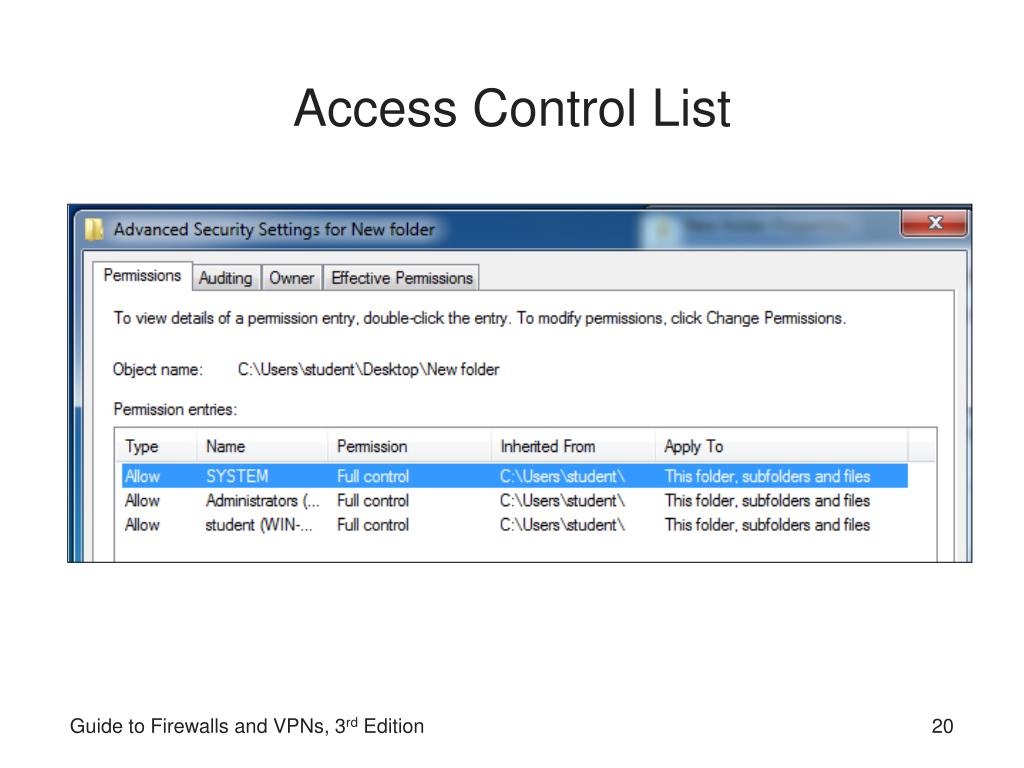
What are two uses of an access control list?
- Complete visibility of the network endpoints connecting to the network
- Give secured network access to BYOD users
- Integration with MDM (Mobile Device Management) Solution for controlled access to mobile devices in a network
- Comprehensive Guest Management with customized captive portal and OTP based authentication
How to implement a basic access control list?
- One user (PC0) from development section should not be able to access anything except its own section.
- One user (PC2) from production section should also be able to access management section but not server section.
- One user (PC3) from production section should be able to access server section but not management section.
How to create an access control list (ACL)?
What Are The Components of An ACL?
- Sequence Number: Identify an ACL entry using a number.
- ACL Name: Define an ACL entry using a name. ...
- Remark: Some Routers allow you to add comments into an ACL, which can help you to add detailed descriptions.
- Statement: Deny or permit a specific source based on address and wildcard mask. ...
What are the different types of access control?
- the sensitivity label applied to data (secret, top secret, etc.),
- by the level of sensitive information the individual is allowed to access (perhaps only secret), and
- by whether the individual actually has a need to access the resource which is the principle of least privilege.

What does an access control list do?
An access control list (ACL) is a list of rules that specifies which users or systems are granted or denied access to a particular object or system resource. Access control lists are also installed in routers or switches, where they act as filters, managing which traffic can access the network.
What is an ACL in networking?
A network access control list (ACL) is made up of rules that either allow access to a computer environment or deny it.
What is ACL and Nat?
acl- access control list. nat- network address translation.
What are the main access control lists?
There are four types of ACLs that you can use for different purposes, these are standard, extended, dynamic, reflexive, and time-based ACLs....What Are The Types of ACLs?Standard ACL. The standard ACL aims to protect a network using only the source address. ... Extended ACL. ... Dynamic ACL. ... Reflexive ACL.
What is difference between ACL and firewall?
An access control list is an implementation of a type of logic that can selectively permit or deny certain packets to go through an interface. A firewall is a device which examines traffic passing through a part of the network and makes decisions about what to let through and what to block.
What is access list and types?
An access control list (ACL) contains rules that grant or deny access to certain digital environments. There are two types of ACLs: Filesystem ACLs━filter access to files and/or directories. Filesystem ACLs tell operating systems which users can access the system, and what privileges the users are allowed.
What is CCNA access list?
An access list is simply a list of conditions or statements that categorize and match packets in a number of interesting ways. Access lists are primarily used as simple filters to permit or deny packets through interfaces in order to exercise control on traffic flowing through the network.
What is QoS protocol?
Quality of service (QoS) is the use of mechanisms or technologies that work on a network to control traffic and ensure the performance of critical applications with limited network capacity. It enables organizations to adjust their overall network traffic by prioritizing specific high-performance applications.
What is Access Control List in router?
The quick definition: An access control list (ACL) is an ordered list of rules used to filter traffic. Each rule states what's permitted or what's denied. When a packet attempts to enter or leave a router, it's tested against each rule in the list — from first to last.
How do you set up an ACL?
To Configure ACLsCreate a MAC ACL by specifying a name.Create an IP ACL by specifying a number.Add new rules to the ACL.Configure the match criteria for the rules.Apply the ACL to one or more interfaces.
What is named ACL?
Named Access Control Lists (ACLs) allows standard and extended ACLs to be given names instead of numbers. Unlike in numbered Access Control Lists (ACLs), we can edit Named Access Control Lists. To create a Named Access Control List (ACL), we can use the following IOS command from Global Configuration mode.
What is a standard ACL?
Standard access control lists (ACLs) allow you to evaluate only the source IP address of a packet. Standard ACLs are not as powerful as extended access lists and can't distinguish between the types of IP traffic, but they are less CPU intensive for the device.
What is an access control list?
An access-list that is developed solely using the source IP address. These access control lists allow or block the entire protocol suite. They don’t differentiate between IP traffic such as UDP, TCP, and HTTPS. They use numbers 1-99 or 1300-1999 so the router can recognize the address as the source IP address.
What is Imperva access control?
Imperva allows for control of user privileges using flexible role-based access controls. Users are provided with view-only, edit, or restricted access to management functions and objects. Organizations can also hierarchically group and manage IT assets into categories for fine-grained access control, even in Managed Security Service Provider (MSSP) deployments and large-scale enterprise.
What are the two types of ACLs?
There are two types of ACLs: Filesystem ACLs ━filter access to files and/or directories. Filesystem ACLs tell operating systems which users can access the system, and what privileges the users are allowed. Networking ACLs ━filter access to the network. Networking ACLs tell routers and switches which type of traffic can access the network, ...
Why is RBAC important?
Thus, RBAC guarantees regulatory persons that only specific users have access to sensitive information, as it gives all approvals based on roles. RBAC is generally considered to be a preferred method for business applications. RBAC is more effective than ACL in relation to administrative overheads and security.
Why do organizations use ACLs?
One reason organizations adopt ACLs is that they have a lower computational overhead than stateful firewalls and that they work at high speeds. This is essential when you try to implement security for fast network interfaces. However, the longer a packet remains in the system, while it is examined against the rules in the ACL, the slower the performance.
What is file system ACL?
A filesystem ACL is a table that informs a computer operating system of the access privileges a user has to a system object, including a single file or a file directory. Each object has a security property that connects it to its access control list. The list has an entry for every user with access rights to the system.
What is an extended ACL?
Extended ACL. An access-list that is widely used as it can differentiate IP traffic. It uses both source and destination IP addresses and port numbers to make sense of IP traffic. You can also specify which IP traffic should be allowed or denied. They use the numbers 100-199 and 2000-2699.
What is an access control list (ACL)?
An access control list (ACL) is a list of rules that specifies which users or systems are granted or denied access to a particular object or system resource. Access control lists are also installed in routers or switches, where they act as filters, managing which traffic can access the network.
What are access control lists used for?
Access control lists are used for controlling permissions to a computer system or computer network. They are used to filter traffic in and out of a specific device. Those devices can be network devices that act as network gateways or endpoint devices that users access directly.
How do ACLs work?
Each ACL has one or more access control entries (ACEs) consisting of the name of a user or group of users. The user can also be a role name, such as programmer or tester. For each of these users, groups or roles, the access privileges are stated in a string of bits called an access mask.
Where can you place an access control list?
Access control lists can be placed on virtually any security or routing device, and having multiple ACLs in different parts of the network can be beneficial.
Components of an access control list
ACL entries consist of several different components that specify how the ACL treats different traffic types. Some examples of common ACL components include the following:
How to implement an ACL
To implement an ACL, network administrators must understand the types of traffic that flow in and out of the network, as well as the types of resources they are trying to protect. Administrators should hierarchically organize and manage IT assets in separate categories and administer different privileges to users.
What are the different types of ACLs?
There are four types of ACLs that play different roles in a network including, Standard, Reflexive, Extended, and Dynamic:
What is ACLS in networking?
In the case of Networking ACLS, they are installed in networking devices (Routers and switches) with the sole purpose of filtering traffic. This is done by using pre-defined rules that decided which packets transferred. Source and destination IP addresses also play a major role in this decision.
What is an ACL?
Access Control List (ACL) refers to a specific set of rules used for filtering network traffic , especially in computer security settings. ACLs also allow specific system objects such as directories or file access to authorized users and denies access to unauthorized users.
Where are ACLs found?
ACLs are mainly found in network devices with packet filtering capabilities including routers and switches.
How many types of access control lists are there?
There are five different types of access control lists.
What is discretionary access control?
Discretionary access control: Discretionary access control can be used in social networking, as there’s a frequent need to change the visibility of the content. This model offers flexibility and allows you to decide who can access your data. It also allows you to customize access policies according to each user.
What is dynamic ACL?
Dynamic ACL: Dynamic ACLs are often known as Lock and Key, and they can be used for specific attributes and timeframes. They rely on extended ACLs, authentication, and Telnet for their functionality.
What is time based ACL?
Time-based ACL: Time-based ACLs are similar to extended ACLs. However, they can be implemented by creating specific times of the day and week.
Why use ACL?
One of the major reasons to use access control lists is to restrict unauthorized users from accessing business-sensitive information. It can also be used to control network traffic by limiting the number of users accessing files, systems, and information. This increases network performance and helps protect business information.
What is role based access control?
Role-based access control: Role-based access control allows you to assign specific roles to employees according to their function within an organization. Moreover, these roles are aligned with access permissions rights. This type of control can be used when you need to share data with a particular department.
What is extended ACL?
Extended ACL: Although extended lists are complex in configurations and resource-intensive, they provide a granular level of control. Using these lists, you can be more precise while filtering data packets. You can also evaluate the packets based on different factors such as source and destination IP addresses, source, and destination port, and type of protocol (ICMP, TCP, IP, UDP), and more.
What is an access control list?
An access control list on a router consists of a table that stipulates which kinds of traffic are allowed to access the system. The router is placed between the incoming traffic and the rest of the network or a specific segment of the network, such as the demilitarized zone (DMZ). The ACL examines the information held within data packets flowing into or out of the network to determine where it came from and where it is going. The ACL on the router then decides whether the data packet should be allowed to pass to the other side.
How to implement ACL?
To properly implement ACL on your router, you have to understand how traffic flows in and out of it. You set the rules based on the point of view of the interface of the router. This is different than that of the networks. For example, if traffic is flowing into a router, it is flowing out of a network, so the perspective makes a big difference as to how the traffic’s motion is described.
How does ACL work?
Networking ACLs are different in that they are installed in switches and routers. Here, they are traffic filters. To filter traffic, a network ACL uses rules that have been predefined by an administrator or the manufacturer. These rules check the contents of packets against tables that govern access parameters. Based on whether the user checks out, their access is either granted or denied.
What are the different types of ACLs?
There are two basic kinds of ACLs: 1 Filesystem ACLs: These work as filters, managing access to directories or files. A filesystem ACL gives the operating system instructions as to the users that are allowed to access the system, as well as the privileges they are entitled to once they are inside. 2 Networking ACLs: Networking ACLs manage access to a network. To do this, they provide instructions to switches and routers as to the kinds of traffic that are allowed to interface with the network. They also dictate what each user or device can do once they are inside.
What is an ACL file?
Filesystem ACLs: These work as filters, managing access to directories or files. A filesystem ACL gives the operating system instructions as to the users that are allowed to access the system, as well as the privileges they are entitled to once they are inside.
What is network ACL?
A network ACL is used to ensure that only approved traffic is allowed to enter a network. It performs a similar function as a filesystem ACL in that the credentials of devices are checked against an approved list. However, a network ACL is different in that it protects a network, as opposed to directories or files inside a network.
What is an ACL?
An access control list (ACL) is made up of rules that either allow access to a computer environment or deny it. In a way, an access control list is like a guest list at an exclusive club. Only those on the list are allowed in the doors. This enables administrators to ensure that, unless the proper credentials are presented by the device, ...
Access Control List Examples
Different ACLs are used for different purposes. Let’s take a look at a few of the access control list types that Cisco defines for IOS:
Tips for implementing access control lists
Name your access control list using all capital letters. Device configurations can be long and crowded with information. One way to make a custom ACL stand out is by naming it in all capital letters. This is a policy I follow for any custom item I create at the command line interface (CLI).
What are some examples of ACLs in action?
Ethan Banks is a network architect, independent IT writer, frequent conference speaker and co-host of the Packet Pushers Podcast.
What is a standard access list?
The standard access list allows for only specifying a source address and wildcard mask. The wildcard mask is used for filtering purposes. The number range is from 1-99 and 1300-1999. It is comprised of permit or deny statement/s from a source address with a wildcard mask only. The single deny statement requires that you add permit any as a last statement for any standard ACL or all packet are denied from all sources.
How many ACLs are there on Cisco?
There are a variety of ACL types that are deployed based on requirements. Only two ACLs are permitted on a Cisco interface per protocol. That would include for instance a single IP ACL applied inbound and single IP ACL applied outbound. Cisco best practices for creating and applying ACLs.
What wildcard is used for 200.200.1.0?
The following wildcard 0.0.0.255 will only match on 200.200.1.0 subnet and not match on everything else. This could be used with an ACL for example to permit or deny a public host address or subnet.
How many ACLs can be applied to a Cisco network?
Maximum of two ACLs can be applied to a Cisco network interface. Only one ACL can be applied inbound or outbound per interface per Layer 3 protocol. There are some recommended best practices when creating and applying access control lists (ACL).
What is more specific ACL?
The more specific ACL statement is characterized by source and destination address with shorter wildcard masks (more zeros). That configures specific subnets to match. In addition, application protocols or port numbers are also specified. The first ACL statement is more specific than the second ACL statement.
What is standard ACL?
There is a common number or name that assigns multiple statements to the same ACL. Standard ACLs are an older type and very general. As a result they can inadvertently filter traffic incorrectly.
What ACL does the network administrator need?
The network administrator must configure an ACL that permits traffic from host range 172.16.1.32/24 to 172.16.1.39/24 only. What is the ACL and wildcard mask that would accomplish this?
What are the two types of access control?
There are two types of access control: physical and logical. Physical access control limits access to campuses, buildings, rooms and physical IT assets. Logical access control limits connections to computer networks, system files and data.
What is the solution to the problem of access control lists?
One solution to this problem is strict monitoring and reporting on who has access to protected resources so that, when a change occurs, it can be immediately identified and access control lists ( ACLs) and permissions can be updated to reflect the change.
How does LDAP work?
These security controls work by identifying an individual or entity, verifying that the person or application is who or what it claims to be, and authorizing the access level and set of actions associated with the username or Internet Protocol (IP) address. Directory services and protocols, including Lightweight Directory Access Protocol (LDAP) and Security Assertion Markup Language ( SAML ), provide access controls for authenticating and authorizing users and entities and enabling them to connect to computer resources, such as distributed applications and web servers.
What is access control?
Access control is a process that is integrated into an organization's IT environment. It can involve identity management and access management systems. These systems provide access control software, a user database, and management tools for access control policies, auditing and enforcement.
How do organizations secure facilities?
To secure a facility, organizations use electronic access control systems that rely on user credentials, access card readers, auditing and reports to track employee access to restricted business locations and proprietary areas, such as data centers. Some of these systems incorporate access control panels to restrict entry to rooms and buildings, as well as alarms and lockdown capabilities, to prevent unauthorized access or operations.
Why are access control strategies static?
Traditional access control strategies are more static because most of a company's computing assets were held on premises. Modern IT environments consist of many cloud-based and hybrid implementations, which spreads assets out over physical locations and over a variety of unique devices. A singular security fence that protects on-premises assets is becoming less useful because assets are becoming more distributed.
What is an example of software that includes most of the tools listed above in a single offering?
Microsoft Active Directory (AD) is one example of software that includes most of the tools listed above in a single offering. Other vendors with popular products for identity and access management (IAM) include IBM, Idaptive and Okta.