How does CBC mode work?
In CBC mode, the current plaintext block is added to the previous ciphertext block, and then the result is encrypted with the key. Decryption is thus the reverse process, which involves decrypting the current ciphertext and then adding the previous ciphertext block to the result.
What is block cipher explain with example?
A block cipher is an encryption method that applies a deterministic algorithm along with a symmetric key to encrypt a block of text, rather than encrypting one bit at a time as in stream ciphers. For example, a common block cipher, AES, encrypts 128 bit blocks with a key of predetermined length: 128, 192, or 256 bits.
Should I disable CBC ciphers?
Vulnerability scanners report the BIG-IP is vulnerable due to the SSH server is configured to use Cipher Block Chaining. They recommend to disable CBC mode cipher encryption, and enable CTR or GCM cipher mode encryption.
What is ECB and CBC?
ECB (Electronic Codebook) - is essentially the first generation of the AES. It is the most basic form of block cipher encryption. CBC (Cipher Blocker Chaining) - is an advanced form of block cipher encryption.
What are the types of block ciphers?
Block Cipher Modes As summarized on the Current Modes page, there are eight confidentiality modes (ECB, CBC, OFB, CFB, CTR, XTS-AES, FF1, and FF3), one authentication mode (CMAC), and five combined modes for confidentiality and authentication (CCM, GCM, KW, KWP, and TKW).
Which algorithm uses block cipher?
Advanced Encryption Standard (AES) − It is a relatively new block cipher based on the encryption algorithm Rijndael that won the AES design competition. IDEA − It is a sufficiently strong block cipher with a block size of 64 and a key size of 128 bits.
Which cipher is hardest to break?
As such, they were regarded by many as unbreakable for 300 years. A Vigenère cipher is difficult to crack using brute-force because each letter in a message could be encoded as any of the 26 26 26 letters.
Which ciphers should be disabled?
If you must still support TLS 1.0, disable TLS 1.0 compression to avoid CRIME attacks. You should also disable weak ciphers such as DES and RC4. DES can be broken in a few hours and RC4 has been found to be weaker than previously thought. In the past, RC4 was advised as a way to mitigate BEAST attacks.
Which ciphers use CBC?
Cipher block chaining (CBC) is a mode of operation for a block cipher -- one in which a sequence of bits are encrypted as a single unit, or block, with a cipher key applied to the entire block. Cipher block chaining uses what is known as an initialization vector (IV) of a certain length.
Which is better ECB or CBC?
Between ECB and CBC mode, it is always better to choose CBC mode. As discussed above, ECB mode leaks information about the plaintext because identical plaintext blocks produce identical ciphertext blocks.
Is AES a block cipher?
The Advanced Encryption Standard (AES) is a symmetric block cipher chosen by the U.S. government to protect classified information. AES is implemented in software and hardware throughout the world to encrypt sensitive data. It is essential for government computer security, cybersecurity and electronic data protection.
Which AES mode is best?
Both the AES-CBC and AES-GCM are able to secure your valuable data with a good implementation. but to prevent complex CBC attacks such as Chosen Plaintext Attack(CPA) and Chosen Ciphertext Attack(CCA) it is necessary to use Authenticated Encryption. So the best option is for that is GCM.
Which of the following is the example of a block cipher?
AES, DES, and 3DES are examples of block ciphers.
What is an example of a cipher?
For example, "GOOD DOG" can be encrypted as "PLLX XLP" where "L" substitutes for "O", "P" for "G", and "X" for "D" in the message. Transposition of the letters "GOOD DOG" can result in "DGOGDOO". These simple ciphers and examples are easy to crack, even without plaintext-ciphertext pairs.
How do you explain a cipher?
What Does Cipher Mean? A cipher is a method of hiding words or text with encryption by replacing original letters with other letters, numbers and symbols through substitution or transposition. A combination of substitution and transposition is also often employed.
What is block cipher advantages and disadvantages?
Block ciphers have the advantage of high diffusion and strong tamper resistance without detection. They have the disadvantage of slower encryption speed since the entire block must be captured for encryption/decryption. Block ciphers also breed errors since a mistake in just one symbol could alter the whole block.
What Does Cipher Block Chaining (CBC) Mean?
In a cipher block chaining process, data is encrypted in specific blocks, and each block is dependent on the blocks before it for decryption. The process uses something called an initialization vector to help tie these blocks of encrypted data together.
What is block cipher?
In a block cipher process, text blocks are treated as isolated units to be encrypted and decrypted sequentially. An alternative is a stream cipher method, where each bit gets acted on independently.
What is the XOR gate in cipher block chaining?
The cipher block chaining process uses a logical gate called XOR to administer this process of observation.
Is cipher block chaining a good method?
Cipher block chaining is often suggested as a stronger method of decryption, ensuring quality . However, some experts warn against certain vulnerabilities of cipher block chaining, including the use of predictable initialization vectors. Advertisement.
How does cipher block chaining work?
In cipher block chaining mode, the plaintext of a block is combined with the ciphertext of the previous block via an exclusive or (xor) operation, and the result is encrypted. The result is the ciphertext of that block, and will also be used in the encryption of the following block. An initialization vector (IV) acts as the “previous ciphertext block” for the first plaintext block. The initialization vector can be made public (i.e., can be sent in the clear along with the ciphertext), but ideally should not be reused for encryption of different messages to avoid having the same ciphertext prefix for two messages with the same plaintext prefix.
Why is CBC used in cipher block chaining?
This is especially critical for packets with a known format and a repeating pattern in the content. To introduce randomness into cipher blocks and make decryption attacks difficult, Cipher Block Chaining (CBC) can be used where before encryption each plain text block is Exclusive operation (XORed) with the previous cipher block.
What is WPA2 encryption?
The outstanding feature of WPA2 is the use of the Advanced Encryption Standard AES. Counter mode cipher block chaining message authentication code protocol (CCMP) provides the highest level of confidentiality, integrity and replay protection available in the 802.11 standard [19]. WPA2 is shown in Fig. 11.28. It uses essentially the same key-establishment process and key hierarchy architecture as WPA ( Fig. 11.26). An exception is that the same key is used for confidentiality and integrity; there are no separate encryption and MIC keys. In contrast to RC4 of WEP which is a stream cipher, AES is a block cipher, although it does use a key stream to encrypt each block. CCMP achieves confidentiality in counter mode by taking each of consecutive 128 bit blocks of packet plaintext and XORing it with a keystream formed from encryption of a counter, incremented for each block, using the temporal key. To create the MIC used to insure integrity, cipher block chaining message mode is used. Each block is XOR'ed with the ciphertext of the previous block and encrypted with the temporal key. The process is started with an initializing vector (IV) created with a counter that is incremented for each packet. MIC is 64 bits of the last ciphertext block. Because of the chaining of blocks, a change in one or more bits of the message will cause a large difference between the MIC sent with the packet and the MIC constructed at the receiver.
How does decryption work?
Decryption reverses the process. The first block of ciphertext is decrypted and then xored with the initialization vector; the result is the first plaintext block. Subsequent ciphertext blocks are decrypted and then xored with the ciphertext of the previous block.
What is CBC in cryptography?
In Cipher Block Chaining (CBC) mode, the first block of the plaintext is exclusive-OR'd (XOR'd), which is a binary function or operation that compares two bits and alters the output with a third bit, with an initialization vector (IV) prior to the application of the encryption key. The IV is a block of random bits of plaintext. The resultant block is the first block of the ciphertext. Each subsequent block of plaintext is then XOR'd with the previous block of ciphertext prior to encryption, hence the term “chaining.” Due to this XOR process, the same block of plaintext will no longer result in identical ciphertext being produced.
How does CBC work?
Decryption in the CBC mode works in the reverse order. After decrypting the last block of ciphertext, the resultant data is XOR'd with the previous block of ciphertext to recover the original plaintext. The CBC mode is used in hash algorithms.
What is the IV block?
The IV is a block of random bits of plaintext. The resultant block is the first block of the ciphertext. Each subsequent block of plaintext is then XOR'd with the previous block of ciphertext prior to encryption, hence the term “chaining.”.
What is cipher block chaining?
Cipher block chaining uses what is known as an initialization vector (IV) of a certain length of a character. There are one of its key characteristics is that it uses chaining the working mechanism that causes the decryption of a block of ciphertext to depend on all the preceding ciphertext blocks. As a result, the entire validity ...
What happens if you lose a bit in ciphertext?
Case of loss or an insert at least one bit into ciphertext, there will be a shift of bits and borders of blocks that will lead to wrong decryption of all subsequent blocks of ciphertext of the cryptography.
What is CBC in cryptography?
This is a Cipher block chaining (CBC) is a cryptography mode of operation for a block cipher (one in which a sequence of bits are encrypted as a single unit or a block with a ciphertext or encrypted key applied to the entire block of the cryptography). Cipher block chaining uses what is known as an initialization vector ...
Is parallel encryption possible?
This is the parallel encryption is not possible since every encryption requires the previous cipher of the cryptography.
Can ciphertext blocks be identical?
They are the identical ciphertext blocks can only give the result if the same plaintext or original text block is encrypted using both the same encrypted key and the initialization vector (IV), and if the ciphertext block order is not changed or rearranged. It has the advantage over the Electronic Code Book mode in that the XOR'ing process hides plaintext patterns in this way.
What is block cipher?
Cryptography is the science of using codes and ciphers to protect messages. And encryption involves encoding messages so that only the intended recipient can understand the meaning of the message.
Why is a block cipher used?
It's a data block, used by several modes of block ciphers to randomize encryption so that different cipher text is created even if the same plain text is repeatedly encrypted. It usually does not need to be secret, though it cannot be re-used. Ideally, it should be random, unpredictable, and single-use.
What Principles are Important When You're Developing a Cipher?
Kerckhoff's principle states that a cryptographic system should be secure, even if all the details (other than the key) are known publicly. Claude Shannon later rewrote this message as 'The enemy knows the system.'
What are the common modes of Block Ciphers?
In order to encrypt data which is longer than a single block, there are several 'modes' which have been developed. These describe how to apply the single block principles to longer messages.
How do Attackers Attempt to Break Ciphers?
There are a number of techniques attackers use, but they broadly fall into the following categories of attack, based on information required to carry it out.
How does stream cipher work?
A stream cipher works by generating a series of pseudorandom bytes which depend on the key (for any given key, the series of bytes is the same for encryption and decryption). Different keys will produce different strings of bytes. In order to encrypt data the plaintext bytes are XORed with the string of pseudorandom bytes.
How many bits are in a block cipher?
Block ciphers convert plaintext to ciphertext block by block, while stream ciphers convert one byte at a time. Most modern symmetric algorithms are block ciphers, though the block sizes vary (such as DES (64 bits), AES (128, 192, and 256 bits), and so on).
What is block cipher?
Block cipher is an encryption algorithm which takes fixed size of input say b bits and produces a ciphertext of b bits again. If input is larger than b bits it can be divided further. For different applications and uses, there are several modes of operations for a block cipher. Electronic Code Book (ECB) –.
Why is the direct plaintext and ciphertext relationship avoided?
Since there is a different counter value for each block, the direct plaintext and ciphertext relationship is avoided. This means that the same plain text can map to different ciphertext.
Why is it so difficult to apply cryptanalysis?
Since, there is some data loss due to the use of shift register, thus it is difficult for applying cryptanalysis.
Does CBC work for input greater than b bits?
CBC works well for input greater than b bits.
Is parallel encryption faster?
Parallel encryption of blocks of bits is possible, thus it is a faster way of encryption.
What is a block cipher?
A block cipher by itself is only suitable for the secure cryptographic transformation (encryption or decryption) of one fixed-length group of bits called a block. A mode of operation describes how to repeatedly apply a cipher's single-block operation to securely transform amounts of data larger than a block. Most modes require a unique binary ...
How does a block cipher work?
A block cipher works on units of a fixed size (known as a block size ), but messages come in a variety of lengths. So some modes (namely ECB and CBC) require that the final block be padded before encryption. Several padding schemes exist. The simplest is to add null bytes to the plaintext to bring its length up to a multiple of the block size, but care must be taken that the original length of the plaintext can be recovered; this is trivial, for example, if the plaintext is a C style string which contains no null bytes except at the end. Slightly more complex is the original DES method, which is to add a single one bit, followed by enough zero bits to fill out the block; if the message ends on a block boundary, a whole padding block will be added. Most sophisticated are CBC-specific schemes such as ciphertext stealing or residual block termination, which do not cause any extra ciphertext, at the expense of some additional complexity. Schneier and Ferguson suggest two possibilities, both simple: append a byte with value 128 (hex 80), followed by as many zero bytes as needed to fill the last block, or pad the last block with n bytes all with value n .
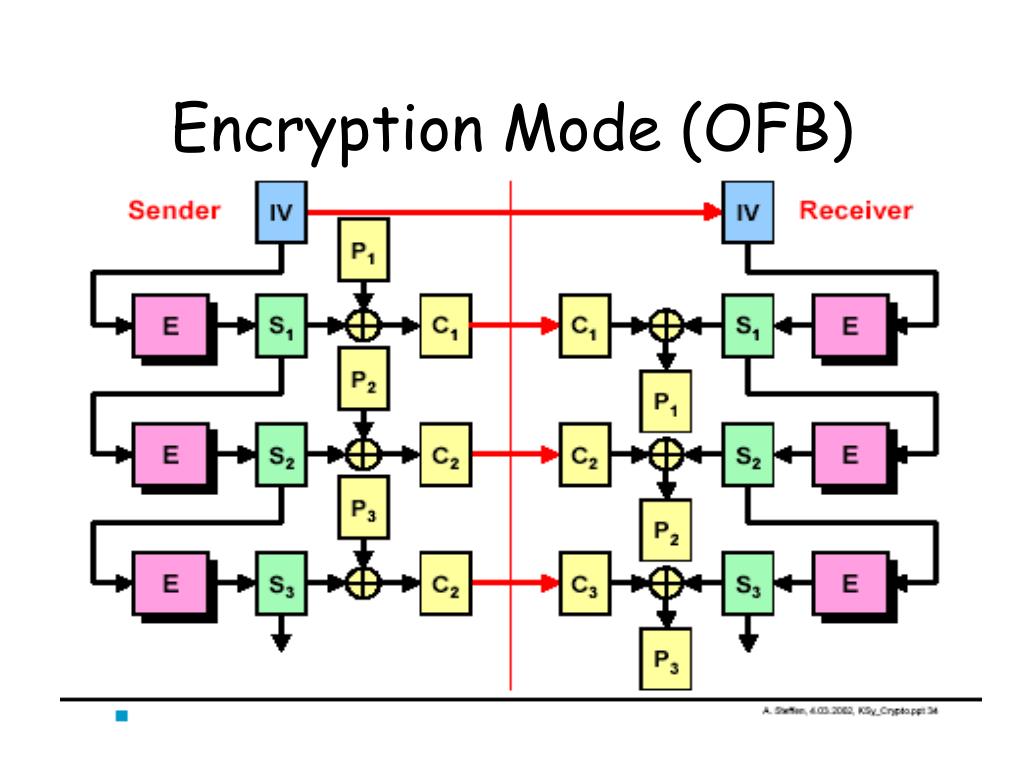
How does CFB work?
CFB, OFB and CTR modes do not require any special measures to handle messages whose lengths are not multiples of the block size, since the modes work by XORing the plaintext with the output of the block cipher. The last partial block of plaintext is XORed with the first few bytes of the last keystream block, producing a final ciphertext block that is the same size as the final partial plaintext block. This characteristic of stream ciphers makes them suitable for applications that require the encrypted ciphertext data to be the same size as the original plaintext data, and for applications that transmit data in streaming form where it is inconvenient to add padding bytes.
What is the IV in encryption?
Most modes require a unique binary sequence, often called an initialization vector (IV), for each encryption operation. The IV has to be non-repeating and, for some modes, random as well. The initialization vector is used to ensure distinct ciphertexts are produced even when the same plaintext is encrypted multiple times independently with the same key. Block ciphers may be capable of operating on more than one block size, but during transformation the block size is always fixed. Block cipher modes operate on whole blocks and require that the last part of the data be padded to a full block if it is smaller than the current block size. There are, however, modes that do not require padding because they effectively use a block cipher as a stream cipher .
What is CTS cryptography?
For example, CTS is ciphertext stealing mode and available in many popular cryptographic libraries. The block cipher modes ECB, CBC, OFB, CFB, CTR, and XTS provide confidentiality, but they do not protect against accidental modification or malicious tampering.
How do different cipher modes mask patterns?
Different cipher modes mask patterns by cascading outputs from the cipher block or other globally deterministic variables into the subsequent cipher block. The inputs of the listed modes are summarized in the following table:
Why are encryption and decryption the same?
Because of the symmetry of the XOR operation, encryption and decryption are exactly the same:
