ICMP message types
| ICMP Message Type number | ICMP Message Type | Description |
| 0 and 8 | Echo Request/Echo Reply | ICMP Echo/Echo Reply type of messages ar ... |
| 3 | Destination Unreachable | ICMP Destination unreachable type of mes ... |
| 4 | Source Quench | ICMP Source Quench type of messages allo ... |
| 5 | Redirect | ICMP redirect type of messages allows a ... |
- Type 0 — Echo Reply.
- Type 1 — Unassigned.
- Type 2 — Unassigned.
- Type 3 — Destination Unreachable.
- Type 4 — Source Quench (Deprecated)
- Type 5 — Redirect.
- Type 6 — Alternate Host Address (Deprecated)
- Type 7 — Unassigned.
What is the most common type of ICMP message?
The most popular ICMP message is the echo request and reply.
What is ICMP explain ICMP message types with their usage?
ICMP creates and sends messages to the source IP address indicating that a gateway to the internet, such as a router, service or host, cannot be reached for packet delivery. Any IP network device has the capability to send, receive or process ICMP messages.
How many ICMP versions are there?
With the different IP versions there are two different types of ICMP versions, ICMPv4 for IPv4 and ICMPv6 for IPv6. ICMP is used by computers and all types of network devices, including network routers, which help identify problems and communicate the status of devices on the network.
How many ICMP error types or message types are possible?
In the original ICMP version 4, five different error messages are defined, which are all described in the original ICMP standard, RFC 792.
What does ICMP type mean?
ICMP (Internet Control Message Protocol) is a network protocol used for diagnostics and network management. A good example is the “ping” utility which uses an ICMP request and ICMP reply message.
What is ICMP message function?
ICMP messages are typically used for diagnostic or control purposes or generated in response to errors in IP operations (as specified in RFC 1122). ICMP errors are directed to the source IP address of the originating packet.
What are two ICMP?
Explanation: The ICMP messages common to both ICMPv4 and ICMPv6 include: host confirmation, destination (net, host, protocol, port) or service unreachable, time exceeded, and route redirection. Router solicitation, neighbor solicitation, and router advertisement are new protocols implemented in ICMPv6.
What ICMP code is ping?
Ping uses two ICMP codes: 8 (echo request) and 0 (echo reply). When you issue the Ping command at the prompt, the Ping program sends out an ICMP packet containing the code 8 in the Type field.
What port number is ICMP?
Firewall rules for ICMP (TCP/UDP port 7)
What does ICMP type 3 mean?
destination unreachableICMP error messages of Type: 3 represent a "destination unreachable" situation, where code values clarify the type of unreachability, as follows: 0 = net unreachable; 1 = host unreachable; 2 = protocol unreachable; 3 = port unreachable; 4 = fragmentation needed and DF is set; 5 = source route failed.
Which of the following is not a type of ICMP message?
Explanation: Router error is not a type of error-reporting message in ICMP. The type of error reporting message is specified in the ICMP header. Destination unreachable is type 3 error message, source quench is type 4, and time exceeded is type 11 error message.
What does ICMP type 3 mean?
destination unreachableICMP error messages of Type: 3 represent a "destination unreachable" situation, where code values clarify the type of unreachability, as follows: 0 = net unreachable; 1 = host unreachable; 2 = protocol unreachable; 3 = port unreachable; 4 = fragmentation needed and DF is set; 5 = source route failed.
What does ICMP type 11 mean?
Whenever a packet or message is sent on a network, a Time to Live (TTL) value is attached. The TTL value decreases after passing reach layer 3 devices such as a router along the way to the destination.
Is ICMP port 7?
ICMP is IP protocol 1, TCP is 6 and UDP is 17. So these are all different protocols with different behaviors. TCP and UDP have Ports, ICMP does not. TCP and UDP have an Echo Service on Port 7, sometimes called TCP-Ping/UDP-Ping, but they have nothing to do with ICMP.
Is ICMP a layer 4?
The ICMP header is at layer 4, just like TCP and UDP so people argue that it belongs in layer 4.
Why is code 5 used for redirect?
Redirect (Code 5): Because routing is a dynamic process and only routers participate in it, so a host has information about only one router (gate way). So when this host sends a data, then the data will go through that router to the correct router.
What happens if a router cannot locate the path for a packet?
If a router cannot locate the path for a packet, then in such an event the packet is discarded and the destination is sent to the destination unreachable message. Source Quench (Code 4): As you know the IP does not have the flow control.
What is the type field in ICMP?
The type field identifies the type of the message sent by the host or gateway. Many of the type fields contain more specific information about the error condition. Table 3.2 lists the ICMP message types.
What is ICMP type 3?
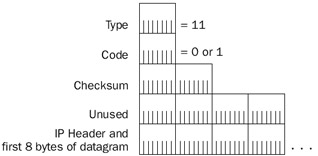
ICMP Type 3 message Destination Unreachable alerts a source host of delivery problems encountered while trying to reach the destination. Note that a destination host sends only code types 2 and 3; a router can send all codes. Destination Unreachable uses several code values to further describe the function of the ICMP message being sent. Each code type describes a different delivery problem encountered, as shown here:
Why does a receiving host send a message?
A receiving host generates this message when it cannot process datagrams at the speed requested due to a lack of memory or internal resources . This message serves as a simple flow control mechanism that a receiving host can utilize to alert a sender to slow down its transmission of data. When the source host receives this message, it must pass this information on to the upper-layer process, such as TCP, which then must control the flow of the application's datastream. A router generates this message when, in the process of forwarding datagrams, it has run low on buffers and cannot queue the datagram for delivery.
Why is ICMP echo request type 8 and echo reply type 0?
We discuss the ICMP Echo Request Type 8 and Echo Reply Type 0 because ICMP uses these messages in tandem. Remote hosts use these two message types to test connectivity. As previously mentioned, the user executes the Ping utility, initiating the generation of ICMP echo requests with the expectation that the destination host sends a corresponding echo reply. Upon successful receipt of the replies to the echo requests, the messages do the following:
How does ICMP address mask work?
Address mask request and reply messages work in tandem. Although we rarely use this message today, its original design supported the function of dynamically obtaining a subnet mask. Hosts can use the ICMP address mask request to acquire subnet masks during bootstrap from a remote host. However, problems can occur when using ICMP to receive a mask if a host gives an incorrect mask from an external source. If the external source does not give a response, the source host must assume a classful mask (that the network is not subnetted).
Is ICMP obsolete?
Although ICMP messages list information request and reply as a potential ICMP message type, they actually do not occur; thus they are obsolete. A host can request information such as to what network it was attached.
Can you use ICMP to update routing table?
Rather than initializing a routing table with static routes specified in configuration files, you can use the router ICMP advertisement and solicitation messages. After bootstrapping, a host can transmit a broadcast or multicast a solicitation message to which a router or routers responds with a router advertisement. This allows communicating hosts to learn of available routes dynamically and update their routing tables. We will discuss routing in more detail in Chapters 5 and 6.
What is ICMP redirect message?
An ICMP redirect message assists in making routing more efficient. In a case where a host has a default gateway, and the default gateway knows that a different local router if better for the network that the host is trying to reach, the gateway will send a redirect to the host, telling the host to use that router from now on. This may apply to all traffic to the particular destination network, or only traffic for the specific destination host.
What is ICMP echo?
ICMP echo and echo-reply are commonly use in the ping application. This sends an ICMP echo to a host, which returns an ICMP echo-reply. If unsuccessful, the request will either time out, or a device along the path will reply with some type of ICMP error message.
What is the echo packet?
An echo packet has type 8 set in the ICMP header, and the reply uses type zero. Neither have any codes defined, so the code field in the header is always set to zero. The second four bytes of the header includes two 16-bit fields; The Identifier and the Sequence. These are used to match a particular echo with the echo-reply.
Why is a code included in a packet?
This is included so the sender can match the error to the process that generated the original packet.
What is a solicitation message?
The Solicitation (type 10) message is sent by a host to multicast address 224.0.0.2, to request any routers on the local segment to identify themselves. Any routers that receive this message (and support IRDP) will reply with the Advertisement (type 9) message to announce their IP address as available for routing. Routers may also send the Advertisement message unsolicited on occasion (as more of an advertisement than a response).
Where is the IP address of a better router?
As shown in the packet capture below, the IP address of the ‘better’ router is included in the second 4 bytes of the header. The data section is populated with the first 8 bytes of the original packet, so the sender can match the message to the originating process.
When does the IP stack start a timer?
To handle this, the IP stack starts a timer when the first fragment arrives . If the timer expires before all the fragments are reassembled, the packet is discarded, and the Time Exceeded message is created and sent to the source.
How do routers broadcast IP addresses?
Routers periodically broadcast their IP addresses via Router Advertisement messages. Hosts may also request a router address by broadcasting a Router Solicitation message to which a router replies with a Router Advertisement. Time Exceeded.
What is the purpose of masking in a router?
Used to find the mask of the subnet (i.e. what address bits define the network). A host sends an Address Mask Request to a router and receives an Address Mask Reply in return.
What is echo ping?
Used to test destination accessibility and status. A host sends an Echo Request and listens for a corresponding Echo Reply. This is most commonly done using the ping command.
What is obsolete message?
Obsolete. These messages were used earlier by hosts to determine their inter-network addresses, but are now considered outdated and should not be used.
What is a datagram in a router?
Sent by a router when it cannot deliver an IP datagram. A datagram is the unit of data, or packet, transmitted in a TCP/IP network.
What is ICMP message?
ICMP Router Advertisement type of messages allows routers to advertise their presence to computers in a network segment. Computers discover the addresses of the routers by listening Router Advertisement messages.
What is ICMP echo?
ICMP Echo/Echo Reply type of messages are used by uilities like Ping, Tracert, Pathping etc. These tools are mainly used for network troubleshooting.
What is ICMP solicitation?
ICMP Router Solicitation type of messages are used by computers in a network segment for immediate Router Advertisement messages.
What is ICMP source queue?
ICMP Source Quench type of messages allows to inform a sending computer to drcrease its sending rate to ease congestion. Deprecated.
How many different types of ICMP messages are there?
There are 15 different types of ICMP messages and some are categorized as error reporting and query.
What is ICMP attack?
ICMP attacks. ICMP stands for Internet Control Message Protocol and is the most used protocol in networking technology. A connectionless protocol, ICMP does not use any port number and works in the network layer.
How many bytes are in an ICMP echo request?
In a normal ICMP echo request, the packet length will be 42 bytes, where the data length is 0, and if we append any data into the ICMP data field then the size of the packet increases. In the above scenario, the total size is 72 bytes out of which 30 bytes is the data “sending packets via tunneling”. So if we want to detect ICMP tunneling via any IDS/IPS devices we need to write a rule stating that if any data is present in the data header of the ICMP, then fire an alert.
How to prevent ICMP tunneling?
Organizations have adopted many ways to prevent ICMP tunneling, like blocking all ICMP traffic, limiting the size of ICMP packets, etc. However, some methods listed above are not realistic for the real-world environment. The use of IDS/IPS is an effective method and many IPS/IDS devices have a signature to detect the presence of LOKI.
What is ICMP error?
ICMP error messages are not sent in response to an ICMP error. When an ICMP error is sent, it always sends the IP header and the datagram that caused the error. So the receiving unit gets to associate the error with the process.
What is ICMP tunnel?
ICMP tunnels are one form of covert channel that is created wherein the information flow is not controlled by any security mechanism. An ICMP tunnel establishes a channel between the client and server, forcing a firewall not to trigger an alarm if data are sent via ICMP. ICMP tunnelling is a covert connection between two endpoints using ICMP echo requests and reply packets. So by using ICMP tunnelling, one can inject arbitrary data into an echo packet and send to a remote computer. The remote computer injects an answer into another ICMP packet and sends it back. This type of communication traffic remains undetectable for a proxy-based firewall, as they are more focused on source and destination IP address.
How to counteract address spoofing?
Put filters on routers and firewalls to counteract address spoofing. An IP address should be assigned to a LAN segment, and if the IP address of the source machine is not in the range of IP address that is assigned to the segment, then the traffic should be dropped.

Ping: Echo Request and Reply—Types 8 and 0
Destination Unreachable—Type 3
Source Quench—Type 4
Redirect—Type 5
Router Advertisement and Solicitation—Types 9 and 10
Time Exceeded—Type 11
Parameter Problem—Type 12
Timestamp Request and Reply—Types 13 and 14
Information Request and Reply—Types 15 and 16
- Although ICMP messages list information request and reply as a potential ICMPmessage type, they actually do not occur; thus they are obsolete. A host canrequest information such as to what network it was attached.
Address Mask Request and Reply—Types 17 and 18