The DHCP snooping feature dynamically builds and maintains the database using information extracted from intercepted DHCP messages. The database contains an entry for each untrusted host with a leased IP address if the host is associated with a VLAN that has DHCP snooping enabled.
How do I enable DHCP snooping?
Where do I put the DHCP snooping trust?
- Enter global configuration mode by issuing the configure terminal command.
- Enable DHCP snooping on a VLAN.
- Change the trust setting of the ports that are connected to the DHCP server to trusted at the interface configuration level.
How to configure DHCP snooping?
These sections describe how to configure DHCP snooping:
- Enabling DHCP Snooping Globally
- Enabling DHCP Option-82 Data Insertion
- Enabling the DHCP Option-82 on Untrusted Port Feature
- Enabling DHCP Snooping MAC Address Verification
- Enabling DHCP Snooping on VLANs
- Configuring the DHCP Trust State on Layer 2 LAN Interfaces
- Configuring DHCP Snooping Rate Limiting on Layer 2 LAN Interfaces
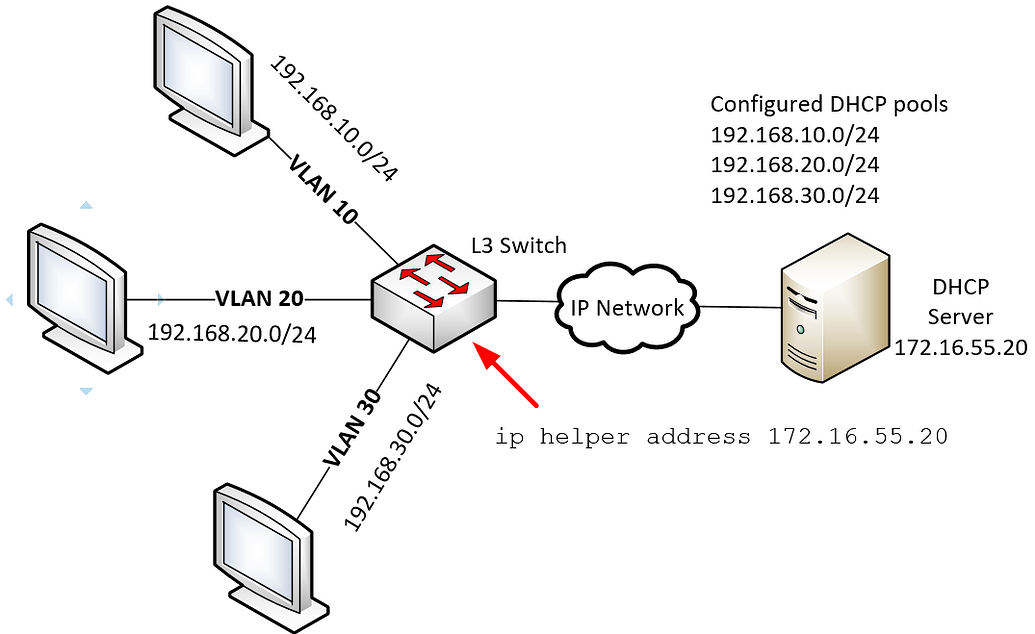
How to set up VLAN to DHCP server?
Packet tracer lab setup
- Create three VLANs and add 2 PCs to each VLAN.
- Configure the DHCP server on the switch and create three DHCP pools.
- Assign a DHCP pool to each VLAN.
- Configure all PCs as DHCP clients.
- Verify that all PCs receive their IP configuration from the DHCP server.
- Test connectivity between all PCs.
Can I use PPPoE together with DHCP?
You would need to have a username and password with PPPOE while the configuration of DHCP is automatic. For DHCP a computer or other device throws out a broadcast requesting an IP and a DHCP server assigns it an IP with a lease for a specific period of time.

What is IP DHCP snooping?
DHCP snooping is a security feature that acts like a firewall between untrusted hosts and trusted DHCP servers. The DHCP snooping feature performs the following activities: • Validates DHCP messages received from untrusted sources and filters out invalid messages. •
What is DHCP VLAN?
The DHCP server responds with the appropriate IP address for the network segment and the additional configuration for network connectivity on the segment. VLANs (Virtual Local Area Networks) allow taking a physical network switch and logically segmenting the physical network environment into multiple network segments.
How do I enable DHCP snooping on a VLAN?
DHCP snooping must be enabled on the client and the DHCP server VLANs. Enter global configuration mode by issuing the configure terminal command. Enable DHCP snooping on a VLAN. Change the trust setting of the ports that are connected to the DHCP server to trusted at the interface configuration level.
What happens when DHCP snooping is enabled?
With DHCP snooping MAC address verification enabled, DHCP snooping verifies that the source MAC address and the client hardware address match in DHCP packets that are received on untrusted ports.
Can you use DHCP on a VLAN?
DHCP VLAN Relay can be applied in such scenario: a DHCP server is deployed to offer IP addresses to clients in multiple VLANs. These VLANs do not have VLAN interfaces. DHCP VLAN Relay can manually designate an L3 interface for all the VLANs as the default relay agent interface.
Does VLAN need DHCP?
Each VLAN is a broadcast domain, so essentially you have to put a DHCP server on each VLAN. There are three possibilities: Put a dedicated DHCP server in each VLAN. Connect a central (multi-homed) DHCP server to each VLAN.
Why is DHCP snooping required when using the?
The Dynamic Host Configuration Protocol (DHCP) snooping feature ensures that DHCP clients obtain IP addresses only from authorized DHCP servers and a DHCP snooping-enabled device records mappings between IP addresses and MAC addresses of DHCP clients, preventing DHCP attacks on the network.
How do I disable IP DHCP snooping?
Disabling DHCP snooping on an interfaceEnter system view.Enter interface view.Disable DHCP snooping on the interface. dhcp snooping disable. By default: If you enable DHCP snooping globally or for a VLAN, DHCP snooping is enabled on all interfaces on the device or on all interfaces in the VLAN.
How do I enable snooping on a DHCP switch?
DHCP snooping must be enabled on the client and the DHCP server VLANs. Enter global configuration mode by issuing the configure terminal command. Enable DHCP snooping on a VLAN. Change the trust setting of the ports that are connected to the DHCP server to trusted at the interface configuration level.
What are the two benefits of DHCP snooping?
DHCP Snooping prevents unauthorized (rogue) DHCP servers offering IP addresses to DHCP clients. The DHCP Snooping feature performs the following activities: Validates DHCP messages from untrusted sources and filters out invalid messages.
Which type of traffic does DHCP snooping drop?
What traffic will DHCP snooping drop? DHCP snooping will drop DHCP messages from a DHCP server that is not trusted. Trusted DHCP servers are identified by configuring a switchport's DHCP snooping trust state.
Can DHCP support remote access?
When you enable Dynamic Host Configuration Protocol (DHCP) to assign a static IP address to an onboard network interface during first-time setup, you can complete the configuration remotely by using an SSH client.
What is DHCP and how does it work?
A DHCP Server is a network server that automatically provides and assigns IP addresses, default gateways and other network parameters to client devices. It relies on the standard protocol known as Dynamic Host Configuration Protocol or DHCP to respond to broadcast queries by clients.
What is VLANs in networking?
VLAN Definition A virtual local area network (VLAN) is a virtualized connection that connects multiple devices and network nodes from different LANs into one logical network.
Why we assign IP address to VLAN?
For a given VLAN you can assign up to 32 IP addresses. This allows you to combine two or more subnets on the same VLAN, which enables devices in the combined subnets to communicate normally through the network without needing to reconfigure the IP addressing in any of the combined subnets. Default gateway operation.
How do I add a DHCP pool to a VLAN?
Use the 'ip dhcp excluded-address' command to define the range of reserved IP addresses. To create a DHCP pool and enter DHCP pool configuration mode, use the 'ip dhcp pool [pool name]' command. use the 'network [network ID] [subnet mask]' command to define the range of IP addresses.
What Is DHCP Snooping?
DHCP Snooping is a layer 2 security technology incorporated into the operating system of a capable network switch that drops DHCP traffic determined to be unacceptable. DHCP Snooping prevents unauthorized (rogue) DHCP servers offering IP addresses to DHCP clients. The DHCP Snooping feature performs the following activities:
What is a DHCP starvation attack?
DHCP starvation attack commonly targets network DHCP servers, in a bid to flood the authorized DHCP server with DHCP REQUEST messages using spoofed source MAC addresses. The DHCP server will respond to all requests, not knowing this is a DHCP starvation attack, by assigning available IP addresses, resulting in the depletion of DHCP pool.
What happens if DHCP Snooping is initiated?
If the DHCP Snooping is initiated, the DHCP offer message can only be sent through the trusted port. Otherwise, it will be dropped. In the acknowledgment stage, a DHCP binding table will be created according to the DHCP ACK message.
What is a trusted port in DHCP?
A trusted port is a port or source whose DHCP server messages are trusted . An untrusted port is a port from which DHCP server messages are not trusted.
Does DHCP Snooping work?
Though DHCP simplifies the IP addressing, it raises security concerns at the same time. To address the concerns, DHCP Snooping, one of the protection mechanisms can prevent the invalid DHCP addresses from the rogue DH CP server and can ward off the resource-exhausting attack that attempts to use up all existing DHCP addresses. FS S3900 series gigabit stackable managed switches can give full play to this feature to protect your network.
Is DHCP snooping only for wired users?
DHCP Snooping is only applicable to wired users . As an access layer security feature, it is mostly enabled on any switch containing access ports in a VLAN serviced by DHCP. When deploying DHCP Snooping, you need to set up the trusted ports (the ports through which legitimate DHCP server messages will flow) before enabling DHCP Snooping on the VLAN you wish to protect. This can be realized in both the CLI interface and also the Web GUI. The CLI commands are showcased in DHCP Snooping Configuration on FS S3900 Series Switches .
How can an Attacker Manuplate DHCP Messages?
Think about it, what if a malicious atttacker gives this IP addresses? If an attacker uses a DHCP software and take over your DHCP messaging, he/she can assign your IP addresses. He/She can do this by replying a DHCP Discover messages earlier than your real DHCP Server. He/she can give his/her IP address as a gateway for you. And then? Your all traffic o through his/her device. This is one of the way that a man-in-the-middle attack occurs.
What are the two types of ports in DHCP?
According to this DHCP security system, there are two port types. These port types are: Trusted Ports. Untrusted Ports. Trusted ports are the ports that is set as verified at the beginning, This means that, any DHCP messages are accepted from this interface.
What is DHCP Snooping?
DHCP Snooping is used on switches to detect such malicious attacks. Basically, this mechanism listens the DHCP messages of “ untrusted ” ports, records port and device information, according to the verification, it determines the harmful ones and prevent.
What is DHCP protocol?
DHCP is one of the most important protocols for our network . With DHCP we can configure IP configurations of our nodes in the network. This DHCP configurations can be done with various DHCP messages. But sometimes these messages can be used for some malicious attacks.
What is an untrusted port?
Untrusted ports are the ports that is set as unverified at the beginning. This means that, “ be careful for the packets coming from this interface ”. At the beginning of the configuration, the required ports set as “ untrusted ”. This ports are generally user ports.
What does a DHCP offer message mean?
This message shows that a DHCP Offer message come from an untursted port. This is a very serious problem. In other words, somebody are trying to be your new DHCP Server, a rogue DHCP Server.
Is DHCP snooping active?
By default DHCP Snooping is not active. Toı use DHCP Snooping, we should enable it. By the way, DHCP Snooping can be enabled either for a single VLAN or for a range of VLANs.
What happens when DHCP Snooping is enabled on all switches?
When DHCP Snooping is enabled on all the switches, by default all “DHCP Offer” packets will be blocked unless the switch is explicitly configured to “trust” certain ports which are facing the legitimate DHCP server.
What does DHCP snooping do?
With DHCP snooping enabled, the switch will listen for DHCP traffic in the network and will allow only “DHCP Offers” coming from trusted sources. Therefore, the DHCP Offer from the fake Rogue server will be blocked by the switch as shown below:
How to disable DHCP snooping?
The general steps include: 1 Enable DHCP Snooping globally on every switch. 2 Enable the snooping feature on the specific VLAN you want to protect (e.g VLAN 10 in our example above). 3 For better compatibility, disable the insertion of DHCP option 82 from the switch. 4 Go to all switches and find the interfaces facing the legitimate DHCP server. These interfaces will receive legitimate DHCP Offer packets and must be configured as “trusted”. All other interfaces by default will block any DHCP Offer packets. 5 Optional: You can place a limit on DHCP client requests (packets per second) so that to avoid an attacker from sending too many DHCP requests and thus deplete the resources of the server.
Why do Cisco switches have DHCP?
This feature can be enabled and configured on Cisco switches with a few commands and protects your network from attackers who might try to connect a rogue DHCP server to your network in order to assign fake IP addresses and DNS servers to your users.
Why limit DHCP requests?
Optional: You can place a limit on DHCP client requests (packets per second) so that to avoid an attacker from sending too many DHCP requests and thus deplete the resources of the server.
Which interfaces are configured to trust the DHCP offer packets?
In our example above, the interfaces Ge0/1 of both SW1 and SW2 and also the interface Fe0/1 of SW3 will be configured to trust the “DHCP Offer” packets because these are coming from the Legitimate DHCP server.
Can a rogue DHCP server be a fake?
However, the Rogue DHCP Server of the attacker will also respond with a “DHCP Offer”. This will create a “race condition” and if the Rogue DHCP Server is a little faster, it will assign fake settings to the user before the legitimate server. This means that the attacker can assign a fake default gateway and DNS server to ...
How does a DHCP relay work?
You can configure the device to run a DHCP relay agent, which forwards DHCP packets between clients and servers. This feature is useful when clients and servers are not on the same physical subnet. Relay agent forwarding is distinct from the normal forwarding of an IP router, where IP datagrams are switched between networks somewhat transparently. By contrast, relay agents receive DHCP messages and then generate a new DHCP message to send out on another interface. The relay agent sets the gateway address (giaddr field of the DHCP packet) and, if configured, adds the relay agent information option (Option 82) in the packet and forwards it to the DHCP server. The reply from the server is forwarded back to the client after removing Option 82.
What happens when you enable DHCP snooping?
When you enable the DHCP snooping feature, the switch begins building and maintaining the DHCP snooping binding database. Features dependent on the DHCP snooping binding database can now make use of it and can therefore also be configured. Enabling the DHCP snooping feature does not globally enable it.
How does DHCP snooping work?
Using information extracted from intercepted DHCP messages, DHCP snooping dynamically builds and maintains a database. The database contains an entry for each untrusted host with a leased IP address if the host is associated with a VLAN that has DHCP snooping enabled. The database does not contain entries for hosts connected through trusted interfaces.
What is DHCP snooping?
DHCP snooping acts like a firewall between untrusted hosts and trusted DHCP servers. DHCP snooping performs the following activities:
What does DHCP do?
When the device receives the DHCP response message, it strips off the Option 82 information and forwards the response to the DHCP client in the client VRF.
How many bindings can a DHCP snooper store?
DHCP snooping has the following configuration guidelines and limitations: The DHCP snooping database can store 2000 bindings. DHCP snooping is not active until you enable the feature, enable DHCP snooping globally, and enable DHCP snooping on at least one VLAN.
What number does DHCP use?
The no option causes DHCP to use RFC numbers 5, 11, and 151 for the link selection, server ID override, and VRF name/VPN ID suboptions, respectively.
What is Table 46-2?
Table 46-2 describes the fields in the show ip dhcp snooping binding command output.
What is snooping MAC address?
The source MAC address is a Layer 2 field associated with the packet, and the client hardware address is a Layer 3 field in the DHCP packet.
What happens when you enable DHCP snooping globally?
Note Configure this command as the last configuration step (or enable the DHCP feature during a scheduled maintenance period) because after you enable DHCP snooping globally, the switch drops DHCP requests until you configure the ports.
How to retain bindings across reloads?
To retain the bindings across reloads, you must use the DHCP snooping database agent. Without this agent, the bindings established by DHCP snooping are lost upon reload, and connectivity is lost as well. The database agent stores the bindings in a file at a configured location.
What is DHCP snooping?
DHCP snooping is a security feature that acts like a firewall between untrusted hosts and trusted DHCP servers. The DHCP snooping feature performs the following activities: • Validates DHCP messages received from untrusted sources and filters out invalid messages.
What is the default trust state of all interfaces?
The default trust state of all interfaces is untrusted. You must configure DHCP server interfaces as trusted. You can also configure other interfaces as trusted if they connect to devices (such as switches or routers) inside your network. You usually do not configure host port interfaces as trusted.
Is DHCP snooping active on all VLANs?
By default, the DHCP snooping feature is inactive on all VLANs. You may enable the feature on a single VLAN or a range of VLANs.