
Full Answer
What are access control best practices?
Six best practices to follow in access control
- Planning for access control. This is the most important stage of organizing access control since what you do here will affect the next two stages.
- Setting up an access control solution. Despite the careful planning things can get awry if you don’t set up the system as planned. ...
- Operating an access control system. ...
What are access control policies?
Policies
- The Need-to-Know Principle. The need-to-know principle dictates that users should only have access to whatever resources they need to perform their job.
- Password Policy. A password policy establishes rules around what passwords are acceptable, and how users can handle their passwords.
- Physical Access Policy. ...
- Remote Access Policy. ...
- Audit Policy. ...
How to implement a basic access control list?
The options are:
- access_list_name —The name of the new or existing ACL.
- Line number—The line line_number option specifies the line number at which insert the ACE; otherwise, the ACE is added to the end of the ACL.
- Permit or Deny—The deny keyword denies or exempts a packet if the conditions are matched. ...
What are access control procedures?
Access control procedures are the methods and mechanisms used by Information Owners to approve permission for Users to access data, information and systems. AUTHENTICATION Authentication is the process of identifying an Information User by the User presenting credentials. In a computer system, this is most often accomplished by using the unique
What is policy based access control?
What is PBAC in IAM?
Which type of access control is policy based?
Definition(s): A strategy for managing user access to one or more systems, where the business roles of users is combined with policies to determine what access privileges users of each role should have.
What is meant by access control policy?
Access control policies are high-level requirements that specify how access is managed and who may access information under what circumstances.
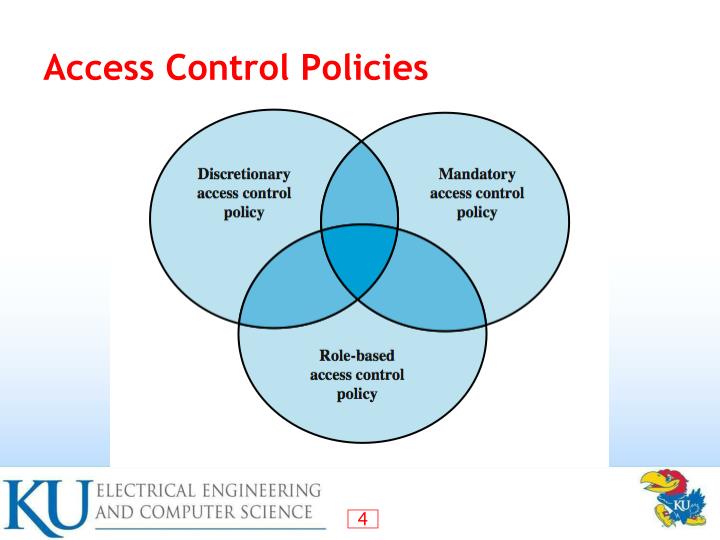
What are the 3 types of access control?
There are three core types of IP access control: discretionary, managed, and role-based. Discretionary access control is extremely flexible and nonrestrictive compared to its alternatives. This is because access rights are specified by users.
What is role-based access control policy?
Role-based access control (RBAC) is a method of restricting network access based on the roles of individual users within an enterprise. RBAC ensures employees access only information they need to do their jobs and prevents them from accessing information that doesn't pertain to them.
What are the 4 types of access control?
Access Control: Models and MethodsThis response leads to more frustration as the user needs to get on with their task and all they need is access to one folder. ... Mandatory Access Control (MAC)Role-Based Access Control (RBAC)Discretionary Access Control (DAC)Rule-Based Access Control (RBAC or RB-RBAC)More items...
What are the two types of access control?
There are two types of access control: physical and logical. Physical access control limits access to campuses, buildings, rooms and physical IT assets. Logical access control limits connections to computer networks, system files and data.
What are the five categories of access control?
The 5 Different Types of Access ControlManual access control.Mechanical access control.Electronic access systems.Mechatronic access control.Physical access systems.
What is the best type of access control?
Discretionary Access Control (DAC) DAC systems are considered to be the most flexible and offer the highest number of allowances compared to other types of access control.
What is the best access control model?
Mandatory Access Control (MAC): the Secure Model. Under mandatory access control (MAC), security administrators set access labels for both users and objects. Mandatory access control is the most secure of the major access control models, and also the most demanding to maintain.
What is an example of role based access control?
One role-based access control example is a set of permissions that allow users to read, edit, or delete articles in a writing application. There are two roles, a Writer and a Reader, and their respective permission levels are presented in this truth table.
What is the difference between role based access control and rule-based access control?
Rule-based access controls are preventative – they don't determine access levels for employees. Instead, they work to prevent unauthorized access. Role-based models are proactive – they provide employees with a set of circumstances in which they can gain authorized access.
What are the three primary rules for RBAC?
The components of RBAC such as role-permissions, user-role and role-role relationships make it simple to perform user assignments.
Which levels of access can be defined in the policies?
Key Points For PoliciesPolicies only allow access; they cannot deny it.You can give policies at two-level, i.e, Compartment Level & Tenancy Level.By default, users can do nothing and have to be granted access through policies.An administrator in your organization defines the groups and compartments in your tenancy.
What are access control security services?
Access control identifies users by verifying various login credentials, which can include usernames and passwords, PINs, biometric scans, and security tokens. Many access control systems also include multifactor authentication (MFA), a method that requires multiple authentication methods to verify a user's identity.
What is an acceptable use policy?
An acceptable use policy (AUP) is a document stipulating constraints and practices that a user must agree to for access to a corporate network, the internet or other resources. Many businesses and educational institutions require employees or students to sign an AUP before being granted a network ID.
What is physical security policy?
Physical security is the practice of protecting elements of government infrastructure, estates and personnel against attacks or compromises in the physical (tangible, real-world) environment.
PBAC - Military and Government - Acronym Finder
The World's most comprehensive professionally edited abbreviations and acronyms database All trademarks/service marks referenced on this site are properties of their respective owners.
Policy-based Access Control in Practice - W3
Policy-based Access Control in Practice Phil Hunt, Rich Levinson, Hal Lockhart, Prateek Mishra Oracle Corporation 1. OpenAz: A framework for Building and Deploying XACML
What Is Policy-Based Access Control (PBAC)?
Attributes are used in Policy-Based Access Control (PBAC) to implement access constraints based on business policies dynamically. Unlike static types of authorization such as Role-Based Access Control (RBAC), PBAC allows you to quickly alter entitlements in response to new rules or business policy without auditing and changing roles across the organization. This feature guarantees that assets do not become jeopardized and that requirements get followed.
Can You Implement PBAC Alongside RBAC?
When deciding between RBAC and PBAC, consider that PBAC can get built to behave like RBAC more consistently than the other way around.
What is a PBAC?
Policy-Based Access Control (PBAC) is an authorization approach composed of using both attributes and roles to determine access rights. PBAC goes beyond even Attribute-Based Access Control (ABAC) to meet the fast, constantly changing, remote access needs of companies as they move increasingly towards cloud-based applications.
Why are RBAC and ABAC not enough?
Management can then add and edit the roles when needed. However, this approach isn’t scalable, because as a company expands but, as the company expands it’s impossible to track the growing number of changing user roles, leading to ‘ role explosion ’.
Can management edit roles?
Management can then add and edit the roles when needed. However, this approach isn’t scalable, because as a company expands but, as the company expands it’s impossible to track the growing number of changing user roles, leading to ‘ role explosion ’.
Can a bank manager access client basic profile?
Banking: Bank management can easily create a policy that states (ideally in plain language) that “ Branch Managers can access the Client Basic Profile, Bank Accounts and Card Data of clients that belong to the same Line of Business (LoB) and same branch as themselves ”. The genius of the GUI-based PBAC is that you don’t need to reference specific LoBs or bank profiles. Everything is simplified through the visual representation.
What is PBAC in data center?
PBAC helps consolidate, control, and simplify access privileges, whether the critical applications are hosted in traditional data centers, private clouds, public clouds, or a hybrid combination of all these spaces. Read the Whitepaper: 5 Myths About Policy-Based Access Control.
What is a business policy example?
For example, let's say the business policy is: “Traders can execute trades”. Trades are managed in the trading system, that is based on a backend application and web-based frontend. The same access decision must be provided to all layers, in the authorization language it understands.
What is the tough part about ABAC?
The tough part about ABAC is that you must have attributes, but that’s easier said than done. In many cases, attributes are not that organized nor available. The building blocks of PBAC are the pieces of information and data, etc. that it relies on to make the access decisions. Attributes are only one part of these blocks. The PBAC method offers a flexible solution to its policy building blocks, to enable the usage of any existing data as part of the decision making.
What is PBAC in IAM?
The time has come for Policy Based Access Control (PBAC), a standard that combines the best of both RBAC and ABAC while offering a way to overcome their shortcomings. The first thing that you need to know about PBAC, is that it's not based on any one implementation ( XACML, for example), but rather a method to manage access decisions and authorizations regardless of technical implementation. Another important point is that it is capable of scaling and building on existing IAM, while providing an access-control solution according to context-based policies.
Why is PBAC important?
That means IT teams have less visibility into and control over identities work practices. By centralizing access control and management PBAC enables IT to define and dictate access control no matter where employees are, what time zone they’re in, what device they’re using, etc.
Is PBAC agnostic?
It’s flexible with technology. PBAC should be agnostic to the consuming application. Policies express the business meaning, and the decision is provided to any consuming application, regardless of its technical implementation. For example, let's say the business policy is: “Traders can execute trades”.
What is policy based access control?
What is policy-based access control? Also known as PBAC, policy-based access control is the exact same thing as attribute-based access control (ABAC). When one mentions PBAC, they tend to focus on the policy language rather than the attributes but in fact both policies and attributes are equally important.
What is ABAC in NIST?
As a best practice, ABAC is the term that is most commonly used and is the one that NIST (the National Institute of Standards and Technology) uses. What is attribute-based access control? Also known as ABAC, attribute-based access control is the latest in the evolution of authorization.
The Purpose of Access Control Policies
Here are a few benefits associated with having clear access control policies in place:
Types of Access Control Policies
Generally speaking, you can define these policies in terms of administrative, physical, and technical or logical access control policies. Administrative policies are responsible for setting up the policies that will be implemented across the entire organization. Administrative policies are a combination of the other two policies.
Policy-Based Access Control
Policy-based access control is a combination of role-based access control and business policies. It is different from role-based access control, where all privileges and access controls are solely decided based on an individual’s roles because, in policy-based access control, roles and policies are both important components of access control.
Access Control Policies to Data
This discussion brings us to the question:how and why do access control policies define the security of data in an organization? The consideration here is simply that limiting data access for people based on specific policies and standards makes the chances of data loss, data exposure, or data misuse almost none.
Examples of Access Control Policies on Data
A policy may restrict users to only access sensitive data and information from the office or during their shift timings and from the IP address of office systems.
Access Control Standards
The standards of access control can be defined as per the organization’s associated goals. However, there are also some international and industrial standards that define the quality and implementation level of access control policies of an organization.
Conclusion
Access control policies help define the standards of data security and data governance for organizations. They set up the level of access to sensitive information for users based on roles, policies, or rules.
What is policy based access control?
Policy Based Access Control is the foundation of context-driven access control models, which are essential to developing viable, dynamic approaches to manage risk across inter-connected systems. Realizing the benefits of PBAC begins with comprehensive data modeling around users (by role/job function) and application privileges. This data model is not just a means of arriving at a PBAC design; it is the definitive specification of the data requirements to develop effective policies. It could be argued that the proliferation of access control models has come about because of the limitations in understanding application, system, and user data. PBAC provides a framework to manage user access in a single model type, meaning less time will be spent on disparate access management activities. This framework is consistent with organizational risk management objectives and is an example of how a data-oriented approach can support business agility without compromising usability or security.
What is PBAC in IAM?
Policy Based Access Control (PBAC) offers an advanced framework to centrally manage permissions and provide assurance for the enterprise in a scalable solution. The first step in maturing your IAM program is assessing your needs and identifying the scenarios where PBAC can help automate risk mitigation. Click here to watch on-demand now.
