Full Answer
What is a modern key management system?
Modern key management systems are automated and use the best of physical and electronic safety standards. Key management systems will be specially adapted for each business, but you can expect: A Key Cabinet: A physical space to keep key sets from unauthorized access.
What is KMS (key management service)?
Introduction. KMS (Key Management Service) is an activation service that allows organizations to manage the activation of their Windows systems and Office by eliminating the need for individual computers to connect to Microsoft for product activation.
What is EKMS key management system?
Key management system A key management system (KMS), also known as a cryptographic key management system (CKMS) or enterprise key management system (EKMS), is an integrated approach for generating, distributing and managing cryptographic keys for devices and applications.
What are the benefits of key management systems?
The key management system maintains a transaction log, so you will have a sealed record of who used which keys when. Your employees will take full responsibility for the keys they have. Improved operation. The key management system can more strictly control how keys are used in your facility.

What is key management system?
Definition(s): A system for the management of cryptographic keys and their metadata (e.g., generation, distribution, storage, backup, archive, recovery, use, revocation, and destruction). An automated key management system may be used to oversee, automate, and secure the key management process.
What is key management and why is it important?
Key Management is the process of putting certain standards in place to ensure the security of cryptographic keys in an organization. Key Management deal with the creation, exchange, storage, deletion, and refreshing of keys. They also deal with the members access of the keys.
What are the components of key management?
Definition(s): The software module applications and hardware security modules (HSMs) that are used to generate, establish, distribute, store, account for, suspend, revoke, or destroy cryptographic keys and metadata.
How do you create a key management system?
The documentation of a key management system should: Classify the different types of keys and other cryptographic information according to their functions. Identify the states in which a cryptographic key may exist during the key's life cycle. Formulate a key compromise recovery plan. Define system owners and managers.
Who is responsible for key management?
A business can approach key management in three different ways: Decentralized: End-users or employees are responsible for key management, and the company does not handle governance. Distributed: Each team or department has a separate key management protocol while the business provides basic guidance.
What are the important phases in the key management process?
Key lifecycle: key generation, pre-activation, activation, expiration, post-activation, escrow, and destruction. Physical access to the key server(s) Logical access to the key server(s) User/Role access to the encryption keys.
What is key management life cycle?
This is the minimal set of cryptographic key attributes that must be present for a cryptographic key to be usable by the appropriate cryptographic algorithm in an age-based key lifecycle management system. We list the three core key attributes. Value. This can include both the secret and public parts of the key.
What is enterprise key management?
Enterprise Key Management (EKM) is an Asana feature that allows you to encrypt your data with keys that you own. EKM affords you more control over your data by putting the keys in your hands, with visibility into how the keys are being used, all while you continue to get the most out of Asana.
What is the key management problem?
Several challenges IT organizations face when trying to control and manage their encryption keys are: Scalability: Managing a large number of encryption keys. Security: Vulnerability of keys from outside hackers, malicious insiders. Availability: Ensuring data accessibility for authorized users.
What is private key management?
Key management. A private key is also used in asymmetric cryptography, which is also known as public key cryptography. In this case, the private key refers to the secret key of a public key pair. In public key cryptography, the private key is used for encryption and digital signatures.
What is key management in IP security?
Security associations (SAs) require keying material for authentication and for encryption. The managing of this keying material is called key management. The Internet Key Exchange (IKE) protocol handles key management automatically. You can also manage keys manually with the ipseckey command.
Which of the following is a key management system in Azure?
Key Management - Azure Key Vault can be used as a Key Management solution. Azure Key Vault makes it easy to create and control the encryption keys used to encrypt your data.
What is key management?
Key management concerns keys at the user level, either between users or systems. This is in contrast to key scheduling, which typically refers to the internal handling of keys within the operation of a cipher.
Why is key management important?
Successful key management is critical to the security of a cryptosystem. It is the more challenging side of cryptography in a sense that it involves aspects of social engineering such as system policy, user training, organizational and departmental interactions, and coordination between all of these elements, in contrast to pure mathematical practices that can be automated.
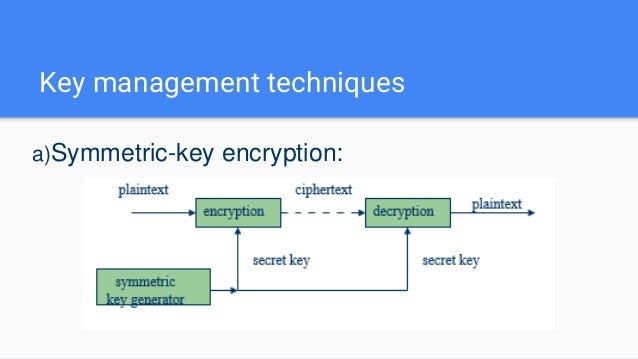
What type of keys are used in cryptography?
Main article: Cryptographic key types. Cryptographic systems may use different types of keys, with some systems using more than one. These may include symmetric keys or asymmetric keys. In a symmetric key algorithm the keys involved are identical for both encrypting and decrypting a message.
How to exchange master key?
Another method of key exchange involves encapsulating one key within another. Typically a master key is generated and exchanged using some secure method. This method is usually cumbersome or expensive (breaking a master key into multiple parts and sending each with a trusted courier for example) and not suitable for use on a larger scale. Once the master key has been securely exchanged, it can then be used to securely exchange subsequent keys with ease. This technique is usually termed key wrap. A common technique uses block ciphers and cryptographic hash functions.
Why do we need to store keys?
However distributed, keys must be stored securely to maintain communications security. Security is a big concern and hence there are various techniques in use to do so. Likely the most common is that an encryption application manages keys for the user and depends on an access password to control use of the key. Likewise, in the case of smartphone keyless access platforms, they keep all identifying door information off mobile phones and servers and encrypt all data, where just like low-tech keys, users give codes only to those they trust.
Why should symmetric keys be changed?
The major issue is length of time a key is to be used, and therefore frequency of replacement. Because it increases any attacker's required effort , keys should be frequently changed. This also limits loss of information, as the number of stored encrypted messages which will become readable when a key is found will decrease as the frequency of key change increases. Historically, symmetric keys have been used for long periods in situations in which key exchange was very difficult or only possible intermittently. Ideally, the symmetric key should change with each message or interaction, so that only that message will become readable if the key is learned ( e.g., stolen, cryptanalyzed, or social engineered).
What is the starting point of a certificate and private key management strategy?
The starting point in any certificate and private key management strategy is to create a comprehensive inventory of all certificates, their locations and responsible parties. This is not a trivial matter because certificates from a variety of sources are deployed in a variety of locations by different individuals and teams - it's simply not possible to rely on a list from a single certificate authority. Certificates that are not renewed and replaced before they expire can cause serious downtime and outages. Some other considerations:
What is key management?
Key management services are designed to help you avoid a key being lost or stolen (which could result in a data breach, downtime, or data loss). Features vary a bit between different solutions, but most key management services include at least these capabilities:
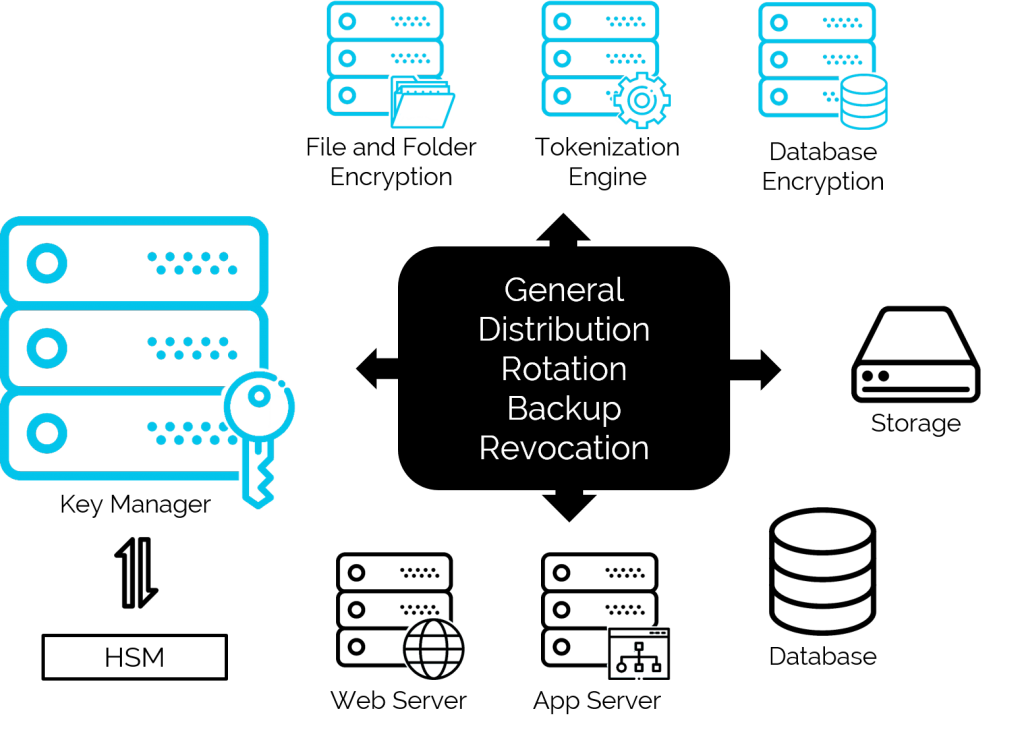
Why do key management systems use HSMs?
However, it’s important to note that many key management services use HSMs on their backends to provide secure storage and backups. They also typically enable you to carry out limited cryptographic operations as well. For example, some key management systems will allow you to use the keys inside the KMS to perform data signing and other related functions.
What is the FIPS level for HSM?
HSM devices typically are offered with one of several Federal Information Processing Standards (FIPS) certified ratings from level 1 to level 4 (with 4 being the highest). The HSMs that many key management systems rely on are typically rated at FIPS 140-2 level 2 or better.
What is a hardware security module?
A hardware security module is typically a physical piece of hardware that handles key storage and cryptographic functions at scale. (There are some cloud HSMs available as well but the term HSM typically refers to the physical devices.) An HSM is a secure environment that allows you to handle key lifecycle management operations and offload many cryptographic operations as well. (This way, you’re not overburdening your servers and other systems.)
What is a KMS?
A KMS is a form of secrets management that helps you manage keys and their meta data. It can deploy on-prem or in the cloud (depending on your chosen platform and vendor). The goal of using one of these systems is to help you keep all of your cryptographic keys as secure as possible. It does this in several ways (depending on which KMS you use):
Why are cryptographic keys useful?
This means preventing unauthorized users from accessing or using them. If someone gets their hands on your private keys (digitally speaking, of course), they can gain access to whatever those keys can touch.
What is PKI in security?
PKI is, basically, the backbone of online security. PKI relies on cryptographic tools known as digital certificates and keys, which allow you to do everything from verifying your identity during logins to protecting your customers’ data in transit as it leaves their browser and transmits to your web server.
What Does Key Management Mean?
When we talk about key management, we’re referring to all the tasks relating to cryptographic keys in an encryption system – creation, usage, storage, exchanging, archiving, deleting, and replacing.
Key Management Challenges
Without a proper management system in place, keys can be lost or compromised, resulting in lost access to critical data. Unfortunately, key management gets harder and harder as the size and complexity of your cryptographic ecosystem increases.
The Benefits of Key Management
Now let’s go into more detail regarding the benefits that key management bring to a business and the reasons for implementing such systems.
Key Management Platforms
If a simple spreadsheet or list of keys sounds like a good idea, think again. Modern key management systems give users the ability to easily and efficiently manage their keys at every point in the lifecycle. There are different types of key management platforms that have different advantages and disadvantages depending on the needs of the end user.
AWS, Microsoft Azure, and Similar
A key manager system can also be dedicated, or “as a service.” This kind of configuration is offered by cloud providers like Amazon Web Services (AWS) or Microsoft Azure, which have marketplace offerings in addition to their own key management as a service (KMaaS) systems.
The Keys to Proper Management
It’s critical that every organization make key security a high priority, no matter what type of key management system they end up going with in the end. Key management systems make life much easier for end users, while maximizing security at the same time.
What is a KMS?
KMS (Key Management Service) is an activation service that allows organizations to manage the activation of their Windows systems and Office by eliminating the need for individual computers to connect to Microsoft for product activation. This service makes activation easier to manage and control for mid-size and large-size companies.
How to enable KMS server?
Starting from Windows Server 2008, all you need to do is to activate the KMS service on the Windows Server using your KMS activation key. It is not required to have a dedicated KMS server as it can be a Windows Server that is running other services.
Does KMS need activation?
At least one KMS server: Starting from Windows Server 2008, it is no longer required to install KMS service. Only the activation is required
Can KMS clients find KMS servers?
KMS clients can use an auto-discovery process to locate KMS servers. In fact, KMS clients do a DNS query for _vlmcs._tcp.domain.com SRV record and will then attempt an activation against the KMS server (s) received in the results.
APAC Compliance
What is Australia Privacy Amendment (Notifiable Data Breaches) Act 2017 Compliance?
Americas Compliance
What is New York State’s Cybersecurity Requirements for Financial Services Companies Compliance?
What is a Centralized Key Management System?
As organizations deploy ever-increasing numbers of encryption solutions, they find themselves managing inconsistent policies, different levels of protection, and experience escalating costs. The best way through this maze is often to transition into a centralized encryption key management system.
Overview
Management and compliance systems
A key management system (KMS), also known as a cryptographic key management system (CKMS) or enterprise key management system (EKMS), is an integrated approach for generating, distributing and managing cryptographic keys for devices and applications. They may cover all aspects of security - from the secure generation of keys over the secure exchange of keys up to secure k…
Types of keys
Cryptographic systems may use different types of keys, with some systems using more than one. These may include symmetric keys or asymmetric keys. In a symmetric key algorithm the keys involved are identical for both encrypting and decrypting a message. Keys must be chosen carefully, and distributed and stored securely. Asymmetric keys, also known as public keys, in contrast are two distinct keys that are mathematically linked. They are typically used together t…
Inventory
The starting point in any certificate and private key management strategy is to create a comprehensive inventory of all certificates, their locations and responsible parties. This is not a trivial matter because certificates from a variety of sources are deployed in a variety of locations by different individuals and teams - it's simply not possible to rely on a list from a single certificate authority. Certificates that are not renewed and replaced before they expire can cause serious d…
Management steps
Once keys are inventoried, key management typically consists of three steps: exchange, storage and use.
Prior to any secured communication, users must set up the details of the cryptography. In some instances this may require exchanging identical keys (in the case of a symmetric key system). In others it may require possessing the other party's public key. While public keys can be openly ex…
Challenges
Several challenges IT organizations face when trying to control and manage their encryption keys are:
1. Scalability: Managing a large number of encryption keys.
2. Security: Vulnerability of keys from outside hackers, malicious insiders.
Compliance
Key management compliance refers to the oversight, assurance, and capability of being able to demonstrate that keys are securely managed. This includes the following individual compliance domains:
• Physical security – the most visible form of compliance, which may include locked doors to secure system equipment and surveillance cameras. These safeguards can prevent unauthorize…
See also
• Dynamic secrets
• Hardware security
• Key ceremony
• Key derivation function
• Key distribution center