- Digital signatures in cryptography are the security functions used to tie a person or an entity to digital data.
- They employ algorithms to verify the integrity and authenticity of digital data while protecting sensitive key information.
- Using digital signatures usually involves a public key and a private key.
Full Answer
How to verify digital signature using public key?
Verifying a Digital Signature
- the data
- the signature
- the public key corresponding to the private key used to sign the data
What is DSA algorithm?
The Digital Signature Algorithm (DSA) is one of these. DSA is a type of public-key encryption algorithm, and it is used to generate an electronic signature. As we have already seen, DSA is one of the many algorithms that are used to create digital signatures for data transmission.
What is the best digital signature software?
The Top 9 Best Electronic Signature Software
- SignWell – Best free electronic signature software
- SignNow – Best for embedded electronic signatures
- DocuSign – Best multi-purpose electronic signature software
- HelloSign – Best for legally binding documents
- Adobe Sign – Best for small businesses
- Sign Easy – Best for individual and personal use
- KeepSolid Sign – Best for signing documents offline
How do I create a digital signature in Microsoft?
- Click “Select Image” to choose an image of a signature that you have already saved.
- Alternatively, if you’re using a touch screen, you can hand draw your signature into the box.
- Or type a printed version of your name directly into the box.

What are digital signatures in cryptography?
A digital signature is a cryptographic output used to verify the authenticity of data. A digital signature algorithm allows for two distinct operations: a signing operation, which uses a signing key to produce a signature over raw data.
Where is digital signature standard used?
A digital signature algorithm is intended for use in electronic mail, electronic funds transfer, electronic data interchange, software distribution, data storage, and other applications that require data integrity assurance and data origin authentication.
What is digital signature and its types?
According to technology, there are mainly three types of signatures which are basic, advance, and Simple. A simple digital signature is the easiest digital signature as no encryption is secured. Basic digital signatures are not very different from simple digital signatures.
Who created the digital signature standard?
Background. The Digital Signature Standard (DSS), first proposed by Kravitz [2] in 1991, became a US federal standard in May 1994. It is published as Federal Information Processing Letters (FIPS) 186.
What is digital signature and its importance?
A digital signature is precisely an electronic form of signature used to authenticate any digital document and identity of the signer. It is important and in vogue because it is safer and secure than traditional pen-paper signatures.
What are the three main purposes of the digital signature?
Uses of digital signatures Digital signatures are used to meet three important goals of information security: integrity, authentication, and non-repudiation.
What are the 3 classes of signature?
The three different types of electronic signatures are simple electronic signatures (SES), advanced electronic signatures (AES), and qualified electronic signatures (QES).
What is Type 2 digital signature?
DSC Class 2: DSC Class 2 is used for filing documents to the Registrar of Companies, Income Tax Return, MCA forms, audit reports, etc. In Class 2 DSC, the identity of a person is verified against a trusted and pre-verified database. It is issued for both business and private individuals use.
What are the four properties of digital signature?
Properties of digital signaturesUnforgeable.Authentic.Can't be modified once sent.Not reusable.Prevent repudiation.
What are the two main purposes of a digital signature?
A digital signature is intended to solve the problem of tampering and impersonation in digital communications. Digital signatures can provide evidence of origin, identity and status of electronic documents, transactions or digital messages. Signers can also use them to acknowledge informed consent.
Which algorithm is used in digital signature?
What Is the DSA Algorithm? Digital Signatures Algorithm is a FIPS (Federal Information Processing Standard) for digital signatures. It was proposed in 1991 and globally standardized in 1994 by the National Institute of Standards and Technology (NIST).
What are the rules of digital signature?
The Digital Signatures require a key pair (asymmetric key pairs, mathematically related large numbers) called the Public and Private Keys. Just as physical keys are used for locking and unlocking, in cryptography, the equivalent functions are encryption and decryption.
Where are digital certificates used?
Digital certificates are used in public key cryptography functions most commonly for initializing Secure Sockets Layer (SSL) connections between web browsers and web servers. Digital certificates are also used for sharing keys used for public key encryption and authentication of digital signatures.
Is digital signature valid in USA?
Yes, electronic signatures are valid in all U.S. states and are granted the same legal status as handwritten signatures under state laws.
What is an example of how a digital signature might be used?
The most common example is a wet signature scanned by an electronic device and then inserted into a document. Another example of a simple digital signature is the email signature that we often add at the end of the email, and check the terms and conditions box in the software installation process.
Where can digital signature be used in India?
Class 3 Digital Signature can be used for the following purposes:MCA e-filing.Income Tax e-filing.e-Tendering.LLP registration.GST application.IE code registration.Form 16.Patent and trademark e-filing.More items...
What is digital signature?
Similarly, digital signature is a way of authenticating a digital data coming from a trusted source. Digital Signature Standard (DSS) is a Federal Information Processing Standard (FIPS) which defines algorithms that are used to generate digital signatures with the help of Secure Hash Algorithm (SHA) for the authentication of electronic documents.
What is the output of verification function?
The output of the verification function is compared with the signature component ‘r’. Both the values will match if the sent signature is valid because only the sender with the help of it private key can generate a valid signature.
What is global public key?
Public key of the sender. Global public key. The output of the verification function is compared with the signature component ‘r’. Both the values will match if the sent signature is valid because only the sender with the help of it private key can generate a valid signature. Attention reader!
What is message authentication?
Message authentication − When the verifier validates the digital signature using public key of a sender, he is assured that signature has been created only by sender who possess the corresponding secret private key and no one else.
Why is it desirable to exchange encrypted messages?
In public key encryption scheme, a public (encryption) key of sender is available in open domain, and hence anyone can spoof his identity and send any encrypted message to the receiver.
What is the public key used for encryption?
The private key used for signing is referred to as the signature key and the public key as the verification key. Signer feeds data to the hash function and generates hash of data.
What happens when an attacker modifies a digital signature?
Data Integrity − In case an attacker has access to the data and modifies it, the digital signature verification at receiver end fails. The hash of modified data and the output provided by the verification algorithm will not match. Hence, receiver can safely deny the message assuming that data integrity has been breached.
What does a signer do?
Signer feeds data to the hash function and generates hash of data.
How does a receiver verify a signature?
The receiver after receiving the encrypted data and signature on it, first verifies the signature using sender’s public key. After ensuring the validity of the signature, he then retrieves the data through decryption using his private key.
Why use hash instead of data?
The most important reason of using hash instead of data directly for signing is efficiency of the scheme. Let us assume RSA is used as the signing algorithm. As discussed in public key encryption chapter, the encryption/signing process using RSA involves modular exponentiation.
What is the Digital Signature Standard (DSS)?
The Digital Signature Standard (DSS) is a digital signature algorithm developed by the U.S. National Security Agency as a means of authentication for electronic documents.
How does the Digital Signature Standard work?
DSA is a pair of large numbers that are computed according to the specified algorithm within parameters that enable the authentication of the signatory and, as a consequence, the integrity of the data attached.
What is the Digital Signature Standard format?
The format or signature scheme for a digital signature, according to DSS, is slightly different on the sender and receiver sides.
How Can Simplilearn Help You?
Hope this article has helped you understand how vital digital signatures are in this digital age and the impact of cryptography in shaping the threat model of our corporate sector. This is, however, a small drop in the vast ocean that is cybersecurity, which is an industry that has a growing demand for trained professionals.
What Is Asymmetric Encryption?
You utilize two distinct keys in asymmetric encryption methods, one for encryption and the other for decryption. You use the public key for encryption; meanwhile, you use the private key for decryption. However, you must generate both keys from the receiver’s end.
What Is the DSA Algorithm?
Digital Signatures Algorithm is a FIPS (Federal Information Processing Standard) for digital signatures. It was proposed in 1991 and globally standardized in 1994 by the National Institute of Standards and Technology (NIST). It functions on the framework of modular exponentiation and discrete logarithmic problems, which are difficult to compute as a force-brute system.
How does asymmetric key work?
Typically, an asymmetric key system encrypts using a public key and decrypts with a private key. For digital signatures, however, the reverse is true. The signature is encrypted using the private key and decrypted with the public key. Because the keys are linked, decoding it with the public key verifies that the proper private key was used to sign the document, thereby verifying the signature's provenance.
What is the difference between the image of a typical digital signature verification process and the one above?
The difference between the image of a typical digital signature verification process and the one above is the encryption and decryption part. They have distinct parameters, which you will look into in the next section of this lesson on the DSA Algorithm.
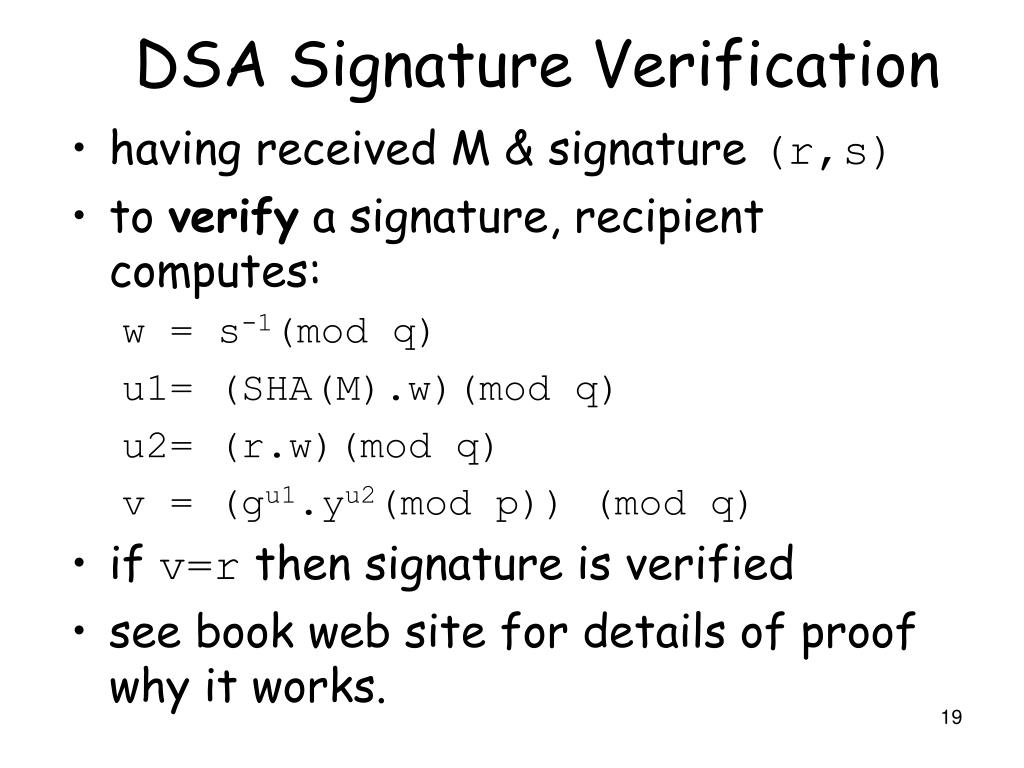
How to find the value of r?
To calculate the value of r, you use the formula r = (gk mod p) mod q.
Why do we use separate keys for encryption?
Using separate keys for encryption and decryption, as seen in the figure above, has helped eliminate key exchange, as seen in the case of symmetric encryption.
Why is digital signature important?
A valid digital signature helps the receiver to know the message comes from the authentic sender and is not altered in between.
What is MAC code?
MAC (Message Authentication Code) was used to provide Message Integrity and Message Authentication but it needs symmetric key established between sender and receiver. A digital signature on other hand uses pair of asymmetric keys.
What does A do in a signature?
A creates a signature from the message and sends a message to B and a signature to the trusted center.
What is the function of preserve integrity hash?
To preserve integrity hash function is applied to the message to create a message digest or fingerprint.
What is the public key used for in a message?
The message is verified using the public key of the sender. When A sends a message to B . B uses the public key of A for verification and A public key cannot create the same signature as C’s private key.
What does it mean to sign a document?
We sign a document to show that is approved by us or created by us. The signature is proof to the recipient that this document is coming from the correct source. The signature on the document simply means the document is authentic.
What keys does Cryptosystem use?
In Cryptosystem uses private and public keys of the receiver.
What is RSA cryptography?
RSA is the most ubiquitous cryptographic algorithm used today and dominates secure transmission of data across the Internet. Soon after, prominent digital signature schemes such as the Lamport Signature and Merkle Trees were developed, with Merkle Trees similarly functioning as a core component of blockchain networks.
What is cryptographic signature?
Cryptographic signature schemes are a fundamental component of cryptocurrency networks that verify the integrity and non-repudiation of transaction messages across the network. They employ asymmetric cryptography and take numerous forms. The types of cryptographic signatures (also known as digital signatures) applied in a specific cryptocurrency ...
How secure is an ECDSA key?
A 384-bit ECDSA key is considered secure enough for the most classified government information by the NSA.
How does Schnorr increase privacy?
Moreover, Schnorr signatures can increase privacy by incentivizing users to use CoinJoin, the coin mixing technique that was traditionally too inconvenient to use regularly.
How does digital signature work?
Digital signatures use public/private key cryptography where a key pair is used as part of an algorithm to send private messages across unsecured channels. The purpose is to achieve the authenticity of the message through the public key verifying that the message came from the corresponding private key. Encryption is where only the holder of the private key can decrypt the message sent and encrypted with the public key. Non-repudiation is another vital component, meaning that a signer cannot deny that they signed a transaction and it is mathematically impossible for a third-party to forge a signature.
Why use public keys in Monero?
Public keys can be used multiple times for various ring signatures across the network. In Monero, they are designed to increase the fungibility of the XMR token by ensuring that transaction outputs are untraceable. There are several types of ring signatures.
What is the signature algorithm?
The Signing Algorithm produces a signature given a message (i.e., transaction) and the private key.
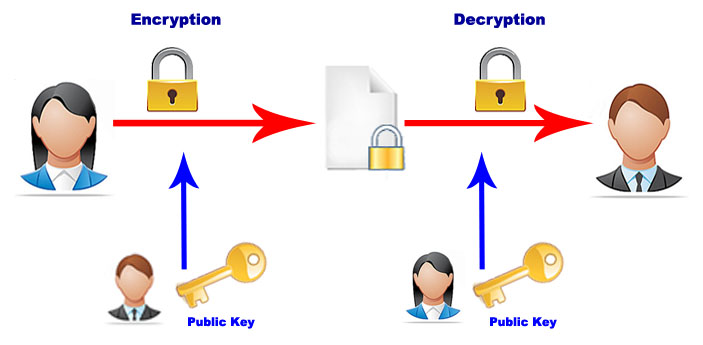
Model of Digital Signature
- As mentioned earlier, the digital signature scheme is based on public key cryptography. The model of digital signature scheme is depicted in the following illustration − The following points explain the entire process in detail − 1. Each person adopting this scheme has a public-private key pair. 2. Generally, the key pairs used for encryption/decry...
Importance of Digital Signature
- Out of all cryptographic primitives, the digital signature using public key cryptography is considered as very important and useful tool to achieve information security. Apart from ability to provide non-repudiation of message, the digital signature also provides message authentication and data integrity. Let us briefly see how this is achieved by the digital signature − 1. Message a…
Encryption with Digital Signature
- In many digital communications, it is desirable to exchange an encrypted messages than plaintext to achieve confidentiality. In public key encryption scheme, a public (encryption) key of sender is available in open domain, and hence anyone can spoof his identity and send any encrypted message to the receiver. This makes it essential for users employing PKC for encryption to see…