Application Override is where the Palo Alto Networks firewall is configured to override the normal Application Identification (App-ID) of specific traffic passing through the firewall.
What does application override do?
How to create an application override policy?
Why do we need to override the application identification process?
About this website

What is override in firewall?
Block rules override Allow rules, so if you have another rule configured that includes blocking the type of traffic you have specified in the Allow rule, then the Allow won't have any effect. Another possibility is your firewall is in Block all connections, which would override any rules.
What is application dependency Palo Alto?
Application dependency warnings are messages from the Palo Alto Networks device that can appear post commit. These warnings advise the administrator there is an application configured on a policy that may not function fully because another application (or applications) is needed.
What is PBF in Palo Alto?
Policy based forwarding allows you to bypass the routing table in favor of routing options dictated by a policy configurable based on applications, source or destination. In short, this means you can choose to have certain applications use a different link without needing to tweak the routing table.
What is ACC in Paloalto?
Using Application Command Center (ACC) from Panorama provides you with a highly interactive, graphical view of application, URL, threat and data (files and patterns) traversing your Palo Alto Networks® firewalls.
What are applications dependencies?
What are Application Dependencies? Application Dependencies occur when technology components, applications, and servers rely on one another to provide a business solution or service. When developers build solutions, they do so with a certain technology stack in mind.
What is application dependency mapping?
Application dependency mapping is pretty much what the name says it is: a process of identifying all the elements in an ecosystem and understanding how they work together. It's connecting a lot of dots to give IT managers a clear picture of their environmental health and overall application performance.
What is FQDN in Paloalto?
The FQDN object is an address object, which means it's as good as referencing a Source Address or Destination Address in a security policy. Therefore, every 30 minutes, the Palo Alto Networks Firewall will do an FQDN Refresh, in which it does an NS lookup to the DNS server that's configured (Setup > Services).
What is DPDK in Palo Alto?
Palo Alto VM-Series firewall supports the PacketMMAP and Data Plane Development Kit (DPDK) drivers to communicate with the drivers on the host. On OCI, the networking launch type consists of: PARAVIRTUALIZED Networking for general purpose workloads and Hardware-Assisted SR-IOV Networking for low-latency workloads.
What is DNS proxy Paloalto?
The Palo Alto Networks security platform can act as a DNS proxy and send the DNS queries on behalf of the clients. DNS queries that arrive on an interface IP address can be directed to different DNS servers based on full or partial domain names.
What are the 3 pillars of Palo Alto Networks strategy?
.Visibility and access control.Data loss protection.Threat prevention.
What is Panorama in Paloalto?
Panorama provides an interactive, graphical view of applications, URLs, threats, data files and patterns traversing your Palo Alto Networks firewalls. Now you can easily visualize network activity, threat activity, and blocked activity and create customized views of current and historical data.
How do you reduce the ACC risk factor in Palo Alto?
Are there any cookie cutter steps that can be taken to lower a Palo Alto's ACC Risk Factor?...The risk factor is based on:Evasive.Excessive Bandwidth.Prone to Misuse.SaaS.Transfers Files.Tunnels Other Apps.Used by Malware.Vulnerabilities.More items...•
What is a dependency in spring boot?
Dependency is nothing but a 'Library' that provides specific functionality that we can use in our application. In Spring-Boot, Dependency Management and Auto-Configuration work simultaneously.
What is dependency in automation?
The automation that's added ensures that the date or timeline of the dependent item never starts before the item which it is dependent on. This dependency automation can come into play whenever an item is delayed.
What is application persistence?
More specifically, application persistence refers to the ability of a software-based application to continue functioning across disruptions in the networks or processes that are fundamental to its operation.
What is third party dependencies?
Third-Party Dependency means any Open-Source Software product used or required by the Software.
How to configure Application Override on Palo Alto device
1. Overview In this article techbast will guide you to configure the Application Override policy on the Palo Alto firewall device. 2. What is Application Override and its uses? Application Override…
How do you disable Layer 7 inspection? - LIVEcommunity
If I wanted no layer 7 inspection for a particular IP at a certain port - how can I do that without Application override? Thank you. - 200956
Create an Application Filter - Palo Alto Networks
Use Case: Configure Active/Active HA for ARP Load-Sharing with Destination NAT in Layer 3
What does application override do?
Application Override to a custom application will force the firewall to bypass Content and Threat inspection for the traffic that is matching the override rule. The exception to this is when you override to a pre-defined application that supports threat inspection .
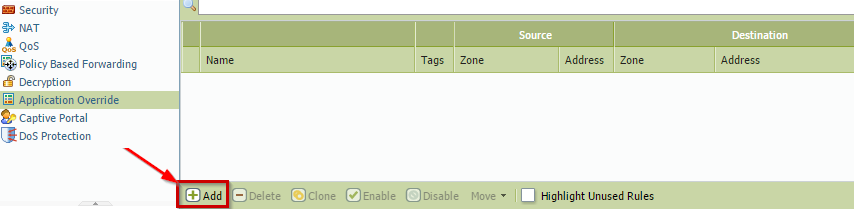
How to create an application override policy?
To create an Application Override policy, go to Policies > Application Override, then click Add:
Why do we need to override the application identification process?
For these applications, we may not have signatures to properly identify the expected behavior and identify the traffic with a known application. In such cases, we recommended creating an application override to allow easier identification and reporting, and to prevent confusion.
What is application override?
Application override forcibly bypasses the AppID process and sets a session to match a manually configured Application name. Any sessions processed like this will not be scanned by parallel processing and will be offloaded to fastpath.
What does a backward slash in front of a dot mean?
This means there needs to be a backward slash in front of the dot to signify the dot is a character and not a wildcard. I'll also set the Qualifier to http-method GET to indicate the signature can be found in the GET request.
What is a signature based app?
A signature-based custom app relies on the App-ID engine to positively identify a signature in the packets passing through the firewall. If you are trying to identify a proprietary application that uses predictable or easily identifiable signatures, you can create a custom application using regex to help identify the signature.
Can a custom app be scanned for threats?
If the custom app does not have a parent app that can be identified by regular App-ID or is used in an app override (see below), it cannot be scanned for threats. In the signatures tab, you can add all the signatures required to identify the application.
Can an app override bypass scanning?
For most use cases, we recommend creating a simple custom application with as few attributes as possible, as the app override will bypass scanning or signature detection. It will simply identify a session as the custom application and take no further action. This can be a very simple but powerful tool to help identify internal applications and improve throughput as the session is offloaded to hardware immediately, but please consider the security implications.
How to add an application to Palo Alto?
Open the Palo Alto web GUI interface. Click “Objects” then “Applications” to open the known applications database. Scroll down to the bottom of the page and click “Add” to create a new application.
How many packets does Palo Alto firewall see?
As a general rule, if the Palo Alto firewall has seen more than 10 packets in a flow, and the application is still not recognized (i.e. incomplete, unknown, undecided), there is a strong possibility it will benefit from an app-override policy. Applications that can also benefit are custom-written applications that are not in ...
What is application override?
Application Override is a feature that allows administrators to create an exception for any application, when this application is in the Application Override policy, it will not be subject to any control from other policies on the wall. Palo Alto fire.
How to add an application to Palo Alto?
Note if the application you want to add is a self-developed company application that is not in Palo Alto’s database, you can customize that application by going to Object > Application > clicking Add and entering the parameters of the application. application you want to add.
What port is Facebook override?
In this article, assuming the administrator has banned all social networking sites and they only want to allow access to the only social networking site facebook, we will create an Application Override for the Facebook application on port 443 for users to access from the internal network to the internet.
What is application shift?
Application-Shift is a session shifting from one application into another application. Whenever an application shift happens, the firewall performs a new security policy lookup to find the closest rule matching with the new application.
Why is the App-ID not-applicable?
App-ID also labels traffic as not-applicable when the firewall discards the traffic because the Security policy does not allow it. If the firewall cannot identify the traffic using either the CN field in the certificate or the SNI field in the TLS handshake, then the traffic is identified generically as the SSL Application-ID.
Can an app override bypass scanning?
For most use cases, we recommend creating a simple custom application with as few attributes as possible, as the app override will bypass scanning or signature detection. It will simply identify a session as the custom application and take no further action. This can be a very simple but powerful tool to help identify internal applications and improve throughput as the session is offloaded to hardware immediately, but please consider the security implications. The following example outline examples for how to setup an Application-override object:
What does application override do?
Application Override to a custom application will force the firewall to bypass Content and Threat inspection for the traffic that is matching the override rule. The exception to this is when you override to a pre-defined application that supports threat inspection .
How to create an application override policy?
To create an Application Override policy, go to Policies > Application Override, then click Add:
Why do we need to override the application identification process?
For these applications, we may not have signatures to properly identify the expected behavior and identify the traffic with a known application. In such cases, we recommended creating an application override to allow easier identification and reporting, and to prevent confusion.