List of Ports
| Port | Protocol | Application protocol | System service name |
| n/a | GRE | GRE (IP protocol 47) | Routing and Remote Access |
| n/a | ESP | IPsec ESP (IP protocol 50) | Routing and Remote Access |
| n/a | AH | IPsec AH (IP protocol 51) | Routing and Remote Access |
| 7 | TCP | Echo | Simple TCP/IP Services |
What ports are the most common?
Port 80 is associated with HTTP, Hypertext Transfer Protocol. It comes under the category of a TCP protocol. It is one of the most famous and widely used ports in the world. The main purpose of port 80 is to allow the browser to connect to the web pages on the internet. Port 80 basically expects or waits for the web client to ask for a connection.
What are ECS protocols and ports?
The ECS service use the following protocols and port numbers:
- The topology fetching: TCP port 264 (source port)
- IKE exchange: UDP port 500 (both source and destination ports)
- UDP encapsulated ESP datagram: UDP port 2746 (both source and destionation ports)
What are the most common HTTP ports?
Top 25 Most Popular Ports
- Port 80 TCP – (HTTP)
- Port 443 TCP – (HTTPS)
- Port 67-68 UDP – (DHCP)
- Port 20-21 – (FTP)
- Port 23 – (Telnet)
- Port 22 – (SSH)
- Port 53 TCP/UDP – (DNS)
- Port 8080
- Port 123 UDP – (NTP)
- Port 25 TCP – (SMTP)
What are the most common networking protocols?
These are:
- Transmission Control Protocol (TCP)
- Internet Protocol (IP)
- User Datagram Protocol (UDP)
- Post office Protocol (POP)
- Simple mail transport Protocol (SMTP)
- File Transfer Protocol (FTP)
- Hyper Text Transfer Protocol (HTTP)
- Hyper Text Transfer Protocol Secure (HTTPS)
- Telnet
- Gopher
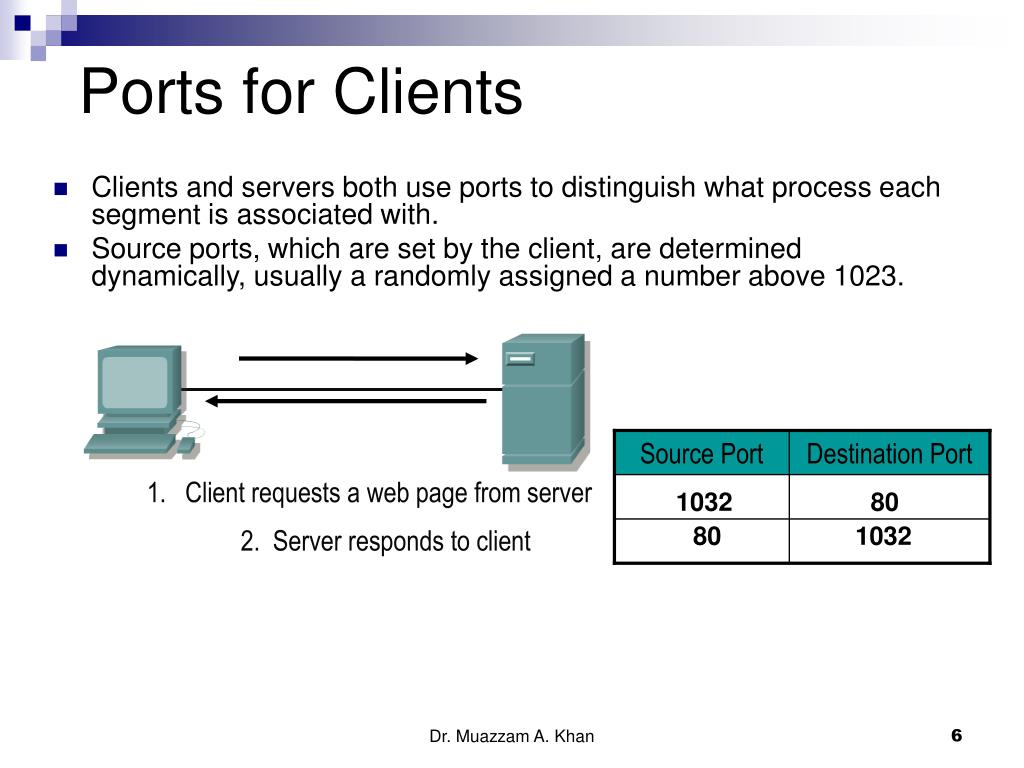
What are ports and protocols?
A protocol is a specification for how two devices should exchange data in a way that they can both understand. A port is kind of a numbered 'tag' that helps a computer decide who should receive an incoming piece of data.
What are protocols and services?
A protocol is a set of rules for communication within a layer. A service is what the layer provides to the layer above it through an interface. Protocols at one layer are unaware of issues at another layer.
What are the 3 types of port?
There are different types of ports available: Serial port. Parallel port. USB port.
What are some common ports and their services?
14 common network ports you should knowPort NumberUsage80Hypertext Transfer Protocol (HTTP) used in World Wide Web110Post Office Protocol (POP3) used by e-mail clients to retrieve e-mail from a server119Network News Transfer Protocol (NNTP)123Network Time Protocol (NTP)10 more rows
What are the 7 protocols?
Common Management Information Protocol (CMIP) On TCP/IP stack:Hypertext Transfer Protocol (HTTP)File Transfer Protocol (FTP)Simple Mail Transfer Protocol (SMTP)Simple Network Management Protocol (SNMP)
What are the examples of protocol?
Among the most important sets of Internet protocols are TCP/IP (Transmission Control Protocol/Internet Protocol), HTTPS (Secure HyperText Transmission Protocol), SMTP (Simple Mail Transfer Protocol), and DNS (Domain Name System).
What port is DHCP?
UDP port 67DHCP is a network protocol to used to configure IP networks. A DHCP server listens to UDP port 67 and dynamically assigns IP addresses and other network parameters to DHCP clients. These clients will listen for responses on UDP port 68.
Which port is used for HTTP?
80By default, these two protocols are on their standard port number of 80 for HTTP and 443 for HTTPS.
What are the two types of ports?
Based on the type of protocol used for communication, computer ports can be of two types: Serial Ports and Parallel Ports.
Why are port protocols important?
Each data packet comes with a port number associated with it. This enables the protocols to decide that what are the requirements of the data packets and to which port are they supposed to be directed. In fact, the existence of ports is crucial to make sure that data packets reach their desired destinations accurately.
Is TCP a protocol?
What is TCP? TCP stands for Transmission Control Protocol a communications standard that enables application programs and computing devices to exchange messages over a network. It is designed to send packets across the internet and ensure the successful delivery of data and messages over networks.
What are the most commonly used ports?
What are the most commonly used ports?HTTP – Port 80.HTTPS – 443.FTP – 21.FTPS / SSH – 22.POP3 – 110.POP3 SSL – 995.IMAP – 143.IMAP SSL – 993.More items...•
What is the relationship between services and protocols?
Services describe the resulting effects of the operation of a protocol without requiring knowledge of the detailed specifications of the protocol itself. A protocol specifies a horizontal dialogue between two computing systems across a network, while a service describes a vertical relationship within a system.
What are the different types of network services?
Network Services include IP addressing, Domain Name System (DNS), primary domain email service, Internet access, web content filtering, security products such as firewalls, VPN termination and intrusion prevention systems (IPS), and the necessary tools and staff to support these services.
What makes a good protocol officer?
Communication: Good communication skills are important for protocol officers because they need to establish expectations for good etiquette at important events and ceremonies. They also coordinate events and need to communicate with multiple stakeholders to ensure events operate smoothly.
What are service primitives in computer network?
A service is a set of primitives or we call it as operations where a user can invoke to access the service. The selective primitives tell the service to perform an action taken by peer nodes. The initiating node wants to establish a connection send CONNECT.
What is a port and protocol?
What are ports and protocols ? As per its word definition, a protocol is a set of rules. In computer networking, a protocol defines a standard way for computers to exchange information. Most common protocols used in computer networks and the internet are TCP (Transmission Control Protocol), UDP (User Datagram Protocol), and IP (Internet Protocol).
What is a port in computer networking?
A port in computer networking is a logical access channel for communication between two devices. Bi-directional communications and more complex connections may use multiple ports (channels) simultaneously. Data on the Internet is organized into standard TCP or UDP packets.
What is the port number of a packet?
The port number (and the destination IP address) is included as part of the header each packet is given. Ports range from 1 to 65535 for the TCP and UDP protocols. Port numbers are generally divided into three ranges: 1.
What is the function and port number used by a number of common services?
One of the many fundamental things to know as a network engineer is the function and port number used by a number of common services as well as many that are typically implemented during the course of a network engineer’s career.
What is the protocol used to retrieve mail from a server?
POP was designed to be very simple by allowing a client to retrieve the complete contents of a server mailbox and then deleting the contents from the server. Network Time Protocol (NTP) (RFC 59 05)
Why is TFTP used instead of TCP?
Because TFTP uses UDP instead of TCP it has no way of ensuring the file has been properly transferred, the end device must be able to check the file to ensure proper transfer . TFTP is typically used by devices to upgrade software and firmware; this includes Cisco and other network vendors’ equipment.
What is telnet in SSH?
23. Telnet is the primary method used to manage network devices at the command level. Unlike SSH which provides a secure connection, Telnet does not, it simply provides a basic unsecured connection. Many lower level network devices support Telnet and not SSH as it required some additional processing.
Why is NTP important?
The use of NTP is vital on networking systems as it provides an ability to easily interrelate troubles from one device to another as the clocks are precisely accurate.
What is SNMP 161?
161/162. SNMP is used by network administrators as a method of network management. SNMP has a number of different abilities including the ability to monitor, configure and control network devices. SNMP traps can also be configured on network devices to notify a central server when specific actions are occurring.
What is FTP protocol?
File Transfer Protocol (FTP) (RFC 959) TCP. 20/21. FTP is one of the most commonly used file transfer protocols on the Internet and within private networks. An FTP server can easily be set up with little networking knowledge and provides the ability to easily relocate files from one system to another.
What is a network protocol?
Simply, a protocol is a set of rules. A network protocol is a set of rules followed by the network. Network protocols are formal standards and policies made up of rules, procedures and formats that defines communication between two or more devices over a network. Network protocols conducts the action, policies, and affairs of the end-to-end process of timely, secured and managed data or network communication. They define rules and conventions for communication. They incorporate all the processes requirement and constraints of initiating and accomplishing communication between computers, routers, servers and other network enabled devices. Network protocols must be confirmed and installed by the sender and receiver to ensure networkdata communication. It also applies software and hardware nodes that communicate on a network. There are several types of network protocols.
What is the purpose of the Internet protocol?
The Internet Protocol is the principal protocol in the Internet protocol suite for relaying data across networks. Its routing function essentially establishes the internet. Historically it was the connectionless datagram service in the original Transmission Control Program; the other being the connection oriented protocol (TCP). Therefore, the Internet protocol suite is referred as TCP/IP.
What is the Internet protocol suite?
Internet protocol suite is the set of communication protocols that implement the protocol stack on which the internet runs. The Internet protocol suite is sometimes called the TCP/IP protocol suite, after TCPIP, which refers to the important protocols in it, the Transmission Control Protocol (TCP) and the Internet Protocol (IP).
What is the SSH port?
Secured Shell (SSH) SSH is the primary method used to manage the network devices securely at the command level . It usually used as the alternative of the Telnet which does not support secure connections. The default port of SSH is 22.
What is TCP delivery?
TCP provides reliable delivery of a stream of octets over an IP network. Ordering and error-checking are main characteristics of the TCP. All major Internet applications such as World Wide Web, email and file transfer rely on TCP.
What is telnet port?
Telnet is the primary method used to manage network devices at the command level. Unlike SSH, Telnet does not provide a secure connection, but it provides a basic unsecured connection. The default port of Telnet is 23.
What is a protocol stack?
A protocol stack is the complete set of protocol layers that work together to provide networking capabilities.
How to ensure that only the appropriate traffic is permitted to access the application?
Use application firewalls and place them in front of any critical servers. This helps ensure that only the appropriate traffic is permitted to access the application.
Why are routes optimized?
Routes are optimized to allow travelers to reach their destinations as quickly as possible. Traffic laws specify who is allowed in which lanes and at what speeds—carpool lanes, slow lanes, truck lanes, and so on. There are special rules in place to control the passage of hazardous cargo and oversized vehicles.
What is a whitelist on a server?
Leverage host-based firewalls on your servers, with whitelists configured to ONLY allow communications between the aspects of the systems (e.g., database connections or administrative access from specific IP spaces). Workstations can also use this technology to the same end. All other non-essential communications should be blacklisted, as they are opening the system up to additional risk.
What is toll booth signage?
Toll booth signage directs traffic based on payment and vehicle type. And all of this has been pre-defined by a group of civil engineers long before the first cubic yard of concrete is poured.
Should you separate critical services?
Separate critical services on individual host machines. We mentioned SNMP and FTP earlier, but it goes deeper than that. While you may be leveraging your domain controller for DHCP, you certainly should not be including any additional critical services on these boxes. If at all possible, physical segregation is ideal, but in complex modern computing and operational environments, this may not be feasible. Regardless of means of segmentation, enhance the security of the hosts by locking them down to only the required services. In the case of critical services such as DNS, DHCP, and database servers, for example, this is simply a means of ensuring that the attack landscape is kept at a minimum and that attackers would not gain access to multiple lines of advancement to the crown jewels.
What is the purpose of PPSM?
The PPSM mission is to create fundamental, definitive, but agile PPSM standards (defined in reference (a)) to maintain strong, secure, uninterrupted access to government resources and critical applications.
How to contact PPSM?
For questions regarding PPSM, contact the PPSM Secretariat by phone at (301) 225-2904, DSN 312-375-2904 or send messages to [email protected] (NIPRNET) or [email protected] (SIPRNET).
How many network protocols have port nos?
40 Network Protocols with Port NOs. Transport Protocols and Meanings
What is network protocol?
Network protocols are the languages and rules used during communication in a computer network. There are two major transport protocols namely;
What is the difference between TCP and UDP?
Therefore, TCP is used for transferring most types of data such as webpages and files over the Internet. UDP which stands for “User Datagram Protocol” is part of the TCP/IP suite of protocols used for data transferring. UDP is a known as a “connectionless-oriented” protocol, meaning it doesn’t acknowledge that the packets being sent have been ...
What is the protocol used to secure data communication?
TCP. It is a protocol that carries data guarantees that data will be delivered properly. 2. Secure Shell (SSH) 22. TCP and UDP. It is a cryptographic network protocol used to secure data communication. 3. Telnet.
Which protocol is used for transferring most types of data such as webpages and files over the local network or Internet?
Therefore TCP is used for transferring most types of data such as webpages and files over the local network or Internet. UDP is ideal for media streaming which does not require all packets to be delivered. Port Numbers: They are the unique identifiers given to all protocol numbers so they can be accessed easily.
What is the protocol used in NetBIOS?
NetBIOS itself is not a protocol but is typically used in combination with IP with the NetBIOS over TCP/IP protocol. 13. Simple Network Management Protocol (SNMP) 161 and 162. TCP and UDP.
What is nntp in email?
It is a protocol used by e-mail client to retrieve e-mail from the servers. 10. Network News Transport Protocol (NNTP) nntp is an application protocol used for transporting USENET news articles between news servers and the end user client.
