uses a single shared key for both encryption and decryption. Asymmetric encryption uses two keys – public key and private key. Usually the data is encrypted using the public key and the cipher text is decrypted using the private key.
How are symmetric and asymmetric encryption algorithms differ?
Symmetric Vs Asymmetric Encryption Algorithms: The Best And Detailed Comparison
- Symmetric Encryption. In the case of symmetric encryption, the same key is used for both encrypting and decrypting messages.
- Asymmetric Encryption. Asymmetric encryption uses a pair of related keys — a public and a private key. ...
- 2 Common Use Cases for Symmetric Cryptography. ...
- 3 Common Use Cases for Asymmetric Cryptography. ...
Does a PKI use symmetric or asymmetric encryption?
PKI merges the use of both asymmetric and symmetric encryption. Both symmetric and asymmetric encryption have their own strengths and best use case scenarios, which is what makes the combination of both so powerful in Public Key Infrastructure .
Which two items are used in asymmetric encryption?
Asymmetric cryptography, which can also be called public-key cryptography, uses private and public keys to encrypt and decrypt the data. The keys are simply large numbers that are paired together; however, they are asymmetric means not identical. Public Key is One of the keys in the pair that can be shared with everyone, whereas Private key is ...
Is symmetric or asymmetric encryption better?
This process uses the same key for both encryption and decryption. Digital Signing: Asymmetric encryption is much better for digital signing, compared to symmetric encryption. The use of both a public and private key means the identity of the signer of the data can easily be known.
What is an advantage symmetric encryption has over asymmetric encryption?
Both methods require keys to decrypt and encrypt data. With symmetric encryption, the same key is used to encrypt and decrypt data, making it easy to deploy. Asymmetric encryption, on the other hand, relies on a public key for encryption and a private key for decryption.
Why is symmetric encryption more efficient?
Symmetric encryption is typically more efficient than asymmetric encryption. In symmetric encryption, only one key is used to both encrypt and decrypt, vs asymmetric encryption, where two different keys are used to encrypt and decrypt.
Is symmetric encryption faster than asymmetric?
Two different keys are now involved in encrypting and decrypting the data. Symmetric encryption is comparably much faster than asymmetric encryption, which is why it is still used massively today.
What is the main disadvantage of the symmetric encryption?
By far the biggest disadvantage of symmetric encryption is its use of a single, secret cryptographic key to encrypt and decrypt information.
What is the largest disadvantage of the symmetric encryption?
Which is the largest disadvantage of symmetric Encryption? Explanation: As there is only one key in the symmetrical encryption, this must be known by both sender and recipient and this key is sufficient to decrypt the secret message.
What is the problem with symmetric encryption?
Symmetric cryptography carries a high risk around key transmission, as the same key used to encrypt messages must be shared with anyone who needs to decrypt those messages.
When should symmetric encryption be used?
Due to the better performance and faster speed of symmetric encryption (compared to asymmetric), symmetric cryptography is typically used for bulk encryption / encrypting large amounts of data, e.g. for database encryption.
Is symmetric encryption still used?
Due to the better performance and faster speed of symmetric encryption, symmetric cryptography is typically used for bulk encryption of large amounts of data.
Why is asymmetric encryption slower?
Asymmetric encryption is slower than symmetric encryption due to the former's longer key lengths and the complexity of the encryption algorithms used. Both of these requirements are due to the fact that one of the keys is public.
Why is symmetric encryption less secure?
The main disadvantage of the symmetric key encryption is that all parties involved have to exchange the key used to encrypt the data before they can decrypt it.
Why is asymmetric cryptography bad for huge data?
Asymmetric encryption uses two separate keys and more complex algorithms in the encryption and decryption process, which makes it slower for encrypting and decrypting large amounts of data.
What are the main differences advantages and disadvantages of symmetrical and asymmetrical encryption?
The main advantage of symmetric encryption over asymmetric encryption is that it is fast and efficient for large amounts of data; the disadvantage is the need to keep the key secret - this can be especially challenging where encryption and decryption take place in different locations, requiring the key to be moved ...
What is one of the advantages of using both symmetric and asymmetric?
What is one of the advantages of using both symmetric and asymmetric cryptogrsphy in SSL/TLS? Supporting both types of algorithms allows less-powerful devices such as mobile phones to use symmetric encryption instead.
What are the advantages and disadvantages of symmetric and asymmetric cryptography?
Symmetric cryptography is faster to run (in terms of both encryption and decryption) because the keys used are much shorter than they are in asymmetric cryptography. Additionally, the fact that only one key gets used (versus two for asymmetric cryptography) also makes the entire process faster.
Why is asymmetric encryption more secure than symmetric encryption?
Asymmetric encryption is considered to be more secure than symmetric encryption as it uses two keys for the process. The public key used for encryption is available to everyone but the private key is not disclosed. This encryption method is used in everyday communication over the internet.
Why is symmetric cryptography faster than asymmetric cryptography?
Symmetric cryptography is faster to run (in terms of both encryption and decryption) because the keys used are much shorter than they are in asymmetric cryptography. Additionally, the fact that only one key gets used (versus two for asymmetric cryptography) also makes the entire process faster.
Why use symmetric and asymmetric cryptography?
Finally, many use cases combine both symmetric and asymmetric cryptography to improve speed and security at once. Most of these instances use symmetric cryptography to encrypt the bulk of the information and then use asymmetric cryptography to encrypt the symmetric encryption/decryption key ...
What is Symmetric Cryptography?
Symmetric cryptography uses mathematical permutations to encrypt a plain text message. It also uses the same mathematical permutation, known as a key, to decrypt messages.
How Do Symmetric and Asymmetric Cryptography Get Used Today?
Both symmetric and asymmetric cryptography get used often today, including in conjunction with one another. Here’s a look at some of the most common use cases for each approach as well as why that approach makes the most sense in each circumstance.
What is symmetric encryption?
By today’s standards, symmetric encryption is a relatively simple cryptographic algorithm, however it was once considered state of the art and used by the German army in World War II.
Can you decrypt a message without a key?
Even though it’s difficult to decrypt messages without the key, the fact that this approach uses the same key for both encryption and decryption creates risk. Specifically, people (or technology) who want to correspond via symmetric encryption must share the key to do so, and if the channel used to share the key gets compromised, ...
Is asymmetric cryptography more secure?
The above example offers a more secure way to encrypt messages compared to symmetric cryptography; however, asymmetric cryptography also powers additional, more advanced use cases.
Which is faster, symmetric or asymmetric encryption?
Symmetric encryption is much faster to execute because of its shorter key lengths. Asymmetric encryption has a tendency to bog down networks because of its longer key lengths and complex algorithms. These are the tradeoffs worth considering when deciding which type of encryption to employ.
What is symmetric encryption?
Symmetric encryption is a widely used data encryption technique whereby data is encrypted and decrypted using a single, secret cryptographic key.
What are some disadvantages of symmetric encryption?
By far the biggest disadvantage of symmetric encryption is its use of a single, secret cryptographic key to encrypt and decrypt information.
What is the most effective symmetric encryption technique?
AES encryption, which uses block ciphers of 128, 192, or 256 bits to encrypt and decrypt data, is one of the most well-known and effective symmetric encryption techniques in use today.
What is AES encryption?
AES encryption is the gold standard for both purposes. Transport Layer Security (TLS), as well as its predecessor, Secure Sockets Layer (SSL), uses symmetric encryption. Basically, when a client accesses a server, unique symmetric keys, called session keys, are generated.
How long does it take for AES to crack?
Security: symmetric encryption algorithms like AES take billions of years to crack using brute-force attacks.
Why is DES encryption withdrawn?
DES encryption is now considered by the National Institute of Standards and Technology (NIST) to be a legacy symmetric encryption algorithm because it has long been ineffective at safeguarding sensitive information from brute-force attacks. In fact, the NIST has withdrawn the standard entirely, and its more secure big brother, Triple DES encryption, will have the same fate. Although still in use today, Triple DES encryption is being withdrawn and disallowed by the NIST in 2023 because of mounting security concerns.
Which is better: symmetric or asymmetric encryption?
Asymmetric and symmetric encryption are each better used for different situations. Symmetric encryption, with its use of a single key, is better used for data-at-rest. Data stored in databases needs to be encrypted to ensure it is not compromised or stolen.
What happens if you use symmetric encryption?
If only symmetric encryption were used on data in emails, the attacker could take the key used for encryption and decryption and steal or compromise the data. With asymmetric encryption, the sender and recipient ensure only the recipient of the data can decrypt the data, because their public key was used to encrypt the data.
How does symmetric encryption work?
Symmetric encryption involves the use of one key for both encryption and decryption. The plaintext is read into an encryption algorithm along with a key. The key works with the algorithm to turn the plaintext into ciphertext, thus encrypting the original sensitive data. This works well for data that is being stored and needs to be decrypted at a later date. The use of just one key for both encryption and decryption reveals an issue, as the compromise of the key would lead to a compromise of any data the key has encrypted. This also does not work for data-in-motion, which is where asymmetric encryption comes in.
Why is encryption used in a private key?
This is because encryption occurs with the public key, while decryption occurs with the private key. The recipient of the sensitive data will provide the sender with their public key, which will be used to encrypt the data. This ensures that only the recipient can decrypt the data, with their own private key.
What is encryption in computer science?
Encryption takes data that can be clearly read, also known as plaintext, and runs it through an encryption algorithm. An encryption algorithm uses a key and mathematics to convert the plaintext into ciphertext, which is an undecipherable collection of letters and symbols.
What type of encryption is used in banking?
Data Storage: As with banking, data storage services and products tend to use symmetric encryption. This method is much swifter to encrypt and decrypt data needed in a timely manner.
What is the difference between a public key and a private key?
The use of both a public and private key means the identity of the signer of the data can easily be known. The signer uses their private key for encryption, while the recipient verifies their identity with their public key. As only the public key of the signer can decrypt data encrypted with the signer’s private key, ...
Why is symmetric encryption better than asymmetric encryption?
Symmetric encryption, because it’s faster and only uses one key, is great for large organizations and businesses that need to encrypt vast quantities of data . Asymmetric encryption uses two separate keys and more complex algorithms in the encryption and decryption process, which makes it slower for encrypting and decrypting large amounts of data .
Which is more secure, symmetric or asymmetric encryption?
Symmetric encryption is more secure than asymmetric encryption when you use smaller key sizes (such as a 256-bit key). That’s because in asymmetric encryption that uses smaller keys, having the public key actually makes the private key easier to calculate. (This is why we use larger keys in asymmetric encryption.)
What is encryption algorithm?
More specifically, it’s a set of mathematical instructions and processes that serve a specific purpose. Some algorithms are designed to work in either private or public channels. So, you can have asymmetric or symmetric encryption algorithms. In general, encryption algorithms are useful for encrypting data.
What is the difference between encryption and cryptography?
However, there’s an important difference: Cryptography is the overarching term for the field of cryptographic communications. Encryption, on the other hand, refers to the actual process of encrypting plaintext data into unreadable ciphertext.
How many bits are in asymmetric encryption?
Symmetric keys are also typically shorter in length than their asymmetric counterparts. Symmetric keys are frequently 128 bits, 192 bits, and 256 bits, whereas asymmetric keys are recommended to be 2048 bits or greater. For example, here’s an example of what a base64-encoded AES-256 symmetric encryption key looks like:
Why is asymmetric encryption important?
Asymmetric encryption, although slower, is better for those circumstances where your data is at risk of being intercepted by unintended third parties.
Why is asymmetric encryption considered public key encryption?
This is why asymmetric encryption is also known as public key encryption and public encryption. The public and private keys are mathematically related yet uniquely paired so that they match only one another. However, one key is publicly available while the other remains hidden and is never shared .
Which is more secure, symmetric or asymmetric encryption?
So, when we talk about symmetric vs asymmetric encryption, which is more secure? Asymmetric encryption is the more secure one, while symmetric encryption is faster. They’re both very effective in different ways and, depending on the task at hand, either or both may be deployed alone or together.
Why is asymmetric encryption more complicated than symmetric encryption?
However, this type of encryption offers a higher level of security as compared to symmetric encryption since the private key is not meant to be shared and is kept a secret.
What is the difference between symmetric and asymmetric keys?
1. Symmetric Key vs Asymmetric key. Only one key (symmetric key) is used, and the same key is used to encrypt and decrypt the message. Two different cryptographic keys (asymmetric keys), called the public and the private keys, are used for encryption and decryption. 2.
Why is symmetric encryption not scaled?
Because the entire mechanism is dependent on keeping the key a shared secret — meaning that it needs to be shared with the recipient in a secure way so that only they can use it to decrypt the message — it does not scale well. Symmetric encryption algorithms can use either block ciphers or stream ciphers.
How many bits are in AES?
With block ciphers, a number of bits (in chunks) is encrypted as a single unit. For instance, AES uses a block size of 128 bits with options for three different key lengths — 128, 192, or 256 bits. Symmetric encryption suffers from key exhaustion issues and, without proper maintenance of a key hierarchy or effective key rotation, ...
What is asymmetric encryption?
Asymmetric Encryption. Asymmetric encryption uses a pair of related keys — a public and a private key. The public key, which is accessible to everyone, is what’s used to encrypt a plaintext message before sending it. To decrypt and read this message, you need to hold the private key.
What happens after calculating symmetric key?
After calculating the symmetric key, both the server and the client send a change cipher spec message to each other. This indicates that the remaining communication involving any bulk data transfer will be done using symmetric keys (by applying encryption standards such as AES) over a secure encrypted channel.
What is the difference between asymmetric and private encryption?
In comparison, asymmetric encryption uses two separate keys which are related to each other mathematically. The keys are called Private keys and public keys.
Why is asymmetric encryption used?
For this reason, asymmetric encryption is often used to exchange the secret key, which can be used to establish symmetric encryption for faster data transfer and make encryption and decryption of the data faster.
What happens if you lose a symmetric key?
As discussed above, symmetric encryption uses the same key for encryption and decryption, so the sender would somehow send the key to the receiver to decrypt the encrypted data. The key involved has to be protected and transferred securely. If the key is lost, then the data cannot be decrypted, and if the key gets compromised, that will compromise the encryption.
Why is symmetric encryption important in banking?
Symmetric encryption provides fast encryption and decryption of a large amount of data, which includes the transaction. It can often contain Personal Identifiable Information (PII), which needs to be protected for being compliant with PCI DSS and preventing Identity Theft. They also need to ensure the identity of the user and the authenticity of the transactions fast. This is one of the reasons why the banking industry uses symmetric encryption.
How long does it take to read a symmetric key?
Read time: 9 minutes. Asymmetric and symmetric encryptions are the types of encryptions used in cryptography. There is only one key involved in symmetric encryption, which is used for both encryption and decryption. The key has to be shared among the parties involved who wish to encrypt and decrypt data. In comparison, asymmetric encryption uses ...
How are symmetric keys transferred?
Thus, symmetric keys are transferred among parties using asymmetric encryption, ensuring that the symmetric key remains encrypted. Two different keys are now involved in encrypting and decrypting the data.
What is the key used for HTTPS?
The key used for symmetric encryption is called session keys.
Symmetric Encryption
In the case of symmetric encryption, the same key is used for both encrypting and decrypting messages. Because the entire mechanism is dependent on keeping the key a shared secret — meaning that it needs to be shared with the recipient in a secure way so that only they can use it to decrypt the message — it does not scale well.
Asymmetric Encryption
Asymmetric encryption uses a pair of related keys — a public and a private key. The public key, which is accessible to everyone, is what’s used to encrypt a plaintext message before sending it. To decrypt and read this message, you need to hold the private key.
2 Common Use Cases for Symmetric Cryptography
Symmetric cryptography typically gets used when speed is the priority over increased security, keeping in mind that encrypting a message still offers a high level of security. Some of the most common use cases for symmetric cryptography include:
3 Common Use Cases for Asymmetric Cryptography
Asymmetric cryptography typically gets used when increased security is the priority over speed and when identity verification is required, as the latter is not something symmetric cryptography supports. Some of the most common use cases for asymmetric cryptography include:
Why is symmetric encryption better than asymmetric encryption?
Furthermore symmetric encryption is nice because it is easier to understand (less likely to mess it up) and the algorithms tend to be faster.
What are symmetric and asymmetric encryption?
Symmetric and asymmetric encryption are distinct operations which operate in distinct contexts, for distinct usages and distinct attack models.
What happens when two peers agree on a shared private key?
Once both peers agreed upon a shared private key then the rest of the communication would be using symmetric encryption. By doing so, the only expensive operation will taken place during the initial handshake and rest of the communication will be using symmetric encryption which is require less resource. Share.
What is the strength of encryption?
More precisely, the strength is the amount of computation that needs to be done to find the secret.
Is SSL symmetric or asymmetric?
Symmetric encryption is less expensive than asymmetric encryption. Expensive as in it requires less processing. To be exact, I am referring to the decryption process. And this is why SSL/TLS uses a combination of both symmetric and asymmetric encryption.
Is AES stronger than symmetric cryptography?
Each one can be either weak or strong, depending. There's no reason whatsoever why asymmetric cryptography is necessarily stronger than symmetric cryptography. For example: AES is more secure against cryptanalytic attacks than 512-bit RSA, even though RSA is asymmetric and AES is symmetric.
Is asymmetric encryption more secure?
Generally asymmetric encryption schemes are more secure because they require both a public and a private key. No. You can't say that. That's baloney. It's just not true. Strength is independent of symmetric vs asymmetric. Symmetric cryptography and asymmetric cryptography are two different kinds of cryptographic tool.

Asymmetric vs Symmetric Encryption
Uses For Asymmetric and Symmetric Encryption
- Asymmetric and symmetric encryption are each better used for different situations. Symmetric encryption, with its use of a single key, is better used for data-at-rest. Data stored in databases needs to be encrypted to ensure it is not compromised or stolen. This data does not require two keys, just the one provided by symmetric encryption, as it on...
Common Asymmetric and Symmetric Encryption Algorithms
- Symmetric Encryption Algorithms: 1. Advanced Encryption Standard (AES) 2. Blowfish 3. Twofish 4. Rivest Cipher (RC4) 5. Data Encryption Standard (DES) Asymmetric Encryption Algorithms: 1. Elliptic Curve Digital Signature Algorithm (ECDSA) 2. Rivest-Shamir-Adleman (RSA) 3. Diffie-Hellman 4. Pretty Good Privacy (PGP)