
How to solve Atbash?
With Atbash, the Affine formula is a = b = (m − 1), where m is the length of the alphabet. Decoding or Encoding the Atbash Cipher. Text that has been encrypted with Atbash is most easily identified using frequency analysis. The most commonly used letters in English are E, T and A. When these have been encrypted using Atbash, they become V, G and Z.
How to decodeatbash cipher?
What is the best way to manage passwords?
- Never reveal your passwords to others.
- Use different passwords for different accounts.
- Use multi-factor authentication (MFA).
- Length trumps complexity.
- Make passwords that are hard to guess but easy to remember.
- Complexity still counts.
- Use a password manager.
How to create substitution ciphers?
Types of Substitution Ciphers
- Simple Substitution. The most basic type of substitution cipher is called a simple substitution. ...
- Homophonic Substitution. Homophonic ciphers were designed to be more difficult to crack than a basic substitution cipher by utilizing homophony.
- Polyalphabetic Substitution. ...
- Polygraphic Substitution. ...
- The Bottom Line. ...
What cipher is described above?
What cipher is described above? This asymmetry cipher is based on factoring the product of two large prime numbers. What cipher is described above? RSA is based on the practical difficulty of factoring the product of two large prime numbers, the factoring problem.
Why is it called Atbash cipher?
It is a simple substitution code, where the first letter of the alphabet (א alef) is replaced by the last (ת taw), the second letter (ב bet) by the second last (ש sin or shin) etc. The name 'atbash' refers to the first letters of the names of these Hebrew characters: alef, taw, bet and shin.
How do I read Atbash cipher?
0:101:34Atbash Cipher - YouTubeYouTubeStart of suggested clipEnd of suggested clipSo that the first letter becomes the last letter the second letter becomes the second-to-last letterMoreSo that the first letter becomes the last letter the second letter becomes the second-to-last letter. And so on for example the latin alphabet that we use would look like this.
Why did the Atbash cipher stop being useful?
The Atbash cipher is another type of substitution cipher. It entails replacing each letter in the plaintext with the corresponding letter if the alphabet were reversed. The Atbash cipher does not use a key and this is the reason why it doesn't provide any communication security.
How do I break Atbash cipher?
The Atbash cipher offers almost no security, and can be broken very easily. Even if an adversary doesn't know a piece of ciphertext has been enciphered with the Atbash cipher, they can still break it by assuming it is a substitution cipher and determining the key using hill-climbing.
How do I decode a cipher code?
10:1622:36How to Use a Basic Cipher to Encode and Decode a Secret MessageYouTubeStart of suggested clipEnd of suggested clipThey'll look for the letter W. And see that W is associated with the letter A. They'll look for theMoreThey'll look for the letter W. And see that W is associated with the letter A. They'll look for the letter L. And see that the letter L is associated with the letter P.
Is Atbash a language?
Atbash (Hebrew: אתבש; also transliterated Atbaš) is a monoalphabetic substitution cipher originally used to encrypt the Hebrew alphabet. It can be modified for use with any known writing system with a standard collating order.
What is a qwerty cipher?
The Qwerty/Keyboard Substitution Cipher (not to be confused with the Qwerty/Keyboard Shift Cipher) is a simple cipher that rearranges the order of the alphabet to the way it is on a standard American keyboard. So A would become Q, B would be W, C would be E, and so on.
How old is the Atbash cipher?
When was Atbash invented? Atbash would have been imagined between -1000 and -500 (before Christ).
Who is the father of cryptography?
Claude E. Shannon is considered by many to be the father of mathematical cryptography. Shannon worked for several years at Bell Labs, and during his time there, he produced an article entitled "A mathematical theory of cryptography".
What is a mirror cipher?
It is a rudimentary device with encrypts the message by switching its letter with its mirror opposite (A => Z), (B => Y), (C => X) etc. Your job is to build a method called "mirror" which will decrypt the messages. Resulting messages will be in lowercase.
What type of cipher is the Atbash cipher?
substitution cipherDefinition: Atbash cipher is a substitution cipher with just one specific key where all the letters are reversed that is A to Z and Z to A. It was originally used to encode the Hebrew alphabets but it can be modified to encode any alphabet.
What is the difference between Caesar cipher and Atbash cipher?
Examples of monoalphabetic ciphers would include the Caesar-shift cipher, where each letter is shifted based on a numeric key, and the atbash cipher, where each letter is mapped to the letter symmetric to it about the center of the alphabet.
How do you decipher Gravity Falls codes?
1:226:17Gravity Falls Cryptogram Secrets Revealed - YouTubeYouTubeStart of suggested clipEnd of suggested clipManliness example time in tourist traps the end credits cryptogram reads zi h o f RP h w r ju d y LWMoreManliness example time in tourist traps the end credits cryptogram reads zi h o f RP h w r ju d y LW b i do o v. Take each letter. And go back three steps and bam.
How do you decode Polybius square?
1:533:55Math for Liberal Studies: Decoding a Message Using the Bifid CipherYouTubeStart of suggested clipEnd of suggested clipMessage underneath the pluteus square G H PK f ni g and what we'll do is we'll look up each of theseMoreMessage underneath the pluteus square G H PK f ni g and what we'll do is we'll look up each of these letters. In our square. So where is the letter G. Well the letter G is in row 1 column 3.
How do you decode a scytale cipher?
To decrypt, all one must do is wrap the leather strip around the rod and read across. The ciphertext is: "Iryyatbhmvaehedlurlp" Every fifth letter will appear on the same line, so the plaintext (after re-insertion of spaces) becomes: "I am hurt very badly help".
How do you decode a Caesar cipher?
To encrypt a message, enter the message in the Plaintext textbox, specify the shift, and click Encrypt. To decrypt a message, enter the message in the Ciphertext textbox, specify the shift, and click Decrypt.
What is the Atbash cipher?
Encryption. The Atbash cipher is a particular type of monoalphabetic cipher formed by taking the alphabet (or abjad, syllabary, etc.) and mapping it to its reverse, so that the first letter becomes the last letter, the second letter becomes the second to last letter, and so on.
Does the Atbash cipher provide security?
B. A. Due to the fact that there is only one way to perform this, the Atbash cipher provides no communications security, as it lacks any sort of key. If multiple collating orders are available, which one was used in encryption can be used as a key, but this does not provide significantly more security, considering that only a few letters can give ...
What is the Atbash cipher?
The Atbash Cipher was originally a monoalphabetic substitution cipher used for the Hebrew alphabet. It is one of the earliest known subtitution ciphers to have been used, and is very simple. However, it's simplicity is also it's biggest pitfall, as it does not use a key. Hence every piece of plaintext enciphered using the Atbash Cipher uses ...
How does the Atbash Cipher work?
The Atbash Cipher simply reverses the plaintext alphabet to create the ciphertext alphabet. That is, the first letter of the alphabet is encrypted to the last letter of the alphabet, the second letter to the penultimate letter and so forth.
What is the ciphertext alphabet?
The ciphertext alphabet for an alphabet containing punctuation, a space and the digits 0-9. For the first two questions, use the given alphabet to encrypt the message using the Atbash Cipher. For the second two questions, use the alphabet to decrypt the ciphertext. Flee at once.
What does the Hebrew word "Aleph" mean?
In the original Hebrew this means that 'aleph' is encrypted to 'tav', and 'beth' to 'shin'. This is where we get the name of the cipher 'atbash'. For the Hebrew alphabet we get the following conversion table. The ciphertext alphabet for the Atbash cipher on the Hebrew alphabet.
Is the Atbash cipher a substitution cipher?
The Atbash Cipher is a very weak substitution cipher, since there is no secret key behind generating the ciphertext alphabet to perform the encryption. Thus, given a piece of ciphertext, known to have been enciphered using the Atbash Cipher, anyone who intercepts the message can easily decipher it to retrieve what was meant to be concealed.
Is decryption the same as encryption?
Decryption. Due to the symmetric nature of this cipher, the decryption process is exactly the same as the encryption process. Thus, for the recipient to decrypt the ciphertext, the same ciphertext alphabet must be generated as was used to encrypt the message in the first place. In this case, the ciphertext alphabet relies only on the alphabet used, ...
What is an atbash cipher?
Definition: Atbash cipher is a substitution cipher with just one specific key where all the letters are reversed that is A to Z and Z to A. It was originally used to encode the Hebrew alphabets but it can be modified to encode any alphabet.
What is the relationship between Atbash and Affine?
Relationship to Affine: Atbash cipher can be thought of as a special case of Affine cipher with both the keys being 25, i.e, a = 25 & b = 25
Is Atbash a constant key?
Analysis : It has one constant key it is the easiest cipher to break and provides almost no security. Anyone can assume that it is atbash and decrypt the message by reversing the letters.
Sex Magick
In both tables above I have used the L/T transposition, but of course the Golden Dawn does not transpose the steps in its rituals. As I have tried to show above, this is not an obstacle to magic. Philosophically, since the End is in the Beginning, we have to assume that the result is already there, but it has not manifested.
Communicating with Spirits
At the fundamental roots of the Atbash code, and structured within Tarot, is the sex magickal system of the Golden Dawn and of the OTO. Daath, the 11th sephira, is also the Gateway to other Universes and beings.
The Supernal Triangle
What happens if we reverse the order of the Sephiroth? Quite simply, the transposition of L and T is within the Supernal Triangle, and involves Kether and Binah, whose Path is the Magus. The sephiroth of Binah and Chokmah as Mother and Father respectively, are replete with sexual imagery – see Liber 777 and Dion Fortune’s Magical Qabalah.
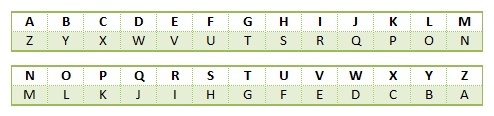
Decoding Or Encoding The Atbash Cipher
- Text that has been encrypted with Atbash is most easily identified using frequency analysis. The most commonly used letters in English are E, T and A. When these have been encrypted using Atbash, they become V, G and Z. If you find a cipher text with a lot of Vs, there’s a good chance y…
History
- While a lot of people look at ancient Egypt for the origins of codes (and that is where the first evidence of encryption was found) Atbash was actually the first cipher. It has its origins in Israel and was originally used to encrypt and decrypt the Hebrew alphabet. That’s where the name comes from, it’s a shortened version of Aleph Taw Bet Shin, The first, last, second, and second-fr…
Usage
- Like other simple substitution ciphers such as ROT13, Atbash doesn’t have any practical uses for encryption because it is so simple to decrypt. With no key needed to translate it, it is easily broken with just a pen and paper. You will see Atbash pop up in puzzle games, and if you get practiced enough at it you can use it to hide the meaning of things from prying eyes, but it won’t stand up t…
Variants
- Atbash in its regular form only encrypts the letters A-Z, leaving numbers and punctuation as plain text. Variant forms of the cipher do exist which include numbers and the most common punctuation symbols. This is similar to the way ROT13 has been expanded in the ROT18 and ROT47 ciphers.
Flip It and Reverse It
- As the first cipher used, we can forgive Atbash for its simplicity. It was invented in days gone by, when far less people were literate and there were no computers who could flip the text with ease. It’s still worth knowing about because of its frequent appearances in puzzle games and the like, but if you really want to hide your secrets, you’re going to have to look elsewhere.
Overview
Atbash (Hebrew: אתבש; also transliterated Atbaš) is a monoalphabetic substitution cipher originally used to encrypt the Hebrew alphabet. It can be modified for use with any known writing system with a standard collating order.
Relationship to the affine cipher
The Atbash cipher can be seen as a special case of the affine cipher.
Under the standard affine convention, an alphabet of m letters is mapped to the numbers 0, 1, ... , m − 1. (The Hebrew alphabet has m = 22, and the standard Latin alphabet has m = 26). The Atbash cipher may then be enciphered and deciphered using the encryption function for an affine cipher by setting a = b = (m − 1):
Encryption
The Atbash cipher is a particular type of monoalphabetic cipher formed by taking the alphabet (or abjad, syllabary, etc.) and mapping it to its reverse, so that the first letter becomes the last letter, the second letter becomes the second to last letter, and so on. For example, the Latin alphabet would work like this:
Due to the fact that there is only one way to perform this, the Atbash cipher provides no commun…
History
The name derives from the first, last, second, and second to last Hebrew letters (Aleph–Taw–Bet–Shin).
The Atbash cipher for the modern Hebrew alphabet would be:
Several biblical words are described by commentators as being examples of Atbash:
• Jeremiah 25:26 – "The king of Sheshach shall drink after them" – Sheshach meaning Babylon in A…
See also
• Temurah (Kabbalah)
• Gematria
• Hebrew language
• ROT13
Notes
1. ^ Rashi and Radak on each of the first three verses. Also other commentators.
External links
• Online Atbash decoder