
NIST controls are generally used to enhance the cybersecurity framework, risk posture, information protection, and security standards of organizations. While NIST 800-53 is mandatory for federal agencies, commercial entities have a choice in leveraging the risk management framework in their security program.
How many controls does NIST 800 53 have?
The most recent edition (Rev. 4) of SP 800-53 includes 212 controls distributed across 18 control families designated by acronyms, such as “AC” for “Access Control,” “IR” for “Incident Response” and “CM” for “Configuration Management”. How many NIST security controls are there?
How many NIST control families?
What Are NIST Controls and How Many Are There? The National Institute of Standards and Technology Special Publication (NIST SP) 800-53 contains a wealth of security controls. NIST SP 800-53 R4 contains over 900 unique security controls that encompass 18 control families.
What is the NIST Cybersecurity Framework (CSF)?
The NIST Cybersecurity Framework (NIST CSF) consists of standards, guidelines, and best practices that help organizations improve their management of cybersecurity risk. The NIST CSF is designed to be flexible enough to integrate with the existing security processes within any organization, in any industry.
What is a NIST control family?
What is Media Protection about in NIST 800-171? The Media Protection family contains nine controls. These controls are primarily focused on the security of media storage including who can access the stored content, how transportation is controlledand the safe use of storage devices. Some of the key points addressed in this family are:

What are NIST 800-53 controls?
NIST Special Publication 800-53 is a catalog of security controls that helps safeguard information systems from a range of risks....NIST SP 800-53 helps to protect information systems from various threats including:Cybersecurity incidents.Privacy breaches.Malicious attack.Mistakes and human error.
What is NIST in simple terms?
NIST is the National Institute of Standards and Technology at the U.S. Department of Commerce. The NIST Cybersecurity Framework helps businesses of all sizes better understand, manage, and reduce their cybersecurity risk and protect their networks and data.
What are the 5 functions of NIST?
Here, we'll be diving into the Framework Core and the five core functions: Identify, Protect, Detect, Respond, and Recover. NIST defines the framework core on its official website as a set of cybersecurity activities, desired outcomes, and applicable informative references common across critical infrastructure sectors.
What are the 4 types of security controls?
One of the easiest and most straightforward models for classifying controls is by type: physical, technical, or administrative, and by function: preventative, detective, and corrective.
What companies use NIST?
Companies from around the world have embraced the use of the Framework, including JP Morgan Chase, Microsoft, Boeing, Intel, Bank of England, Nippon Telegraph and Telephone Corporation, and the Ontario Energy Board.
What are the 5 cybersecurity domains?
5 Domains of the NIST Security Framework. The five domains in the NIST framework are the pillars support the creation of a holistic and successful cybersecurity plan. They include identify, protect, detect, respond, and recover.
How do I use NIST framework?
6 Steps for Implementing the NIST Cybersecurity FrameworkSet Your Goals. ... Create a Detailed Profile. ... Determine Your Current Position. ... Analyze Any Gaps and Identify the Actions Needed. ... Implement Your Plan. ... Take Advantage of NIST Resources.
What are the different NIST frameworks?
There is the NIST Cybersecurity Framework, NIST 800-53 and NIST 171. While these three frameworks share most elements in common, there are some minor differences in structure and controls based on their specific use cases.
What is NIST security model?
The NIST cybersecurity framework is a powerful tool to organize and improve your cybersecurity program. It is a set of guidelines and best practices to help organizations build and improve their cybersecurity posture.
What are 3 primary types of security controls?
There are three primary areas or classifications of security controls. These include management security, operational security, and physical security controls.
What are the 3 levels of security?
The security features governing the security of an identity can be divided into three levels of security, i.e. Level 1 Security (L1S) (Overt), Level 2 Security (L2S) (Covert) and Level 3 Security (L3S) (Forensic).
What are the 3 types of security policies?
A: Three types of security policies in common use are program policies, issue-specific policies, and system-specific policies.
What is NIST role and why IT is so important in cyber security?
The NIST cybersecurity framework is a powerful tool to organize and improve your cybersecurity program. It is a set of guidelines and best practices to help organizations build and improve their cybersecurity posture.
Why is NIST important?
The NIST's goal is to help businesses and organizations secure information that is sensitive but not classified. The benefits of implementing best practices recommend by the NIST include: Protecting critical infrastructure and information from both insider threats and general human negligence.
Why is NIST important in cyber security?
The NIST Cybersecurity Framework is a powerful asset for cybersecurity practitioners. Given its flexibility and adaptability, it is a cost-effective way for organizations to approach cybersecurity and foster an enterprise-wide conversation around cyber risk and compliance.
What is cybersecurity NIST?
The process of protecting information by preventing, detecting, and responding to attacks.
What is NIST framework?
NIST Cybersecurity Framework released by NIST is a framework of security policies and guidance for organizations to secure their systems. This framework guides the organization in improving its abilities to handle cyber-attacks.
What is NIST SP 800-53?
NIST has recommended its own security controls in its special publication NIST SP 800-53 which is an open publication. When domain-specific standards are not available and if the organization decides not to procure a new standard, then NIST SP 800-53 will be highly useful. This special publication has more than 350 pages and it will take more efforts to understand. This section briefly presents how to use this publication. It is highly recommended to refer NIST SP 800-53 for the details.
What is common control?
Common controls are applicable for a family of systems controls that are inheritable by one or more organizational systems.
What is the first step in identifying security controls?
The essential step before identifying security controls for a system is to determine how critical and sensitive is the information to be processed. This process is called the security categorization. FIPS Publication 199 describes this process in detail.
What is the essential step before choosing a standard and selecting security controls?
Hence, the essential step before choosing a standard/framework is to identify whether the target system is information technology or operational technology or a hybrid one.
What is security control enhancement?
The security control enhancements section gives information about the security capabilities which can be applied to particular security control.
What is the control section?
The control section explains the security requirements need to be implemented by the organization or the system
What is a control?
A measure that is modifying risk. (Note: controls include any process, policy, device, practice, or other actions that modify risk. )
What is the control phase of a project?
the Control phase consists of managing investments while monitoring for results. Once the IT projects have been selected, senior executives periodically assess the progress of the projects against their projected cost, scheduled milestones, and expected mission benefits.
What is a control measure?
measure that is modifying risk. (Note: controls include any process, policy, device, practice, or other actions which modify risk. )
What is a control?
The controls are flexible and customizable and implemented as part of an organization-wide process to manage risk. The controls address diverse requirements derived from mission and business needs, laws, executive orders, directives, regulations, policies, standards, and guidelines.
What is security and privacy control?
This publication provides a catalog of security and privacy controls for information systems and organizations to protect organizational operations and assets, individuals, other organizations, and the Nation from a diverse set of threats and risks, including hostile attacks, human errors, natural disasters, structural failures, foreign intelligence entities, and privacy risks. The controls are flexible and customizable and implemented as part of an organization-wide process to manage risk. The controls address diverse requirements derived from mission and business needs, laws, executive orders, directives, regulations, policies, standards, and guidelines. Finally, the consolidated control catalog addresses security and privacy from a functionality perspective (i.e., the strength of functions and mechanisms provided by the controls) and from an assurance perspective (i.e., the measure of confidence in the security or privacy capability provided by the controls). Addressing functionality and assurance helps to ensure that information technology products and the systems that rely on those products are sufficiently trustworthy.
What is NIST 800-53?
Recently, NIST published a significant update to its flagship security and privacy controls catalog , Special Publication 800-53, Revision 5. This update created a set of next generation controls to help protect organizations, assets, and the privacy of individuals—and equally important—manage cybersecurity and privacy risks.
How does organization-generated control selection work?
Rather, the organization uses its own process to select controls. This may be necessary when the system is highly specialized (e.g., a weapons system or a medical device), has a limited purpose or scope (e.g., a smart meter), requires protection from a specific set of threats, or the nature of the data processing poses specific types of privacy risks. In these situations, it may be more efficient and cost-effective for an organization to select the controls for the system instead of starting with a pre-defined set of controls from a control baseline and adding or eliminating controls through the tailoring process. As in the baseline control selection approach, the selection of specific controls in the organization-generated selection approach can be guided and informed by the system security categorization, risk assessment, and requirements derived from stakeholder protection needs, laws, executive orders, regulations, policies, directives, and standards.
What is baseline control?
The baseline control selection approach uses control baselines, which are pre-defined sets of controls assembled to address the protection needs of a group, organization, or community of interest. Security and privacy control baselines serve as a starting point for the protection of information, information systems, and individuals’ privacy. Federal security and privacy control baselines are defined in draft NIST Special Publication 800-53B. The three security control baselines contain sets of security controls and control enhancements that offer protection for information and information systems that have been categorized as low-impact, moderate-impact, or high-impact—that is, the potential adverse consequences on the organization’s missions or business operations or a loss of assets if there is a breach or compromise to the system. The system security categorization, risk assessment, and security requirements derived from stakeholder protection needs, laws, executive orders, regulations, policies, directives, and standards can help guide and inform the selection of security control baselines from draft Special Publication 800-53B.
What is privacy control baseline?
The privacy control baseline is based on a mapping of the controls and control enhancements in Special Publication 800-53, Revision 5 to the privacy program responsibilities under the Office of Management and Budget (OMB) Circular A-130. After the pre-defined security and privacy control baselines are selected, organizations can tailor the baselines in accordance with the guidance provided in draft Special Publication 800-53B. A privacy risk assessment and privacy requirements derived from stakeholder protection needs, laws, executive orders, regulations, policies, directives, and standards can also help guide and inform the tailoring of the privacy controls. The baseline control selection approach can provide consistency across broad and diverse communities of interest (e.g. federal agencies, healthcare sector, financial services sector, cloud service providers).
Do organizations need to choose a single control selection approach?
Organizations do not need to choose a single control selection approach, but instead, can choose the appropriate approach as circumstances dictate. This flexibility is needed to effectively manage security and privacy risks and to ensure that organizations are doing their security and privacy due diligence.
What is security control?
The security controls (i.e., safeguards or countermeasures) for an information system that focus on the management of risk and the management of information system security.
What is management control?
management controls are actions taken to manage thedevelopment, maintenance, and use of the system, including system-specific policies, procedures, and rules of behavior, individual roles and responsibilities, individual accountability and personnel security decisions.
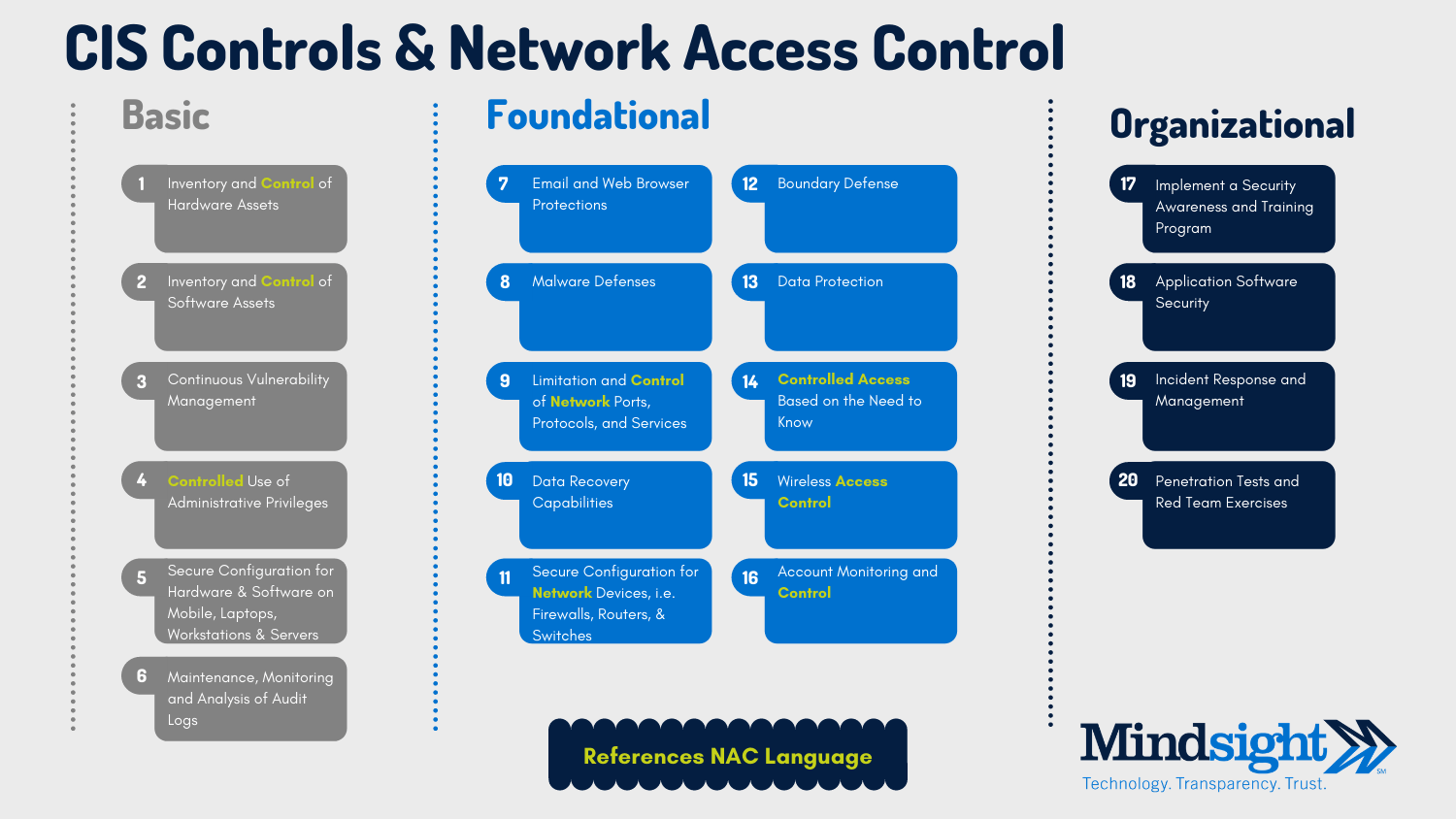
Control Family 2 - Awareness and Training
Control Family 4 - Assessment, Authorization, and Monitoring
- The Assessment, Authorization and Monitoring family covers the monitoring, maintenance and improvements of security and privacy controls.
Control Family 5 - Configuration Management
- The Configuration Management family contains controls to manage, asses and improve configuration of software and systems.
Control Family 7 - Identification and Authentication
- The Identification and Authentication family contains controls to protect the identity of users and devices.
Control Family 9 - Maintenance
- The Maintenance family of controls handles all aspects of system maintenance, such as software updates, logging, and inspection tools.
Control Family 10 - Media Protection
- The controls in the Media Protection family covers how media and files are used, stored, and safely destroyed.
Control Family 11 - Physical and Environmental Protection
- The controls in the Physical and Environmental Protection family covers how to protect physical locations.
Control Family 12 - Planning
- The Planning family of controls is about the creation and approach to cybersecurity and privacy related plans.
Control Family 13 - Program Management
- The Program Management family of controls contains controls to manage cybersecurity and privacy programs.
Control Family 14 - Personnel Security
- The different policies and procedures for managing employees are covered by the Personnel Security family of controls.