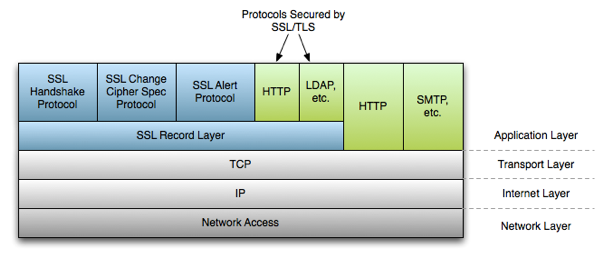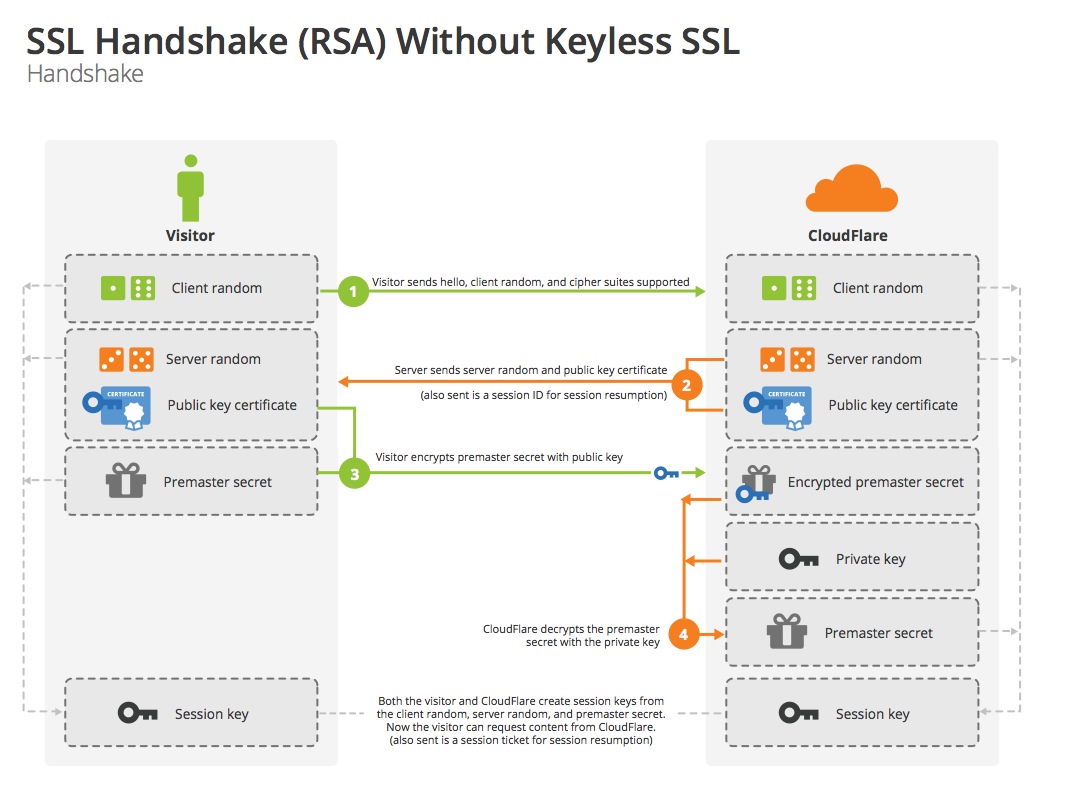
When is RSA key used in TLS handshake?
The following is a standard TLS/SSL Handshake when the RSA key exchange algorithm is used: Client Hello - Information that the server needs to communicate with the client using SSL. This includes the SSL version number, cipher settings, session-specific data. Server Hello - Information that the server needs to communicate with the client using SSL.
What does TLS stand for in client?
Transport Layer Security (TLS) is an encryption protocol that protects Internet communications. TLS replaced SSL in 1999. Read about the TLS protocol and HTTPS. ... One is TLS False Start, which lets the server and client start transmitting data before the TLS handshake is complete. Another technology to speed up TLS is TLS Session Resumption ...
What is the best handshake?
Passive Handshakes
- Limp Fish. Opposite the bone crusher is the limp fish. ...
- Fingers Only. Even worse than the limp handshake is one in which you only offer your fingers to the other person. ...
- Cold, Clammy, or Sweaty. If you are nervous about introductions, you may end up with cold, clammy, or sweaty hands in social situations. ...
- No Eye Contact. ...
How to solve TLS handshake failed error?
Troubleshooting for clients
- Update or change your browser. As a rule, all browsers update TLS protocol, but users often utilize the outdated version of a browser.
- If you use Chrome, then try to turn off the QUICK protocol. In the search line of Google Chrome put in chrome://flags. ...
- Try to deactivate your extensions. ...
- Change WiFi connection. ...
- Clear cache and cookies
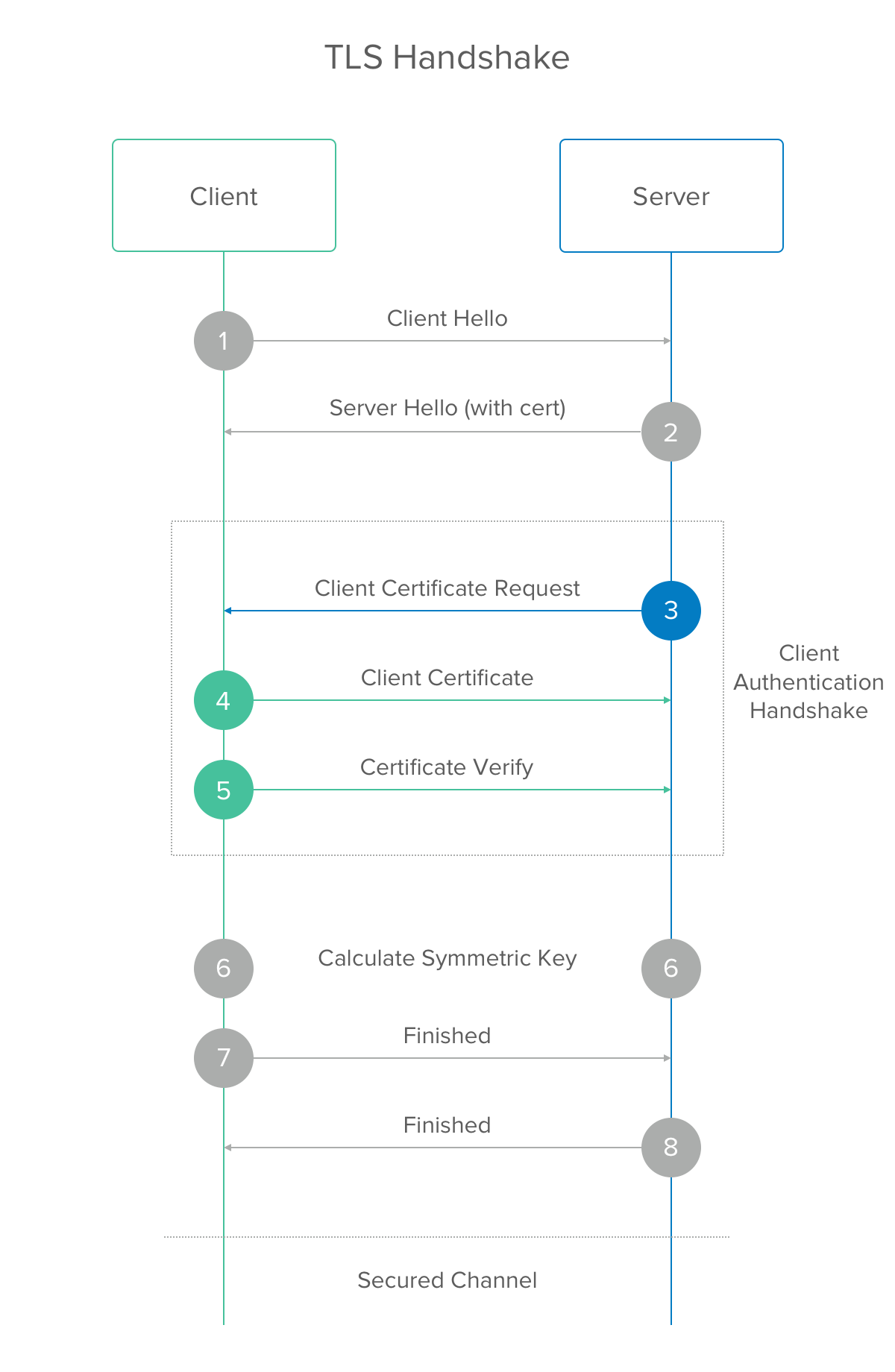
Is TLS handshake safe?
Inside the TLS Handshake. The goal of the TLS handshake is for the client and the server to agree on a shared symmetric encryption key in a secure fashion. To do so, they use asymmetric encryption, which allows encrypted messages to be sent using only a public key.
How do you fix TLS handshake?
The fastest way to fix this SSL/TLS handshake error-causing issue is just to reset your browser to the default settings and disable all your plugins. From there, you can configure the browser however you want, testing your connection with the site in question as you tweak things.
What is TLS and how does it work?
Transport Layer Security (TLS) encrypts data sent over the Internet to ensure that eavesdroppers and hackers are unable to see what you transmit which is particularly useful for private and sensitive information such as passwords, credit card numbers, and personal correspondence.
How many steps are in a TLS handshake?
The TLS 1.2 Handshake: Step by Step. Each TLS handshake involves a series of steps, which accomplish the three main tasks we summarized above: exchanging encryption capabilities, authenticating the SSL certificate, and exchanging/generating a session key.
What causes a TLS handshake failure?
A TLS/SSL handshake failure occurs when a client and server cannot establish communication using the TLS/SSL protocol. When this error occurs in Apigee Edge, the client application receives an HTTP status 503 with the message Service Unavailable.
What causes SSL handshake failure?
The SSL Handshake Error occurs if the read access has not been granted to the OS, thus preventing the web server from completing authentication. It indicates that the browser's connection to the web server isn't secure.
What is difference between SSL and TLS?
Transport Layer Security (TLS) is the successor protocol to SSL. TLS is an improved version of SSL. It works in much the same way as the SSL, using encryption to protect the transfer of data and information. The two terms are often used interchangeably in the industry although SSL is still widely used.
Can TLS be hacked?
A team of researchers has documented a vulnerability in TLS 1.2 (and earlier versions) that could allow a man-in-the-middle attacker to acquire a shared session key and decrypt SSL/TLS traffic.
How do I create a TLS connection?
To set up a TLS connectionNavigate to the System > Network > Config page.Click to add or edit a network forwarder or a network listener.For the Protocol, select TCP-TLS. The following options are displayed:Complete the following options: Option. ... Click Save.
What happens after TLS handshake?
A TLS handshake marks the onset of TLS communication between the client and the server. During a TLS handshake, both the parties exchange messages verify the identity, agree on cipher suite and TLS version to be used in communication, and finally establish the session's keys.
How long does a TLS handshake take?
First, the TLS 1.3 handshake process only requires 1 round trip. Resuming a TLS session is also much faster with TLS 1.3 as this protocol support the “0-RTT round trip” resumption!
How do you handshake between two servers?
SSL handshakeThe client sends a request to the server for a secure session. ... The client receives the server's X. ... The client authenticates the server, using a list of known certificate authorities.The client generates a random symmetric key and encrypts it using server's public key.More items...•
How do I fix unsafe TLS security settings?
Please check your privacy settings and check that TLS is enable for your browser settings, IE and Chrome share the browser settings so we need to check:Open "Internet Options"Go to Advanced Tab and verify the Use TLS check boxs.Select Use SSL 3.0, TLS 1.0/1.1/1.2.Apply changes Ok.Clear the browser cache.More items...•
How do I fix TLS settings?
The fix is easy: In the windows search box, near the Windows Start button, type Internet Options. Open the result “Internet options - control panel”. Then click the Advanced tab. Scroll down in the long list to “security” and make sure “use TLS 1.2” is checked.
How do I fix TLS handshake timeout?
Anyway, to fix:Fully close your k8s emulator. (docker desktop, minikube, etc.)Shutdown WSL2. ( wsl --shutdown ) [EDIT: This step is apparently not necessary -- at least not always, since this time I skipped it, and the problem still resolved.]Restart your k8s emulator.Rerun the commands you wanted.
How do I troubleshoot TLS connection?
Troubleshooting TLS-enabled ConnectionsVerify effective configuration.Verify that the node listens for TLS connections.Verify file permissions.Verify TLS support in Erlang/OTP.Verify certificate/key pairs and test with alternative TLS client or server using OpenSSL command line tools.More items...
Asymmetric vs Symmetric Encryption
The handshake itself uses asymmetric encryption – two separate keys are used, one public and one private. Since asymmetric encryption systems have...
What Is A “Cipher Suite”?
The handshake itself has multiple stages, each managed according to different rules. The details can be found here, but the nut of it is that rathe...
Basic vs Mutually-Authenticated Handshake
Another confusing point is that the basic model we described above lets the client verify the server, and the vast majority of sessions secured by...
Different Sessions Will Have Different Security Parameters
Each new handshake creates a new session, and the settings used in one can differ drastically from another depending on the cipher suite chosen. Th...
What is SSL/TLS handshake?
An SSL/TLS handshake is a negotiation between two parties on a network – such as a browser and web server – to establish the details of their connection. It determines what version of SSL/TLS will be used in the session, which cipher suite will encrypt communication, verifies the server (and sometimes also the client ), ...
What is a “cipher suite”?
The details can be found here, but the nut of it is that rather than a series of separate back and forth negotiations (about what keys to use, how to encrypt the handshake itself, how to authenticate the handshake and so forth) the parties can agree to use a “cipher suite” – a pre-existing selection or kit of agreed-upon components. (Remember that asymmetric encryption is costly time- and resource-wise – using the cipher suite as a shortcut speeds up the handshake itself.) TLS specifications allow for quite a number of cipher suites, and the client and server will almost always have access to one they can both employ.
Do all SSL sites have handshake diagrams?
All SSL/TLS-related sites have their own version of a handshake diagram – here’s ours! (Click to enbiggen.)
Does TLS require a certificate?
Another confusing point is that the basic model we described above lets the client verify the server, and the vast majority of sessions secured by TLS only require this. However, some cipher suites will require the client to also send a certificate and public key for mutual authentication of both parties. This two-way authentication will of course add overhead to the handshake – however, in some cases (for instance, where two banks are negotiating a secure connection for fund transfers) the cipher suite will insist upon it, and the extra security is deemed worth it.
What happens during a TLS handshake?
During the TLS handshake, the servers verify each other and establish encryption, and also exchange keys. If everything is authentic, and as expected, more data exchange will take place. There are four major steps: Specify which version of TLS will be used for communication.
Why does my TLS handshake fail?
It is the top reason why the TLS handshake has failed most of the time. The system time is used to test whether the certificate valid or expired. If there is a mismatch between the time on your computer and the server, it can make certificates look expired. Fix the time by setting it to automatic.
What is TLS encryption?
TLS or Transport Layer Security is an encryption protocol. It is designed such that communication through TLS remains secure and private. In this post, I will explain what TLS handshake is and how to fix the TLS handshake if you face issues.
What is HTTPS handshake?
You should know that HTTPS is an implementation of TLS encryption. What is TLS handshake. A handshake is a form of negotiation between two ends. Just like when we meet people, we shake hands, and then go ahead with anything else. On similar lines, the TLS handshake is a form of acknowledgment between two servers.
How to change TLS in Firefox?
Here is how to change the TLS protocol in Firefox: Open Firefox, type about:config and press Enter. In the search box, type TLS, and locate security.tls.version.min. You can change it to:
How is authentication verified?
Authenticity is verified using public key and the SSL certificate authority’s digital signature. Session keys are generated and exchanged. In layman’s word, they first say hello, then the server offers a certificate that the client needs to verify. Once the verification is complete, a session is generated.
When is TLS used?
Before we go ahead and talk about the TLS handshake, let’s understand when TLS occurs. Every time you access a website or application over HTTPS , TLS is used. When you access emails, messages, and even VOIP, it uses TLS. You should know that HTTPS is an implementation of TLS encryption.
What is SSL handshake?
The SSL or TLS handshake enables the SSL or TLS client and server to establish the secret keys with which they communicate.
What does SSL mean in TLS?
The SSL or TLS client sends the server a finished message, which is encrypted with the secret key, indicating that the client part of the handshake is complete.
What happens when a client sends a certificate request?
If the SSL or TLS server sent a client certificate request, the client sends a random byte string encrypted with the client's private key, together with the client's digital certificate, or a no digital certificate alert. This alert is only a warning, but with some implementations the handshake fails if client authentication is mandatory.
What is a TLS client?
The SSL or TLS client sends a client hello message that lists cryptographic information such as the SSL or TLS version and, in the client's order of preference, the CipherSuites supported by the client. The message also contains a random byte string that is used in subsequent computations. The protocol allows for the client hello to include the data compression methods supported by the client.
Can a TLS server and client exchange encrypted messages?
For the duration of the SSL or TLS session, the server and client can now exchange messages that are symmetrically encrypted with the shared secret key.
What is SSL/TLS Handshake?
SSL/TLS handshake is an arbitration made between the browser and the server for establishing the connection details. Since TLS replaced SSL before some time, all SSL handshakes are now defined as TLS handshakes. Both these parties decide on the below steps:
Why is SSL/TLS Handshake Important?
The main motive of the TLS handshake is to ensure data privacy and data integrity by securing communication between browser and server.
What is a client hello message?
This message comprises the TLS version supported by the server, session identifier number, cipher selected from the preferred list of clients, compression algorithm agreed by both parties (optional), and the random string of bytes created by the server which is later used for generating cryptographic keys.
What does it mean when a client and server confirm that the handshake process is rolling in action?
Both the client and the server confirm that the handshake process is rolling in action as desired, identical keys have been generated, and the final encrypted finished message is sent to each other. This also indicates that the cipher suite is activated.
What is client hello?
The client (browser) will send a “ Client Hello ” message stating that it wishes to commence a secure communication. This message also contains the TLS version (TLS 1.0, 1.2, 1.3, etc.) supported by the client, list of cipher suites supported (key exchange algorithm, bulk encryption algorithm, MAC algorithm, a pseudorandom function written in order), the listing of compression methods (optional) and extensions, and the random string to be used for generating cryptographic session keys.
What happens if a server does not accept cipher choices?
If the server does not accord the cipher choices or the TLS version, it will convey a “Handshake Failure” message and close the connection.
What is one way SSL?
One-Way SSL: Only the client (browser) approves the server identity. Two-Way SSL: Both browsers and servers validate each other’s identity. In the majority of the cases, two-way SSL is used, and both parties need to validate each other’s identity.
What is an SSL handshake?
Pull up a website on your browser, and you may believe the connection happened both instantly and spontaneously . In reality, the two devices need to negotiate how they'll communicate and transfer information. That negotiation happens through an SSL handshake.
When did Netscape use SSL?
Netscape developed the SSL protocol in 1995. Unfortunately, it was riddled with security flaws. In the early 2000s, the industry moved to the TLS protocol for the promise of better security. The handshake process remains the same despite the name change.
What does a server send back?
First response: The server sends back proof of security (via certificates), the server's cipher settings, and session-specific data.
Can hackers change data in transit?
These steps should protect data in transit. But unfortunately, attacks are still possible. The BREACH attack, for example, allows hackers to change data in transport. Hackers can also take over and perform a man-in-the-middle attack. The problem begins with data that attackers steal as it's encrypted.
What is SSL/TLS handshake?
The ‘SSL/TLS handshake’ is the technical name for the process that establishes an HTTPS connection. Most of the hard work involved in the SSL/TLS protocol is done here. It’s a process that has evolved since the original SSL protocol was first created in 1996, with each new iteration becoming faster, with less overhead.
Why is TLS 1.3 handshake?
In TLS 1.3’s handshake, because of the limited selection of key exchange schemes, the client can successfully guess the scheme and send their part of the key share during the opening portion (Client Hello) of the handshake. RSA wasn’t the only key exchange scheme that got tossed out in TLS 1.3.
Why is SSL TLS taxing?
As we just touched on, one of the biggest factors in terms of how taxing an SSL/TLS handshake is on your servers stems from the asymmetric encryption being employed, specifically for authentication and key exchange.
What are the three tasks of TLS?
Each TLS handshake involves a series of steps, which accomplish the three main tasks we summarized above: exchanging encryption capabilities, authenticating the SSL certificate, and exchanging/generating a session key.
How many round trips does TLS 1.2 make?
Optimally, the TLS 1.2 handshake makes two round trips. There are scenarios where additional round trips may be needed, so when we refer to the number of round trips we’re talking about in an optimal scenario. I’ve illustrated it here:
How to understand TLS 1.3?
The best way to understand the improvements TLS 1.3 made to the SSL/TLS handshake is to start by discussing round trips. For the sake of making it easier to understand, we pulled the handshake into ten distinct steps in the explanation above. In reality, a lot of these things are happening side-by-side, simultaneously, so it’s common for them to be grouped together and referred to as round trips.
Why is a MAC used in TLS 1.2?
In the TLS 1.2 handshake the negotiation stages of the handshake were not secured, rather a simple MAC is used to ensure nobody tampered with what was transmitted.
How to do a TLS handshake?
So, have a try. Step 1: Type Control inside the Windows search bar and then click Enter to open Control Panel. Step 2: Once Control Panel opens, switch to the view mode to Category and then choose Network and Internet.
Why is my TLS handshake error?
If you received the “Performing a TLS handshake” error after adding any new add-ons, the added add-ones might be the culprit of the error. In this case, you need to remove them.
How to Fix TLS Handshake Failure in Firefox?
Based on the above reasons for “Performing a TLS handshake”, the following solutions have been developed and you can try them one by one .
Why does my antivirus say TLS handshake?
As we know, the antivirus software scans the sites’ certificates, which slows down the process of requesting files from the server and eventually causes the “Performing a TLS handshake” error . Therefore, to get rid of the error, you can try disabling the HTTPS scanning settings on your installed antivirus software.
What is the last solution to Firefox TLS handshake failure?
The last solution to Firefox TLS handshake failure is to disable IPv6. The detailed steps are:
Why does TLS fail?
Why does “Performing a TLS handshake” show up? There are various reasons and they are: 1 Unsupported protocol: The protocol that your browser is using is not supported by the server. 2 Browser error: There is something wrong with Firefox. 3 Antivirus/Addons interference: The installed antivirus software and addons are interfering with the connection. 4 IPv6 and DNS issues: The TLS handshake failure is also associated with IPv6 and DNS issues.
How to disable HTTPS scanning?
Here is the tutorial on how to disable the HTTPS Scanning setting on Avast. Step 1: Launch Avast on your computer. Step 2: Go to the path: Home > Settings > Components > Web Shield > Enable HTTPS Scanning and uncheck Enable HTTPS Scanning.
What is TLS protocol?
TLS is a security protocol that provides privacy and data integrity for Internet communications. Implementing TLS is a standard practice for building secure web apps.
What does TLS do?
There are three main components to what the TLS protocol accomplishes: Encryption, Authentication, and Integrity.
What is Transport Layer Security (TLS)?
Transport Layer Security, or TLS, is a widely adopted security protocol designed to facilitate privacy and data security for communications over the Internet. A primary use case of TLS is encrypting the communication between web applications and servers, such as web browsers loading a website. TLS can also be used to encrypt other communications such as email, messaging, and voice over IP (VoIP). In this article we will focus on the role of TLS in web application security.
What is the difference between TLS and SSL?
TLS evolved from a previous encryption protocol called Secure Sockets Layer ( SSL ), which was developed by Netscape. TLS version 1.0 actually began development as SSL version 3.1, but the name of the protocol was changed before publication in order to indicate that it was no longer associated with Netscape. Because of this history, the terms TLS and SSL are sometimes used interchangeably.
Why should businesses and web applications use the TLS protocol?
TLS encryption can help protect web applications from data breaches and other attacks. Additionally, TLS-protected HTTPS is quickly becoming a standard practice for websites. For example, the Google Chrome browser is cracking down on non-HTTPS sites, and everyday Internet users are starting to become more wary of websites that do not feature the HTTPS padlock icon.
How does TLS work?
For a website or application to use TLS, it must have a TLS certificate installed on its origin server (the certificate is also known as an " SSL certificate " because of the naming confusion described above). A TLS certificate is issued by a certificate authority to the person or business that owns a domain. The certificate contains important information about who owns the domain, along with the server's public key, both of which are important for validating the server's identity.
How does TLS affect web application performance?
The latest versions of TLS hardly impact web application performance at all.