What is ACAS and how does it work?
The ACAS solution delivers comprehensive network and application vulnerability scanning and configuration assessment. TASKORD 20-0020 mandates the use of Tenable.sc (formally SecurityCenter), Nessus Vulnerability Scanner, Nessus Agents, and Nessus Network Monitor. Nessus technologies scan targeted networks and endpoints to gather resulting data.
What is the ACAS Nessus scanner?
Nessus is the scanning component of ACAS that is compliant with not only CVE vulnerability identifiers, but also DISA STIGs. This is one of the main advantages of Nessus over DoD’s previous scanner, Retina.
What is ACAS (assured compliance assessment solution)?
Assured Compliance Assessment Solution (ACAS) is an integrated software solution with an ability to perform automated vulnerability scanning, configuration assessment. It has the ability to scale to an unlimited number of locations.
What is a “scan”?
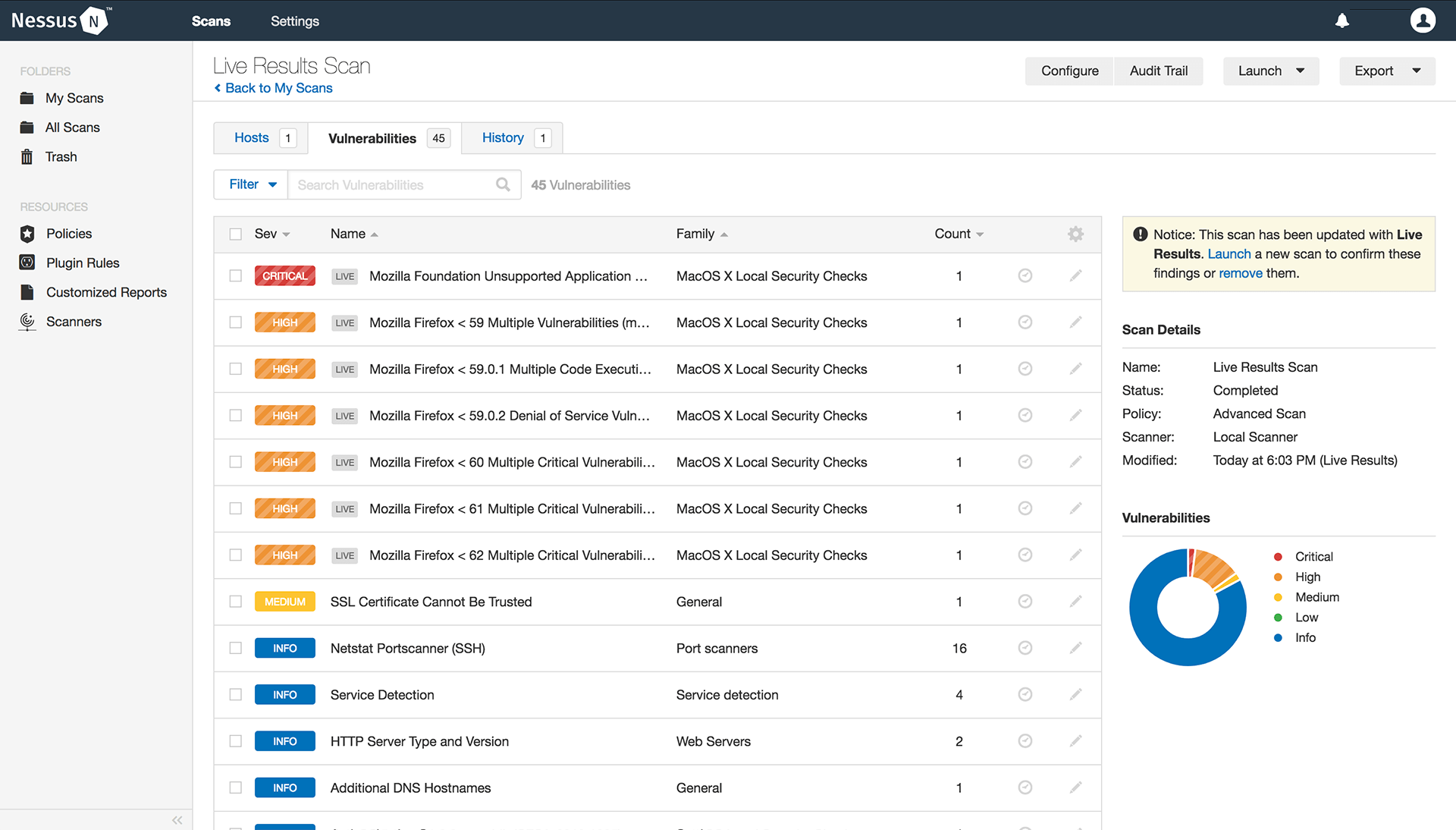
The scan contains a customized policy which includes specific tests or “plugins” (referenced by plugin id number in the Building the Scan section below). Note that “scan” and “scan policy” are used synonymously in this blog. When I first started working with Nessus and SecurityCenter, I scanned using vulnerability and compliance scans.

What is included in ACAS?
This next generation vulnerability analytics component for ACAS includes: Assurance Report Cards, Advanced Analytics/Trending, Customizable Dashboards/Reports and Cumulative Scan Results. Tenable®, Inc. is the Cyber Exposure company.
What is the difference between Nessus and ACAS?
Nessus is the scanning component of ACAS that is compliant with not only CVE vulnerability identifiers, but also DISA STIGs. This is one of the main advantages of Nessus over DoD's previous scanner, Retina. In the DoD world, the compliance with STIGS is just as important as the compliance with software vulnerabilities.
What is DISA ACAS?
The Defense Information Systems Agency's (DISA) selection of Tenable as the foundation of its Assured Compliance Assessment Solution (ACAS) cements Tenable's standing as the undisputed leader in vulnerability management in the U.S. Federal government.
What does Nessus ACAS stand for?
assured compliance assessment solutionACAS = stands for assured compliance assessment solution. It includes COTS from Tenable and HP. The word's become sort of a catchall term for the following: Nessus = the scanners Security Center = manages the scanners and collects the results. 1.
Is ACAS software free?
ACAS consists of a suite of products to include the Security Center, Nessus Scanner and the Nessus Network Monitor which is provided by DISA to DoD Customers at no cost.
What are Nessus scans?
Nessus is a remote security scanning tool, which scans a computer and raises an alert if it discovers any vulnerabilities that malicious hackers could use to gain access to any computer you have connected to a network.
Is Tenable and ACAS the same?
Tenable Network Security, Inc., the leader in Unified Security Monitoring (USM), announced today it has been selected by the Defense Information Systems Agency (DISA) as the Assured Compliance Assessment Solution (ACAS).
What is DoD Stig?
What is STIG Security? Security Technical Implementation Guides (STIGs) are a series of cybersecurity requirements for IT products deployed within DoD agencies. STIGs are the source of configuration guidance for network devices, software, databases and operating systems.
How often are ACAS plugins updated?
By default, Nessus checks for updated components and plugins every 24 hours. Alternatively, you can update plugins manually from the Scanner Settings Page in the user interface.
What devices can Nessus scan?
Nessus can perform audits on Windows and several Unix-compatible systems, including: Windows: Windows 2008 Server....Unix-Compatible:Solaris.Linux.FreeBSD/OpenBSD/NetBSD.HP/UX.AIX.Mac OS X.
How does a vulnerability scanner work?
A vulnerability scanner is an automated vulnerability testing tool that monitors for misconfigurations or coding flaws that pose cybersecurity threats. Vulnerability scanners either rely on a database of known vulnerabilities or probe for common flaw types to discover unknown vulnerabilities.
How do you analyze Nessus report?
0:333:59Basic Scan Results Analysis in Nessus Professional - YouTubeYouTubeStart of suggested clipEnd of suggested clipWe list each individual hosts and the number of vulnerabilities contained in each host. We can'tMoreWe list each individual hosts and the number of vulnerabilities contained in each host. We can't click on a host. I'm bearing up information now you'll notice we have a list of vulnerabilities.
What is Tenable and Nessus?
Nessus is a proprietary vulnerability scanner developed by Tenable, Inc. Tenable.io is a subscription-based service. Tenable also contains what was previously known as Nessus Cloud, which used to be Tenable's Software-as-a-Service solution.
Who created ACAS?
ACAS was implemented by the DoD in 2012, with contracts awarded to Tenable, Inc. (then known as Tenable Network Security) and Hewlett Packard Enterprise Services to improve cybersecurity within the DoD. It is mandated by regulations for all DoD agencies and is deployed via download.
What is the SCAP tool?
An SCAP scanner is a tool that compares a target computer or application's configuration and/or patch level against that of the SCAP content baseline. The tool will note any deviations and produce a report.
What is Tenable security Center?
Tenable.sc is a comprehensive vulnerability management solution that provides complete visibility into the security posture of your distributed and complex IT infrastructure.
What is an ACAS?
Written by Jeremy Galliani on May 29, 2015. The Assured Compliance Assessment Solution (ACAS) is a suite of COTS applications that each meet a variety of security objectives and was developed by Tenable.
What components of ACAS are used to monitor load?
The two components of ACAS you’ll have to monitor for load are Nessus and PVS. Nessus is considered the active scanner while PVS is passive.
What is ACAS security?
ACAS is just one of many security programs DoD has put in place to protect sensitive information.
What is passive vulnerability scan?
The main purpose of Passive Vulnerability Scanner (PVS) is to monitor network traffic at the packet level. While Nessus monitors device vulnerabilities, PVS monitors the network traffic traversing your network for vulnerabilities. Please note that PVS is not an IDS and does not replace one in your network. PVS provides the ability to discover new hosts added to a network, find out which ports are passing traffic across the network, identify when applications are compromised, and monitor mobile devices connected to your network.
Is Nessus a scanner?
This is one of the main advantages of Nessus over DoD’s previous scanner, Retina. In the DoD world, the compliance with STIGS is just as important as the compliance with software vulnerabilities. The library of Nessus plugins (audit files) is massive and is updated almost daily to account for the latest threat vectors.
What is ACAS software?
Assured Compliance Assessment Solution (ACAS) is a software set of information security tools used for vulnerability scanning and risk assessment by agencies of the United States Department of Defense (DoD). It performs automated vulnerability scanning and device configuration assessment. ACAS was implemented by the DoD in 2012, with contracts awarded to Tenable and Hewlett Packard Enterprise Services to improve cybersecurity within the DoD. It is mandated by regulations for all DoD agencies and is deployed via download. Part of the ACAS software monitors passive network traffic, new network hosts, and applications that are vulnerable to compromise. It also generates required reports and data that are remotely accessible, with a centralized console, and is Security Content Automation Protocol (SCAP) compliant. The Defense Information Systems Agency 's Cyber Development (CD) provides program management and support in the deployment of ACAS. The Army's Systems Engineering and Integration Directorate said in 2016 that ACAS gives the Army "a clear, specific and timely picture of cyber vulnerabilities and how they are being addressed. Not only does the technology streamline processes at the operator level, it also enables broader goals such as the Cybersecurity Scorecard and automated patching for improved mission assurance."
When was ACAS implemented?
ACAS was implemented by the DoD in 2012, with contracts awarded to Tenable, Inc. (then known as Tenable Network Security) and Hewlett Packard Enterprise Services to improve cybersecurity within the DoD. It is mandated by regulations for all DoD agencies and is deployed via download.
What is a QCD scan?
The QCD scan is built with tests recommended by Tenable customers and other sources. QCD works with Tenable scanning products: from Tenable.io™ and SecurityCenter® to Nessus® Manager and Professional. The scan contains a customized policy which includes specific tests or “plugins” (referenced by plugin id number in the Building the Scan section below). Note that “scan” and “scan policy” are used synonymously in this blog.
Can you build a scan policy?
You can build this scan policy yourself or download the XML file available on the Tenable Community.
What is credentialed scan?
Credentialed scans can perform a wider variety of checks than non-credentialed scans, which can result in more accurate scan results. This facilitates scanning of a very large network to determine local exposures or compliance violations. Credentialed scans can perform any operation that a local user can perform.
What are the two types of scans that can be performed with Tenable?
Scanning Overview. You can perform two types of scans using Tenable products: discovery scans and assessment scans. Tenable recommends performing discovery scans to get an accurate picture of the assets on your network and assessment scans to understand the vulnerabilities on your assets.
Do discovery scans count toward license?
Assets identified by discovery scans do not count toward your license.
