
Authentication methods
- Protected EAP (PEAP) This section contains configuration information for the two default inner EAP methods that are provided with PEAP. EAP-Transport Layer Security (TLS) ...
- EAP-Tunneled Transport Layer Security (TTLS)
- EAP-Subscriber Identity Module (SIM), EAP-Authentication and Key Agreement (AKA), and EAP-AKA Prime (AKA') ...
What can I use my EAP for?
The most common reasons we see for EAP counseling are:
- Partner/marital concerns
- Relationship issues (family, friends, colleagues)
- Stress—feeling stress, not knowing what to do with stress
- Communication issues
- Anxiety, depress, mental health concerns
- Substance abuse
How can the EAP help you?
How Can Your Employee Assistance Program (EAP) Help You?
- Identify Mental Health Conditions. It had almost been a month that Reena was not her chirpy self. ...
- Resolve Every Day Life Challenges. An unresolved conflict with spouse, challenges faced as a working mother, loss of interest at work, irritability without any reason or feeling under-confident at meetings!
- Learn New Skills. ...
What is the advantage of using EAP?
These are some of the common problems an EAP can help employees with:
- Stress management. Work and finances are some of the top causes of stress, according to WebMD. ...
- Domestic violence. ...
- Grief counseling. ...
- Alcoholism. ...
- Crisis management. ...
- Psychological (mental health) disorders. ...
- Substance abuse. ...
- Health and caregiving. ...
- Family services. ...
- Counseling referrals. ...
Can EAP use be required by an employer?
The Employee Assistance Program should be voluntary for employees to use, not required by the employer. The EAP is designed to be a voluntary program that provides short-term, no-cost services for issues related to finances, work, chemical dependency, stress, relationships and other life concerns.
What are EAP methods?
The Extensible Authentication Protocol (EAP) is an architectural framework that provides extensibility for authentication methods for commonly used protected network access technologies, such as IEEE 802.1X-based wireless access, IEEE 802.1X-based wired access, and Point-to-Point Protocol (PPP) connections such as ...
What is the most common EAP method?
PEAP: Protected EAP. Originally proposed by Microsoft, this EAP Tunnel type has quickly become the most popular and widely deployed EAP method in the world. PEAP will form a potentially encrypted TLS tunnel between the client and server, using the x.
What EAP method should I use for WIFI?
PEAPFor "EAP method" select "PEAP". For "Phase 2 authentication" select "MSCHAPV2". If you are using the Nougat (7) OS on your Android, set "CA Certificate" to "Use system certificates" and "Domain" to "ed.ac.uk".
What is EAP-TLS and PEAP?
The Protected Extensible Authentication Protocol, also known as Protected EAP or simply PEAP, is a protocol that encapsulates the Extensible Authentication Protocol (EAP) within an encrypted and authenticated Transport Layer Security (TLS) tunnel.
Which is more secure EAP-TLS or PEAP?
PEAP-MSCHAPv2 leaves your organization vulnerable to cyber attacks. EAP-TLS is a superior authentication protocol that uses digital certificates as opposed to credentials.
What is the most secure EAP?
EAP-TLS. This is the most secure method as it requires certificates from client and server end. The process involves mutual authentication where client validates server certificate and server validates client certificate. Hence, it is difficult to implement.
What is PEAP method for WiFi?
PEAP (Protected Extensible Authentication Protocol) provides a method to transport securely authentication data, including legacy password-based protocols, via 802.11 Wi-Fi networks. PEAP accomplishes this by using tunneling between PEAP clients and an authentication server.
Is PEAP secure?
PEAP (Protected Extensible Authentication Protocol) is a version of EAP, the authentication protocol used in wireless networks and Point-to-Point connections. PEAP is designed to provide more secure authentication for 802.11 WLANs (wireless local area networks) that support 802.1X port access control.
Does PEAP require certificate?
PEAP-MSCHAPV2 and PEAP-EAP-GTC—Requires two certificates: a server certificate and private key on the RADIUS server, and a trusted root certificate on the client. The client's trusted root certificate must be for the CA that signed the RADIUS server's certificate.
Does EAP PEAP use certificates?
PEAP—Protected EAP (PEAP) is an 802.1X authentication method that uses server-side public key certificates to authenticate clients with server. The PEAP authentication creates an encrypted SSL / TLS tunnel between the client and the authentication server.
Why EAP-TLS is best?
Benefits of EAP-TLS There are two primary advantages of EAP-TLS: EAP-TLS is the strongest authentication security. The use of X. 509 digital certificates makes the protocol the undisputed champion, especially when those certificates are encrypted using modern techniques like elliptical curve cryptography (ECC).
What is 802.1 EAP security?
What is 802.1X EAP Security? The standard authentication protocol used on encrypted networks is Extensible Authentication Protocol (EAP), which provides a secure method to send identifying information over-the-air for network authentication.
What is PWD EAP method?
EAP-PWD (Password) is an EAP authentication method that uses a shared password for authentication. EAP-PWD addresses the problem of password-based authenticated key exchange using a possibly weak password for authentication to derive an authenticated and cryptographically strong shared secret.
What is EAP method leap?
LEAP (Lightweight Extensible Authentication Protocol), is an EAP authentication type used primarily in Cisco Aironet* WLANs. It encrypts data transmissions using dynamically generated WEP keys, and supports mutual authentication.
What is EAP method identity?
EAP identity: The identity of the Extensible Authentication Protocol (EAP) peer as specified in [RFC3748]. EAP method: An authentication mechanism that integrates with the Extensible Authentication Protocol (EAP); for example, EAP-TLS, Protected EAP v0 (PEAPv0), EAP-MSCHAPv2, and so on.
How does EAP MD5 work?
EAP-MD5 is a password-based and one-way authentication protocol, often used in wireless X802. 1 networks and PPP connections [3]. This protocol consists of three components, the applicant, the identity authentication (WAP) and the server (RADIUS), in which only the identity of the applicant is authenticated (Figure 1).
What is EAP authentication?
Extensible Authentication Protocol (EAP) is used to pass the authentication information between the supplicant (the Wi-Fi workstation) and the authentication server (Microsoft IAS or other). The EAP type actually handles and defines the authentication. The access point acting as authenticator is only a proxy to allow the supplicant and ...
What is EAP TLS?
EAP-TLS (Transport Layer Security) provides for certificate-based and mutual authentication of the client and the network. It relies on client-side and server-side certificates to perform authentication and can be used to dynamically generate user-based and session-based WEP keys to secure subsequent communications between the WLAN client and the access point. One drawback of EAP-TLS is that certificates must be managed on both the client and server side. For a large WLAN installation, this could be a very cumbersome task.
What is VPN in LAN?
Another option is VPN. Instead of relying on Wi-Fi LAN for authentication and privacy (encryption), many enterprises implement a VPN. This is done by placing the access points outside the corporate firewall and having the user tunnel in via a VPN Gateway - just as if they were a remote user.
What is 802.1x port?
802.1X is a port access protocol for protecting networks via authentication. As a result, this type of authentication method is extremely useful in the Wi-Fi environment due to the nature of the medium. If a Wi-Fi user is authenticated via 802.1X for network access, a virtual port is opened on the access point allowing for communication.
What is a supplicant?
Supplicant A software client running on the Wi-Fi workstation.
Does EAP Fast require a certificate?
EAP-FAST is now available for enterprises that can't enforce a strong password policy and don't want to deploy certificates for authentication. The more recent PEAP works similar to EAP-TTLS in that it doesn't require a certificate on the client side.
Does Funk Software use TLS?
Making this an often preferred option. Funk Software* is the primary promoter of TTLS, and there's a charge for supplicant and authentication server software .
How does TLS work?
TLS provides mutual authentication through certificate exchange. The user is required to submit a digital certificate to the authentication server for validation, but the authentication server must also supply a certificate. By validating the server certificate against a list of trusted certificate authorities, the client can be assured that it is connecting to an network authorized by the certificate authority.
What is EAP TLS?
EAP-TLS was the first authentication method to meet all three goals for wireless networks. Certificates provide strong authentication of both the users to the network, and the network to users. Mutual authentication provides a strong guard against so-called "rogue" access points by enabling clients to determine that an AP has been configured by the right department, rather than an attacker who is intent only on stealing passwords. TLS also establishes a master secret that can be used to derive keys for link layer security protocols.
Why is PKI required?
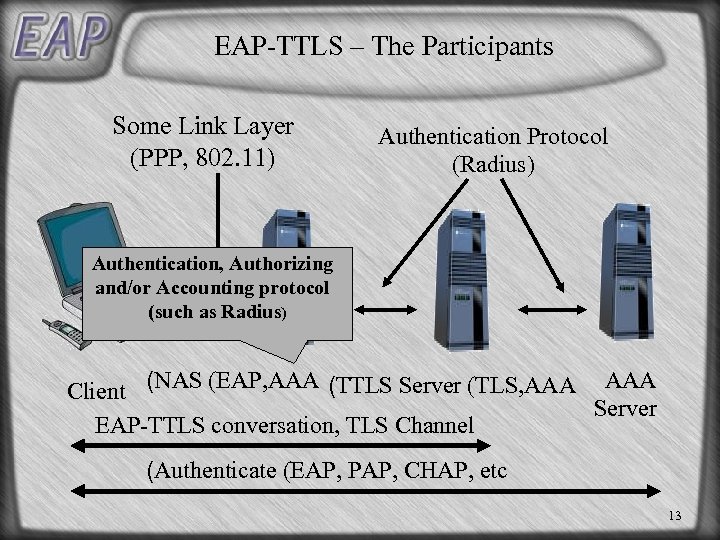
Practically speaking, the requirement for PKI was a major bar to the use of strong authentication on wireless LANs. PKIs are a significant undertaking in both technology and process. Most organizations found it desirable to re-use existing authentication systems, such as a Windows domain or Active Directory, LDAP directory, or Kerberos realm. Re-using existing accounts is much easier than creating a parallel authentication system. The two EAP methods intended to enable the use of so-called "legacy authentication methods" are Tunneled TLS (TTLS) and Protected EAP (PEAP).
What is TLS in wireless?
Transport Layer Security (TLS) was designed for use on links subject to eavesdropping. TLS is the standards-based successor to the Secure Socket Layer (SSL), the protocol that enabled secure web transactions. In many respects, the use case for wireless LANs is similar to the Internet. Data must be transmitted over a totally untrusted network with all manner of attackers. Establishing a trusted communication channel over an untrusted network is the purpose of TLS.
What is a LEAP network?
The first widely-used method for authenticating wireless networks was Cisco's proprietary Lightweight EAP (LEAP).
- ] LEAP was a huge step forward from manual-key WEP, though it leaves a great deal to be desired. In essence, LEAP is two MS-CHAP version 1 exchanges. One authenticates the network to the user, and the second authenticates the user to the network. Dynamic keys are derived from the MS-CHAP exchanges.
What is WEP with manually defined keys?
WEP with manually-defined keys provides very little protection of frames on the radio link. Stronger security protocols need to use dynamic keys that are derived from an entropy pool. One of the side effects of providing strong cryptographic protection is that such protocols also generate a shared stream of cryptographically secure bits that can be used to distribute keys to link-layer security protocols.
Why is EAP-MD5 used?
EAP-MD5 is often selected as a target for EAP type filtering because it is much weaker than TLS-based methods. EAP method filtering is not necessary, and has the potential to get in the way of good security practice. Many filters only allow TLS-based tunnel methods (types 13, 21, and 25).
What is the Extensible Authentication Protocol?
The Extensible Authentication Protocol (EAP) is a protocol for wireless networks that expands the authentication methods used by the Point-to-Point Protocol ( PPP ), a protocol often used when connecting a computer to the internet.
How does EAP work?
EAP uses the 802.1x standard as its authentication mechanism over a local area network or a wireless LAN (WLAN). There are three primary components of 802.1X authentication:
Tunneled EAP methods
There are upwards of 40 EAP methods, including several commonly used ones that are often called inner methods or tunneled EAP methods. These include the following.
The takeaway
Security is a critical aspect of public network architecture. This is more important than ever given how fast telecommunications technology is changing and the development of 5G. Security features in 5G include native support of EAP.
What is EAP TLS?
EAP-TLS: An EAP type that uses TLS (Transport Layer Security) to provide the secure identity transaction. This is very similar to SSL and the way encryption is formed between your web browser and a secure website. EAP-TLS has the benefit of being an open IETF standard, and is considered "universally supported.".
What is EAP authentication?
EAP is an authentication framework that defines the transport and usage of identity credentials. EAP encapsulates the usernames, passwords, certificates, tokens, OTPs, etc. that a client is sending for purposes of authentication. In fact, did you know that 802.1X is really “just” defining EAP over LAN?
What is EAP-MSCHAPv2?
EAP-MSCHAPv2: Using this inner method, the client’s credentials are sent to the server encrypted within an MSCHAPv2 session. This is the most common inner method, as it allows for simple transmission of username and password, or even computer-name and computer-passwords to the RADIUS server, which in-turn will authenticate them to Active Directory.
Is EAP TLS secure?
It is considered among the most secure EAP Types, since password capture is not an option; the endpoint must still have the private-key. Note: EAP-TLS is quickly becoming the EAP type of choice when supporting BYOD in the Enterprise.
Does EAP MD5 have mutual authentication?
The HASH is sent to the server where it is compared to a local hash to see if the credentials were accurate. However, EAP-MD5 does not have a mechanism for mutual authentication. That means the server is validating the client, but the client does not authenticate the Server (i.e.: does not check to see if it should trust the server).
Is EAP TLS open?
EAP-TLS has the benefit of being an open IETF standard, and is considered "universally supported .". EAP-TLS uses X.509 certificates and provides the ability to support mutual authentication, where the client must trust the server’s certificate, and vice-versa.
Who is Aaron Woland?
Aaron Woland, CCIE No. 20113, is a Principal Engineer at Cisco Systems. His primary job responsibilities include Secure Access and Identity deployments with ISE, solution enhancements, standards development, and futures.
What is EAP authentication?
EAP, or eap, or extensible authentication protocol is a very common set of frameworks that can be used to authenticate people onto things like wireless networks. For instance, WPA2 and WPA use five different EAP types as authentication mechanisms.
What does "leap" mean in wireless?
And it’s called LEAP, that stands for light weight extensible authentication protocol.
