Full Answer
Why does OAuth V2 have both access and refresh tokens?
Only the Microsoft identity platform endpoint (v2.0) allows you to obtain access tokens to authenticate both work and personal accounts via the Bing Ads API. To ensure that your application can support all users without friction or interruption of service, you should upgrade to the Microsoft identity platform endpoint in production.
What is OAuth and how does it work?
OAuth is an authorization mechanism where services can authorize against each other on your behalf once you’ve given them permission. It is often referred to as delegated access for this reason. It is also an open standard — as it obviously needs to be — because multiple services over the internet need to talk to each other.
How to get OAuth2 access tokens for services?
- The post request should be sent with a content type of x-www-form-urlencoded, and include the following parameters:
- Grant_type: The method you are using to get a token. ...
- Username: The user key for the user who will be authenticated and associated with this token.
- Password: If this is an internal Panopto user, send the user’s password in this field. ...
What is the OAuth 2.0 Bearer Token exactly?
Bearer Tokens are the predominant type of access token used with OAuth 2.0. A Bearer Token is an opaque string, not intended to have any meaning to clients using it. Some servers will issue tokens that are a short string of hexadecimal characters, while others may use structured tokens such as JSON Web Tokens.

What is inside an OAuth token?
An OAuth Access Token is a string that the OAuth client uses to make requests to the resource server. Access tokens do not have to be in any particular format, and in practice, various OAuth servers have chosen many different formats for their access tokens.
What are the main components of OAuth?
The main components of the OAuth 2 architecture are the resource owner, the Client, the authorization server, and the resource server. Each of them has its own responsibility, essential in the authentication and authorization process.
What does OAuth access token look like?
0:593:07OAuth 2.0 access tokens explained - YouTubeYouTubeStart of suggested clipEnd of suggested clipSo an OAuth access token is exactly the same thing. The access token doesn't even necessarily haveMoreSo an OAuth access token is exactly the same thing. The access token doesn't even necessarily have to have a user ID in it all it needs to encode is whether or not the thing that has the access token.
What is OAuth 2 token?
OAuth 2.0, which stands for “Open Authorization”, is a standard designed to allow a website or application to access resources hosted by other web apps on behalf of a user.
What is difference between OAuth and JWT?
JWT is a JSON based security token forAPI Authentication JWT is just serialised, not encrypted. OAuth is not an API or a service: it's an open standard for authorization . OAuth is a standard set of steps for obtaining a token.
What is difference between OAuth and OAuth2?
OAuth 2.0 promises to simplify things in following ways: Once the token was generated, OAuth 1.0 required that the client send two security tokens on every API call, and use both to generate the signature. OAuth 2.0 has only one security token, and no signature is required.
How are OAuth tokens generated?
You use the client ID and one private key to create a signed JWT and construct an access-token request in the appropriate format. Your application then sends the token request to the Google OAuth 2.0 Authorization Server, which returns an access token. The application uses the token to access a Google API.
Where is OAuth token stored?
Tokens received from OAuth providers are stored in a Client Access Token Store. You can configure client access token stores under the Libraries > OAuth2 Stores node in the Policy Studio tree view.
Is JWT an access token?
JWT access tokens JSON Web Token (JWT) access tokens conform to the JWT standard and contain information about an entity in the form of claims. They are self-contained therefore it is not necessary for the recipient to call a server to validate the token.
How do OAuth tokens work?
OAuth doesn't share password data but instead uses authorization tokens to prove an identity between consumers and service providers. OAuth is an authentication protocol that allows you to approve one application interacting with another on your behalf without giving away your password.
How are access tokens generated?
An access token is generated by the logon service when a user logs on to the system and the credentials provided by the user are authenticated against the authentication database.
Does OAuth2 use JWT?
JWT and OAuth2 are entirely different and serve different purposes, but they are compatible and can be used together. The OAuth2 protocol does not specify the format of the tokens, therefore JWTs can be incorporated into the usage of OAuth2.
What is an access token?
Access tokens are the thing that applications use to make API requests on behalf of a user. The access token represents the authorization of a specific application to access specific parts of a user’s data.
Can access tokens be used over https?
The application should ensure the storage of the access token is not accessible to other applications on the same device. The access token can only be used over an https connection, since passing it over a non-encrypted channel would make it trivial for third parties to intercept.
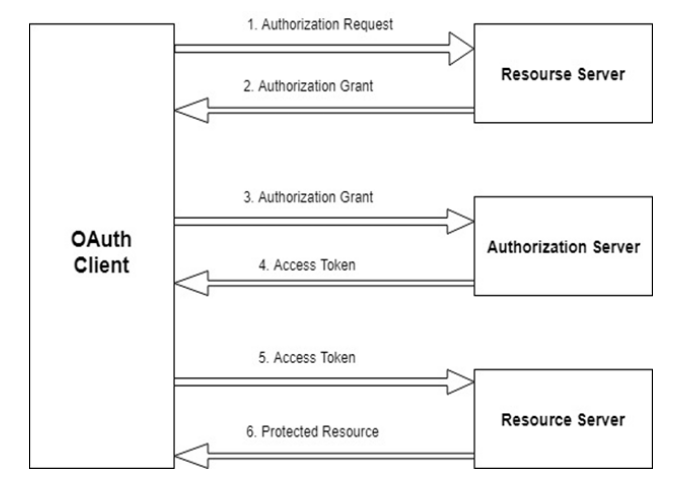
How Does OAuth 2.0 Work?
The authorization flow in a typical OAuth 2.0 implementation is a six-step process. In the example below, an online calendar creation application needs to be able to access a user's photos stored on their Google Drive:
Examples of OAuth
OAuth is often used to consolidate user credentials and streamline the login process for users, so that when they access an online service, they don't have to reenter information that many of their other online accounts already possess.
OAuth 1.0 vs. OAuth 2.0
OAuth 2.0 is a complete rewrite of OAuth 1.0 and uses different terminology and terms. OAuth 1.0's consumer, service provider and user become client, authorization server, resource server and resource owner in OAuth 2.0. OAuth 1.0 does not explicitly separate the roles of resource server and authorization server.
SAML vs. OAuth
While OAuth is an authorization protocol, SAML (Security Assertion Markup Language) is a federated authentication protocol geared towards enterprise security. It is designed for use in single sign-on (SSO) scenarios, allowing a user to log in to various related systems and services using just a single ID and password.
OAuth vs. OpenID
OpenID Connect is an identity layer built on top of the OAuth 2.0 protocol.
What is OAuth 2.0?
OAuth 2.0 is an authorization protocol and NOT an authentication protocol. As such, it is designed primarily as a means of granting access to a set of resources, for example, remote APIs or user’s data.
What is scope in OAuth?
Scopes are an important concept in OAuth 2.0. They are used to specify exactly the reason for which access to resources may be granted. Acceptable scope values, and which resources they relate to, are dependent on the Resource Server.
Can OAuth 2 tokens be exchanged?
The OAuth 2 Authorization server may not directly return an Access Token after the Resource Owner has authorized access. Instead, and for better security , an Authorization Code may be returned, which is then exchanged for an Access Token. In addition, the Authorization server may also issue a Refresh Token with the Access Token. Unlike Access Tokens, Refresh Tokens normally have long expiry times and may be exchanged for new Access Tokens when the latter expires. Because Refresh Tokens have these properties, they have to be stored securely by clients.
