Authorization policy concepts
- User group. A set of users who can initiate the operation.
- Role. A collection of permissions that can be assigned to users or user groups.
- Operation. An action such as create, delete, modify, distribute , or view.
- Object type. A categorization of the object that the operation is performed on. ...
- Resource. ...
- Resource type
What is an authorization policy and why is it important?
An authorization policy dictates what your identity is allowed to do. For example, any customer of a bank can create and use an identity (e.g., a user name) to log into that bank's online service but the bank's authorization policy must ensure that only you are authorized to access your individual account online once your identity is verified.
What is audit authorization policy change?
Privacy policy. Thank you. Audit Authorization Policy Change allows you to audit assignment and removal of user rights in user right policies, changes in security token object permission, resource attributes changes and Central Access Policy changes for file system objects.
What is the use of authorizationpolicy in Linux?
AuthorizationPolicy enables access control on workloads. For example, the following authorization policy allows nothing and effectively denies all requests to workloads in namespace foo. The following authorization policy allows all requests to workloads in namespace foo. Optional.
What is authorization and access control?
What is Authorization and Access Control? What is Authorization and Access Control? You are probably familiar with the concept of authentication, the way that security systems challenge you to prove you are the customer, user, or employee whom you claim to be, using a password, token, or other form of credential.
What are the three types of authorization policies?
SharePoint provides three types of authorization policies:Add-in-only policy. When the add-in-only policy is used, SharePoint checks only the permissions of the add-in principal. ... User-only policy. When the user-only policy is used, SharePoint checks only the permissions for the user. ... User+add-in policy.
What is authorization with example?
Authorization is the process of giving someone the ability to access a resource. Of course, this definition may sound obscure, but many situations in real life can help illustrate what authorization means so that you can apply those concepts to computer systems. A good example is house ownership.
What is the purpose of authorization?
Authorization is a process by which a server determines if the client has permission to use a resource or access a file. Authorization is usually coupled with authentication so that the server has some concept of who the client is that is requesting access.
What is authorization policy in Kubernetes?
Kubernetes authorizes API requests using the API server. It evaluates all of the request attributes against all policies and allows or denies the request. All parts of an API request must be allowed by some policy in order to proceed. This means that permissions are denied by default.
What are the types of authorization?
There are four types of Authorization – API keys, Basic Auth, HMAC, and OAuth.
What is the word authorization mean?
1 : to endorse, empower, justify, or permit by or as if by some recognized or proper authority (such as custom, evidence, personal right, or regulating power) a custom authorized by time.
How do you implement authorization?
Implementing authorization can be done either in the API gateway or in the microservices. To be able to do extensive application-specific authorization checks, authorization should be handled in the specific microservices. This can be done by passing along the JWT with the request.
What are the characteristics of authorization?
Characteristics are authorization information stored for each PUID. Authorization differs from authentication in that authentication is tied to identity (viz., proving you are who you say you are) and authorization is tied to rights (what you can do). Characteristics may be either basic, public, or private.
What is cluster role in Kubernetes?
A cluster role for Kubernetes defines user permissions required to perform operations on a Kubernetes cluster. You do not need permissions on the cluster to run the script for creating a cluster role because the kubectl api-resources can be accessed by any account.
What are roles in Kubernetes?
In Kubernetes, ClusterRoles and Roles define the actions a user can perform within a cluster or namespace, respectively. You can assign these roles to Kubernetes subjects (users, groups, or service accounts) with role bindings and cluster role bindings.
Which method is used for authentication in Kubernetes?
Kubernetes uses client certificates, bearer tokens, or an authenticating proxy to authenticate API requests through authentication plugins.
What is authorization in banking?
An authorized transaction is a debit or credit card purchase for which the merchant has received approval from the bank that issued the customer's payment card.
What is authorization in database?
Authorization is the process where the database manager gets information about the authenticated user. Part of that information is determining which database operations the user can perform and which data objects a user can access.
What is authorization of users?
What Is Authorization? Authorization in system security is the process of giving the user permission to access a specific resource or function. This term is often used interchangeably with access control or client privilege.
What is authorization and authentication?
Authentication and authorization are two vital information security processes that administrators use to protect systems and information. Authentication verifies the identity of a user or service, and authorization determines their access rights.
What Should A Handler Return?
Note that the Handle method in the handler example returns no value. How is a status of either success or failure indicated? 1. A handler indicates...
Why Would I Want Multiple Handlers For A Requirement?
In cases where you want evaluation to be on an OR basis, implement multiple handlers for a single requirement. For example, Microsoft has doors whi...
Using A Func to Fulfill A Policy
There may be situations in which fulfilling a policy is simple to express in code. It's possible to supply a Func
The HandleRequirementAsync method you implement in an authorization handler has two parameters: an AuthorizationHandlerContext and the TRequirement...
An authorization policy consists of one or more requirements. It's registered as part of the authorization service configuration, in the Startup.ConfigureServices method:
The primary service that determines if authorization is successful is IAuthorizationService:
Policies can be applied to Razor Pages by using an authorization convention.
Policies are applied to controllers by using the [Authorize] attribute with the policy name. For example:
Globally require all users to be authenticated. For information on how to globally require all users to be authenticated, see Require authenticated users. Underneath the covers, role-based authorization and claims-based authorization use a requirement, a requirement handler, and a pre-configured policy.
Authorization is the process of giving someone the ability to access a resource.
In the authorization context, your name is an attribute of your identity. Other attributes are your age, your language, your credit card, and anything else relevant in a specific scenario.
The age of the consumer validated during the registration process is a claim, that is the proof of the user’s age attribute
For instance, accessing the house is a permission, that is, an action that you can perform on a resource. Other permissions on the house may be furnishing it, cleaning it, repair it, etc.
The boarding pass, along with the proof of identity of consumers, represents a kind of ‘access token’ that grants access rights to jump onto the plane.
Consider the case of a salesperson and a programmer. Authentication is used to confirm that each is a valid user and that each is whom they claim to be. Authorization is used to ensure that the programmer can see all of the company’s development files, while the salesperson can see only their business files, and that neither can see the other’s files.
Authorization is an essential part of an enterprise’s IAM solution#N#As a company’s “gatekeeper” Authorization is the process that determines which employees can access which company data. Advanced, fine-grained authorization solutions can apply policies to further limit authorization by factors such as time of day or user location.
Authorization rules or policies should be able to consumed in any of the standard languages, even those such as eXtensible Access Control Markup Language (XACML) and Open Authorization (OAuth).
This means active access governance by management to coordinate the efforts of all units that are responsible for Authorization to “ensure compliance in a consistent, efficient and effective manner: in the words of the Identity Management Institute. Otherwise, access policies may inadvertently vary between units of the enterprise, which could weaken security or interfere with cooperation between members of different units.
Administration is about planning and controlling business decisions. “Administration” is usually associated with logistics and efficiency, but Authorization itself is a business decision since it determines who has access to a company’s data and other intellectual property.
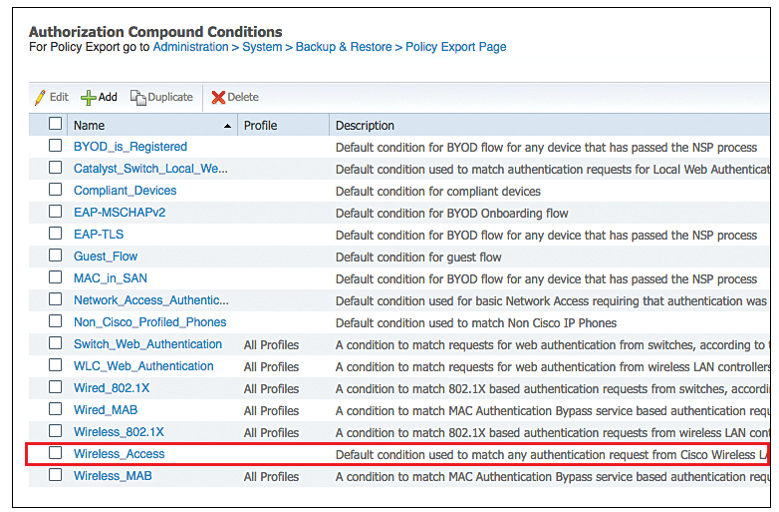
These are the two types of authorization policies that you can configure: • Standard. • Exception. Standard policies are policies created to remain in effect for long periods of time, to apply to a larger group of users or devices or groups, and allow access to specific or all network endpoints.
Authorization profiles let you choose the attributes to be returned when a RADIUS request is accepted. Cisco ISE provides a mechanism where you can configure Common Tasks settings to support commonly-used attributes. You need to enter the value for the Common Tasks attributes, which Cisco ISE translates to the underlying RADIUS values.
To display the Authorization Profile window, you start from the Policy tab (choose Policy > Policy Elements > Results > Authorization > Authorization Profiles). The Authorization Profile window is your starting point for managing the Cisco ISE standard authorization profiles. This is where you can display any existing profiles, create new profiles, or modify or delete existing authorization profiles to meet your specific user or group network needs.
Authorization policies can contain conditional requirements that combine one or more identity groups using a compound condition that includes authorization checks that can return one or more authorization profiles. In addition, conditional requirements can exist apart from the use of a specific identity group (such as in using the default "Any").
Authorization rules have three elements: name, attributes, and permissions. It is the permissions function that maps to an authorization profile. This chapter provides a description of authorization policies and provides example procedures for the following authorization policy-related tasks:
For simple condition-based policy scenarios, authorization checks are made using the AND Boolean operator within the rule. For compound condition-based policies, any type of authorization verification expression can be used. However, for both authorization policy types the verification must comply with the authorization profiles to be returned.
Standard policies can be used as templates in which you modify the original values to serve the needs of a specific identity group, using specific conditions or permissions to create another type of standard policy to meet the needs of new divisions, or groups of users, devices, or groups in your network.
An authorization policy dictates what your identity is allowed to do. For example, any customer of a bank can create and use an identity (e.g., a user name) to log into that bank's online service but the bank's authorization policy must ensure that only you are authorized to access your individual account online once your identity is verified.
A merchant could create an authorization policy for this database to allow a marketing group access to all customer purchases but prevent access to all customer personal and credit card information , so that the marketing group could identify popular products to promote or put on sale.
Correct configuration of access privileges is a critical component of protecting information against unauthorized access and protecting computer systems from abuse, but access control configuration is tricky business. In our next post, we'll look at how organizations implement authorization policies using access conrols or user permissions. We'll follow that with a post that examines attacks that malicious actors or criminals can conduct when access controls are not adequate to prevent unauthorized use, unintended disclosure, or privilege escalation.
Whereas authorization policies define what an individual identity or group may access, access controls – also called permissions or privileges – are the methods we use to enforce such policies. Let's look at examples:
You are probably familiar with the concept of authentication, the way that security systems challenge you to prove you are the customer, user, or employee whom you claim to be, using a password, token, or other form of credential. You may be less familiar with the concept of authorization, and the related term, access control.
Authorization can be applied to more granular levels than simply a web site or company intranet. Your individual identity can be included in a group of identities that share a common authorization policy.
We implicitly create authorization policies when we use social media: Facebook, LinkedIn, or Twitter may authenticate hundreds of millions of users, but to some extent we can authorize whether or how these users engage with us. The same is true when you share files, videos, or photos from sites like Google Docs, Dropbox, Instagram, Pinterest, or Flickr or even when you create a "shared" folder from on your laptop.
What Is a User Authentication Policy? A user authentication policy is a process in which you verify that someone who is attempting to access services and applications is who they claim to be.
Authentication is used to verify that you are who you say you are. After a user’s identity is confirmed, for instance with a username and password, that identity may be used in an authorization policy to determine the appropriate access privileges.
A user authentication policy may be used to help ensure that only the intended audience is accessing certain assets in your organization. User authentication policies strive to ensure that the person requesting sensitive information and data is the right person to access that information.
Network authentication protocols are used to help securely transfer identity credentials for authentication between the subject (user or device) and the authentication server. There are several different authentication protocols for network access control, including:
Accessing Mvc Request Context in Handlers
What is authorization policy?
Which primary service determines if authorization is successful?
How to apply policies to razor pages?
How are policies applied to controllers?
What is globally required?
What is authorization in a business?
What is your name in authorization?
What is the age of the consumer validated during the registration process?
What is accessing a house?
What is boarding pass?
What is the difference between authorization and authentication?
What is authorization in IAM?
What language should authorization policies be able to consume?
What is enforcement policy?
What is administrative decision?
What are the two types of authorization policies?
What is authorization profile?
How to display authorization profile in Cisco ISE?
What is conditional authorization policy?
What are the three elements of authorization rules?
What operator is used for authorization checks?
What is standard policy?
What is authorization policy?
Why would a merchant create an authorization policy for this database?
Why is correct access control configuration important?
What is access control?
What is the meaning of authentication?
Can authorization be applied to a web site?
Can you authorize Facebook?
What is user authentication policy?
What is authentication used for?
Why do we need user authentication?
What is network authentication?

Popular Posts: