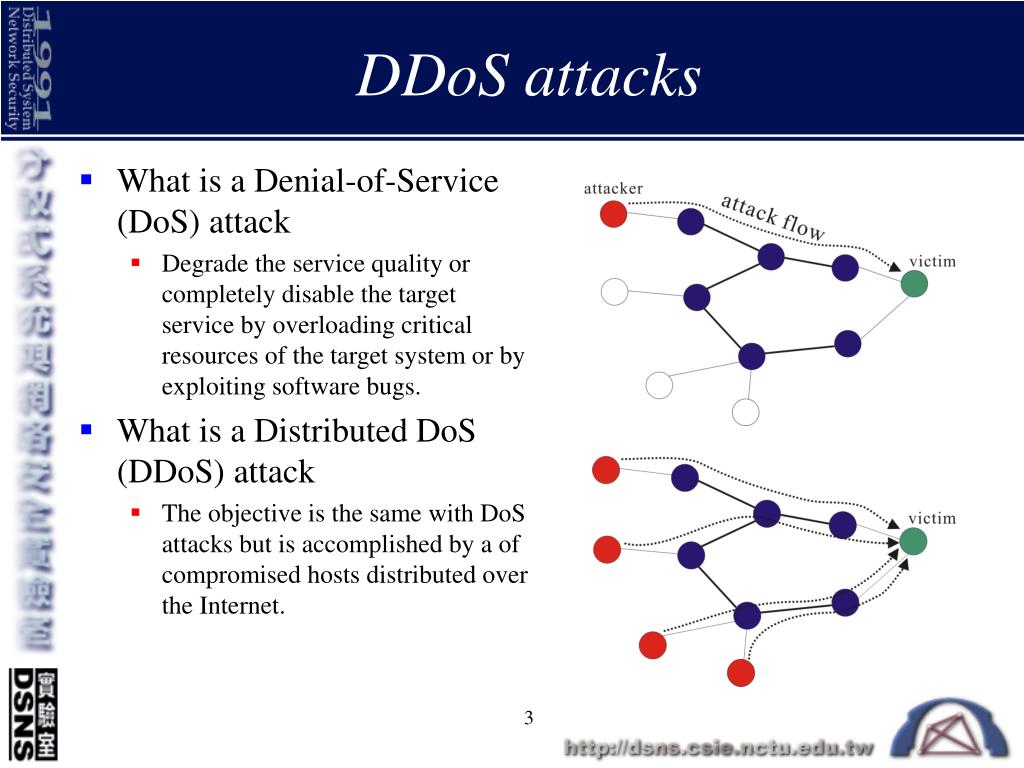
What is a distributed denial of service (DDoS) attack?
A distributed denial-of-service (DDoS) attack is a cybercrime in which the attacker floods a server with internet traffic to prevent users from accessing connected online services and sites. Motivations for carrying out a DDoS vary widely, as do the types of individuals and organizations eager to perpetrate this form of cyberattack.
What is a DNS reflection/amplification DDoS attack?
The Domain Name System (DNS) is a database that stores internet domain names and further translates them into IP addresses. A DNS reflection/amplification distributed denial-of-service (DDoS) attack is a common two-step DDoS attack in which the attacker manipulates open DNS servers.
What is a DDoS botnet attack?
What is a DDoS Botnet? What is a DDoS Attack? What is a DDoS Attack? What is a DDoS Botnet? What is a DDoS attack? A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic.
How do different types of DDoS attacks work?
Different types of DDoS attacks target varying components of a network connection. In order to understand how different DDoS attacks work, it is necessary to know how a network connection is made. A network connection on the Internet is composed of many different components or “layers”.

What is the difference between a normal DoS attack and a reflected DoS attack?
The key difference between DoS and DDoS attacks is that the latter uses multiple internet connections to put the victim's computer network offline whereas the former uses a single connection.
What is a DDoS using a LDAP reflection attack?
DDoS using an LDAP reflection attack is an attack in which there is Third-party include for spoofing the IP address of the user and will send a request to the server as well. Then the server will consider that it is an IP address but it actually is a third party.
What is reflection in cyber security?
In computer security, a reflection attack is a method of attacking a challenge–response authentication system that uses the same protocol in both directions. That is, the same challenge–response protocol is used by each side to authenticate the other side.
What is an amplified DDoS attack?
What is a DNS amplification attack. DNS amplification is a Distributed Denial of Service (DDoS) attack in which the attacker exploits vulnerabilities in domain name system (DNS) servers to turn initially small queries into much larger payloads, which are used to bring down the victim's servers.
What is the largest DDoS attack?
On Thursday, July 21, 2022, Akamai detected and mitigated the largest DDoS attack ever launched against a European customer on the Prolexic platform, with globally distributed attack traffic peaking at 853.7 Gbps and 659.6 Mpps over 14 hours.
How does DDoS attack happen?
In a DDoS attack, cybercriminals take advantage of normal behavior that occurs between network devices and servers, often targeting the networking devices that establish a connection to the internet. Therefore, attackers focus on the edge network devices (e.g., routers, switches), rather than individual servers.
How do reflection attacks work?
A reflection attack involves an attacker spoofing a target's IP address and sending a request for information, primarily using the User Datagram Protocol (UDP) or in some caes, the Transmission Control Protocol (TCP). The server then responds to the request, sending an answer to the target's IP address.
What is TCP Middlebox reflection?
Please note that exploiting TCP Middlebox reflection involves sending custom packets that push payloads in TCP packets that normally do not contain payloads (such as for example a TCP SYN packet), so you cannot verify the susceptibility of a device to attacks by simply running an nmap scan or trying a telnet or netcat ...
What is a logic bomb and how does it work?
A Logic Bomb is a piece of often-malicious code that is intentionally inserted into software. It is activated upon the host network only when certain conditions are met. Logic bombs execute their functions, or launch their payload, once a certain condition is met such as upon the termination of an employee.
What describes a teardrop attack?
A teardrop attack is a type of denial-of-service (DoS) attack (an attack that attempts to make a computer resource unavailable by flooding a network or server with requests and data.)
What is DNS poisoning attack?
Domain Name Server (DNS) spoofing (a.k.a. DNS cache poisoning) is an attack in which altered DNS records are used to redirect online traffic to a fraudulent website that resembles its intended destination.
What is a characteristic of a DNS amplification and reflection attack?
A DNS Amplification Attack is a Distributed Denial of Service (DDOS) tactic that belongs to the class of reflection attacks -- attacks in which an attacker delivers traffic to the victim of their attack by reflecting it off of a third party so that the origin of the attack is concealed from the victim.
How does a reflection attack work?
A reflection attack involves an attacker spoofing a target's IP address and sending a request for information, primarily using the User Datagram Protocol (UDP) or in some caes, the Transmission Control Protocol (TCP). The server then responds to the request, sending an answer to the target's IP address.
What describes a teardrop attack?
A teardrop attack is a type of denial-of-service (DoS) attack (an attack that attempts to make a computer resource unavailable by flooding a network or server with requests and data.)
Can LDAP be exploited?
Using LDAP injection, an attacker can enter the directory to gain access to unauthorized information or modify LDAP statements and content inside the LDAP tree. They can also exploit web applications that create LDAP statements based on user input.
What is a reflection attack quizlet?
Reflection Attack. a direct attack that sends packets to a known service on the intermediary with a spoofed source address of the actual target system. SYN Reflection. sends SYN packets with spoofed source addresses to the target intermediary.
What is a DNS Reflection/Amplification DDoS Attack?
The Domain Name System (DNS) is a database that stores internet domain names and further translates them into IP addresses. A DNS reflection/amplif...
What Are the Signs of a DNS Reflection/Amplification DDoS Attack?
It is extremely common for these types of attacks to occur on open DNS servers. When leveraging a botnet to generate spoofed DNS requests, the targ...
Why Is a DNS Reflection/Amplification DDoS Attack Dangerous?
DNS reflection/amplification DDoS attacks, while common, pose serious threats to organization’s servers. When the massive amounts of traffic are be...
How Can Companies Mitigate and Prevent a DNS Reflection/Amplification DDoS Attack?
Although these attacks are difficult to mitigate, network operators can implement numerous strategies to combat them. To avoid having their own DNS...
How to defend against reflection/amplification attacks?
The primary defense against reflection/amplification attacks is to block the spoofed source packets. Because attacks come from legitimate sources using trusted services such as DNS and NTP, it becomes difficult to tell the difference between genuine user workloads and reflected traffic generated by attackers. Adding to the challenge, when a service comes under attack, legitimate user traffic may be forced to retry responses due to the slowdown in service, possibly causing these retries to be falsely identified as DDoS attacks in their own right.
What type of attack is used to generate higher volume attacks?
One of the more popular DDoS attack types being employed today is the reflection/amplification attack, which enables attackers to generate higher-volume attacks by combining two methods:
What makes reflection/amplification attacks so dangerous?
What makes this type of attack so dangerous is that the servers/devices used for these types of attacks can be ordinary servers or consumer devices with no clear sign of having been compromised, making it difficult to prevent them. Also, launching a reflection/amplification attack doesn’t require sophisticated tools, which means attackers can create enormous volumetric attacks by using a modest source of bots or a single robust server.
Why is port blocking important?
It’s important to note that this doesn’t prevent attacks on ports that are used by both legitimate and attacker traffic.
What Is a DDoS Attack and How Does It Work?
The IT industry has recently seen a steady increase of distributed denial of service (DDoS) attacks. Years ago, DDoS attacks were perceived as minor nuisances perpetrated by novice attackers who did it for fun and it was relatively easy to mitigate them. Unfortunately, that situation is no more. DDoS attacks are now a sophisticated activity, and in many cases, big business.
How effective is a DDoS attack?
The best analogy for a coordinated attack involves comparing a DDoS botnet to a colony of fire ants. When a fire ant colony decides to strike, they first take a position and ready themselves for the attack. Acting under a single directive and without obvious warning, they wait for the signal and then act simultaneously.
What does DDoS stand for?
Many people wonder about the meaning of DDoS, asking what exactly is a DDoS attack and what does DDoS stand for? DDoS stands for distributed denial-of-service attack. DDoS attacks occur when servers and networks are flooded with an excessive amount of traffic. The goal is to overwhelm the website or server with so many requests that the system becomes inoperable and ceases to function.
Why do attackers want to hide DDoS?
Attackers usually want to hide any trace of their involvement in a DDoS attack. To do this, they manipulate the default behavior of internet services so that the services effectively hide the actual attacker. Services often used in these types of attacks include the thousands of Domain Name System (DNS), Network Time Protocol (NTP) and Simple Network Management (SNMP) servers. This is one of the primary reasons that attackers are attracted to a DDoS strategy. Internet services not only provide the traffic, but they also tend to make it more difficult for defenders to trace the origin of the attack because most servers don’t keep detailed logs of the services that have used them.
Why are DDoS attacks so slippery?
DDoS attacks are known to be cunning and therefore tricky to nail down. One of the reasons they are so slippery involves the difficulty in identifying the origin. Threat actors generally engage in three major tactics to pull off a DDoS attack:
How long does a DDoS attack take?
According to a 2018 report from International Data Group (IDG), the median downtime caused by a DDoS attack is 7 to 12 hours.
What are some examples of monoculture attacks?
Other IoT devices create potentially dangerous monoculture conditions which are vulnerable to DDoS attacks. The 2010 Stuxnet incident in Iran is another example of a monoculture attack.
What is a DDoS attack?
DDoS Meaning: What is DDoS? A distributed denial-of-service ( DDoS) attack is a cybercrime in which the attacker floods a server with internet traffic to prevent users from accessing connected online services and sites. Motivations for carrying out a DDoS vary widely, as do the types of individuals and organizations eager to perpetrate this form ...
How does a DDoS attack work?
How DDoS Attacks Work. A DDoS attack aims to overwhelm the devices, services, and network of its intended target with fake internet traffic, rendering them inaccessible to or useless for legitimate users.
What is a DDoS protection solution?
A fully robust DDoS protection solution includes elements that help an organization in both defense and monitoring. As the sophistication and complexity level of attacks continue to evolve, companies need a solution that can assist them with both known and zero-day attacks. A DDoS protection solution should employ a range of tools that can defend against every type of DDoS attack and monitor hundreds of thousands of parameters simultaneously.
What is the primary way DDoS attacks are carried out?
Botnets are the primary way DDoS attacks are carried out. The attacker will hack into computers or other devices and install a malicious piece of code, or malware, called a bot. Together, the infected computers form a network called a botnet.
Why is DDoS important?
As such, the importance of DDoS protection and mitigation is crucial.
Why do people do DDoS?
Motivations for carrying out a DDoS vary widely, as do the types of individuals and organizations eager to perpetrate this form of cyberattack. Some attacks are carried out by disgruntled individuals and hacktivists wanting to take down a company's servers simply to make a statement, have fun by exploiting cyber weakness, or express disapproval.
Why is it so hard to avoid DDoS attacks?
DDoS Prevention. It is extremely difficult to avoid attacks because detection is a challenge. This is because the symptoms of the attack may not vary much from typical service issues, such as slow-loading web pages, and the level of sophistication and complexity of DDoS techniques continues to grow.
What happens when an attacker forges the source address of request packets, pretending to be the victim?
Attackers usually do not have to abuse old versions of protocols or exploit vulnerabilities. Instead, legitimate traffic is used. Reflection occurs when an attacker forges the source address of request packets, pretending to be the victim.
How to abuse NTP?
The abuse of NTP requires that an old feature of the protocol be active. The attacker uses the debug command ‘monlist’ to trigger large amounts of data directed to the victim system. The usage of this command doesn’t require authentication or authorization. A server is supposed to return statistics about NTP clients, such as IP address, NTP version and the number of requests to the NTP server. The response is sent in up to 100 UDP datagrams with a 440 bytes payload each. The amplification factor of ‘monlist’ depends directly on the number of client IPs returned by the server but is always very high. The maximum number of table entries that ‘monlist’ returns is 600 (for Linux implementations of NTP). This means that the maximum amount of data returned for a single query can go up to 50KB. The ‘monlist’ command is not the only one with a significant amplification factor, others can be abused as well to produce attacks.
Can UDP be abused?
These servers suddenly have to deal with abnormally large amounts of spoofed requests that may prevent them from serving legitimate traffic. Many UDP protocols can be abused.
What is a DDoS attack?
A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic.
What is the most obvious symptom of a DDoS attack?
The most obvious symptom of a DDoS attack is a site or service suddenly becoming slow or unavailable. But since a number of causes — such a legitimate spike in traffic — can create similar performance issues, further investigation is usually required.
What is the process for mitigating a DDoS attack?
The key concern in mitigating a DDoS attack is differentiating between attack traffic and normal traffic.
How many Tbps is Cloudflare?
Cloudflare has a 67 Tbps network, which is an order of magnitude greater than the largest DDoS attack recorded. If you are currently under attack, there are steps you can take to get out from under the pressure. If you are on Cloudflare already, you can follow these steps to mitigate your attack.
Why is botnet denial of service difficult?
When a victim’s server or network is targeted by the botnet, each bot sends requests to the target’s IP address, potentially causing the server or network to become overwhelmed, resulting in a denial-of-service to normal traffic. Because each bot is a legitimate Internet device, separating the attack traffic from normal traffic can be difficult.
What is a group of bots called?
These individual devices are referred to as bots (or zombies), and a group of bots is called a botnet. Once a botnet has been established, the attacker is able to direct an attack by sending remote instructions to each bot.
What is exploited machine?
Exploited machines can include computers and other networked resources such as IoT devices. From a high level, a DDoS attack is like an unexpected traffic jam clogging up the highway, preventing regular traffic from arriving at its destination.
