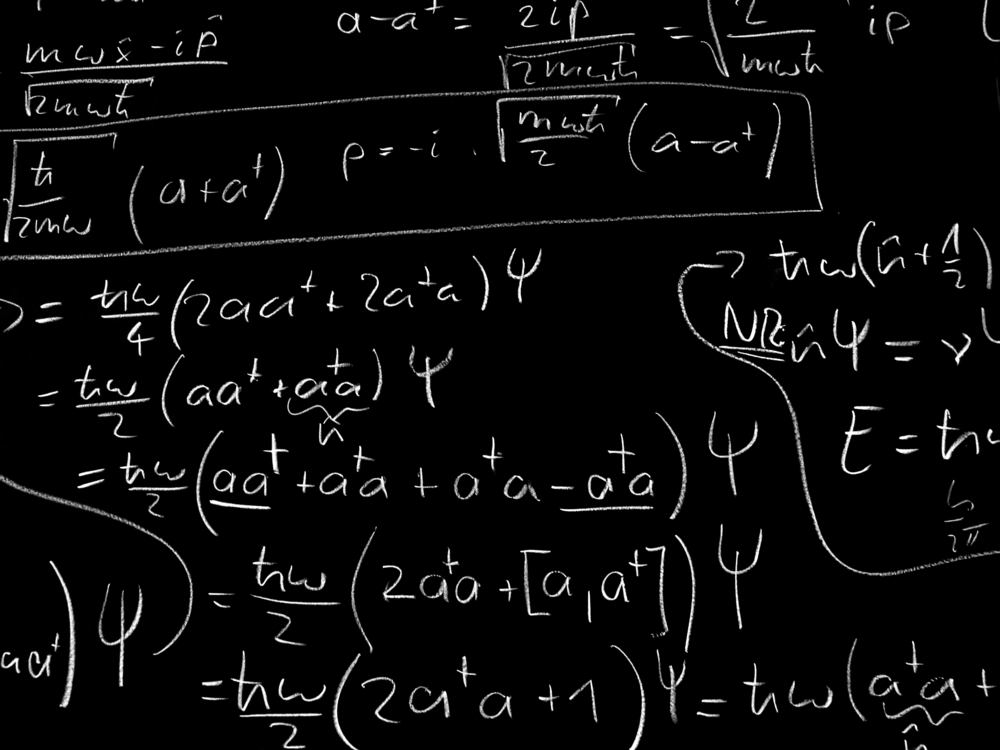
Digital forensics
Digital forensics (sometimes known as digital forensic science) is a branch of forensic science encompassing the recovery and investigation of material found in digital devices, often in relation to computer crime. The term digital forensics was originally used as a synonym for computer foren…
What is the primary goal of digital forensics?
“Digital forensics is the process of uncovering and interpreting electronic data. The goal of the process is to preserve any evidence in its most original form while performing a structured investigation by collecting, identifying, and validating the digital information to reconstruct past events.
What are digital forensic techniques?
Digital Forensic Investigation Techniques. Digital forensics is the application of discovering and presenting evidence in court that has been obtained from computing and storage devices. This course will examine digital forensic as it relates to both civil and criminal investigations.
What does digital forensics mean?
- Digital Forensics is the
- preservation, identification, extraction, interpretation, and documentation of computer evidence which can be used in the court of law
- Branches of Digital Forensics :
- Network Forensics
- Firewall Forensics
- Database Forensics
- Mobile Forensics
- Digital Forensics help to protect from and solve cases involving:
How to become a digital forensics investigator?
Skill requirements likely to be encountered with employers include:
- In-depth knowledge of technology, including mobile operating systems, networks, and hardware
- Knowledge of investigative methods to locate specific electronic data
- Proficiency in the latest cyber forensics, response, and reverse engineering skills and understanding of the latest exploit methodologies.
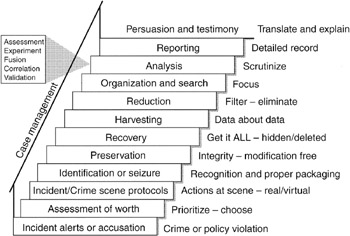
What are the forensic methodologies?
Traditional forensic analysis methods include the following: Chromatography, spectroscopy, hair and fiber analysis, and serology (such as DNA examination) Pathology, anthropology, odontology, toxicology, structural engineering, and examination of questionable documents.
How many stages are there in digital forensic methodology?
The process is predominantly used in computer and mobile forensic investigations and consists of three steps: acquisition, analysis and reporting.
What are 5 digital forensics elements?
Process of Digital forensics includes 1) Identification, 2) Preservation, 3) Analysis, 4) Documentation and, 5) Presentation.
What are the five 5 steps of digital forensics?
Digital forensics is the process of identifying, preserving, analyzing, and documenting digital evidence....Identification. First, find the evidence, noting where it is stored.Preservation. ... Analysis. ... Documentation. ... Presentation.
What are the types of digital forensics?
Here is a brief overview of the main types of digital forensics:Computer Forensics. Computer forensic science (computer forensics) investigates computers and digital storage evidence. ... Mobile Device Forensics. ... Network Forensics. ... Forensic Data Analysis. ... Database Forensics.
What are the 4 steps of the forensic process?
The general phases of the forensic process are: the identification of potential evidence; the acquisition of that evidence; analysis of the evidence; and production of a report.
What tools do digital forensics use?
Featured Digital Forensics and Cybersecurity ToolsAutopsy. ... Bulk Extractor. ... Computer Aided Investigative Environment. ... Digital Forensics Framework. ... DumpZilla. ... EnCase. ... ExifTool. ... FTK Imager.More items...
What are four uses of digital forensics?
As well as identifying direct evidence of a crime, digital forensics can be used to attribute evidence to specific suspects, confirm alibis or statements, determine intent, identify sources (for example, in copyright cases), or authenticate documents.
What is the best tool for digital forensics?
Top 8 Digital Forensics SoftwareIBM Security QRadar.Magnet Forensics.ExtraHop.Parrot Security OS.FTK Forensic Toolkit.Imperva Attack Analytics.EnCase Forensic.Autopsy.
What are the three main goals of digital forensics?
The main goal of digital forensics is to extract data from the electronic evidence, process it into actionable intelligence and present the findings for prosecution.
What are the 3 A's of computer forensic methodologies?
Acquisition (without altering or damaging), Authentication (that recovered evidence is the exact copy of the original data), and Analysis (without modifying) are the three main steps of computer forensic investigations.
What are three 3 sources of digital evidence?
There are many sources of digital evidence, but for the purposes of this publication, the topic is divided into three major forensic categories of devices where evidence can be found: Internet-based, stand-alone computers or devices, and mobile devices.
What are the 3 A in digital forensics?
Acquisition (without altering or damaging), Authentication (that recovered evidence is the exact copy of the original data), and Analysis (without modifying) are the three main steps of computer forensic investigations.
Which of the following are stages of process in digital forensics?
Here are the nine main phases of digital forensics:First Response – the initial reaction of the forensics team following a security incident.Search and Seizure – the forensics team searches all affected devices and seizes them so that the perpetrators can't continue to act.Evidence Collection –Securing the Evidence –More items...•
What are the 7 steps in identifying analysis at a forensic case?
The Seven S'S of Crime-Scene InvestigationSecuring the Scene.Separating the Witnesses.Scanning the Scene.Seeing the Scene.Sketching the Scene.Searching for Evidence.Securing and Collecting Evidence.
What are 4 methods of documenting a crime scene?
There are several methods of documentation: Notes, photography, sketches, and video are all important. Note taking is one of the most important parts of processing the crime scene.
Summary
Digital evidence includes data on computers and mobile devices, including audio, video, and image files as well as software and hardware. Digital evidence can be a part of investigating most crimes, since material relevant to the crime may be recorded in digital form.
Description
The project team develops tools for testing computer forensic software, including test criteria and test sets. ITL also maintains the National Software Reference Library – a vast archive of published software applications that is an important resource for both criminal investigators and historians.
Why is digital forensics so complex?
Due to rapid developing and evolving technology, these types of forensic investigations can become complex and intricate. However, creating a general framework for digital forensic professionals to follow during those investigations would lead to a successful retrieval of relevant digital evidence.
What is the proper completion of a digital forensic investigation?
According to Ruibin, Yun, and Gaertner (2005), the proper completion of any digital forensic investigation is directly related to conducting the processes that are similar to the ones highlighted by Selamat et al. (2008). Ruibin, Yun, and Gaertner also explained that in order to properly perform these phases, proper technique must be used. These techniques would ensure that the authenticity and reliability of the evidence is acceptable by the legal standards of the jurisdiction where the methodologies are being implemented. The use of the term legal is not foreign to digital forensic methodologies, as many researchers have addressed the importance of performing digital forensic investigations using the proper legal authorizations. For instance, the Integrated Digital Investigation Process (IDIP) Model has included obtaining legal authorization to perform a digital forensic investigation as one of the sub-phases of the Deployment Phase (Baryamureeba and Tushabe, 2004).
What are the phases of digital forensics?
Some of those methodologies have used different terminology and sequencing of the phases that a forensic practitioner would have to perform throughout their investigations. Most of the methodologies have agreed on certain processes that are related to the forensic aspect of digital forensic investigations (Selamat et al., 2008). Selamat et al. studied 11 different digital forensic methodologies and concluded that all of them had common phases; preservation, collection, examination, analysis, and reporting. This means that all these researchers have agreed on these specific phases and any newly developed methodology would have to include similar phases.
Why is the volume of data increasing?
The authors explained that three factors have contributed to the volume of data that has become an issue for digital forensic practitioners; increase in the number of electronic devices for each investigation, the increase in the size of memory for those devices, and the number of investigations that require digital forensic examinations.
What is forensic acquisition?
Forensic Acquisition. During this phase, any data that was not acquired or preserved on scene would be imaged. The imaging process would focus on the items that are on the top of the list that was generated during the Evaluation of the Evidence phase. This means that only items that are believed to hold the relevant data would be acquired and not the entire list of items. This would save on the storage space required to save all the forensic images to and also reduce the time required for imaging.
How to ensure a forensic team is executing a forensic methodology properly?
To ensure the forensic team is executing a forensic methodology properly, they must have all the training that would equip all team members with the knowledge needed. This training does not only focus on how to collect or search evidence properly but also trains the members on how to use the tools needed during those processes. For instance, the team should have the knowledge needed regarding the value of preserving data. They should also be able to utilize any software or hardware tools that are capable of preserving and acquiring data from different platforms.
What is the preparation phase of forensics?
The preparation phase can be applied in two situations; when creating a new digital forensic team and after completing a digital forensic investigation. This phase is mainly aimed at ensuring that digital forensic teams, no matter what their mission might be, are capable of initiating and completing an investigation properly and without any problems. Just as the case for the EIDIP, the focus in this phase is ensuring that the forensic team is trained and equipped for their assigned mission.
What is digital forensics?
Digital Forensics is the process of identifying, preserving, examining, and analyzing the digital evidence by validating the procedures and its final representation of that digital evidence in the court to evident few legal questions regarding the crime and attacks. It is a method of discovering proofs from digital media like a PC, ...
What are the objectives of digital forensics?
Below are the few objectives of using digital forensics: 1 Evidence to Court: It recovers, analyzes, and preserves digital and forensic evidence in such a way that it will help in the investigation of the department to present the evidence in the court. 2 Identifying the culprit: It aims to cause the attacks and identify the main culprit behind the crimes. 3 Legal Procedures: To Design the methods at a suspicious crime place, which will assure that the evidence found is uncorrupted. 4 Data Redundancy: Recover the files that were deleted and subdivide them from digital media to validate them. 5 It also promotes you to find the evidence instantly and makes you identify the impact of the culprit on the crime or the attacks. 6 Storing the evidence or the proofs by the procedures in the way of legal custody in the court of law.
What is digital evidence?
It is also defined as “the way of identifying, preserving, examining, and analyzing the digital evidence, by validating the procedures, and its final representation of that digital evidence in the court to evident few legal questions regarding the crime and attacks. ”. Start Your Free Software Development Course.
What is evidence to court?
Evidence to Court: It recovers, analyzes, and preserves digital and forensic evidence in such a way that it will help in the investigation of the department to present the evidence in the court. Identifying the culprit: It aims to cause the attacks and identify the main culprit behind the crimes. Legal Procedures: To Design ...
What is network forensics?
Network Forensics: It is generally a sub-part of digital forensics relating to the monitoring and detecting of system network traffic to extract crucial data for all legally evidence to present at the court.
Why is digital forensics important?
Digital forensic Tools are much accurate and more helpful to investigating officers who try to find the culprits who perform digital crimes or attacks. They are also used for digital criminal cases such as Theft of Intellectual Property, Industrial damage, Employment issues regarding their job security, and investigations on Fraud cases.
What is the first step in the forensic process?
1. Identification. It is the first and fore more step in the process that will include the forensic process like where the evidence is found, where the evidence is preserved, and then the way it is stored. Electronic Device media includes PC, digital phones, IPads, etc. 2.
What Is Digital Forensics?
Digital forensics is the collection, assessment and presentation of evidence gathered from digital media. Digital evidence comes from computers, mobile phones and servers. Digital forensics helps solve complicated cases that rely on evidence from electronic devices.
What is a cellebrite?
Cellebrite UFED (Universal Forensic Extraction Device) allows forensic specialists to employ data collection capabilities in the lab, at a remote location and in the field; retrieve cloud tokens and app data; and overcome mobile encryption challenges and password/PIN locks.
What is a forensic sleuth kit?
The Sleuth Kit allows forensic specialists to utilize a collection of command-line tools, access a C library, and analyze disk images and recover files.
What skills do forensic investigators need?
Necessary skills include countering anti-forensic techniques, understanding system forensics, navigating file systems and hard disks, and investigating email crimes.
What is webinspect testing?
Webinspect allows forensic specialists to test the dynamic behavior of web applications for security vulnerabilities; conduct simultaneous crawl testing at various levels, from professional to novice; and use centralized program management features.
How many steps are there in digital forensics?
There are nine steps that digital forensic specialists usually take while investigating digital evidence.
What is an expert witness?
An expert witness is a professional who works in a field related to the case. The expert witness affirms that the data is useful as evidence and presents it in court.
Identifying, extracting and analyzing – The devil is in the details
Identification is the first step in the digital forensics methodology. In this stage, the evidence is examined by type, location, format and condition. How the evidence will be stored is also identified. The storage media can be any digital source such as mobile phones, personal computers, servers, networks, etc.
It is all about documenting and presenting
All the written and digital documents based on the attack are created. The documentation helps recreate and review the crime scene and present it in the court of law. In addition, the photographs, mapping and methodology must be included. In the end, it all must be summarised, and conclusions must be drawn.
Preserving digital evidence to ensure authenticity
The digital evidence must be preserved properly not just to use as evidence after the breach or crime but also for future use, as legal cases at times may run for weeks, months and sometimes years. Preservation also ensures that the evidence is not tampered with. Time is crucial when it comes to the protection of digital evidence.
Conclusion
The steps or activities in the digital forensics methodology may need to be repeated to find conclusive evidence. All this means that the investigation is thorough with no room for error or doubt. The result is to uncover the motive, identify the culprit and present the evidence in the court of law.
What is contemporaneous note taking?
A crucial activity that accompanies the first four steps is contemporaneous note-taking. This is the documentation of what you have done immediately after you have done it in sufficient detail for another person to reproduce what you have done from the notes alone.
What is analysis in a research?
Analysis – an in-depth systematic search of evidence relating to the incident being investigated. The outputs of examination are data objects found in the collected information; they may include system- and user-generated files. Analysis aims to draw conclusions based on the evidence found.
What are the steps of digital forensics?
The digital forensic process has the following five basic stages: 1 Identification – the first stage identifies potential sources of relevant evidence/information (devices) as well as key custodians and location of data. 2 Preservation – the process of preserving relevant electronically stored information (ESI) by protecting the crime or incident scene, capturing visual images of the scene and documenting all relevant information about the evidence and how it was acquired. 3 Collection – collecting digital information that may be relevant to the investigation. Collection may involve removing the electronic device (s) from the crime or incident scene and then imaging, copying or printing out its (their) content. 4 Analysis – an in-depth systematic search of evidence relating to the incident being investigated. The outputs of examination are data objects found in the collected information; they may include system- and user-generated files. Analysis aims to draw conclusions based on the evidence found. 5 Reporting – firstly, reports are based on proven techniques and methodology and secondly, other competent forensic examiners should be able to duplicate and reproduce the same results.
Why is forensic reporting important?
Forensic reporting is important because the entire forensic process is only worth as much as the information examiners convey to the requester. After the reporting, the requester does case-level analysis where he or she (possibly with examiners) interprets the findings in the context of the whole case.
What is computer forensics?
The complete definition of computer forensics is as follows: "The use of scientifically derived and proven methods toward the preservation, collection, validation, identification, analysis, interpretation, documentation and presentation of digital evidence derived from digital sources for the purpose of facilitating or furthering the reconstruction of events found to be criminal…." A Road Map for Digital Forensic Research, Report from the First Digital Forensic Research Workshop (DFRWS), available at http://dfrws.org/2001/dfrws-rm-final.pdf.
What do the prosecutor and forensic examiner decide?
The prosecutor and forensic examiner must decide, and communicate to each other, how much of the process is to be completed at each stage of an investigation or prosecution. The process is potentially iterative, so they also must decide how many times to repeat the process. It is fundamentally important that everyone understand whether a case only needs preparation, extraction, and identification, or whether it also requires analysis.
What is the second list of data that examiners add to a search lead?
They add anything extracted to a second list called an "Extracted Data List." Examiners pursue all the search leads, adding results to this second list. Then they move to the next phase of the methodology, identification.
Where to find cybercrime flowchart?
It is available on the public Web site at www.cybercrime.gov/forensics_gov/forensicschart.pdf. The flowchart is helpful as a guide to instruction and discussion. It also helps clarify the elements of the process. Many other resources are available on the section's public Web site, www.cybercrime.gov. In addition, anyone in the Criminal Division or U.S Attorneys' offices can find additional resources on the new intranet site, CCIPS Online. Go to DOJ Net and click on the "CCIPS Online" link. You can also reach us at (202) 514-1026.
How do examiners produce the most valuable analysis?
Often examiners can produce the most valuable analysis by looking at when things happened and producing a timeline that tells a coherent story. For each relevant item, examiners try to explain when it was created, accessed, modified, received, sent, viewed, deleted, and launched.
How do examiners get original evidence?
If examiners get original evidence, they need to make a working copy and guard the original's chain of custody. The examiners make sure the copy in their possession is intact and unaltered. They typically do this by verifying a hash, or digital fingerprint, of the evidence.

Abstract
Focused Digital Forensic Methodology
- Modern society has become very dependent on computers and technology to run all aspects of their lives. Technology has had a very positive impact on humanity, which can be easily proven with a short visit to any hospital and witnessing how computers and technology have become tools used to treat and save lives. However, computers have an indisputable disadvantage of bei…
Previous Work
- As it was mentioned above, there are a large number of digital forensic methodologies that were developed all over the world. One of the first serious attempts to develop a standardized methodology that could be used during digital forensic investigations was in 1995. Pollitt (1995) utilized processes that were originally developed to handle physical evidence as a framework to …
Challenges Facing Current Methodologies
- Technology has been developing on two aspects; hardware and software. For instance, a mobile device hardware has seen great advances that allows these devices to be able to perform complex operations efficiently. At the same time, the software operates on mobile devices has also undergone great advancements to be able to support the consumers’ demand. However, th…
Volume of Data
- The increase in the volume of data was caused by the increasing sizes of electronic storage devices and at the same time the significant decrease in prices of those devices. According to Quick and Choo (2014), digital forensic practitioners have seen a significant increase in the amount of data that is being analyzed in every digital forensic examination. The authors explain…
Current Solutions to The Data Volume Issue
- Ruibin et al. (2005) offered a way to reduce the amount of data for each case by determining the relevant data based on the preliminary investigation. The relevant data for a certain case can be determined through two sources; case information and the person investigating the matter. Combining the information from both sources would assist in building a case profile, which can …
The Proposed Methodology
- Digital forensic practitioners continue to face a great deal of pressure from the challenges explained earlier. These challenges are placing obstacles in the way of examinations, in return causing practitioners to spend an extensive amount of time working on each investigation. However, it appears that researchers have not invested much effort into creating methodologie…
Phases of The FDFM
- The FDFM is designed in a way similar to the IDIP and EIDIP, as it is broken down into multiple phases, which are further broken down into sub-phases. The FDFM is designed in a way similar to the IDIP and EIDIP, as it is broken down into multiple phases, which are further broken down into sub-phases. Preparation Phases.The preparation phase can be applied in two situations; when c…
Conclusions and Future Research
- There are many literatures that propose different types of methodologies that have different focuses. However, many of those methodologies have included phases that are not related to the forensic aspect of those methodologies. Many researchers also addressed the issue of the volume of data that is causing huge delays with digital forensic exams. The proposed methodol…
References
- Agarwal, A., Gupta, M., & Gupta, S. (2011). Systematic digital forensic investigation model.International Journal of Computer Science and Security (IJCSS), 5(1), 118-131. Baryamureeba, V., & Tushabe, F. (2004). The Enhanced Digital Investigation Process Model. Proceedings of the Digital Forensic Research Conference. Baltimore, MD. Carrier, B., & Spafford, …
What Is Digital Forensics?
Objectives of Digital Forensics
- Below are the few objectives of using digital forensics: 1. Evidence to Court:It recovers, analyzes, and preserves digital and forensic evidence in such a way that it will help in the investigation of the department to present the evidence in the court. 2. Identifying the culprit:It aims to cause the attacks and identify the main culprit behind the crimes. 3. Legal Procedures: To Design the meth…
Process of Digital Forensics
- Digital Forensics follows a pattern where each case is first identified then preserved to analyze to document in such a way that it is then presented in the court of law to identify the culprit in the crime. Digital forensics involves the following steps:
Types of Digital Forensics
- There are a few types of digital forensics that include below: 1. Disk Forensics:It will deal with deriving the evidence from digital storage media like USB Devices, DVDs, CDs, etc., by gathering the active files or modifying or deleting the files. 2. Network Forensics:It is generally a sub-part of digital forensics relating to the monitoring and detecting of system network traffic to extract cru…
Advantages of Digital Forensics
- Below are the few advantages of Digital Forensic: 1. To assure the security of the digital forensic system. 2. To gather the proofs in the law of court, which may point to have action on the culprit in the crime scene? 3. It assures the forensic team to capture relevant information if their digital systems or traffic are not working as expected. 4. Accurately track the series of cybercriminals’ …
Disadvantages of Digital Forensics
- Below are the few disadvantages of Digital Forensic: 1. There should not be any tampering with the digital evidence that is presented in the court. We need to prove that no data is corrupted. 2. Storing electronic records is very costly. 3. Legal advisors should have more knowledge on digital devices. 4. It should need to give more secure and easily understandable evidence to the court. …
Conclusion
- Digital forensic Tools are much accurate and more helpful to investigating officers who try to find the culprits who perform digital crimes or attacks. They are also used for digital criminal cases such as Theft of Intellectual Property, Industrial damage, Employment issues regarding their job security, and investigations on Fraud cases.
Recommended Articles
- This is a guide to What is Digital Forensics?. Here we also discuss the introduction and objectives of digital forensics along with advantages and disadvantages. you may also have a look at the following articles to learn more – 1. Cyber Forensics 2. Hardware Hacking 3. Kali Linux Commands 4. Threat Hunting Tools