
Full Answer
What are the disadvantages of Splunk?
Disadvantages. Splunk is expensive. For large scale companies where the data takes the highest priority, they would be able to take benefit from the software compared to small scale organizations. The cost of Splunk for GB is $4,500, Which is a lot for a small scale organization to handle on a regular basis.
How to add data in Splunk?
Add data to Splunk There are three ways to add data to Splunk: The easiest way to add data to Splunk is to use the first option (Upload). From the home screen, click on the Add Data icon: Click on the Upload icon: Next, you will need to select the file source. Browse to the file you would like to include:
What is indexer in Splunk?
indexer: A Splunk Enterprise instance that indexes data, transforming raw data into events and placing the results into an index. It also searches the indexed data in response to search requests. Solved! Jump to solution 01-02-2018 01:52 AM index. : The repository for data in Splunk Enterprise.
What is Splunk and how does it work?
What is Splunk and how does it work? Splunk is a software mainly used for searching, monitoring, and examining machine-generated Big Data through a web-style interface. Splunk performs capturing, indexing, and correlating the real-time data in a searchable container from which it can produce graphs, reports, alerts, dashboards, and visualizations.
See more
What is Splunk indexing?
Indexing is a mechanism to speed up the search process by giving numeric addresses to the piece of data being searched. Splunk indexing is similar to the concept of indexing in databases. The installation of Splunk creates three default indexes as follows.
How to create index in Splunk?
The additional data that comes in can use this newly created index but better search functionality. The steps to create an index is Settings → Indexes → New Index. The below screen appears where we mention the name of the index and memory allocation etc.
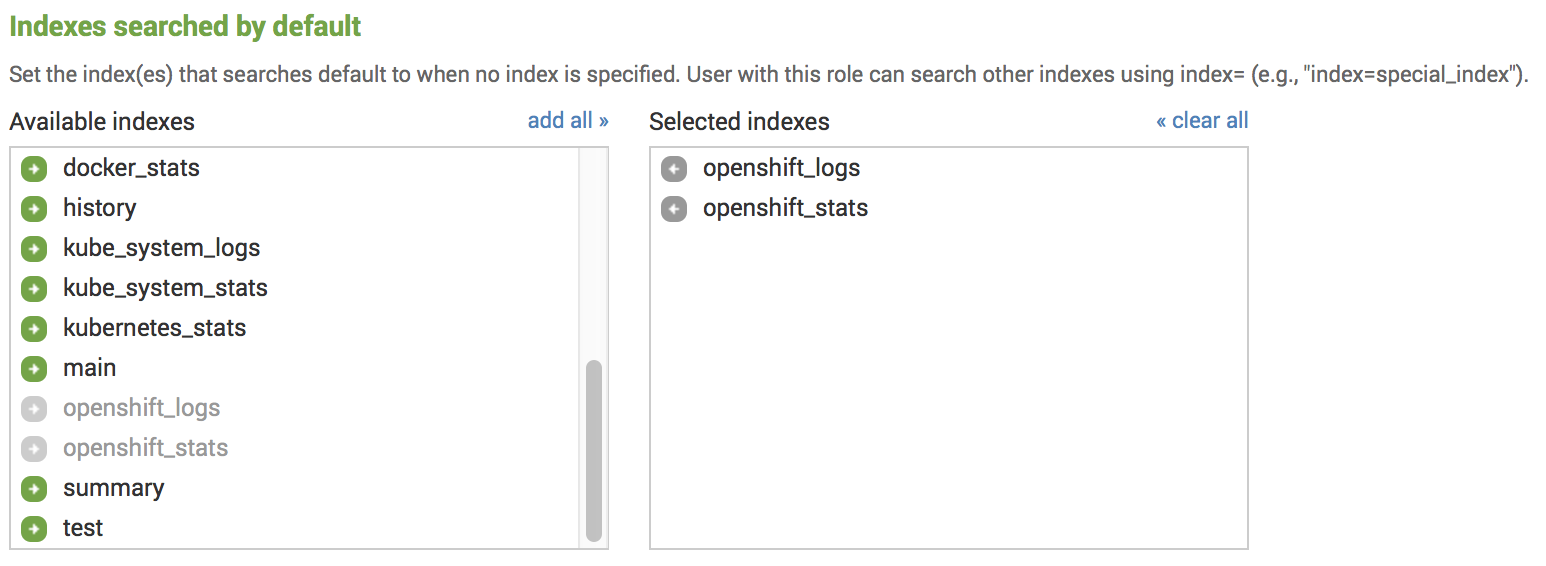
How to look at indexes in Splunk?
We can have a look at the existing indexes by going to Settings → Indexes after logging in to Splunk. The below image shows the option.
What is audit index?
audit − This index contains events related to the file system change monitor, auditing, and all user history.
What is raw data in Splunk?
Data that has not been previously added to Splunk is refer red to as raw data . When the data is added to Splunk, it indexes the data (uses the data to update its indexes), creating event data. Individual units of this data are called events. In addition to events, Splunk also stores information related to Splunk's structure and processing ...
Does Splunk have a database?
Splunk stores the data it indexed and its indexes within flat files (actually, files in a structured directory), meaning that it doesn't require any database ...
Event Processing and The Data Pipeline
What's in An Index?
- Splunk Enterprise stores the data it processes in indexes. An index consists of a collection of subdirectories, called buckets. Buckets consist mainly of two types of files: rawdata files and index files. See How Splunk Enterprise stores indexes.
Immutability of Indexed Data
- Once data has been added to an index, you cannot edit or otherwise change the data. You can delete all data from an index or you can delete, and optionally archive, individual index buckets based on policy, but you cannot selectively delete individual events from storage. See Remove indexes and indexed data.
Default Set of Indexes
- Splunk Enterprise comes with a number of preconfigured indexes, including: 1. main: This is the default Splunk Enterprise index. All processed data is stored here unless otherwise specified. 2. _internal: Stores Splunk Enterprise internal logs and processing metrics. 3. _audit: Contains events related to the file system change monitor, auditing, and all user search history. A Splunk Enterpri…