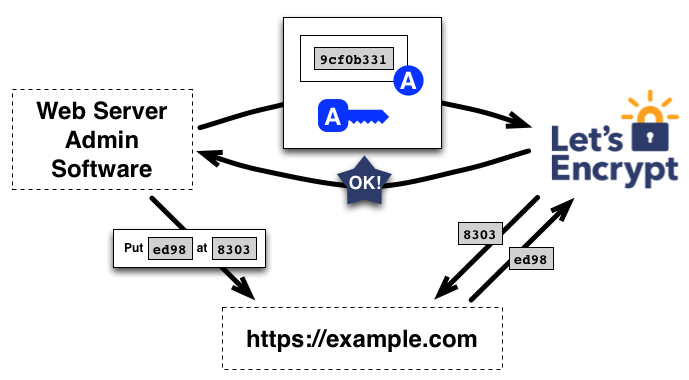
What does the process of Authorisation include? Authorization is a security mechanism used to determine user/client privileges or access levels related to system resources, including computer programs, files, services, data and application features. Authorization is normally preceded by authentication for user identity verification.
How to submit an authorization?
The following information is generally required for all authorizations:
- Member name
- Member ID number
- Provider ID and National Provider Identifier (NPI) number or name of the treating physician
- Facility ID and NPI number or name where services will be rendered (when appropriate)
- Provider and/or facility fax number
- Date (s) of service
- Diagnosis and diagnostic codes
- CPT codes
How to complete an authorization form?
- Find the web sample from the library.
- Complete all necessary information in the required fillable areas. ...
- Make sure everything is completed properly, with no typos or lacking blocks.
- Place your e-signature to the PDF page.
- Click Done to confirm the adjustments.
- Download the papers or print out your copy.
- Submit immediately to the recipient.
What should you use for authorization?
authorization
- Authentication. Authentication is the process of proving that you are who you say you are. ...
- Authorization. Authorization is the act of granting an authenticated party permission to do something. ...
- Next steps. To learn how access tokens, refresh tokens, and ID tokens are used in authorization and authentication, see Security tokens.
How to apply for authorization?
- Your Form I-766 to prove your immigration status and that you can work in the U.S., - or
- Your Form I-551 or Permanent Resident Card (PRC) to prove your immigration status.
- Your birth certificate to prove your age. If you do not have a birth certificate or you cannot obtain it in 10 business days, we may accept your foreign passport, ...
What are types of authorization?
There are four types of Authorization – API keys, Basic Auth, HMAC, and OAuth.
What is authorization in data processing?
Definition: Authorization is a security mechanism to determine access levels or user/client privileges related to system resources including files, services, computer programs, data and application features.
What are the three levels of authorization?
The amount of information about a project that's displayed to a specific user is defined by one of three authorization levels: full, restricted, or hidden.
What is authorization and example?
Authorization is the process of giving someone the ability to access a resource. Of course, this definition may sound obscure, but many situations in real life can help illustrate what authorization means so that you can apply those concepts to computer systems. A good example is house ownership.
What is the general authorization?
General authorization means a rule adopted by the director authorizing, without a permit from the division, a category of activities involving removal or fill, or both, on a statewide or other geographic basis.
What is authorization service?
The authorization service ensures that the user is authorized to have access to a particular resource. Authorization can be done through role-based access control (RBAC) or list-based access control (LBAC).
Which three authorization factors are used to establish identity using electronic means?
Knowledge factor, which is something that the user knows, such as a password, answers to challenge questions, ID numbers or a PIN. Possession factor, which is something that the user has, such as mobile phone, PC or token.
What is Authorisation level?
Ensuring Authorization. Authorization is the rights and permissions granted to a user or application that enables access to a network or computing resource. Once a user has been properly identified and authenticated, authorization levels determine the extent of system rights that the user has access to.
What is authentication and Authorisation?
Simply put, authentication is the process of verifying who someone is, whereas authorization is the process of verifying what specific applications, files, and data a user has access to. The situation is like that of an airline that needs to determine which people can come on board.
How do you implement authorization?
Implementing authorization can be done either in the API gateway or in the microservices. To be able to do extensive application-specific authorization checks, authorization should be handled in the specific microservices. This can be done by passing along the JWT with the request.
What is Authorisation in business?
Authorization is the basis by which the authority to complete the various stages of a transaction is delegated. These stages include the processes of Recording (initiate, submit, process), Approving (pre-approval, post entry review), and Reconciling.
What is authorization characteristics?
Characteristics are authorization information stored for each PUID. Authorization differs from authentication in that authentication is tied to identity (viz., proving you are who you say you are) and authorization is tied to rights (what you can do). Characteristics may be either basic, public, or private.
Handling Authorization in a Computer System
In computer systems, authorization rules are part of an IT discipline called Identity and Access Management (IAM). Within IAM, authorization and authentication help system managers to control who has access to system resources and set client privileges.
Definition of Authorization Using Authorization Strategies
There are several different authorization strategies that computer systems leverage during application deployment. The most prominent ones are Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC). Recently, Auth0 has been investigating and solving for Relationship Based Access Control (ReBAC).
Attribute-Based Access Control (ABAC) and Authorization
When using ABAC, a computer system defines whether a user has sufficient access privileges to execute an action based on a trait (attribute or claim) associated with that user. An example use case of this authorization process is an online store that sells alcoholic beverages.
Role-Based Access Control (RBAC) and Authorization
RBAC, on the other hand, treats authorization as permissions associated with roles and not directly with users. A role is nothing but a collection of permissions. For example, imagine that you work as a department manager in an organization.
Relationship-Based Access Control (ReBAC) and Authorization
Relationship Based Access Control examines the following question in regards to authorization: “Does this user have a sufficient relationship to this object or action such that they can access it?” The relationship can come via a user attribute, such as being a member of a role group related to the object, or having a direct relationship, such as being shared on a document.
What Does Authorization Mean?
Authorization is a security mechanism used to determine user/client privileges or access levels related to system resources, including computer programs, files, services, data and application features. Authorization is normally preceded by authentication for user identity verification.
Techopedia Explains Authorization
Modern and multiuser operating systems depend on effectively designed authorization processes to facilitate application deployment and management. Key factors include user type, number, credentials requiring verification and related actions and roles.