What is the best way to check for OWASP dependency vulnerabilities?
Dependency-Check is also available as a command line tool for your favorite OS. TL;DR: Add OWASP Dependency-Check to your build process to get insight into your dependency vulnerabilities.
What is dependency check?
Dependency-Check is a software composition analysis tool that identifies project dependencies on open-source code and checks if there are known vulnerabilities associated with that code. It was created by the Open Web Application Security Project (OWASP), a trusted non-profit organization aimed at improving the security of products and systems.
Should you add dependency-check to your Java project?
Other than not having the technology that stack Dependency-Check can help you with, there isn’t a reason not to at least add Dependency-Check to give a little insight into your open source dependencies. The following parts will help you get Dependency-Check integrated into your Java project’s build process.
How does dependency-check generate a report for a vulnerability?
Once the vulnerability data has been downloaded, Dependency-Check uses the CPE to retrieve the CVE information from the H2 database. The report is then generated with this information and add to the default /target directory. Dependency-Check can be configured to use other databases.
See more

What does Owasp mean?
The Open Web Application Security ProjectDefinition. The Open Web Application Security Project (OWASP) is a nonprofit foundation dedicated to improving software security.
How do you run a dependency check?
0:122:11OWASP Dependency Check: Part 2 - How to Scan Your Project - YouTubeYouTubeStart of suggested clipEnd of suggested clipSo we're going to type dependency check. And then we want to use the scan option and feed it theMoreSo we're going to type dependency check. And then we want to use the scan option and feed it the folder that our project is in you go ahead and hit enter.
Is Owasp dependency check free?
Dependency-Check was built by The Open Web Application Security Project (OWASP), a non-profit organization formed for application security. The solution is free to use, easy to integrate, and quick to report actionable information to ensure the security of your application.
What is dependency scanning?
The Dependency Scanning feature can automatically find security vulnerabilities in your software dependencies while you're developing and testing your applications. For example, dependency scanning lets you know if your application uses an external (open source) library that is known to be vulnerable.
How do you check the vulnerability of a jar?
The CLI identifies the package name, version, and vulnerabilities only if the package is available in Maven Central, and the JAR file hash matches the hash in Maven Central. Use the snyk test --scan-all-unmanaged CLI command to scan all JAR files in a single folder.
What does dependency determination mean?
A Dependency Determination is a document used to prove a Sponsor (military service member) is not only responsible for but does, in actuality, provide more than 50% of the support, or living expenses, of the dependent in question.
What tools are used in OWASP?
General TestingOWASP ZAP. The Zed Attack Proxy (ZAP) is an easy to use integrated penetration testing tool for finding vulnerabilities in web applications. ... Burp Proxy. ... Webstretch Proxy. ... Firefox HTTP Header Live. ... Firefox Tamper Data. ... Firefox Web Developer Tools. ... DOM Inspector. ... Grendel-Scan.More items...
What is OWASP checklist?
OWASP based Web Application Security Testing Checklist is an Excel based checklist which helps you to track the status of completed and pending test cases.
What are the benefits of OWASP?
Among the main benefits that OWASP provides to companies and IT professionals, we can highlight the following:helps make applications more armored against cyber attacks;helps reduce the rate of errors and operational failures in systems;contributes to stronger encryption;More items...
What are the types of dependency?
Dependency typesgoal dependency.task dependency.resource dependency.softgoal dependency.
How do you identify a dependency?
In order to identify project dependencies, you must first create a map of project tasks. Next, look for tasks that the team cannot perform until they receive information or deliverables from a previous task. Those tasks are dependent.
What is dependency with example?
Dependencies can occur between teams, initiatives, or deliverables. One very common example of an internal dependency would be requiring another team to do something they own within their function, before developers are able to deploy a new feature.
What is dependency check in Devops?
Dependency-Check is a Software Composition Analysis (SCA) tool that attempts to detect publicly disclosed vulnerabilities contained within a project's dependencies. It does this by determining if there is a Common Platform Enumeration (CPE) identifier for a given dependency.
What is dependency check in spring?
In Spring,you can use dependency checking feature to make sure the required properties have been set or injected....none dependency checking. ... simple dependency checking. ... objects dependency checking. ... all dependency checking.
What does waiting for dependency mean?
If the dependency status in a task's detail page is shown as Waiting for, it means the task is waiting for other tasks to be completed before it can be start. If the status is shown as Blocking, it means the task is blocking other tasks from starting before its completion.
What is CycloneDX?
OWASP CycloneDX is a lightweight Software Bill of Materials (SBOM) standard designed for use in application security contexts and supply chain component analysis. Strategic direction and maintenance of the specification is managed by the CycloneDX Core working group, with origins in the OWASP community.
What Is OWASP Dependency-Check?
Dependency-Check is a software composition analysis tool that identifies project dependencies on open-source code and checks if there are known vulnerabilities associated with that code. It was created by the Open Web Application Security Project (OWASP), a trusted non-profit organization aimed at improving the security of products and systems.
How does a dependency check work?
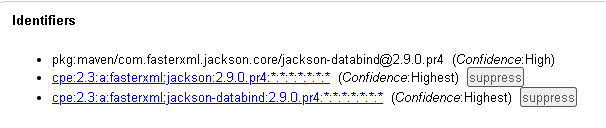
Dependency-Check works by collecting Evidence in the form of vendor, product, and version information, from files scanned by its Analyzers. Evidence is assigned a confidence level of low, medium, high, or highest according to its reliability.
Do you need a dependency vulnerability analyzer?
Regardless of the method you choose, if you want to maintain a secure environment and release secure products, you need to be using a dependency vulnerability analyzer of one type or another.
Is OWASP dependencies free?
In order to ensure that you are releasing secure products, you must have a solution in place that evaluates these dependencies and provides actionable information on fixes. OWASP Dependency-Check is a free, ...
What plugin does OWASP dependencies check?
Include the Maven plugin for OWASP Dependency Check in our project.
How does dependency check work?
Dependency Check works by identifying CPEs (Common Platform Enumerations) for each dependency and comparing them to a list of CVEs (Common Vulnerabilities and Exposures) from third party libraries such as the National Vulnerability Database . It then creates a report that allows you to quickly go through and view the possible dependency vulnerabilities in your application. While the report does quickly and easily present a list of dependencies with known vulnerabilities it can contain false positives and vulnerabilities that are not relevant to how you are using that specific dependency. It can be difficult correctly identify the risk of the issues presented.
What is dependency check?
Dependency-Check is a software composition analysis utility that identifies project dependencies and checks if there are any known, publicly disclosed, vulnerabilities. Currently, Java and .NET are supported; additional experimental support has been added for Ruby, Node.js, Python, and limited support for C/C++ build systems (autoconf and cmake). The tool can be part of a solution to the OWASP Top 10 2017 A9-Using Components with Known Vulnerabilities previously known as OWASP Top 10 2013 A9-Using Components with Known Vulnerabilities.
Does Dependency Check export test results?
Dependency Check supports exporting the results to JUNIT formatted test results . To parse the JUNIT test results, create a new Publish Test Results build task with the following configuration.
Why not add dependency check?
Other than not having the technology that stack Dependency-Check can help you with, there isn’t a reason not to at least add Dependency-Check to give a little insight into your open source dependencies. The following parts will help you get Dependency-Check integrated into your Java project’s build process.
What is dependency check in Maven?
If you have a Maven multi-module project, Dependency-Check provides an aggregate goal along with the check goal. This will allow the child project results to get rolled-up into the parent project report. Some of the details of the child project in which the CVE exists is lost as a result.
How long does dependency check take?
The initial download can take 10 – 20+ minutes. The data is stored in an H2 database located in the local M2 repo. Once the vulnerability data has been downloaded, Dependency-Check uses the CPE to retrieve the CVE information from the H2 database. The report is then generated with this information and add to the default /target directory.
Can a plugin be configured as a build or reporting plugin?
The plugin can be configured as a build or reporting plugin.
Can Dependency Check be used with other databases?
Dependency-Check can be configured to use other databases.
Can Dependency Check be overridden?
There are a few configuration defaults that can be overridden to make sure each build job isn’t slowed down too much by the Dependency-Check plugin . The analyzers are fairly quick but there could be a penalty if a data update is performed. As mentioned before, the initial database download is a drag but each incremental update is minor assuming Dependency-Check run a few times a day.
