How do I launch a host discovery scan?
To launch the scan immediately, click the button, and then click Launch. Nessus runs the host discovery scan, and the My Scans page appears. In the scans table, click the row of a completed host discovery scan. The scan's results page appears.
What is the host discovery method?
This host discovery method looks for either responses using the same protocol as a probe, or ICMP protocol unreachable messages which signify that the given protocol isn't supported on the destination host. Either type of response signifies that the target host is alive.
What is a discovery scan and how does it work?
A discovery scan identifies the operating systems that are running on a network, maps those systems to IP addresses, and enumerates the open ports and services on those systems. A discovery scan is the internal Metasploit scanner.
Can Nessus scan just discover hosts on network?
A Nessus user recently contacted me about performing a scan that would simply discover hosts on the network. This is a very low impact scan that does not look for vulnerabilities or enumerate ports.

What is the difference between a host discovery scan and a basic network scan?
As far as I understand, Host Discovery does a sweep of a whole subnet to detect hosts. In the case of a Basic Scan, it only detects the IP that have been specified; correct me if I'm wrong. The problem is the following: I obtain different results when I scan the same subnet.
Why is it useful to run host discovery scans?
Knowing what hosts are on your network is the first step to any vulnerability assessment. Launch a host discovery scan to see what hosts are on your network , and associated information such as IP address, FQDN, operating systems, and open ports, if available .
What is a discovery scan?
A discovery scan identifies the operating systems that are running on a network, maps those systems to IP addresses, and enumerates the open ports and services on those systems. A discovery scan is the internal Metasploit scanner.
What is host scan?
A common method to accessing host systems is by identifying and exploiting vulnerabilities in the operating system, installed applications, and other programs. Tools such as Nessus are automated methods to evaluate systems for known vulnerabilities.
What does ping sweep do?
Ping sweep, also known as ICMP sweep or a ping scan, is a network scanning technique you can use to find out which IP addresses map to live hosts. In contrast to a single ping, a ping sweep uses ICMP (Internet Control Message Protocol) ECHO requests to communicate with multiple hosts at the same time.
How do you do a discovery scan?
0:222:43Launch a Host Discovery Scan in Nessus Professional - YouTubeYouTubeStart of suggested clipEnd of suggested clipUnder notifications if my SMTP server is configured I can tell it to email me the results when it'sMoreUnder notifications if my SMTP server is configured I can tell it to email me the results when it's done under discovery the default is just host enumeration.
Which is primarily used for network discovery scanning?
Nmap1. Which one of the following tools is used primarily to perform network discovery scans? A. Nmap is a network discovery scanning tool that reports the open ports on a remote system.
What is a full vulnerability scan?
Full vulnerability scanning is the act of looking for every possible vulnerability on a network or computer system using every tool possible.
What are the types of vulnerability scans?
Five types of vulnerability scannersNetwork-based scanners. Network based vulnerability scanners identify possible network security attacks and vulnerable systems on wired or wireless networks. ... Host-based scanners. ... Wireless scanners. ... Application scanners. ... Database scanners.
What does host up mean?
During a TCP ACK scan, Nmap sends an empty TCP packet with the ACK flag set to port 80. If the host is up, it will answer with an RST packet since the connection doesn't exist. If the host is down, there will be no response. The port can be defined by the user. nmap -sP -PA IP.
What is Cisco host scan?
Cisco AnyConnect Secure Mobile client has a feature called, Host Scan, that has the ability to identify the operating system, anti-virus, anti-spyware, and firewall software installed on the computer its running on.
How do I scan a public IP address?
The most basic way to find all the IP addresses on a network is with a manual network scan....How to Find All IP Addresses on a NetworkOpen the command prompt.Enter the command “ipconfig” for Mac or “ifconfig” on Linux. ... Next, input the command “arp -a”. ... Optional: Input the command “ping -t”.
What is discovery scan?
A discovery scan is the internal Metasploit scanner.
How many ports are there in the Discovery Scan?
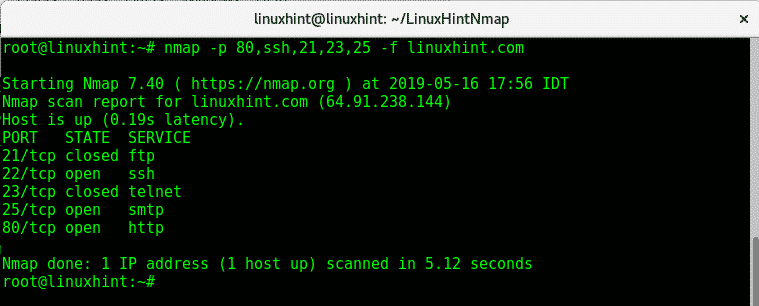
Ports Included in the Discovery Scan. In total, the discovery scan includes over 250 ports, which includes the following set of ports: Standard and well known ports, such as ports 20, 21, 22, 23, 25 53, 80, and 443.
What is a Nmap scan?
Nmap sends probes to various ports and classifies the responses to determine the current state of the port. The scan covers a wide variety of commonly exposed ports, such as HTTP, telnet, SSH, and FTP. The discovery scan uses the default Nmap settings, but you can add custom Nmap options to customize the Nmap scan.
How long does it take to scan a port?
If you want to scan all ports, you can specify 1-65535 as the port range. Keep in mind that a discovery scan that includes all ports can take several hours to complete. If there is a port that you do not want to scan, you can exclude the port from the discovery scan.
Why do we review the host data?
You can review the host data to obtain a better understanding of the topology of the network and to determine the best way to exploit each target. Oftentimes, the network topology provides insight into the types of applications and devices the target has in place.
Where is the scan button in Discovery?
When the New Discovery Scan page appears, enter the target addresses that you want to include in the scan in the Target addresses field. You can enter a single IP address, an address range, or a CIDR notation.
Does Metasploit Pro detect IPv6?
Specifying IPv6 Addresses. Metasploit Pro does not automatically detect IPv6 addresses during a discovery scan. For hosts with IPv6 addresses, you must know the individual IP addresses that are in use by the target devices and specify those addresses to Metasploit Pro.
ICMP Ping Types ( -PE, -PP, and -PM)
In addition to the unusual TCP and UDP host discovery types discussed previously, Nmap can send the standard packets sent by the ubiquitous ping program. Nmap sends an ICMP type 8 (echo request) packet to the target IP addresses, expecting a type 0 (echo reply) in return from available hosts.
ARP Scan ( -PR)
One of the most common Nmap usage scenarios is to scan an ethernet LAN. On most LANs, especially those using private address ranges granted by RFC 1918, the vast majority of IP addresses are unused at any given time.
Default Combination
If none of these host discovery techniques are chosen, Nmap uses a default which is equivalent to the -PE -PS443 -PA80 -PP arguments for Windows or privileged (root) Unix users. Attentive readers know that this means an ICMP echo request, a TCP SYN packet, a TCP ACK packet, and an ICMP timestamp request are sent to each machine.