
A security token is a physical or digital device that provides two-factor authentication (2FA) for a user to prove their identity in a login process. It is typically used as a form of identification for physical access or as a method of computer system access.
Full Answer
How do I get a security token?
- Log into Salesforce via the browser to request your security token.
- Do one of the following: If you have a regular Salesforce account, go to Setup > My Personal Information > Reset Security Token.
- Select and copy the token from the email.
What are the challenges to establish security tokens?
security tokens presents multiple challenges, be they technological, regulatory or legal. The regulatory framework applicable to the relevant arrangements, as well as the contractual documents that govern them, must be able to manage them as a whole. In view of the responses received, developing the use of security tokens is subject to various
What is a security token?
As the name would suggest, a security token is a tokenized security, most likely one that is based upon a blockchain. Security tokens can be used to represent many different kinds of traditional assets, including stocks, commodities, debts, and real estate.
What are the implications of security tokens?
The specificity of security tokens is that they are investment products (e.g., stocks and bonds) and thus usually confer cashflow rights to investors and, in some cases, also voting rights. Security tokens are issued through an STO and, as investment products, represent an alternative way for firms to raise external capital.
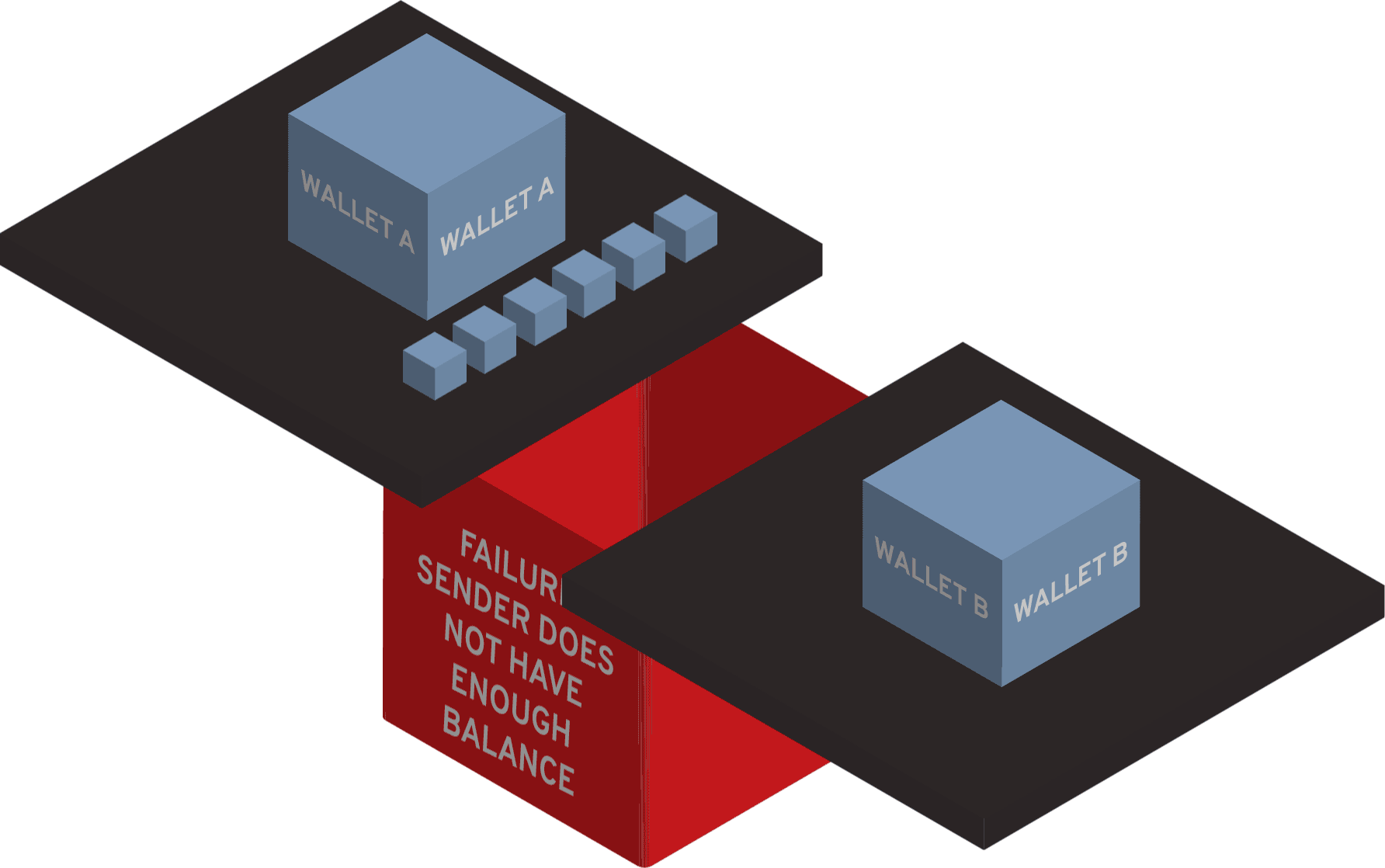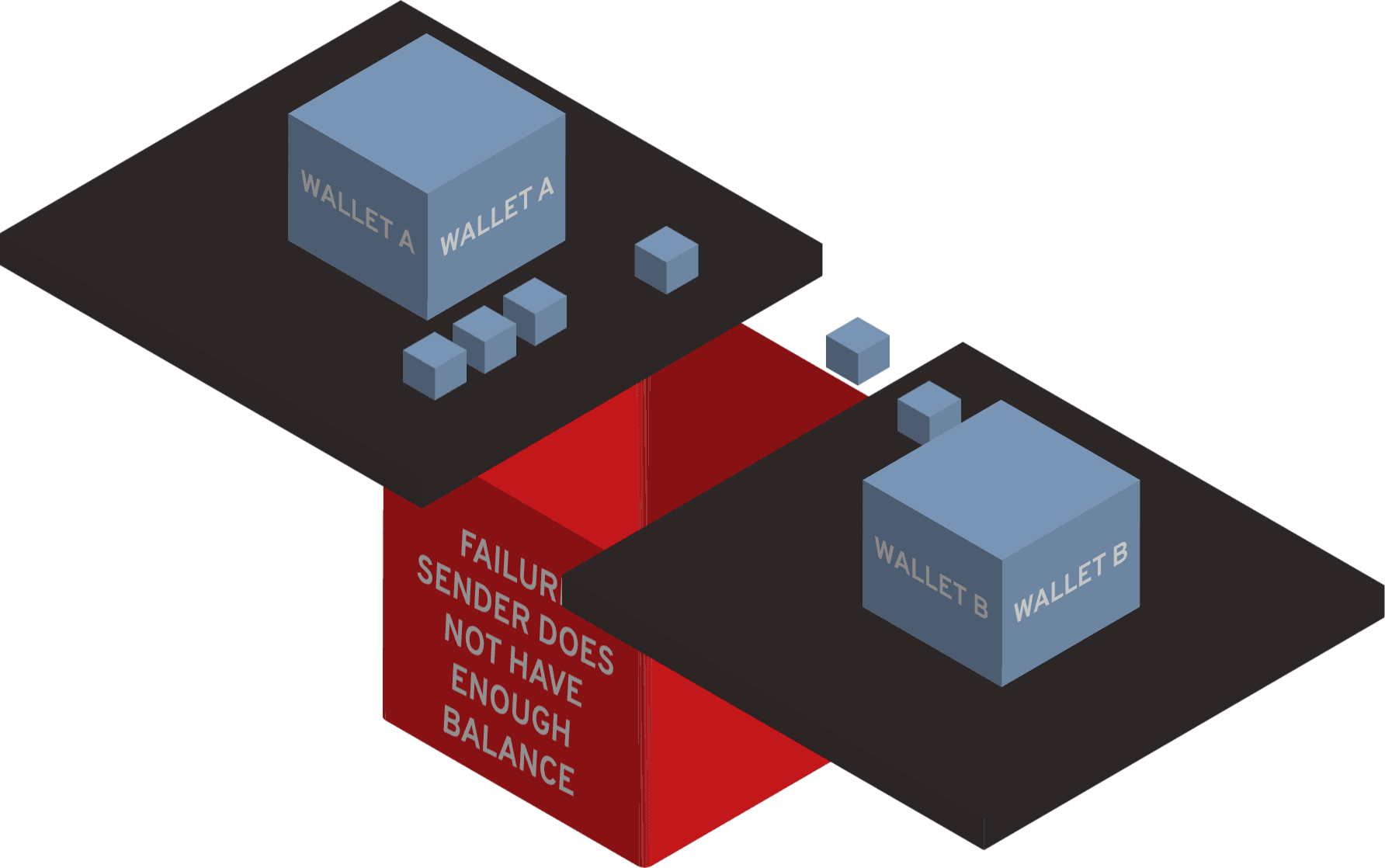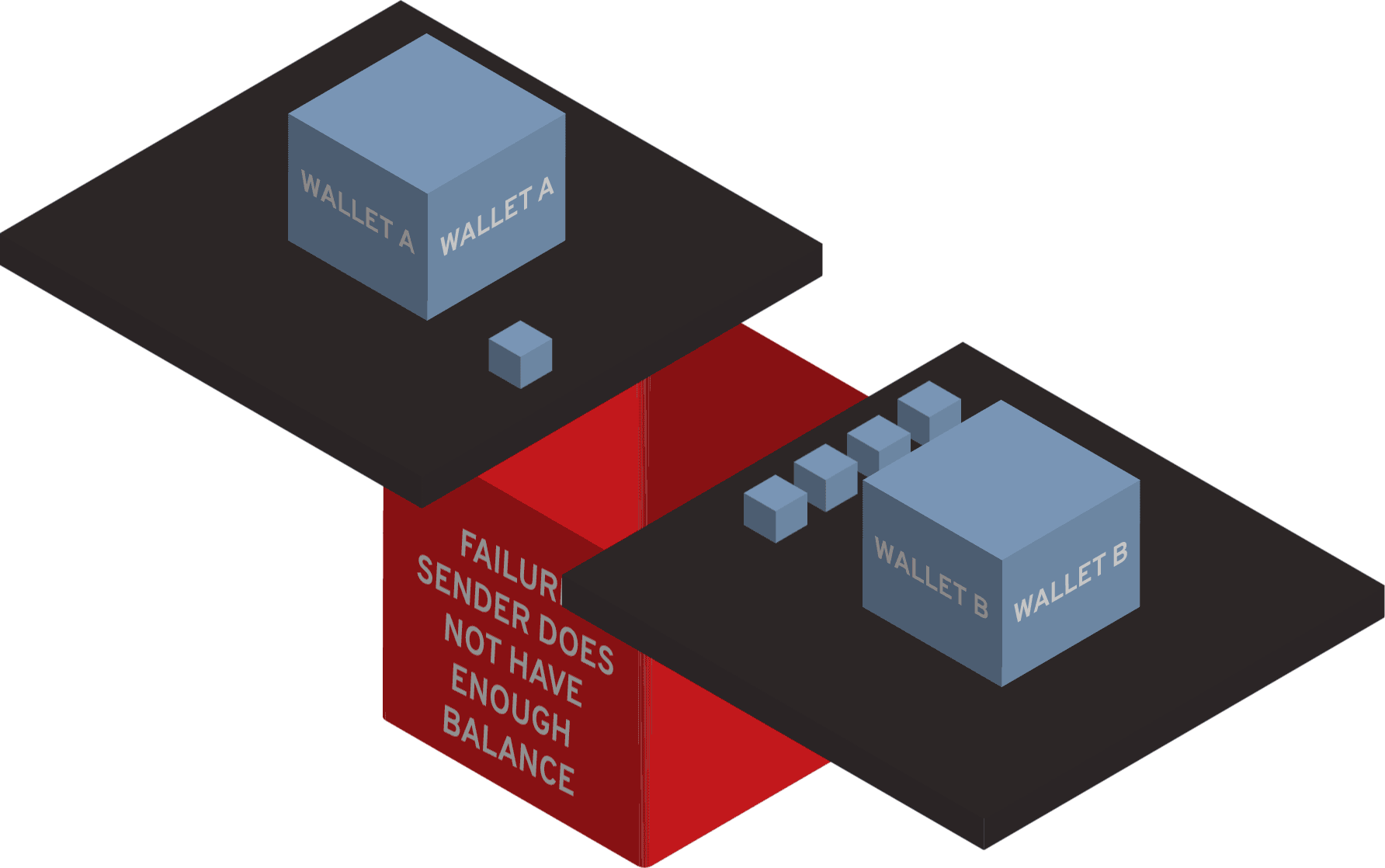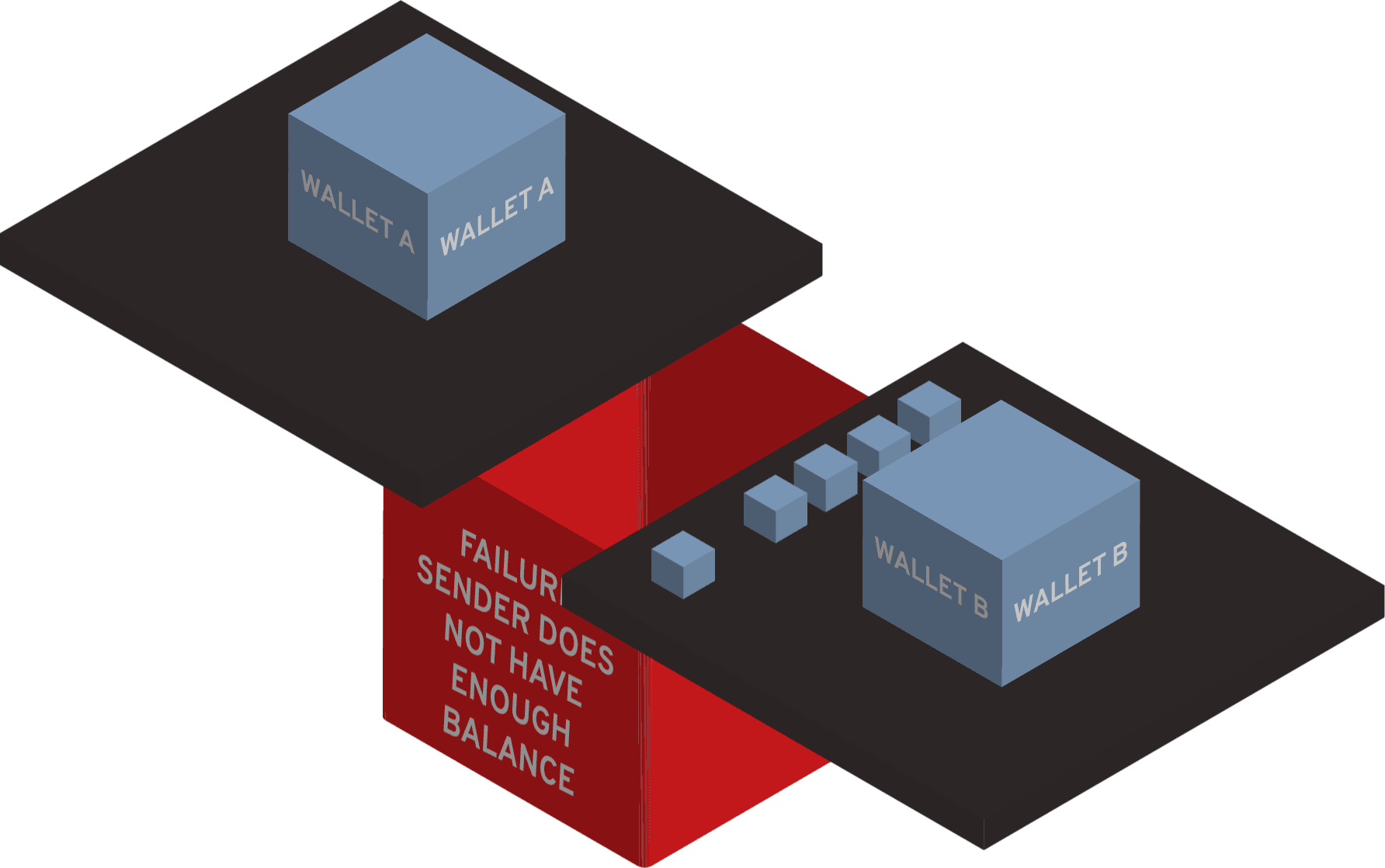
What is a security token example?
Car remotes are examples of security tokens people use regularly. Security tokens are used to authenticate users, and they can be used either to substitute passwords or other authentication methods or used as additional authentication in multi-factor authentication (MFA) flow.
What is the meaning of security tokens?
A security token is a physical or digital device that provides two-factor authentication (2FA) for a user to prove their identity in a login process. It is typically used as a form of identification for physical access or as a method of computer system access.
How do I find my security token?
To gain access to your security token, go to “Setup” (appears in the top right corner, under your name). In the left side menu column (under Personal Setup), open the drop down item “My Personal Information.” The option to reset your security token will appear right under password reset option.
How do security tokens work?
How do tokens work? In many cases, tokens are created via dongles or key fobs that generate a new authentication token every 60 seconds in accordance with a known algorithm. Due to the power these hardware devices hold, users are required to keep them safe at all times to ensure they don't fall into the wrong hands.
Which crypto is a security token?
Most security token platforms use the Ethereum ERC 2.0 or Tezos' FA1.
Is ethereum a security token?
Just like utility tokens, most security tokens run on the Ethereum blockchain. However, other smart contract-enabled blockchains also support them. The tokens can come in a variety of forms, from shares of ownership in a company, piece of art, intellectual property, or any other kind of asset.
How do I activate my security token?
Activate your Security TokenLogin to Online Banking via a desktop computer.Click on the hyperlink to activate the token.Key in the 10-digit serial number found on the back of your token.Press and hold the OTP button on your token and key in the OTP displayed on the LCD screen into the field provided.That's all.
How do I reset my security token?
To reset your token, contact your admin. From your personal settings, in the Quick Find box, enter Reset , and then select Reset My Security Token. Click Reset Security Token. The new security token is sent to the email address in your Salesforce personal settings.
How do I activate token code?
Once you are logged in, go to settings and click on the Help menu on your left. Enter your token Identification Number without the hyphen (for example 1234718343) in the space provided and then select “Acknowledge” and click “Continue”. The Identification Number is on a white panel at the back of your token.
What is a token used for?
Tokens can be used for investment purposes, to store value, or to make purchases. Cryptocurrencies are digital currencies used to facilitate transactions (making and receiving payments) along the blockchain. Altcoins and crypto tokens are types of cryptocurrencies with different functions.
Can security token be hacked?
Hacking. Tokens should protect users from malware, and companies like banks often tell their customers token systems are safer for that reason. But anything that's electronic and connected to a network can be hacked by someone with skill and patience.
What token means?
In general, a token is an object that represents something else, such as another object (either physical or virtual), or an abstract concept as, for example, a gift is sometimes referred to as a token of the giver's esteem for the recipient. In computers, there are a number of types of tokens.
What token means?
In general, a token is an object that represents something else, such as another object (either physical or virtual), or an abstract concept as, for example, a gift is sometimes referred to as a token of the giver's esteem for the recipient. In computers, there are a number of types of tokens.
What are the best security tokens?
Top Security Token PlatformstZERO.INX.ADDX.Nxchange.
What are tokens used for?
Tokens can be used for investment purposes, to store value, or to make purchases. Cryptocurrencies are digital currencies used to facilitate transactions (making and receiving payments) along the blockchain. Altcoins and crypto tokens are types of cryptocurrencies with different functions.
How do I create a security token?
How to create a security token and run an STOSection one: Decide what rights the security token provides.Section two: Choose which jurisdiction to operate in.Section three: Choose a security token issuance platform.Section four: Create the token.Section five: Run the security token offering.
What is a security token?
A security token is a physical device that users must possess to access a system. Authentication data must flow between both the user and the system to validate identities and access. A security token is the conduit for this data.
How Do Security Tokens Work?
Each year, hackers cause approximately $400 billion in losses. Businesses have to protect against this very real threat, or the damage could be immense.
Why are tokens important?
Hacking. Tokens should protect users from malware, and companies like banks often tell their customers token systems are safer for that reason. But anything that's electronic and connected to a network can be hacked by someone with skill and patience. While security tokens add another layer of support, they aren’t impervious to hacking.
What is connected token?
Connected tokens. Users must physically tie the token to the system they want to use. A smartcard or fob like a Yubikey is a good example. Users slide the device into a reader, and the device automatically pushes authentication information to the computer system.
How does crypto work?
Crypto security tokens work as a sort of liquid contract. Some experts believe this form of security token represents the future of finance. These tokens have a security element, but they aren't germane to the work most IT administrators do every day.
What is a static password?
Static passwords. A string of numbers, letters, or both sit within the token. The password never changes without direct support from a security professional. The person who holds the token may not know that the password exists, and the person can't call out the data if asked. Dynamic passwords.
Why do banks use two factor authentication?
Some companies, including banks, use their two-factor authentication plans as selling points to cautious customers. By proving the company cares about safety, they are more likely to retain and build their customer base.
What are Security Tokens?
As the name would suggest, a security token is a tokenized security, most likely one that is based upon a blockchain. Security tokens can be used to represent many different kinds of traditional assets, including stocks, commodities, debts, and real estate. Anthony Pompliano, founder and partner of Morgan Creek Digital Assets, aptly describes security tokens as “the intersection of digital assets (tokens) with traditional financial products — a new technology improving old things.”
What is a Security?
In traditional finance, a security is defined as a tradable financial instrument that has some form of monetary value. Securities are generally issued by a company or government in order to raise capital—and purchased by investors looking to make a profit.
What is ICO in blockchain?
If you’ve been following the cryptocurrency industry for any length of time, you’re likely familiar with initial coin offerings (ICOs), which allow blockchain developers to acquire funding for future projects through digital token sales. During the height of the ICO boom, much was made about how ICOs were the future of crowdfunding, and how ICOs were going to replace earlier funding mechanisms like initial public offerings (IPOs).
What is the SEC?
In the United States, the relevant government agency is the Securities and Exchange Commission (SEC), which was created as part of the Securities Exchange Act of 1934.
What is equity security?
Equity securities represent ownership interest in a company (like a stock). Ownership of an equity security does not usually entitle the holder to regular payments; however, holders can still profit from an equity security through capital gains or by trading on a secondary exchange. Additionally, equity securities usually confer upon their owners voting rights—giving them a partial say in how the company is run based on the number of shares that they own.
Is Ethereum a security?
Many have suspected that ether, the cryptocurrency of the Ethereum network, might be labeled a security, particularly because the platform was crowdfunded in its early days. However, statements made by SEC Director William Hinman suggest that Ethereum is sufficiently decentralized such that there is not a single “issuer” of ether that can be held accountable under securities laws:
Is cryptocurrency a security?
Thankfully, it is clear that not every cryptocurrency is a security.
What is an ID token?
They can be sent alongside or instead of an access token. ID tokens are used by the client to authenticate the user. To learn more about how the Microsoft identity platform issues ID tokens, see ID tokens.
How does a token work?
The token is signed by the authorization server with a private key. The authorization server publishes the corresponding public key. To validate a token, the app verifies the signature by using the authorization server public key to validate that the signature was created using the private key.
What is a refresh token?
A refresh token, which is used to refresh the access token when the access token is close to expiring.
Why are tokens issued via implicit mode limited?
Tokens issued via the implicit mode have a length limitation because they're passed back to the browser via the URL, where response_mode is query or fragment. Some browsers have a limit on the size of the URL that can be put in the browser bar and fail when it's too long.
What is JWT authentication?
Since JWTs are used as security tokens, this form of authentication is sometimes called JWT authentication. A claim provides assertions about one entity, such as a client application or resource owner, to another entity, such as a resource server. A claim might also be referred to as a JWT claim or a JSON Web Token claim.
What Is a Security Token?
A Security Token is a portable device that stores all your personal information. This is why they are often called authentication tokens. In order to get access to a software service, you need to connect the Security Token to the system. There are Security Token Services (STS) that can issue you with a Security Token and confirm your identity.
How does a security token work?
If everything is correct, you will be granted access to the system. Security tokens use the same authentication concept as passwords.
What is a disconnected token?
Disconnected tokens. These are the most commonly used type of Security Tokens. Here a two-factor authentication with passwords is used for identification. You do not need to physically plug these tokens into a device. Instead, you must enter a code that generates a token for you.
What is cryptographic key?
Some store cryptographic keys, a system used in cryptographic currency services such as Bitcoin, but the key must be kept secret. Some use time-sensitive passwords that are matched between the token and the network and reset at constant intervals.
Why are security tokens compliant?
He must also be in possession of the token. Security Tokens are also compliant with regulations. One reason for this is that there is a real object behind the token. That is why you can trade with them in almost any country.
What is contactless token?
Contactless tokens. With a contactless token, there is no need to physically connect to a device or enter a code. With this type of token, your authentication data is sent to a specific system via a token. This system then checks whether you have access rights. Bluetooth tokens are a good example of this.
What is the advantage of using security tokens?
If you protect your access data with Security Tokens, you are of course also protecting your assets. Another advantage is the additional verification . With a Security Token you not only have a knowledge factor but also a possession factor. This means that it is no longer enough for a hacker to know your password.
What is a security token?
A security token is a type of cryptocurrency that represents a real-world asset, which you can trade as you would a security. Here’s everything you need to know about this game-changing application of blockchain technology. The following article is not investment advice.
What are tokens in crypto?
What Is a Token? 1 Cryptocurrency coins like Bitcoin (BTC) or Ethereum (ETH) mostly serve as a means of exchange. 2 Tokens typically represent something besides currency.
What is a cryptocurrency token?
A cryptocurrency token is one of two main types of cryptocurrency: coins vs tokens. Cryptocurrency coins like Bitcoin (BTC) or Ethereum (ETH) mostly serve as a means of exchange. Tokens typically represent something besides currency. Additionally, coins often have their own blockchain while tokens do not.
What is security investment?
In other words, a security is an investment that an investor buys from an issuer (or company). For the investor, it represents partial ownership in a company, which can translate to payments, voting on company decisions and the ability to resell for a profit on a stock exchange. For the issuer, it allows them to finance without borrowing money.
Can anyone buy a security?
Not Just Anyone Can Buy a Security. In order to buy a security, you have to go through a stockbroker. Stockbrokers have to have studied finance and received the appropriate licenses. They also charge their clients fees for their services.
Who regulates securities?
Securities Are Regulated by the SEC. Not only do you have to follow a specific protocol to buy securities but securities themselves are subject to federal regulation. The SEC, or U.S. Securities and Exchange Commission, has regulated security sales since the 1930s.
Can blockchain be used as a trustless agreement?
They’re also a way to benefit from blockchain technology ‘s other applications, like smart contracts. Instead of paying for a lawyer to work as the middleman, the investor and issuer can sign a ‘trustless’ agreement.
What Is a Security Token?
A security token is a portable device that authenticates a person's identity electronically by storing some sort of personal information. The owner plugs the security token into a system to grant access to a network service. Security Token Services (STS) issue security tokens that authenticate the person's identity.
Why do security tokens store data?
Also, security tokens store data in order to authenticate the owners' identities. Some store cryptographic keys, a system used in cryptocurrency services such as Bitcoin, but the key must be kept secret. Some use time-sensitive passwords, which are coordinated between the token and the network and are reset at constant intervals. Others use biometrics such as fingerprint data to ensure that only the owner of the security token can access protected information.
What is a single sign on service?
Single sign-on services also use security tokens to log users into third-party websites seamlessly. Disconnected tokens are not linked to the computer or network in any way; rather, the user enters the information from the token manually into the system. Connected tokens work electronically and automatically transmit information to the network once they're connected.
What is time sensitive password?
Some use time-sensitive passwords, which are coordinated between the token and the network and are reset at constant intervals. Others use biometrics such as fingerprint data to ensure that only the owner of the security token can access protected information.
Can security tokens be hacked?
Security tokens can also be hacked. This often happens when the owner unknowingly provides sensitive information to an unauthorized provider who then inputs the information into the secure network. This is known as man-in-the-middle fraud. Any network connected to the Internet is vulnerable to such an attack.
Is a security token always secure?
Security tokens are not always secure—they may be lost, stolen, or hacked.
Can you use a security token to access a service?
As with any system, security tokens are not flawless. If the token is lost or stolen or if it isn't in the owner's possession, it cannot be used to access a service. However, the owner can take steps to prevent loss or theft, such as locks or alarms, and the token can be rendered useless to a thief by using two-factor authentication, which requires both an item in the owner's possession (for example, a bank card) and a piece of knowledge (for example, a PIN) to access the token.
What Is A Security Token?
In simple language, a security token is a blockchain-based “share” of an underlying asset, such as a company, real estate, or gold. A useful analogy is buying a share of Apple stock, making you the owner of a small piece of Apple. A security token is similar to that share of Apple stock — but capable of much more. (Think of it as a smart stock.)
Why do people buy blockchain tokens?
But let’s be honest: most people buy blockchain tokens in the hope that their value will rise over time. That’s a security. Security tokens are a legal concept, not a technical one. A security token is any blockchain asset that meets the SEC’s standards for a securitized asset.
Why is a share of stock a security?
This is why a share of stock is a security, because you put money in and make a profit off the company’s hard work. This is how most investors see blockchain tokens: they are buying into a project that they hope will rise in value, like a share of stock.
Do you have to comply with securities regulations if you trade blockchain?
If you trade any blockchain tokens, you should comply with securities regulations. Those tokens are probably investment products, and your profits and losses from trading security tokens will likely be taxed as investment income and you should approach them as such.
Do tokens have to confer ownership?
The SEC has made it clear that tokens don’t have to confer ownership in anything to meet the Howey Test. All that matters is that investors buy the tokens expecting to then profit off of the performance of the underlying company. Ownership is optional.
Who has always questioned the legitimacy of utility tokens?
The SEC has always questioned the legitimacy of utility tokens.
Is a utility token a coupon?
The trouble with this business model is that it is not entirely useful. A pure utility token, one that isn’t an investment product but which only gives access to the platform, is little more than a coupon. There’s rarely a reason why consumers couldn’t simply purchase access directly.

Validate Security Tokens
Json Web Tokens and Claims
- The Microsoft identity platform implements security tokens as JSON Web Tokens (JWTs) that contain claims. Since JWTs are used as security tokens, this form of authentication is sometimes called JWT authentication. A claim provides assertions about one entity, such as a client application or resource owner, to another entity, such as a resource serv...
How Each Flow Emits Tokens and Codes
- Depending on how your client is built, it can use one (or several) of the authentication flows supported by the Microsoft identity platform. These flows can produce various tokens (ID tokens, refresh tokens, access tokens) and authorization codes. They require different tokens to make them work. This table provides an overview. Tokens issued via the implicit mode have a length li…
Next Steps
- For more information about authentication and authorization in the Microsoft identity platform, see the following articles: 1. To learn about the basic concepts of authentication and authorization, see Authentication vs. authorization. 2. To learn about registering your application for integration, see Application model. 3. To learn about the sign-in flow of web, desktop, and m…