What is a lock in database?
A database lock is used to “lock” some data in a database so that only one database user/session may update that particular data. So, database locks exist to prevent two or more database users from updating the same exact piece of data at the same exact time.
What is lock and its types in DBMS?
Locks are of two kinds − Binary Locks − A lock on a data item can be in two states; it is either locked or unlocked. Shared/exclusive − This type of locking mechanism differentiates the locks based on their uses. If a lock is acquired on a data item to perform a write operation, it is an exclusive lock.
What is lock point in DBMS?
The “Lock Point” is when all locks are held for the whole transaction. Binds all of the data used in a transaction together. It, therefore, prevents a transaction from being split into parts.
How many lock in DBMS?
There are two types of lock: 1. Shared lock: It is also known as a Read-only lock.
What are the two types of locks?
What Are the Different Types of Door Locks?Knob Locks. Knob locks are the most common type of door lock available and the chief security method for most doors. ... Cam Locks. Cam locks consist of a fastener with an attached arm, or cam, that rotates to lock. ... Deadbolt Locks. ... Padlocks. ... Mortise Locks.
What is a lock in concurrency?
A lock is designed to enforce a mutual exclusion concurrency control policy, and with a variety of possible methods there exists multiple unique implementations for different applications.
What is lock level?
A lock level is a device people use in surveying to improve the accuracy and reliability of measurements. Surveying equipment can include a lock level to allow people to fix the surveying level in place with the use of a locking nut while collecting data.
What are locking methods?
There are a number of concurrency control techniques that are used to ensure the isolation and serializability properties of concurrent transactions. The most frequently used concurrency control technique is the Locking method and most commercial DBMSs employ this technique.
What is Serialisation in DBMS?
DBMSDatabaseBig Data Analytics. A schedule is serialized if it is equivalent to a serial schedule. A concurrent schedule must ensure it is the same as if executed serially means one after another. It refers to the sequence of actions such as read, write, abort, commit are performed in a serial manner.
What is strict 2PL?
Strict 2-PL – This requires that in addition to the lock being 2-Phase all Exclusive(X) locks held by the transaction be released until after the Transaction Commits. Following Strict 2-PL ensures that our schedule is: Recoverable. Cascadeless.
What is a lock in DBMS?
Generally, a lock can be defined as a data variable that is related to a data item and the lock indicates that operations can be executed on the data item. Therefore, these DBMS Locks aid to coordinate access to the database record items through concurrent transactions.
What are the advantages of DBMS?
Find some of the listed advantages of the DBMS Locks typed below: 1 DBMS Locks delivers Data integrity for the information stored or accessed from the server. 2 The transactions being performed in any altered manner to confirm serializability and also to escape deadlock. 3 This Lock based protocol is most suitable for read-only type transactions. 4 Here, in this DBMS Locks, all read requests are acknowledged always. 5 This DBMS Locks can be applied to get an improved level of concurrency with a precise low rate of conflict.
Can you have only one exclusive lock on one resource?
But we can place only a single exclusive lock on one resource at one time. It means that the initial user who will obtain an exclusive lock will be able to continue to hold the individual proprietorship of the resource, and here, no other operator can obtain the exclusive lock on that resource.
What is the simplest way to lock data?
1. Simplistic lock protocol. It is the simplest way of locking the data while transaction. Simplistic lock-based protocols allow all the transactions to get the lock on the data before insert or delete or update on it. It will unlock the data item after completing the transaction. 2.
What is a lock based protocol?
Lock-Based Protocol. In this type of protocol, any transaction cannot read or write data until it acquires an appropriate lock on it. There are two types of lock: 1. Shared lock: It is also known as a Read-only lock. In a shared lock, the data item can only read by the transaction.
What is exclusive lock?
2. Exclusive lock: In the exclusive lock, the data item can be both reads as well as written by the transaction.
What is lock protocol in DBMS?
Thus, a need arises to deal with the said concurrency to handle the simultaneous execution of tractions among the multiple databases in the picture. One such method is termed as Lock Based Protocols. In this topic, we are going to learn about Lock Based Protocol s in DBMS.
What is exclusive lock?
Often represented as lock-X (), Exclusive locks provide the privilege of reading and modifying the data as seen fit by a user. For the sake of security and consistency of the database, this process will be exclusive to the user using them and is not permitted to other users trying to access the same data item. Once the exclusive lock is placed, no other locks including the Shared lock can be placed on the same row or column until its unlocked.
What is keynote in DBMS?
A keynote while applying the Lock based protocols in DBMS is that: any number of tractions can hold a Shared Lock while only one traction has a claim over Exclusive Lock since because shared lock is only reading the data and not performing any other actions whereas the exclusive lock is performing both read and write operations.
Can a shared lock be read by multiple users?
This means when a shared lock is implemented on a database, it can be READ by multiple users, however, none of the users reading the data items will be able to update it. In other words, there is no write access associated with Shared Lock.
Can you put a shared lock on the same row?
For the sake of security and consistency of the database, this process will be exclusive to the user using them and is not permitted to other users trying to access the same data item. Once the exclusive lock is placed, no other locks including the Shared lock can be placed on the same row or column until its unlocked.
What is a lock in DBMS?
In DBMS, the lock is a mechanism used for validating data integrity. In Oracle, the engine locks j table data automatically while executing the SQL query commands such as Insert/ Select/ Delete/ Update. This N kind of locking represents implicit locking. In common, the DBMS looks are of 2 types as mentioned below: 1 Shared Locks 2 Binary Locks
What is a shared lock in database management system?
The shared locks in Database Management System are placed on resources at whatever time a read operation such as the SELECT command is performed. Various shared locks can be set on a store concurrently.
Security Model
There might be operating system-specific limits on the maximum number of total locks available. This must be considered when using locks or making this package available to other users. Consider granting the EXECUTE privilege only to specific users or roles.
Rules and Limits
When another process holds "held", an attempt to get "get" does the following:
Operational Notes
User locks never conflict with Oracle locks because they are identified with the prefix "UL". You can view these locks using the Enterprise Manager lock monitor screen or the appropriate fixed views. User locks are automatically released when a session terminates.The lock identifier is a number in the range of 0 to 1073741823.
CONVERT Function
This function converts a lock from one mode to another. CONVERT is an overloaded function that accepts either a user-defined lock identifier, or the lock handle returned by the ALLOCATE_UNIQUE procedure.
RELEASE Function
This function explicitly releases a lock previously acquired using the REQUEST function. Locks are automatically released at the end of a session. RELEASE is an overloaded function that accepts either a user-defined lock identifier, or the lock handle returned by the ALLOCATE_UNIQUE procedure.
REQUEST Function
This function requests a lock with a given mode. REQUEST is an overloaded function that accepts either a user-defined lock identifier, or the lock handle returned by the ALLOCATE_UNIQUE procedure.
Shared lock
Shared locks are placed on resources whenever a read operation (select) is performed. Multiple shared locks can be simultaneously set on a resource.
Exclusive lock
Exclusive locks are placed on resources whenever a write operation (INSERT, UPDATE And DELETE) are performed. Only one exclusive lock can be placed on a resource at a time. i.e. the first user who acquires an exclusive lock will continue to have the sole ownership of the resource, and no other user can acquire an exclusive lock on that resource
Levels of Locks
Oracle does not provide a field level lock. Oracle provides the following three levels of Locking.
Row Level locking
If the WHERE clause evaluates to only one row in the table, a row level lock is used.
Page Level locking
If the WHERE clause evaluates to a set of data, a page level lock is used.
Table Level locking
If there is no WHERE clause, the query accesses the entire table, a table level lock is used. Can't update entire table data when update is done by other user.
Syntax
LOCK TABLE <tablename> [<tablename>]….. IN { ROW SHARE / ROW EXCLUSIVE / SHARE UPDATE / SHARE / SHARE ROW EXCLUSIVE / EXCLUSIVE} [ NOWAIT]
What is a lock in DBMS?
Locks are an integral part to maintain concurrency control in DBMS. A transaction in any system implementing lock based concurrency control cannot read or write a statement until it has obtained the required locks.
What are the two types of locks in a lock based protocol?
There are two types of locks in Lock based protocols. These are: Binary Locks - These can only be in one of two states, locked or unlocked. Shared/Exclusive Locks - Shared locks are acquired when only read operation is to be performed.
What is a strict two phase locking protocol?
Here, all the locks held by a transaction, whether shared or exclusive, are only released once the transaction commits or aborts. An example of Rigorous two - phase locking protocol is:
What is strict 2 phase locking?
Strict two phase locking protocol is similar to two phase locking protocol. The only difference is that in strict 2PL protocol all the exclusive locks acquired by the protocol need to be held until the protocol either commits or aborts. An example of Strict two - phase locking protocol is:
How is a lock obtained?
A lock is obtained by the transaction on the data value before the write operation is performed. After the write operation, the lock can be released. An example of Simplistic Lock Protocol is:
When can a transaction acquire locks?
The transaction can only acquire locks when it is in the growing phase. When it enters the shrinking phase, it can release the previously acquired locks but cannot acquire new locks. The exclusive locks are represented by X and the shared locks are represented by S. An example of Two phase locking protocol is −.
Can a shared lock be used for multiple transactions?
Shared locks can be shared between multiple transactions as there is no data being altered. Exclusive locks are used when write operation is performed. Only the transaction holding the exclusive lock is allowed to make changes to the data value. The different locking protocols are −.
What is deadlock in DBMS?
In a database, a deadlock is an unwanted situation in which two or more transactions are waiting indefinitely for one another to give up locks. Deadlock is said to be one of the most feared complications in DBMS as it brings the whole system to a Halt. Example – let us understand the concept of Deadlock with an example :
When a database is stuck in a deadlock, is it better to avoid the deadlock?
When a database is stuck in a deadlock, It is always better to avoid the deadlock rather than restarting or aborting the database. Deadlock avoidance method is suitable for smaller databases whereas deadlock prevention method is suitable for larger databases.
What is deadlock prevention?
For large database, deadlock prevention method is suitable. A deadlock can be prevented if the resources are allocated in such a way that deadlock never occur. The DBMS analyzes the operations whether they can create deadlock situation or not, If they do, that transaction is never allowed to be executed.
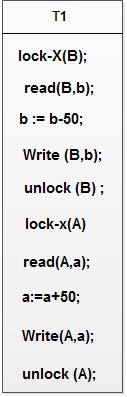
Rules of Binary Locks
- If the simple binary locking scheme described here is used, every transaction must obey the following rules: 1. A transaction must issue the operation lock_item (A) before any read_item (A) or write, item operations are performed in T. 2. A transaction T must issue the operation unlock_…
Disadvantages of Binary Locks
- As discussed earlier, binary locking scheme is too restrictive for database items, because at most one transaction can hold a lock on a given item. So, binary locking system cannot be used for practical purpose.
Share/Exclusive (For Read/Write) Locks
- We should allow several transactions to access the same item A if they all access A’ for reading purposes only. However, if a transaction is to write an item A, it must have exclusive access to A. For this purpose, a different type of lock called a multiple-mode lock is used. In this scheme there are shared/exclusive or read/write locks are used.
Locking Operations
- There are three locking operations called read_lock(A), write_lock(A) and unlock(A) represented as lock-S(A), lock-X(A), unlock(A) (Here, S indicates shared lock, X indicates exclusive lock)can be performed on a data item. A lock associated with an item A, LOCK (A), now has three possible states: “read-locked”, “write-locked,” or “unlocked.” A read-locked item is also called share-locke…
Compatibility of Locks
- Suppose that there are A and B two different locking modes. If a transaction T1 requests a lock of mode on item Q on which transaction T2 currently hold a lock of mode B. If transaction can be granted lock, in spite of the presence of the mode B lock, then we say mode A is compatible with mode B. Such a function is shown in one matrix as shown below: The graphs shows that if two t…
Solution of Inconsistency Problem
- Suppose now that unlocking is delayed to the end of the transaction. The transaction T3 corresponds to T I with unlocking delayed and is defined as Transaction T4 corresponds to T2 with unlocking delayed, and is defined as You should verify that the sequence of reads and writes in schedule I which leads to an incorrect total of Rs.250 being displayed, is no longer possible wi…
How Locks Work in DBMS?
Examples
- Let us discuss an example to explain the DBMS Locks illustrated as follows considering the transaction process that occurred taking the database tables. Before proceeding forwards, we will create a details table to practice with the locking of table statements as, CREATE TABLE details ( id INT NOT NULL AUTO_INCREMENT, detail VARCHAR(100) NOT NULL, PRIMARY KEY (id) ); Out…
Advantages and Disadvantages
- Find some of the listed advantages of the DBMS Locks typed below: 1. DBMS Locks delivers Data integrity for the information stored or accessed from the server. 2. The transactions being performed in any altered manner to confirm serializability and also to escape deadlock. 3. This Lock based protocol is most suitable for read-only type transactions. 4. Here, in this DBMS Lock…
Conclusion
- In DBMS, we have various techniques based on protocols followed for the concurrency control that delivers several benefits for controlling the overhead amount which they enforce. DBMS Locks helps to maintain serializability to resolve the conflicts caused among the synchronized transactions. These lock-based protocols provide a mechanism where the transaction cannot w…
Recommended Articles
- This is a guide to DBMS Locks. Here we discuss definition, syntax, and parameters, How locks work in DBMS? examples with code implementation. You may also have a look at the following articles to learn more – 1. DBMS Components 2. DBMS Transaction Processing 3. DBMS_Scheduler 4. DBMS Multivalued Dependency