Full Answer
What are the components of Citrix Endpoint Management?
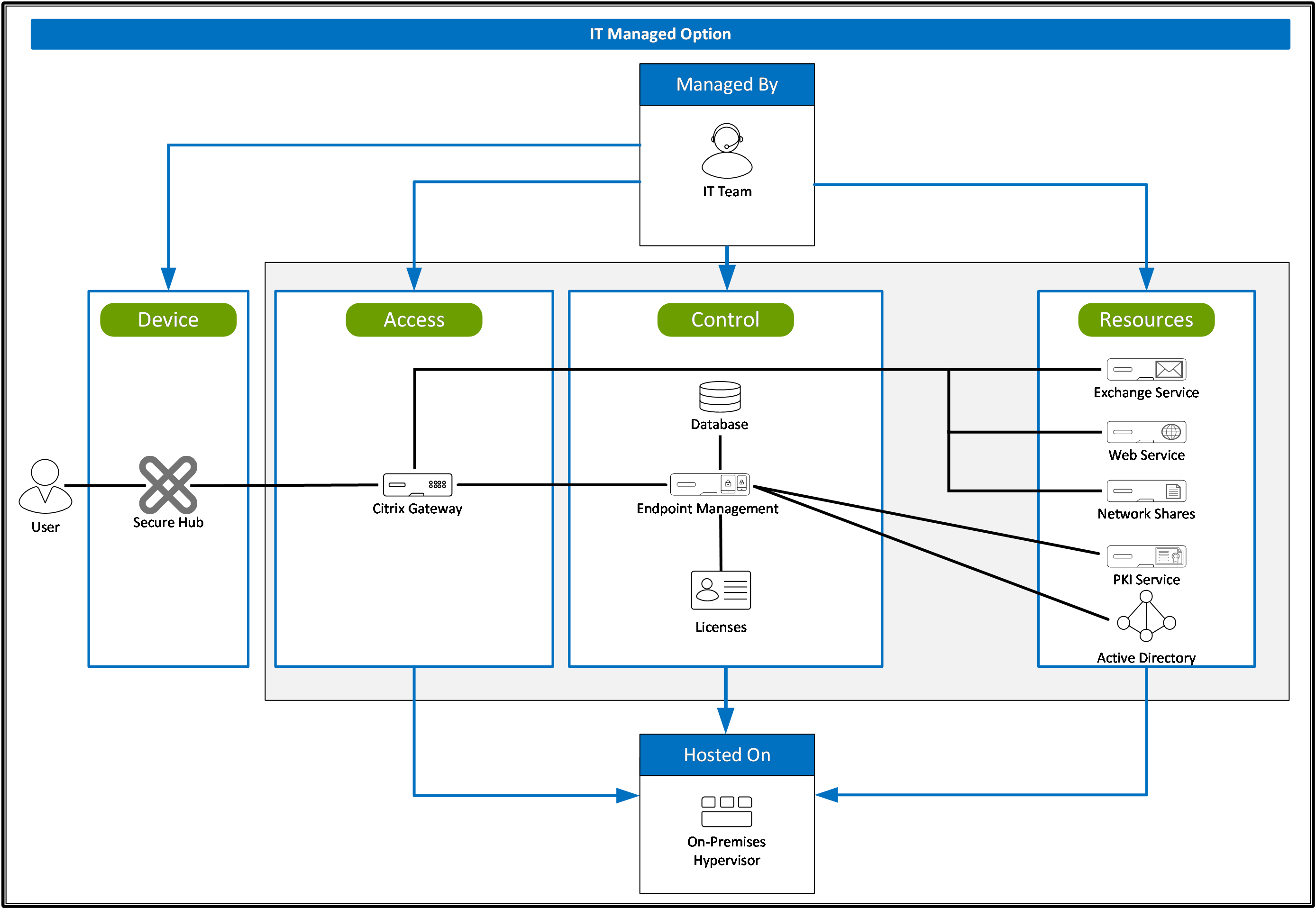
The components of Endpoint Management are modular and build on each other. For example, your deployment includes Citrix Gateway to give users remote access to mobile apps and to track user device types. Endpoint Management is where you manage apps and devices, and Citrix Gateway enables users to connect to your network.
How often does Citrix update Endpoint Management?
Citrix aims to deliver new features and product updates to Endpoint Management customers when they’re available. New releases provide more value, so there’s no reason to delay updates. Rolling updates to Endpoint Management release approximately every two weeks. These updates don’t result in any downtime for your instance or device users.
What is endpoint management software?
Endpoint management software is a program used by IT administrators to ensure that no unapproved devices access a system and that every endpoint device on a network has updated software with security patches to prevent unwanted access. What is endpoint security management?
Is there any configuration or administration guidance for Citrix Cloud?
Isn’t configuration or administration guidance for Citrix Cloud or any of its components or services. For information about the technology used by Endpoint Management to deliver comprehensive, end-to-end security, see the Citrix whitepaper, Citrix Endpoint Management Security Overview.
See more

What does Citrix Endpoint management do?
Citrix Endpoint Management is a solution for managing endpoints, offering mobile device management (MDM) and mobile application management (MAM) capabilities. With Endpoint Management, you manage device and app policies and deliver apps to users.
What is Endpoint Management?
Endpoint management is an IT and cybersecurity process that consists of two main tasks: evaluating, assigning and overseeing the access rights of all endpoints; and applying security policies and tools that will reduce the risk of an attack or prevent such events.
Why do customers choose Citrix Endpoint Management?
Citrix Endpoint Management keeps sensitive data off unauthorized devices and keeps it secure with controls based on user context, like role, location, or device. With predictive analytics and machine learning, your IT team can uncover potentially dangerous user behavior and proactively handle threats.
What is Citrix unified endpoint management?
Citrix Endpoint Management is a unified endpoint management (UEM) solution that brings every app and endpoint into one unified view to increase security and improve productivity.
What is an example of an endpoint?
Examples of endpoints include: Desktops. Laptops. Smartphones.
Why is endpoint management important?
Endpoint management allows IT teams to identify, monitor and control end-users' access to corporate networks and systems. This protects data from being exposed to a breach through employee mistakes that allow malware or ransomware to be installed, for example, and the abuse of local admin accounts by cyber-attackers.
What is Citrix and why is IT on my computer?
Remote PC Access is a feature of Citrix Virtual Apps and Desktops that enables organizations to easily allow their employees to access corporate resources remotely in a secure manner. The Citrix platform makes this secure access possible by giving users access to their physical office PCs.
Is endpoint protection necessary?
As hackers continue to target confidential company data, it is important to secure every device connected to the central network to avoid data breaches. A good MSP security offering should include endpoint protection alongside other solutions, such as a backup and disaster recovery program.
Is endpoint security necessary?
Endpoint Security is Critical for Your Enterprise In today's mobile world, security is evolving rapidly—endpoints now form the new perimeter, and organizations must protect their data across networks.
What does Endpoint use mean?
An endpoint is any device that is physically an end point on a network. Laptops, desktops, mobile phones, tablets, servers, and virtual environments can all be considered endpoints. When one considers a traditional home antivirus, the desktop, laptop, or smartphone that antivirus is installed on is the endpoint.
What are the benefits of endpoint protection?
Coming up are eight essential benefits of endpoint protection that every business owner should consider.Spyware, Malware, and Ransomware Protection. ... Insider Threat Prevention. ... AI Threat Intelligence. ... Content Web Filtering. ... ZTNA and VPN Functionality. ... Single Pane of Glass Device Management.More items...•
What is Citrix and do I need IT?
It gives people access to all the apps they use for work — web, virtual, mobile, and SaaS — from one easy-to-use portal on any of their devices, from wherever they need to work. And because the entire workspace is centralized, IT can see everything that's going on and have a simple way to manage and control it all.
What do you mean by endpoint?
Definition of end point 1 : a point marking the completion of a process or stage of a process especially : a point in a titration at which a definite effect (such as a color change) is observed.
What does endpoint mean in business?
Any device that can connect to the central business network is considered an endpoint.
What is the difference between endpoint and server?
An endpoint is a URL which allows you to access a (web) service running on a server. A server(program) may actually host multiple such services exposing them through different endpoint.
What is the difference between endpoint and firewall?
A software-based firewall, for example, permits or denies traffic on the specific device it is installed on. Traditional endpoint antivirus scans an endpoint's local applications and files searching for known signatures indicative of malware.
What is unified endpoint management?
Unified endpoint management is an overarching approach to manage all of an organization’s endpoint devices from one centralized location. Endpoint...
What is endpoint management software?
Endpoint management software is a program used by IT administrators to ensure that no unapproved devices access a system and that every endpoint de...
What is endpoint security management?
Endpoint security management is the process by which businesses and organizations authenticate endpoint devices that attempt to access a network. E...
What is endpoint security management?
Endpoint security management is the process of supervising and authenticating the devices that access a network. All endpoint devices must be authenticated, throughout the entire network.
What is unified endpoint management?
Unified endpoint management is a comprehensive approach to managing all endpoint devices in an organization from one centralized location. Such management includes:
What are the different types of endpoint management?
The major types of endpoint management include: Endpoint detection and response (EDR): The continuous monitoring of all files entering an organization’s endpoint devices. Network access control: Determine which devices and users have access to the network and what permissions they are granted.
Why is remote work important?
It’s important for organizations to be able to effectively address any threats that could attack their network via endpoint devices.
What is deployment application?
Deploying applications: Schedule deployment of apps to endpoint devices and make it available via the internet or intranet.
Why is endpoint management important?
Endpoint management is vital to companies because although most businesses install anti-virus anti-malware software on devices in their office, not many bother doing so on devices that are operated outside of the office.
What is the purpose of visibility of endpoint devices?
Risk monitoring and mitigation: Visibility of all endpoint devices enables early threat detection and the shutting down of compromised devices.
How to add Citrix Gateway to endpoint?
After you save the authentication settings, you add a Citrix Gateway instance to Endpoint Management. In the Endpoint Management console, click the gear icon in the upper-right corner. The Settings page opens. On the Settings page, scroll to the Citrix Gateway tile and then click Start setup.
How to edit Citrix session profile?
In the session policy bound to the Citrix Gateway virtual server, navigate to Edit session profile > Published Applications. Make sure that Single Sign-On Domain is blank.
How to add LDAP to endpoint?
In the Endpoint Management console, go to Settings > LDAP and add or edit a directory.
What is Citrix Gateway?
When integrated with Endpoint Management, Citrix Gateway provides remote device access to your internal network and resources. Endpoint Management creates a micro VPN from the apps on the device to Citrix Gateway.
How to authenticate Citrix?
Open a web browser, connect to the Citrix Gateway URL, and attempt to authenticate. If the authentication succeeds, you are redirected to an “HTTP Status 404 - Not Found” message.
When using certificate-based authentication at the Citrix Gateway, must you create SSL certificates on a Citrix?
When using certificate-based authentication at the Citrix Gateway, you must create SSL certificates on a Citrix ADC Appliance. See Create and Use SSL Certificates on a Citrix ADC Appliance.
Where to install certificate on Citrix ADC?
Upload and install the certificate files (provided in the script bundle) on the Citrix ADC appliance in the /nsconfig/ssl/ directory. See Create and Use SSL Certificates on a Citrix ADC Appliance.
What happens if you upgrade Citrix ADC to 13.0-64.35?
If you upgrade on-premises Citrix ADC to 13.0-64.35 or later, and Endpoint Management isn’t Workspace-enabled: Single sign-on to Citrix Files or the ShareFile domain URL in a browser with the Company Employee Sign in option results in an error. The user is unable to sign in.
What happens after you delete Citrix Cloud administrator?
After you delete a Citrix Cloud administrator who has a device enrolled: Endpoint Management doesn’t update the User Role in the Endpoint Management console until after the administrator logs in again from the Secure Hub app or the Self-Help Portal. [CXM-45730]
How often does Citrix update endpoint management?
New releases provide more value, so there’s no reason to delay updates. Rolling updates to Endpoint Management release approximately every two weeks.
What happened to Google Play EMM?
During the outage, if you went to Settings > Android Enterprise, Endpoint Management removed the Android Enterprise configuration from the console. As a result, currently enrolled devices don’t receive the policy and app updates. To fix the issue, contact Citrix Technical Support for assistance. [XMHELP-2811]
When updating an administrator role in the Citrix Cloud console, the change is not reflected in the Citrix?
This issue is strictly a user interface issue and does not impact any functionality. Only customers onboarded in version 21.10.0 or later are affected. [CXM-101044]
How long does it take for a device to lock after inactivity?
Lock device after inactivity extension. The maximum amount of device inactivity time before the device locks has been increased to 15 minutes. For more information, see Passcode device policy.
What is App notification policy?
App notification device policy support for Grouping Type and Preview Type settings. With these two settings, you can control how app notifications are grouped and previewed on supervised iOS devices. For more information, see Apps notifications device policy.
FAQs
Citrix Endpoint Management is enterprise mobility management software for businesses. Businesses use Citrix Endpoint Management (formerly Xenmobile) to increase productivity by managing all the apps and devices operating in the workplace.
What is Citrix Endpoint Management?
Citrix Endpoint Management is enterprise mobility management software for businesses. Businesses use Citrix Endpoint Management (formerly Xenmobile) to increase productivity by managing all the apps and devices operating in the workplace.
What is Citrix Endpoint Management?
Citrix Endpoint Management can provision, manage, secure, and inventory a broad range of device types within a single management console.
How to configure scope in device search?
You can configure the search scope through a server property, include.device.properties.during.search, which defaults to false. To include all device properties in a device search, go to Settings > Server Properties and change the setting to true.
How to manage user devices remotely?
To manage user devices remotely and securely, you enroll user devices in Endpoint Management. The Endpoint Management client software is installed on the user device and the user identity is authenticated. Then, Endpoint Management and the user profile are installed. For enrollment details for supported device platforms, see the device articles under this section.
What does app lock mean?
App lock: Denies access to all apps on a device. On Android, after an app lock, users can’t sign in to Endpoint Management. On iOS, users can sign in, but they can’t access any apps.
How to track a device on Secure Hub?
The device info is on the General tab under Security. Use Enable tracking to track the device continuously. Secure Hub reports the location periodically when the device is running.
How to wipe a device?
Selectively wipe a device. Go to Manage > Devices, select a managed device, and then click Secure. In Security Actions, click Selective wipe. For Android devices only, disconnect the device from the corporate network: After the device is wiped, in Security Actions, click Revoke.
What are the actions on a device?
You perform device and app security actions from the Manage > Devices page. Device actions include revoke, lock, unlock, and wipe. App security actions include app lock and app wipe.
Assess
As with any deployment, assessing your needs should be your first priority.
Design & Configure
Once you finish assessing your deployment needs, you can decide how to design and configure your environment. The items to plan include:
Operate & Monitor
After your Endpoint Management environment is up and running, you’ll want to monitor it to ensure smooth operation. The monitoring section discusses where you can find the various logs and messages Endpoint Management and its components generate, and how to read those logs.
Features Scorecard
No scorecards have been submitted for this product yet. Start a Scorecard.
What is Citrix Endpoint Management?
Citrix Endpoint Management (formerly XenMobile), is a UEM and enterprise mobility management application for securing mobile applications and devices.
Frequently Asked Questions
Citrix Endpoint Management (formerly XenMobile), is a UEM and enterprise mobility management application for securing mobile applications and devices.