What Does Identity Life Cycle Mean? An identity life cycle is a term for the full life cycle of identity and access for a user on a given system. This is often used in a business context, when someone is talking about identity life cycle management, systems that handle the entire context of someone accessing data on a company's network.
What is identity management life cycle?
Identity lifecycle management refers to the process of managing the user identities and evolving access privileges of employees and contractors throughout their tenure—from day one through separation.
What is the concept of identity management?
IDENTITY management is all about managing the attributes related to the USER, group of users, or other identity that may require access from time to time. ACCESS management is all about evaluating those attributes based on existing policies and making a yes or no access decision based upon those attributes.
What are the three stages of an identity and access management system?
IAM systems are designed to perform three key tasks: identify, authenticate, and authorize. Meaning, only the right persons should have access to computers, hardware, software apps, any IT resources, or perform specific tasks.
What is the difference between identity and access management?
The difference between identity management and access management is thus: Identity Management is about managing the attributes related to the user. Access Management is about evaluating the attributes based on policies and making Yes/No decisions.
What are the four layers of identity?
CTI proposes four layers of identity— personal, relational, enactment, and communal (Hecht, Warren, Jung, & Krieger, 2005). These theorists contended that the internalization, externalization, and social enactment of identity are perpetuated by and through communication.
What are the three layers of identity?
It can be helpful to think of identity as three layers: 1) Superficial you: The activities you engage in day in and day out. 2) Personality: Your deeply grooved habits and the energy they create. 3) Deep you: The awareness, or the knower, underneath personality and superficial you.
What are layers of identity?
Identity is conceptualized as experienced at multiple layers, reflecting the person (self), communication (enactment), relationship, and community. The corresponding four layers of identity are labeled as personal, enacted, relational, and communal. The personal identity is an individual's self-concept or self-image.
What are the five pillars of IAM?
The five pillars of IAM: Lifecycle and governance; federation, single sign-on and multi-factor authentication; network access control; privileged account management; and key encryption.
What are the main features of identity management?
9 Features of a Great Identity and Access Management SystemMulti-factor authentication services. ... Passwordless authentication options. ... Single sign-on. ... Privileged account management. ... Compliance and audit services. ... Automatic provisioning services. ... Role-based access control. ... Self-service access requests.
What are the 3 types of access control?
What are the Different Types of Access Control Systems?Discretionary Access Control (DAC) A discretionary access control system, on the other hand, puts a little more control back into the business owner's hands. ... Rule-Based Access Control. ... Identity-Based Access Control.
What is the best identity management?
What Are the 20 Best Identity Management Software Solutions?Microsoft Azure Active Directory.Oracle Identity Management.Okta Identity Management.Zoho Vault.OneLogin.LogMeIn Pro.Auth0.ExcelID.More items...•
Is SSO same as IAM?
AWS Single Sign-On (AWS SSO) is now AWS IAM Identity Center. It is where you create, or connect, your workforce users once and centrally manage their access to multiple AWS accounts and applications.
What is the concept of identity?
Identity refers to our sense of who we are as individuals and as members of social groups. It also refers to our sense of how others may perceive and label us.
What is identity management and why is IT important?
Why is IAM important? Identity and access management, or IAM, is the security discipline that makes it possible for the right entities (people or things) to use the right resources (applications or data) when they need to, without interference, using the devices they want to use.
What are the main features of identity management?
9 Features of a Great Identity and Access Management SystemMulti-factor authentication services. ... Passwordless authentication options. ... Single sign-on. ... Privileged account management. ... Compliance and audit services. ... Automatic provisioning services. ... Role-based access control. ... Self-service access requests.
What is the purpose of identity management theory?
Identity management theory (IMT) explains how people from different cultures may negotiate a shared relationship identity, by balancing one another's face wants and needs across three phases: trial, enmeshment, and renegotiation.
Why is Identity Lifecycle Management Required?
Many corporate IT and security organizations rely on inefficient, manual processes to provision new users and manage their privileges. It can take days (or even weeks in some businesses) to onboard new hires and give them secure access to the applications and IT systems they need to effectively perform their jobs.
What is IDaaS cloud?
IDaaS solutions combine all the features and benefits of an enterprise-class identity security solution with all the economic and operational advantages of a cloud-based service. They help businesses reduce risk, avoid IT infrastructure cost and complexity, and accelerate digital transformation.
What is IDaaS in business?
Historically, most businesses used on-premises solutions to manage user identities and access privileges. Today, many organizations use Identity as a Service (IDaaS) offerings to streamline operations, accelerate time-to-value, and support digital transformation initiatives. An IDaaS offering is delivered as a cloud-based service, hosted and managed by a trusted third party for ultimate simplicity and agility.
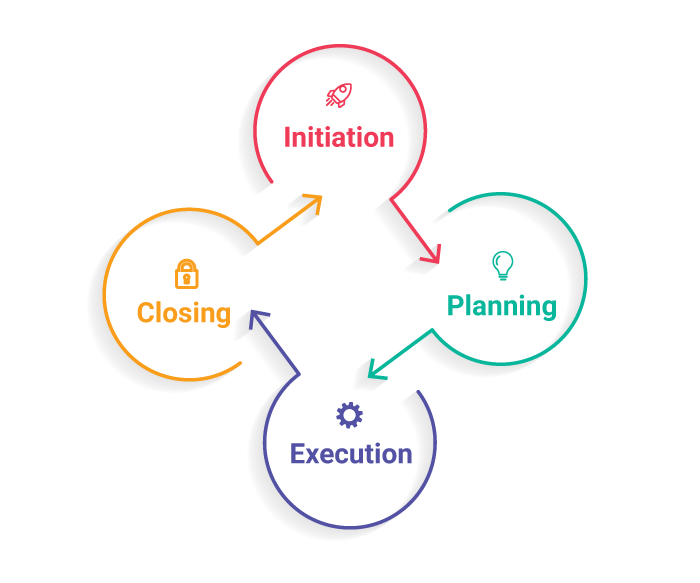
What is the identity lifecycle?
In any ID system, the process of establishing a person’s identity and then using this identity in later transactions involves multiple stages often referred to as the “ identity lifecycle ”.
What is registration of identity?
Identity claim. Registration begins with capturing and recording attributes from a person who “claims” a certain identity, such as biographic data (e.g., name, date of birth, gender, address, email) and biometric features (e.g., fingerprints, face, iris scan). It also may include the collection of meta-data about the time and location, location, and other details of the claim, which might be necessary for auditing purposes. During this process, people also typically provide supporting documentation or evidence to substantiate their claimed identity or—in the absence of such evidence—they may have their data vouched for by a trusted person, such as a local government official. Which attributes and evidence are captured during this phase, the methods and standards used to capture them, and the resulting data quality will have important implications for the inclusivity and trustworthiness of the identity, the speed of data collection, program cost, interoperability with other ID systems, and its utility for various stakeholders.
Why is technology important in the lifecycle of a system?
The technology and protocols used throughout the lifecycle—including for registration, credential issuance, authentication, and management—are critical for ensuring the inclusivity and trustworthiness of the system and its ability to facilitate authentication for different transactions at the appropriate “level of assurance.”.
What is identity proofing?
Identity proofing also commonly involves a deduplication process to ensure uniqueness based on biographic data and/or biometric recognition (e.g., in cases where there is no trusted source of identity information). In some cases, identity proofing also includes a process to verify that the applicant is the true owner of ...
What is the purpose of ID system?
In addition to, or as part of the authentication processes, ID systems can also be used to verify specific attributes of a person—e.g., their name or age—in accordance with regulations on data sharing. This can be done using the credentials that a person presents (e.g., info stored on a card’s chip or a barcode), and/or by querying the database directly.
What is the process of authenticating someone?
The authentication process can involve one or multiple factors—i.e., identity credentials and/or attributes. For example, people may use a username and PIN to login to an e-government portal to pay their taxes or use their card and photo or fingerprint to prove their identity at a hospital.
When do identity records have to be retired?
Identity records may be retired if it is discovered that they were fraudulently created, after security breaches, or following an individual’s death. Identity providers must also work to correct errors, address grievances, and continuously engage with the public and relying parties.
