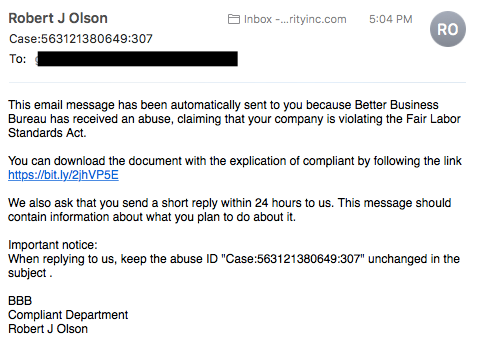
SMS phishing
In computing, SMS phishing or smishing is a form of criminal activity using social engineering techniques. Phishing is the act of attempting to acquire personal information such as passwords and details by masquerading as a trustworthy entity in an electronic communication. Short Message Service is the technology used for text messages on cell phones.
What is phishing and vishing?
What is Phishing, Vishing, SMiShing and Pharming? (Infographic) Phishing is a scam which targets victims via email where individuals are encouraged to click through to fraudulent sites, give personal information about themselves or even send money. The scams vary widely but a majority of them are fairly easy to spot.
What is vishing and SMiShing?
This bring us onto vishing and SMiShing. Vishing, or voice phishing, is a type of phishing attack that involves using a phone to trick victims into handing over sensitive information, rather than an email.
What is smishing and how can you prevent it?
Smishing is short for SMS phishing and it works much the same as phishing. Users are tricked into downloading a Trojan horse or virus onto their phones from an SMS text as opposed from an email onto their phone. Social engineering techniques are also used to leverage personal information and money from victims.
What are the different types of phishing?
But this is done in different ways: 1 In phishing – via e-mail. 2 In vishing – by means of a phone call. 3 In smishing – via SMS. 4 In pharming – by using the DNS cache on the end user device or the network equipment of the provider.
What's the difference between phishing vishing and smishing?
Phishing: fraudulent e-mails and websites meant to steal data. Vishing: fraudulent phone calls that induce you to reveal personal information. Smishing: fraudulent text messages meant to trick you into revealing data.
What pharming means?
Pharming is like phishing in that it is a threat that tricks users into divulging private information, but instead of relying on email as the attack vector, pharming uses malicious code executed on the victim's device to redirect to an attacker-controlled website.
What is smishing and vishing attack?
Smishing and vishing are two types of fraud that use SMS (smishing) and voice (vishing) to trick people into giving up money or personal information.
What is Smishing in cyber security?
Smishing is a form of phishing attack that targets mobile devices. Instead of sending phishing content over email, smishers use SMS or MMS text messages to deliver their messages.
How do you say pharming?
0:051:00How To Say Pharming - YouTubeYouTubeStart of suggested clipEnd of suggested clipFor me por mí for me por mí for me for me.MoreFor me por mí for me por mí for me for me.
What is a vishing attack?
Vishing – a portmanteau of voice and phishing – attacks are performed over the phone, and are considered a type of a social engineering attack, as they use psychology to trick victims into handing over sensitive information or performing some action on the attacker's behalf.
What is vishing attack example?
Vishing attacks examples include: The fraudster calls the victim saying they are from their bank or another institution and informs them that there is a problem with their account or credit card. The false alert may also arrive by SMS initially, asking the person to call a number to resolve the issue.
Why is it called phishing?
The word is a variant of fishing, influenced by phreaking, and alludes to the use of increasingly sophisticated lures to "fish" for users' sensitive information. Attempts to prevent or mitigate the impact of phishing incidents include legislation, user training, public awareness, and technical security measures.
How do pharming attacks work?
In a pharming attack, users aren't tricked into navigating to a malicious website. Instead, the attacker steals data using malware background processes or automatically sends a user to a phishing website in their browser. Pharming is much more effective than phishing because it doesn't require the user to click a link.
How is phishing different from pharming?
In phishing, the attacker tries to find the sensitive information of users by the means of electronic communication illegally. Pharming is a more advanced technique to get users' credentials by making effort to enter users into the website. It is an attempt to scam people one at a time via an email or instant message.
How would you know if someone is trying to pharming you?
Pharming attack warning signs Here are two signals of pharming. An unsecure connection. If your site address says “http” instead of “https” in the address line, the website may be corrupted. A website doesn't seem right.
What is Prepending in cyber security?
7. Prepending. Prepending is basically adding mentions, the @username, whether it's Twitter or some type of social media, to tweets or other social media posts to make them seem more personal. So what that does is it creates a higher engagement.
What is phishing email?
Place of birth or other common password retrieval question. Phishing is a scam which targets victims via email where individuals are encouraged to click through to fraudulent sites, give personal information about themselves or even send money.
What to do if you receive an unexpected request via email, text message or phone call?
If you received an unexpected request via email, text message or phone call to take some kind of action, the best course is to check the company’s details via their website and take any actions using those details.
What to do if you are in any doubt about correspondence received?
If you are in any doubt about correspondence received, send it on to the customer service or security of the company in question to verify it.
Can scammers piggy back on text messages?
Avoid clicking on links within text messages. It is even possible for scammers to piggy back onto existing message threads from trusted sources, like your bank. Double check all sources before sharing personal data or moving money if prompted to do so by text message.
Is spear phishing easy to spot?
The scams vary widely but a majority of them are fairly easy to spot. Other variations of phishing are spear phishing and whaling, they are both targeted forms of phishing in which managers, directors and CEO’s are the objective.
How does phishing work?
Phishing attacks exploit two vulnerabilities in an organization: human error, and our global reliance on email communication. The attacker sends an email to their victim, posing as a trusted source or contact, in order to manipulate them into handing over sensitive data such as financial information or login credentials. They usually do this by encouraging the user to click on a URL that takes them to a fake login page, where they enter their credentials for the attacker, or by convincing the user to download a malicious attachment that installs malware such as a keylogger onto their machine, enabling the attacker to steal data by tracking their keystrokes.
What is spear phishing?
Spear phishing attacks target one user at a time. The attacker puts a lot more effort into learning about their victim, including the details of their job role and the people they connect with on a regular basis. This enables the attacker to send a highly personalized email that’s much more difficult to detect.
How Can You Stop Social Engineering Attacks?
The second step is implementing a strong email security architecture to help prevent your employees from receiving malicious content in the first place, and to encourage them not to open any suspicious messages that do slip through.
How many phishing attacks are delivered by email?
Recent research has shown that 96% of phishing attacks are delivered by email, but it’s important that you’re aware of the other mediums that attackers can utilize to gain access to your organization’s data. This bring us onto vishing and SMiShing.
Why does the dwell time of a phishing attack decrease?
When employees have completed a training program, the dwell time of an attack decreases dramatically, because trained employees are much quicker at reporting phishing attempts. According to Cofense’s study, which analyzed the millions of results across their simulated phishing campaigns, 82% of trained employees reported a simulated phish within an hour, 52% reported it within 5 minutes, and 19% within 30 seconds of receiving the simulated attack.
How does deepfake work?
They use a branch of artificial intelligence called “deep learning” to analyze what the source material looks or sounds like, and replicate that onto another image, video or sound bite, making it appear to be an original. In deepfake vishing attacks, the imposter usually poses as a manager or C-level executive and asks their victim to complete an urgent transfer of money or data.
How many recipients can a phishing attempt target?
Traditional phishing attempts target hundreds or even thousands of recipients at once. Because of this, the content of the message is impersonal, so attacks can be fairly easy to spot, as the message content won’t always be relevant to the recipient. For example:
Dark Web Analysis
We've all heard of the Dark Web, but what is it? Where is it? Should normies venture there? Hint: You can't get there from your Chrome browser.
Email Security Best Practices for Businesses
Email security best practices involve trying to change employee behavior through drills like a phishing test for employees.
Common Phishing Techniques: Can You Unmask Them?
Pharming vs. Smishing vs. Vishing: Can you identify these common phishing techniques?
Navigating Trademark and Copyright Law in Cybersecurity
In cybersecurity awareness training, authenticity is key. Let's take a look at navigating trademark law in cybersecurity.
How does scamming work?
Through the use of a virus or similar technique, your browser is hijacked without your knowledge. You type a legitimate website into the address bar of a browser and the virus redirects you to a fake site. Although you entered the website address in the browser yourself and the website appears identical to the site you are accustomed to doing business with, you have actually been redirected to a different site. You enter in your identifying information , such as bank passwords and credit card numbers, and unknowingly submit it to someone who is out to steal your identity .
Is phishing a scam?
Many consumers are now familiar with the Internet scam known as “phishing”. This is a spam message that contains a link to what appears to be a legitimate business, such as your bank, but it is actually a fake website.
What is spear phishing?
That is targeting a specific individual for specific information that can be used against them or their organization. The extension of Spear Phishing is Whaling, where an executive, celebrity or high-ranking government official is targeted. In comparison, a Phishing email expedition to tens of millions of email addresses is like a swarm of krill. Wait a minute, I just invented a new term: Phrilling.
What is fishing for information?
Traditionally, fishing for information took place face to face where someone would ask round-about questions on a topic they wanted to know more about. Think about the soft side of interrogation. Of course, an actual criminal interrogation requires some deft and psychological techniques to get an uncooperative suspect to talk.
Do criminals change their tactics?
As consumers have become accustomed to being wary about emails they don’ t recognize or expect, the criminals are changing their tactics. Not that the old tactics will go away, just look at your spam filter, but the smart ones are turning over new ground.
What is smishing, vishing, and spear phishing?
Essentially, smishing, vishing, and spear-phishing are becoming increasingly popular tactics for hackers to breach companies’ critical systems. Though typical phishing strategies are still very commonly used, many companies have properly trained employees to recognize and avoid phishing emails. For this reason, attackers are relying more and more on smishing, vishing, and spear-phishing. Though these attacks appear to be difficult to detect, it is quite the opposite. There are some clear indications that a message, call, or email is a social engineering attack. Businesses should train their staff to recognize the hallmarks of smishing, vishing, and spear-phishing, and implement procedures to reduce the probability of a successful social engineering attack.
How much does phishing cost?
Overall, these forms of phishing can result in chaos and require significant sums to rectify. Successful phishing attacks cost an average of $3.86 million according to Norton. Spear-phishing emails can sometimes cost more. Small Business Trends says that spear-phishing payouts average $7.2 million. Some have to pay more.
What is phishing email?
Phishing is a social engineering tactic used by hackers to obtain sensitive data, such as financial information or login details. Attackers send fraudulent emails, disguised as legitimate emails from a trustworthy institution, in order to deceive targets into giving personal information. Smishing, vishing, and spear-fishing are derivatives ...
What is the tactic used by Russian hackers to hack into people's email?
This allowed hackers to obtain their login and password credentials. This breach was enacted through a tactic called spear-phishing.
How many people use spear phishing?
The same report states that even now, 65% of attackers use spear-phishing as a primary mode of infection. Targeting specific people, oftentimes people with great power, influence, or wealth, can allow for great benefits. Overall, these forms of phishing can result in chaos and require significant sums to rectify.
Who is Akhil Deo?
Akhil Deo. Akhil Deo is a high school student with an avid interest in computer science, cybersecurity and robotics. He has participated in and has won prizes in a number of competitions in robotics, coding and cybersecurity and has gained success at the national level.
Is email a social engineering attack?
There are some clear indications that a message, call, or email is a social engineering attack. Businesses should train their staff to recognize the hallmarks of smishing, vishing, and spear-phishing, and implement procedures to reduce the probability of a successful social engineering attack.
The 3 siblings of cyber scams explained
Although similar in name, the three siblings of cyber scams differ in some important respects. As well as their central channel to scam people, phishing, vishing, and smishing can vary in the indicators they offer to suggest they are not genuine.
How to protect yourself from cyber scams
Now that you know the different types of cyber scams, it’s important to take preventative measures to secure your email and phone. Particularly in a business context, having employees regularly trained to protect themselves from cyber threats and report spam calls can save your business from serious security breaches and potential financial losses.