
What is the main goal of an APT attack?
- Gain access. APT groups gain access to a target by targeting systems through the internet. ...
- Establish a foothold. After gaining access to the target, threat actors use their access to do further reconnaissance. ...
- Gain even greater access. ...
- Move laterally. ...
- Stage the attack. ...
- Take the data. ...
- Remain until they're detected. ...
What is the latest malware?
More Tips To Keep Your Computer Safe From Computer Virus-
- Install good antivirus software on your computer.
- Use a firewall (It is inbuilt in Windows 10 and 8).
- Update software regularly.
- Avoid opening suspicious web pages.
- Don’t respond to spam mail.
- Avoid clicking on suspicious links or attachments.
- Don’t attach new external drives to your computer.
- Choose strong passwords and never share it with anyone.
Is Malwarebytes a good malware software?
- Malwarebytes constantly monitors for all malware and ransomware, protecting your systems and network from being attacked. ...
- Malwarebytes runs silently and does not create a bunch of overhead, dragging your system resources down. ...
- Malwarebytes has been one of the best values with reasonable subscription costs
What are Advanced Persistent Threats?
Advanced Persistent Threat (APT) Protection Market by Offering (Solutions (Sandboxing, Endpoint Protection, SIEM, IDS/IPS, and Next-generation Firewall) and Services), Deployment Mode, Organization Size, Vertical, and Region – Global Forecast to 2025 The ...

Is APT a malware?
APT is a broad term used to describe a prolonged, more strategic and targeted attack which is quite different than traditional worms, viruses or malware.
What is an ATP attack?
An advanced persistent threat (APT) is a prolonged and targeted cyberattack in which an intruder gains access to a network and remains undetected for an extended period of time. APT attacks are initiated to steal data rather than cause damage to the target organization's network.
What is APT in antivirus?
What Is an Advanced Persistent Threat (APT)? An advanced persistent attack (APT) uses continuous and sophisticated hacking techniques to gain access to a system and remain inside for a prolonged and potentially destructive period of time.
What is an example of APT?
Examples of APTs include Stuxnet, which took down Iran's nuclear program, and Hydraq. In 2010, U.S. and Israeli cyberforces attacked the Iranian nuclear program to slow down the country's ability to enrich uranium. Stuxnet was unlike any other virus or worm that came before.
What tools can be used to detect an APT?
You can detect APTs by using tools like UEBA, deception technology, and network monitoring. You can prevent APTs by performing penetration testing, educating employees on proper cyber security standards, limiting access to systems, and keeping your systems updated.
What is ATP in cyber security?
Advanced Threat Prevention (ATP) is a suite of analysis tools designed to defend against advanced threats that use known and unknown attack vectors. ATP augments more common security solutions aimed at repelling known intrusion strategies.
What is an example of an advanced persistent threat?
Cyber Espionage, including theft of intellectual property or state secrets. eCrime for financial gain. Hacktivism. Destruction.
What are rootkits used for?
The whole purpose of a rootkit is to protect malware. Think of it like an invisibility cloak for a malicious program. This malware is then used by cybercriminals to launch an attack. The malware protected by rootkit can even survive multiple reboots and just blends in with regular computer processes.
What is APT or suite?
"Apt" means apartment (number). "Suite" means suite (number). These help pinpoint a location within a specific building. They are typically used when more than one person share an address.
What is a APT answer?
Apt, pertinent, relevant all refer to something suitable or fitting. Apt means to the point and particularly appropriate: an apt comment. Pertinent means pertaining to the matter in hand: a pertinent remark.
How many APT groups are there?
Since then, these organisations have identified more than 150 APT groups globally.
Who are advanced threat actors?
An advanced persistent threat (APT) is a stealthy threat actor, typically a nation state or state-sponsored group, which gains unauthorized access to a computer network and remains undetected for an extended period.
How does ATP work in Office 365?
If you have Office 365 Advanced Threat Protection activated within your Office 365 environment, every time someone checks an email with an attachment included, Safe Attachments automatically opens the file and tests it within a virtual environment that doesn't affect your real-time environment.
What is ATP in artificial intelligence?
Advanced Threat Protection (ATP) solutions are designed to protect an organization's endpoints against advanced and sophisticated threats. They accomplish this using technologies like artificial intelligence (AI) and machine learning (ML).
What is ATP in tech?
Advanced threat protection (ATP) refers to a category of security solutions that defend against sophisticated malware or hacking-based attacks targeting sensitive data.
What is azure ATP?
Microsoft Defender for Identity (formerly Azure Advanced Threat Protection, also known as Azure ATP) is a cloud-based security solution that leverages your on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your ...
What is an APT hacker?
The intention of an APT is to exfiltrate or steal data rather than cause a network outage, denial of service or infect systems with malware. APTs often use social engineering tactics or exploit software ...
What is an APT?
What Is an Advanced Persistent Threat (APT)? An advanced persistent threat (APT) is a covert cyber attack on a computer network where the attacker gains and maintains unauthorized access to the targeted network and remains undetected for a significant period.
Who would launch an APT attack?
Many suspect that governments and nation states have used APT attacks to disrupt specific military or intelligence operations. Examples include the Titan Rain, Ghostnet, Stuxnet attacks and others. In addition, smaller groups are using simpler tools, such as social engineering, to gain access and steal intellectual property.
Why would someone launch an APT?
A successful advanced persistent threat can be extremely effective and beneficial to the attacker. For nation states, there are significant political motivations, such as military intelligence. For smaller groups, APTs can lead to significant competitive advantages or lucrative payouts.
How does APT differ from traditional web application threats?
APT attacks differ from traditional web application threats, in that: They’re significantly more complex. They’re not hit and run attacks—once a network is infiltrated, the perpetrator remains in order to attain as much information as possible.
What are the stages of APT?
A successful APT attack can be broken down into three stages: 1) network infiltration, 2) the expansion of the attacker’s presence and 3) the extraction of amassed data—all without being detected.
What is Imperva application security?
Application security can become an afterthought which leaves opening for attackers. Imperva is the global leader in application security, protecting your edge and all paths to your data.
What are the three attack surfaces that an enterprise is typically infiltrated by?
Enterprises are typically infiltrated through the compromising of one of three attack surfaces: web assets, network resources or authorized human users.
Where is stolen information stored?
While an APT event is underway, stolen information is typically stored in a secure location inside the network being assaulted. Once enough data has been collected, the thieves need to extract it without being detected.
Can an infiltrator execute a DDoS attack?
Additionally, infiltrators may simultaneously execute a DDoS attack against their target. This serves both as a smoke screen to distract network personnel and as a means of weakening a security perimeter, making it easier to breach.
What is an APT attack?
An APT attack is carefully planned and designed to infiltrate a specific organization, evade existing security measures and fly under the radar. Executing an APT attack requires a higher degree of customization and sophistication than a traditional attack.
How does an APT attack work?
To prevent, detect and resolve an APT, you must recognize its characteristics. Most APTs follow the same basic life cycle of infiltrating a network, expanding access and achieving the goal of the attack, which is most commonly stealing data by extracting it from the network.
What is an APT email?
One indication of an APT is a phishing email that selectively targets high-level individuals like senior executives or technology leaders, often using information obtained from other team members that have already been compromised. Email attacks that target specific individuals are called “spear-phishing.”.
What is APT27 in China?
GOBLIN PANDA (APT27) was first observed in September 2013 when CrowdStrike discovered indicators of attack (IOAs) in the network of a technology company that operates in multiple sectors. This China-based adversary uses two Microsoft Word exploit documents with training-related themes to drop malicious files when opened. Targets are mostly in the defense, energy and government sectors in Southeast Asia, particularly Vietnam.
What is an APT?
An Advanced Persistent Threat (APT) is a prolonged, aimed attack on a specific target with the intention to compromise their system and gain information from or about that target. The target can be a person, an organization or a business.
Why do security researchers groan when they hear the expression "APT"?
The reason security researchers will groan when they hear the expression APT is the fact that some people tend to use it in cases where the threat does not meet the requirements that we specified in our definition.
How to identify an advanced persistent threat?
Stages of an Advanced Persistent Threat 1 Get to know the target. This can vary from figuring out if there is anything worth stealing to compiling a list of employees, or even better, disgruntled ex-employees. Find out what interests the subjects, so you can use that information. in or spear-phishing attacks. 2 Finding an entrance. This usually involves social engineering techniques like spear phishing and watering holes in order to deliver customized malware. 3 Accomplishing a foothold. Get a target to run the malware on his system which is inside the targets network. 4 Carefully widen the scope from the created foothold. For example reconnaisance of the network from an infected computer. This includes putting malware and other tools on the compromised system and hiding them. 5 Find and steal the sought after or other valuable information. To do so, it may be necessary to raise the privileges of the compromised ssytem in the network. 6 Once a firm grip on the network is established it may be necessary to move or widen the entry points in the network so a more permanent access to the information is secured. If there is no need for a permanent monitoring, the tools will usually be removed to cover up the tracks. Sometimes a backdoor is left in place to make a return easier.
Is an attack an APT?
Too many professionals in the security field an attack only qualifies as an APT if it is initiated by a government (agency) or a similar organization. Given the needed resources and patience this certainly make sense.
Who's Most Commonly Targeted by APT Attacks?
Traditionally, enterprises and governments were most targeted by APTs as the nature of the attack requires resources, targeted efforts, and highly sophisticated methods.
Who's Behind APT Attacks?
Nation-state hacker groups are most often behind APT attacks, with US-sponsored groups even leveraging the technique against their adversaries. But APT groups are also on the rise and well-funded hacker groups are now leveraging the attack.
How an Advanced Persistent Threat (APT) Works
Because APTs stay within an organization's environment for so long, there's a lengthy lifecycle to the threat. Here's a breakdown.
APT Tactics and Techniques
An APT is a multifaceted attack and takes advantage of a number of different tools and methods to compromise a network, evade detection, and exfiltrate valuable data. Methods include:
How to Defend Against an APT attack
Because APTs leverage a number of different attack methods and tools, it may seem intimidating to defend against them. However, that's precisely the reason why you should be investing in a number of defense tools and processes that limit how susceptible you are to these types of attacks.
Defending Against APTs Requires a Strong Security Posture
APTs can be scary threats given that they're often hard to detect and are pinpointed to the organization that's targeted. But it doesn't mean you can't defend against them and fundamental cybersecurity tools and solutions play an important role.
What is advanced persistent threat (APT)?
An advanced persistent threat (APT) is a prolonged and targeted cyberattack in which an intruder gains access to a network and remains undetected for an extended period of time.
What is the goal of APT?
The goal of most APT attacks is to achieve and maintain ongoing access to the targeted network rather than to get in and out as quickly as possible. Because a great deal of effort and resources can go into carrying out APT attacks, hackers typically select high-value targets, such as nation-states and large corporations, with the goal of stealing information over a long period of time.
How do APT groups gain access to their network?
To gain access, APT groups often use advanced attack methods, including advanced exploits of zero-day vulnerabilities, as well as highly-targeted spear phishing and other social engineering techniques. To maintain access to the targeted network without being discovered, threat actors will continuously rewrite malicious code to avoid detection and other sophisticated evasion techniques. Some APTs are so complex that they require full-time administrators to maintain the compromised systems and software in the targeted network.
What is the worm that attacks Iran?
The Stuxnet worm used to attack Iran's nuclear program was detected by cybersecurity researchers in 2010. It is still considered to be one of the most sophisticated pieces of malware ever detected. The malware targeted SCADA (supervisory control and data acquisition) systems and was spread with infected USB devices. The U.S. and Israel have both been linked to the development of Stuxnet, and while neither nation has officially acknowledged its role in developing it, there have been unofficial confirmations that they were responsible for Stuxnet.
What is the APT29?
APT29, the Russian advanced persistent threat group also known as Cozy Bear, has been linked to a number of attacks, including a 2015 spear phishing attack on the Pentagon, as well as the 2016 attacks on the Democratic National Committee.
How do threat actors use malware?
They use the malware they've installed to create networks of backdoors and tunnels to move around unnoticed. APTs may use advanced malware techniques such as code rewriting to cover their tracks.
Can threat actors move laterally?
Move laterally. Once threat actors have breached their target systems, including gaining administrator rights, they can then move around the enterprise network at will. They can also attempt to access other servers, as well as other secure areas of the network.
What is APT malware?
Typically, APT refers to China or some other nation-state or well-funded and established criminal entities who want to compromise a very specific sensitive organization. The term was originally used as a code name for Chinese-related intrusions against US military organizations. But as the technology progresses, the term has evolved into advanced adversaries that are hell-bent on exploiting information and sensitive data in a more covert manner. On the contrary, most malware attacks are plain, quick damaging attacks aimed at a specific individual, company, or organization to manipulate their system or network by providing executable instructions inside of user input, as opposed to APTs which take a more strategic, systematic approach.
What is Advanced Persistent Threat (APT)?
APT, short for Advanced Persistent Threat, is a cyber-adversary and a combination of several sophisticated cyber attacks which composed of advanced logistical and operational capability for long-term intrusion campaigns. It is a prolonged and targeted attack on sensitive, corporate, banking networks to maintain access to their networks and infiltrate intellectual property data as well as information that is economically and politically beneficial. The APT is well funded, organized groups that are systematically compromising government and commercial entities. The term was originally developed as a code name for Chinese-related intrusions against US military organizations. The ATP attacks are stealthy and target-specific which is quite different than traditional worms, viruses or malware. The goal is to remain undetected for an extended period of time to gather sensitive data.
How to deal with malware attacks?
– The best way to deal with most malware attacks is to avoid opening suspicious mails or download unverified attachments in the first place. All the network devices and web applications running on the Intranet must be thoroughly and regularly audited for unknown vulnerabilities. Security assessments help solidify network security and eradicate critical security flaws. Coming to protection against APT attacks, choosing a reliable firewall is the first layer of defense against APTs. APTs are new-age threats that use advanced techniques to avoid detection and can stay undetected for a long time. So, a robust security system is required to detect, analyze and eradicate APTs.
What is the first layer of defense against APTs?
Coming to protection against APT attacks, choosing a reliable firewall is the first layer of defense against APTs. APTs are new-age threats that use advanced techniques to avoid detection and can stay undetected for a long time. So, a robust security system is required to detect, analyze and eradicate APTs.
What is a targeted attack on sensitive, corporate, banking networks?
It is a prolonged and targeted attack on sensitive, corporate, banking networks to maintain access to their networks and infiltrate intellectual property data as well as information that is economically and politically beneficial. The attack is carried out by a professional attacker on specific sensitive organizations.
What is ATP attack?
The ATP attacks are stealthy and target-specific which is quite different than traditional worms, viruses or malware. The goal is to remain undetected for an extended period of time to gather sensitive data.
What is an Advanced Persistent Threat?
An Advanced Persistent Threat (APT) is an organized cyberattack by a group of skilled, sophisticated threat actors. APTs are not “hit and run” attacks. Attackers plan their campaign carefully against strategic targets, and carry it out over a prolonged period of time.
What are the Unique Characteristics of Advanced Persistent Threats?
There are a number of sure signs that point to the existence of an APT attack. These signs include:
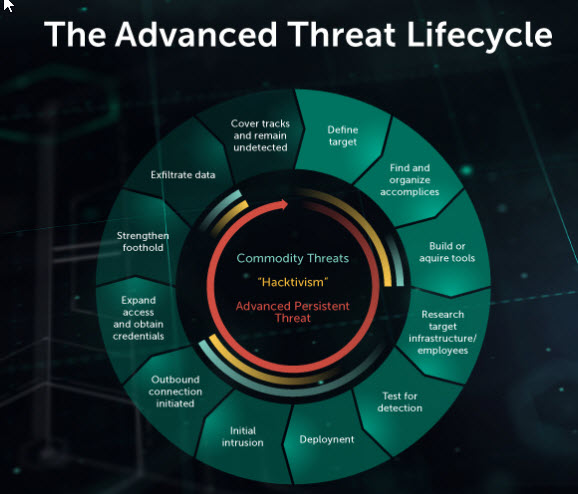
Five APT Attack Stages
APT attacks have multiple stages, from initial access by attackers to ultimate exfiltration of the data and follow-on attacks:
Advanced Persistent Threat Examples
Here are a few examples of APT malware-based attacks and known APT groups:
APT Detection and Protection Measures
APT is a multi-faceted attack, and defenses must include multiple security tools and techniques. These include:
Cynet 360: Advanced Threat Protection for the Enterprise
Cynet 360 is a holistic security platform that can provide multi-faceted protection against Advanced Persistent Threats. Cynet correlates data from endpoints, network analytics and behavioral analytics to present findings with near-zero false positives.
Who is APT1?
APT1 has been identified by various parties as unit 61398 of the People’s Liberation Army. They were one of the first APT groups to be publicly named, in a report released by Mandiant (now owned by FireEye) in 2013. APT1 was noted for wide scale and high volume collection, targeting roughly 150 mostly English-speaking companies at time of reporting.
What is APT1 in China?
Next up in the Advanced Persistent Threat Files: APT1, a unit of the People's Liberation Army of China known for wide-scale and high-volume data collection on mostly English-speaking companies.
Is it inappropriate to attribute an attack based solely on the malware deployed?
NOTE: It’s generally inappropriate to attribute an attack based solely on the malware deployed. APT actors do not operate in a vacuum; they’re capable of collaborating with each other, as well as selling malware to other groups upon conclusion of an ops cycle.
Does APT1 have impunity?
Given that APT1 themselves were no longer able to operate with impunity, it seems reasonable that they would disseminate tools to threat actor groups with better counterintelligence postures.
Introduction
Characteristics of Apt Attacks
- For those attacks that are hard to put your finger on, there are certain characteristics that have been attributed to ATP attacks that may help identify APT as they leave behind different signs than other cyberattacks. These characteristics are briefly explored below.
Phases of Apt
- There are 6 distinct phases of an APT attack. There is no time limit for these phases to conclude as an APT can persist for a long time. 1. Getting to know the target – the information gathered can help in furtherance of the attack. 2. Finding an entrance and deliver custom malware – may be accomplished by spear phishing or taking advantage of watering holes. 3. Gaining the foothol…
Real-World Apt Examples
- Stuxnet
Used by an APT attack group, Stuxnet refers to a worm used in the APT attack that is considered one of the most sophisticated instances of malware ever used. Stuxnet targeted mainly SCADA systems servicing nuclear plants in Iran, - GhostNet
This China-based APT cyberattack group used spear phishing loaded with malicious attachments to gain entry to systems in over 100 countries beginning in 2009. Among the many attack techniques GhostNet used were audio and screen capture to gain information about targets.
Conclusion
- APTs are, in many ways, the collective culmination of the world’s cyberattacks. APT attack groups leverage different types of pre-existing malware, custom made malware, and well work methods to launch targeted attacks that may continue for an extended time period. APT attacks tend to persist after initial detection and mitigation attempts, making them possibly the most serious m…